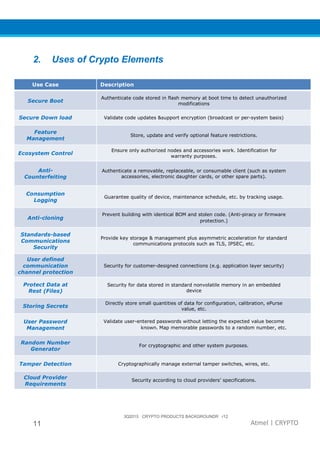
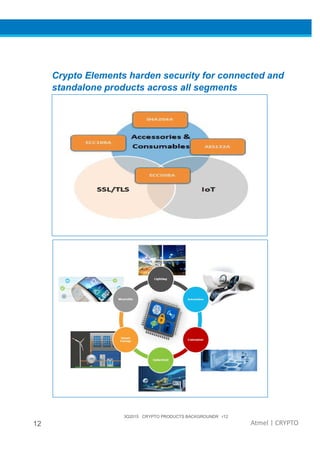
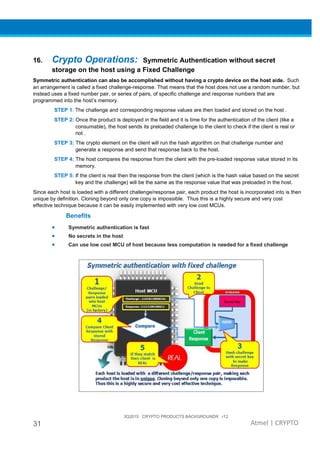
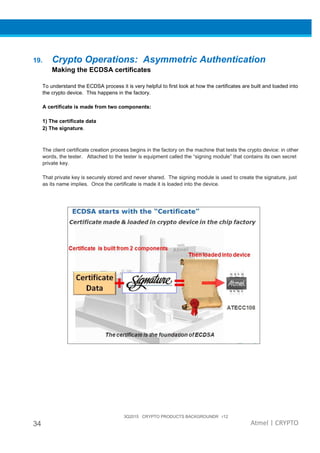
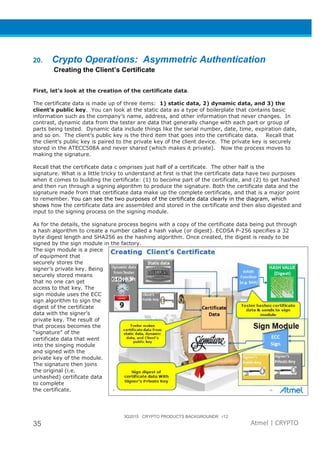
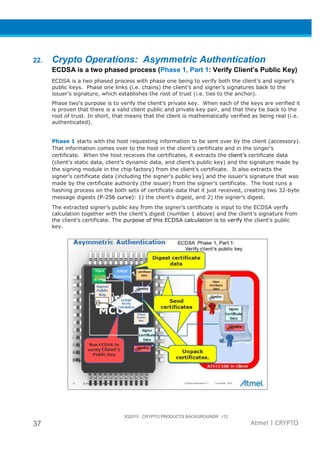
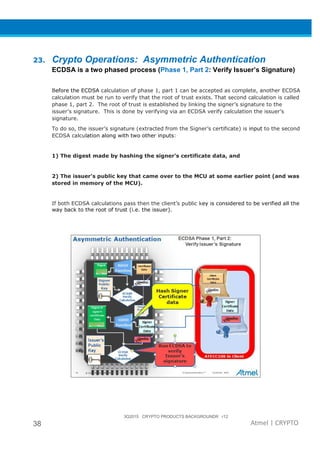
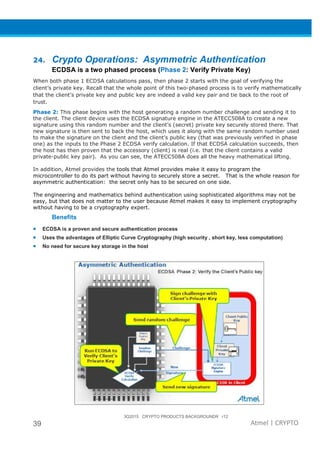
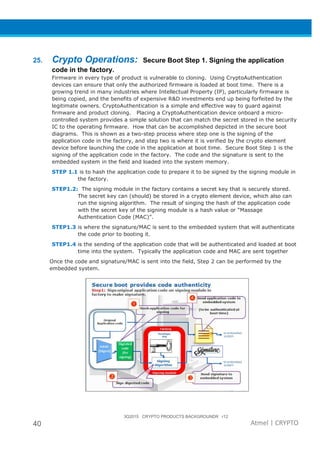
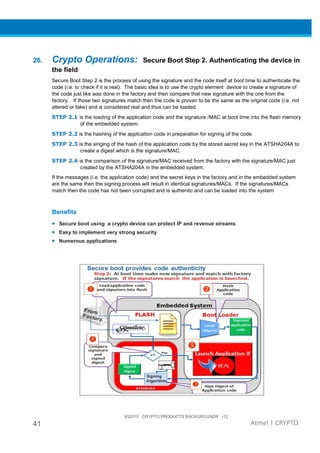
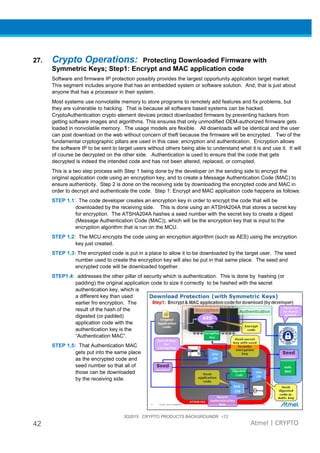
