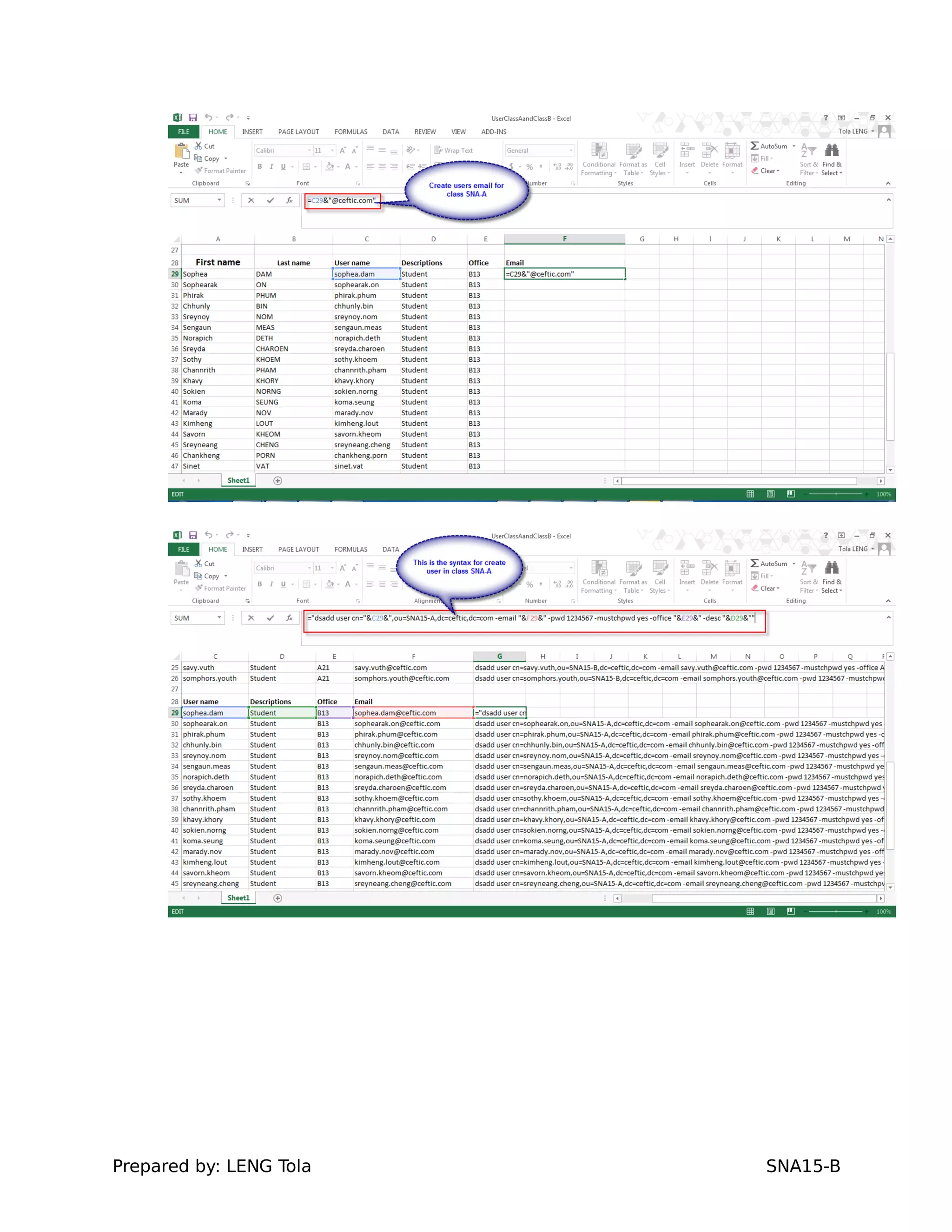
