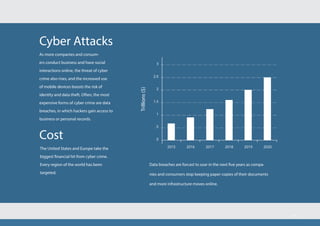
Cubeitz is an advanced encryption software designed to protect data from breaches, leveraging a unique one million bit encryption engine. It offers a solution for personal, business, and government use, ensuring that data stored locally or in the cloud remains secure and encrypted. The platform allows seamless sharing of files and instant messaging while overcoming vulnerabilities of traditional technology.