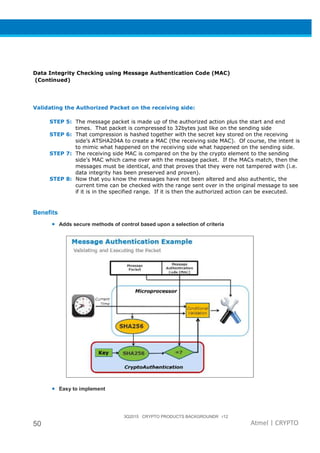
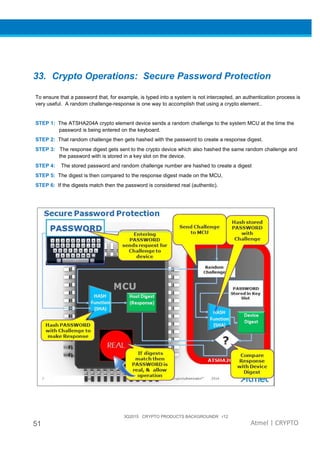
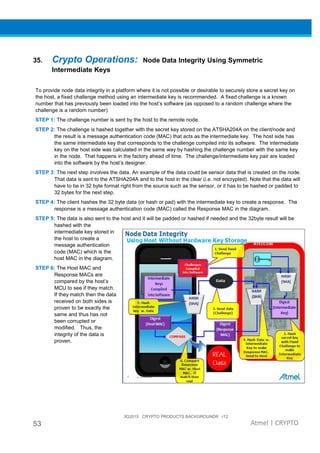
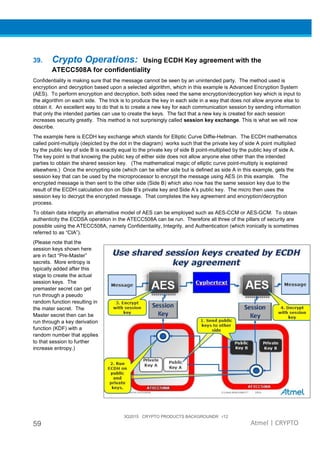
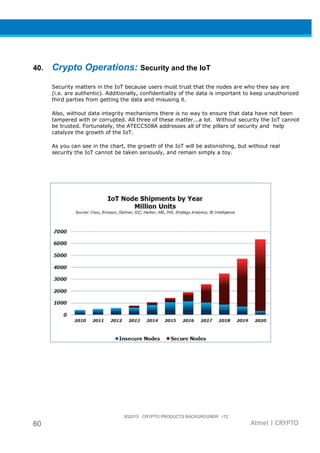
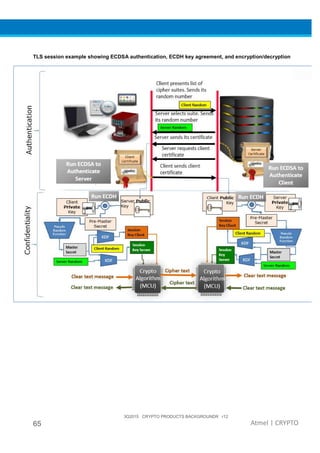
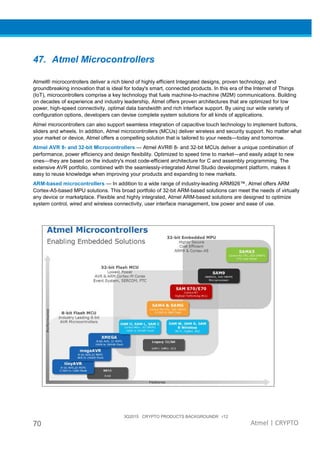
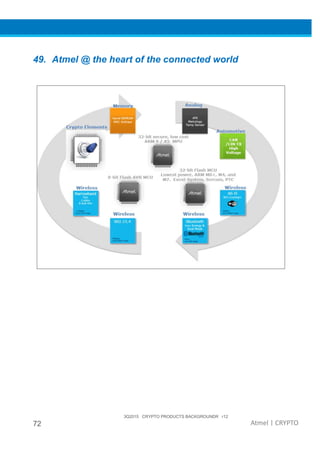
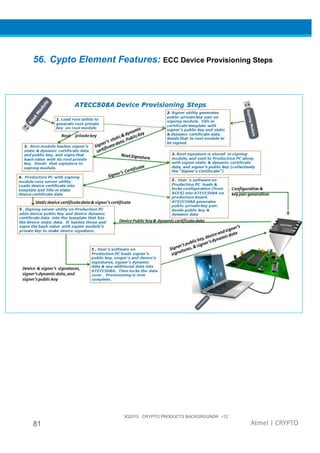
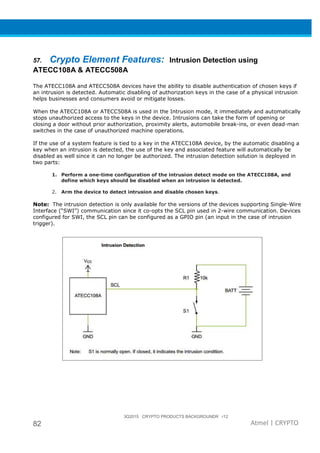
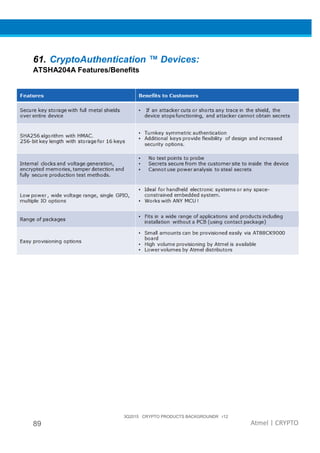