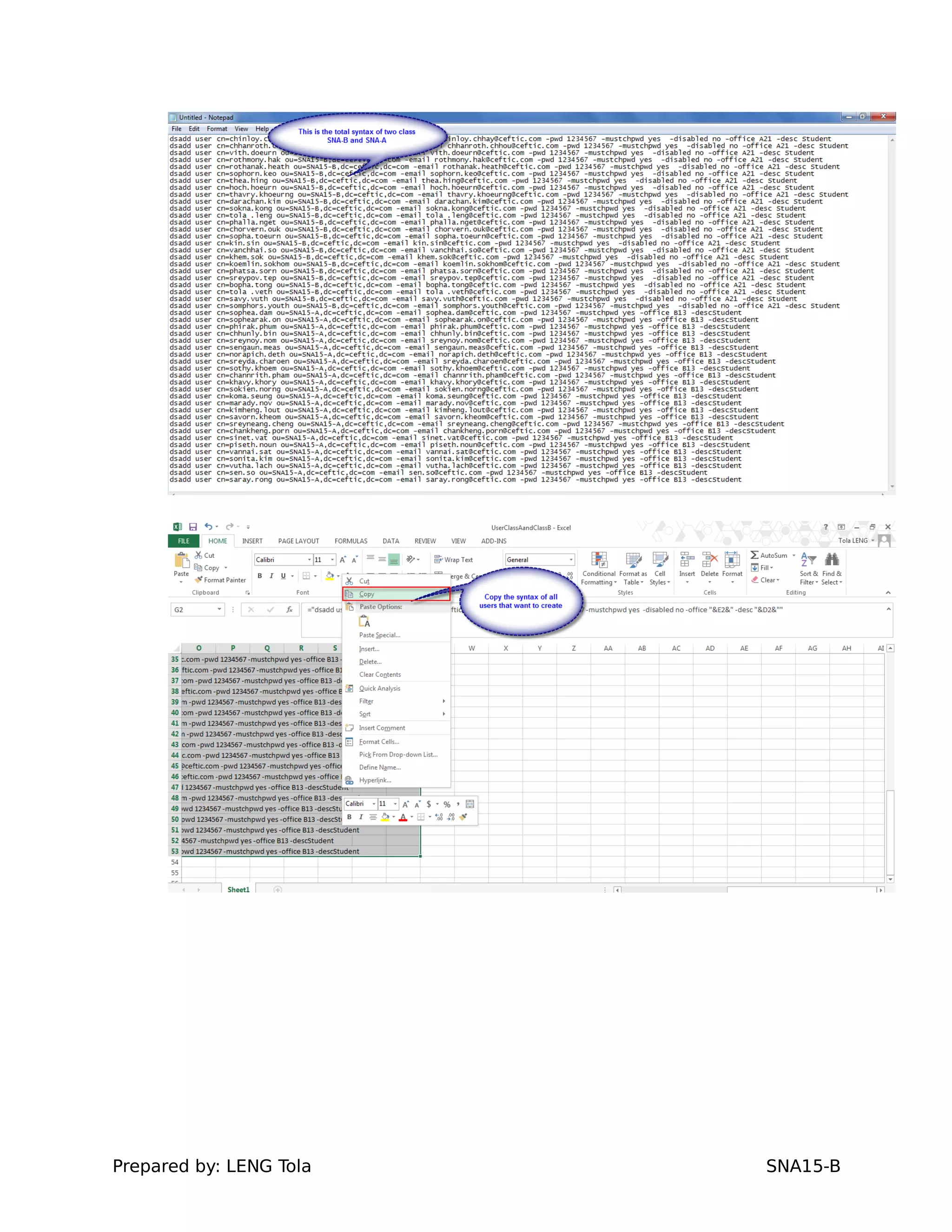
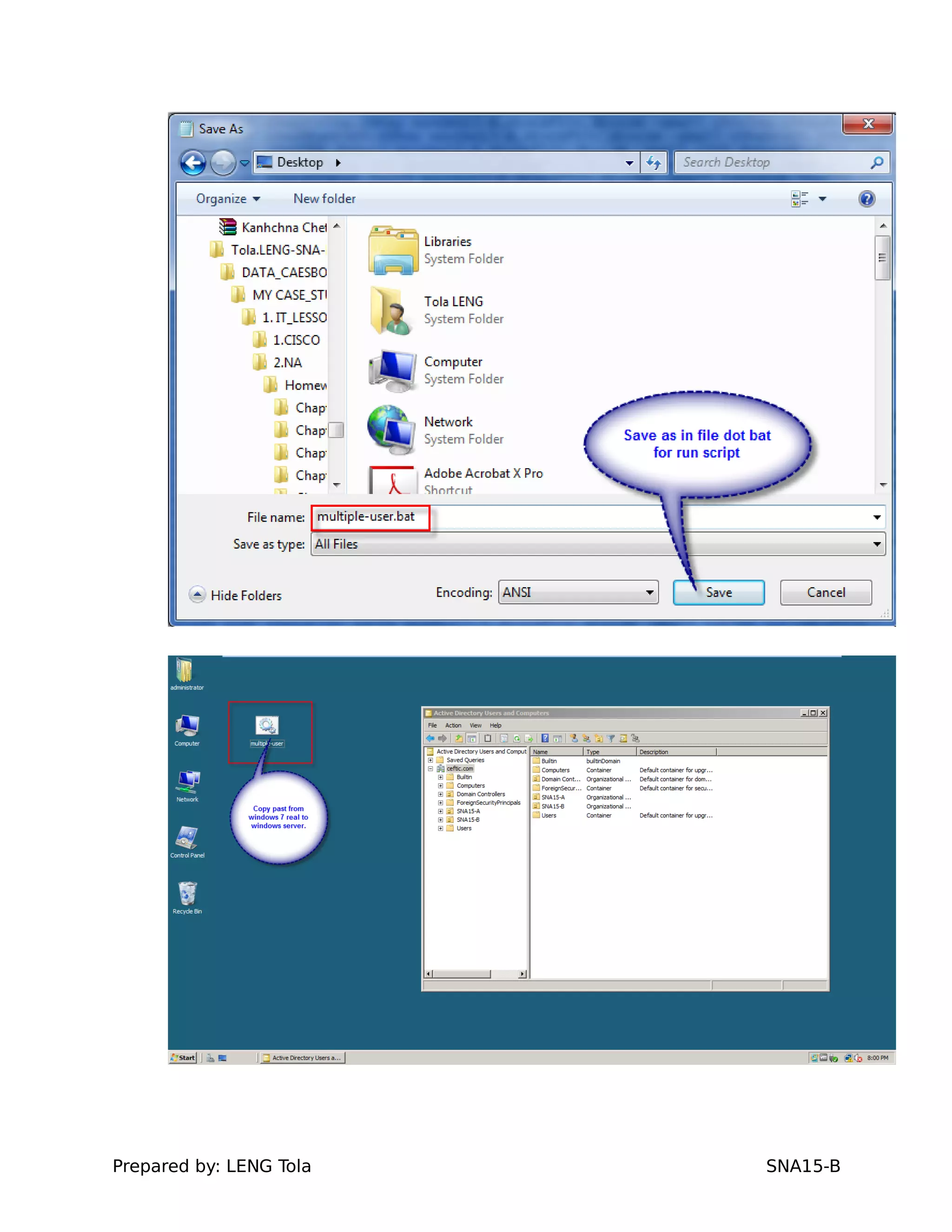
