This document discusses abusing public keyservers by uploading large, bloated keys and files using PGP. It introduces PGP File System (PGPFS), a proof-of-concept that stores files encrypted in PGP keys and uploads them to keyservers. While slow and relying on obscurity, PGPFS ensures keys are never truly deleted and replicates data across keyservers. The document argues this is an amusing way to abuse keyservers since they cannot delete keys. It provides code and invites questions.





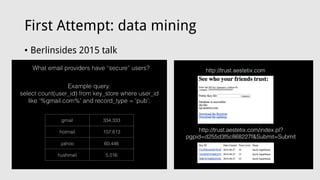
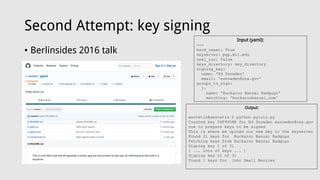
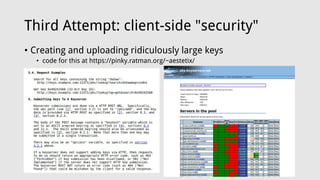
![Third Attempt: client-side "security"
• Creating and uploading ridiculously large keys
• code for this at https://pinky.ratman.org/~aestetix/
aestetix@pinky ~/public_html $ ls -lah please_sir.gpg
-rw-r--r-- 1 aestetix users 1.9M Jun 17 2016 please_sir.gpg
aestetix@pinky ~/public_html $ ./gpg2 --list-packet please_sir.gpg
:public key packet:
version 4, algo 17, created 1466190081, expires 0
pkey[0]: [2048 bits]
pkey[1]: [256 bits]
pkey[2]: [2048 bits]
pkey[3]: [2048 bits]
keyid: F591661738FFED2F
:user ID packet: "{ 1.9 megs of crap }"
:signature packet: algo 17, keyid F591661738FFED2F
version 4, created 1466190081, md5len 0, 2 1)
hashed subpkt 21 len 5 (pref-hash-algos: 8 2 9 10 11)
hashed subpkt 22 len 2 (pref-zip-algos: 2 1)
hashed subpkt 30 len 1 (features: 01)
hashed subpkt 23 len 1 (key server preferences:](https://image.slidesharecdn.com/berlinsides2017-170527201105/85/Berlinsides2017-12-320.jpg)
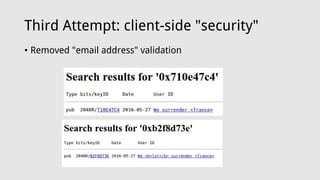
![Third Attempt: client-side "security"
• Creating and uploading ridiculously large keys
• code for this at https://pinky.ratman.org/~aestetix/
aestetix@pinky ~/public_html $ ls -lah please_sir.gpg
-rw-r--r-- 1 aestetix users 1.9M Jun 17 2016 please_sir.gpg
aestetix@pinky ~/public_html $ gpg --list-packet
please_sir.gpg
gpg: packet(13) too large
# off=0 ctb=99 tag=6 hlen=3 plen=814
:public key packet:
version 4, algo 17, created 1466190081, expires 0
pkey[0]: [2048 bits]
pkey[1]: [256 bits]
pkey[2]: [2048 bits]
pkey[3]: [2048 bits]
keyid: F591661738FFED2F
# off=817 ctb=b6 tag=13 hlen=5 plen=1398149
:user ID packet: [too large]
aestetix@pinky ~/public_html $ gpg --keyserver pgp.mit.edu --
search-keys F591661738FFED2F
gpg: data source: http://pgp.mit.edu:11371
(1)
DZl60ir7WOuOTHODbIMVaLzlDNQGKtaaLXFuIRMPhQemnKKp0AKd
vdYQrP83POYbnqqz/2
2048 bit DSA key F591661738FFED2F, created: 2016-
06-17
Keys 1-1 of 1 for "F591661738FFED2F". Enter number(s), N)ext,
or Q)uit > 1
gpg: packet(13) too large
gpg: read_block: read error: Invalid packet
gpg: Total number processed: 0](https://image.slidesharecdn.com/berlinsides2017-170527201105/85/Berlinsides2017-13-320.jpg)