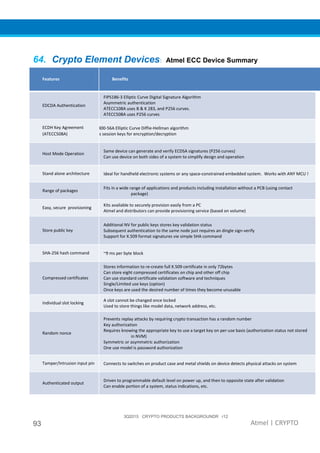
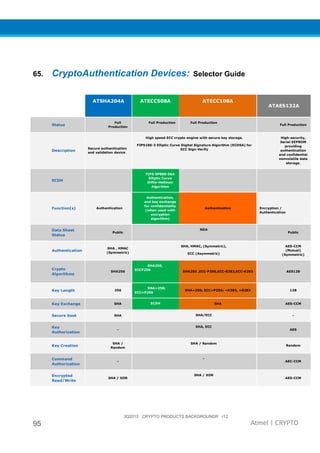
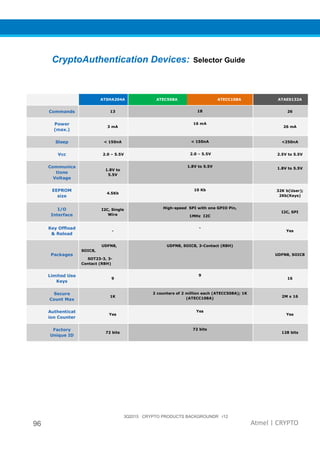
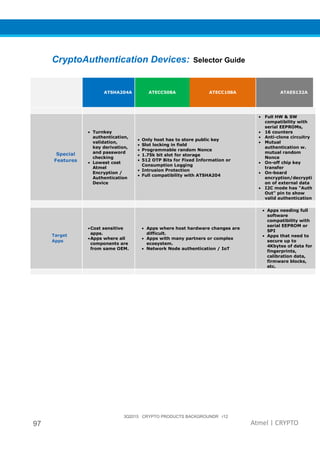
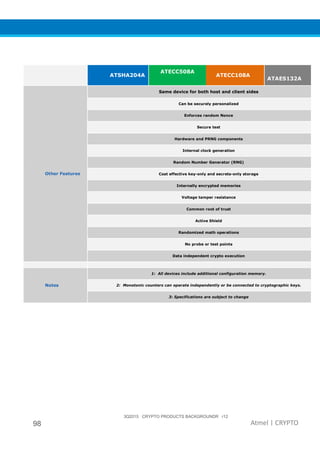
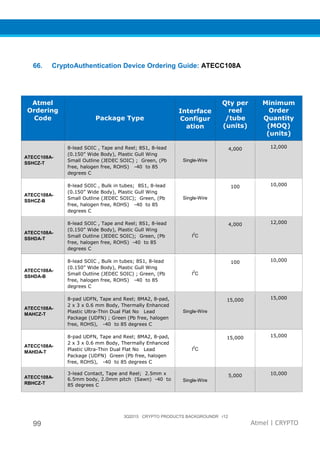
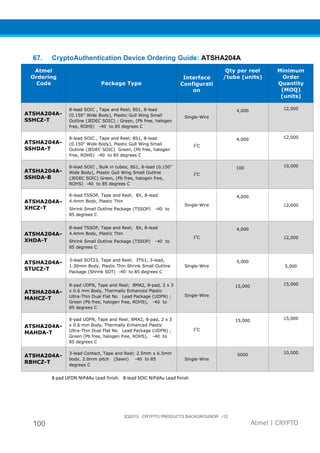
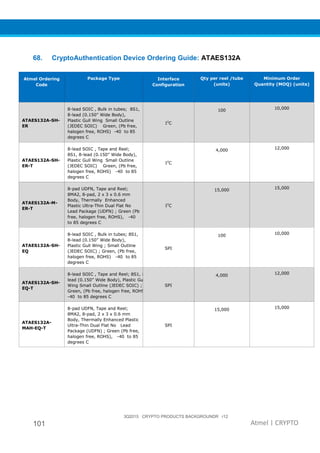
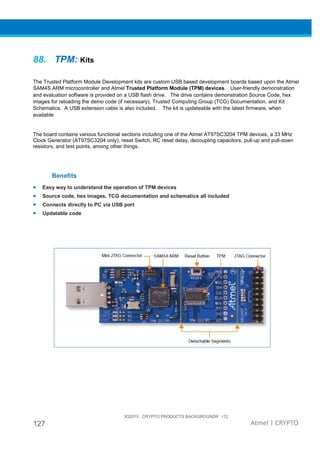
The document provides an overview of Atmel's crypto element devices, which utilize hardware-based key storage to protect products from cloning and tampering. It outlines their support for modern cryptographic standards and their wide range of applications, emphasizing the importance of robust security in connected and standalone products. Additionally, it serves as an introductory reference for users to integrate strong security measures into their digital systems without requiring extensive cryptographic knowledge.