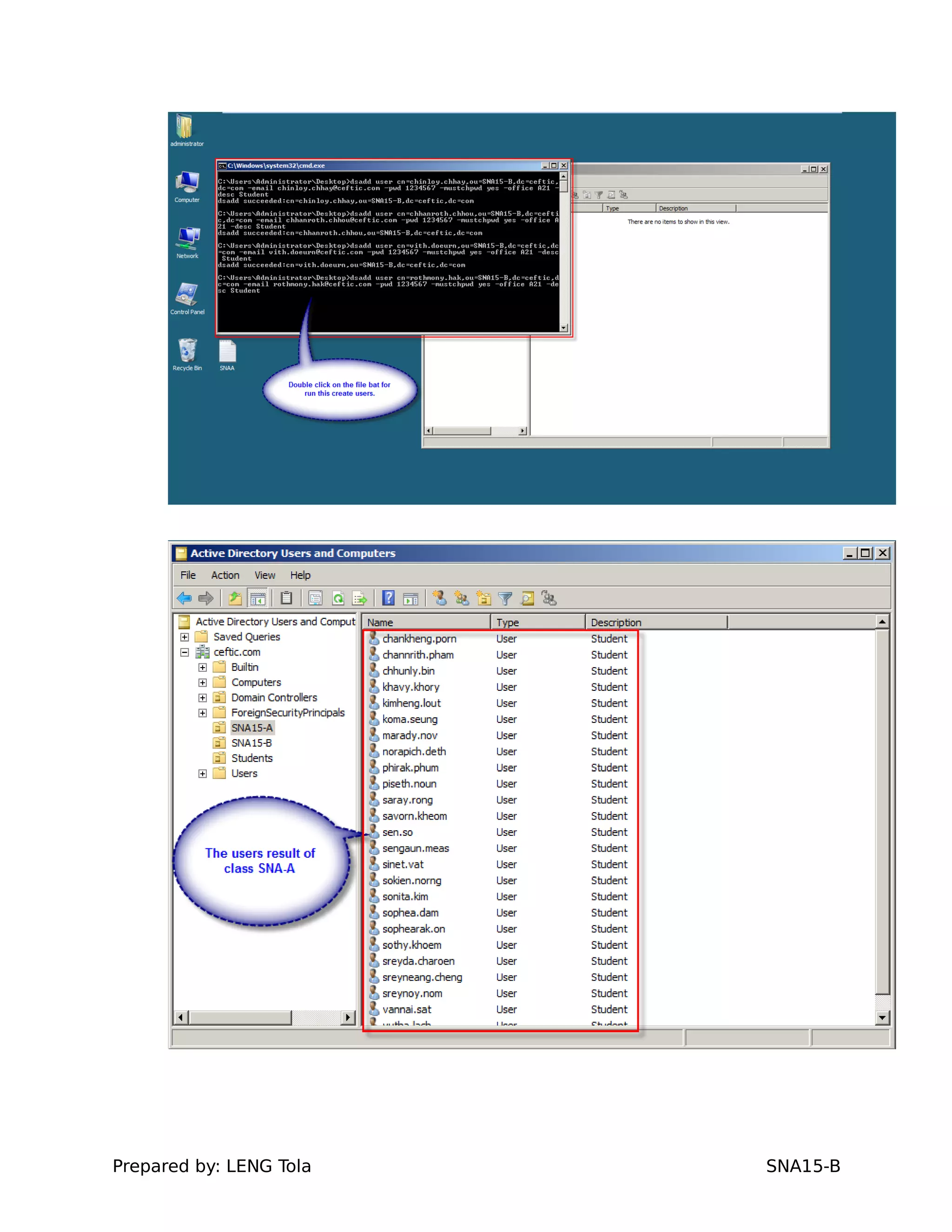
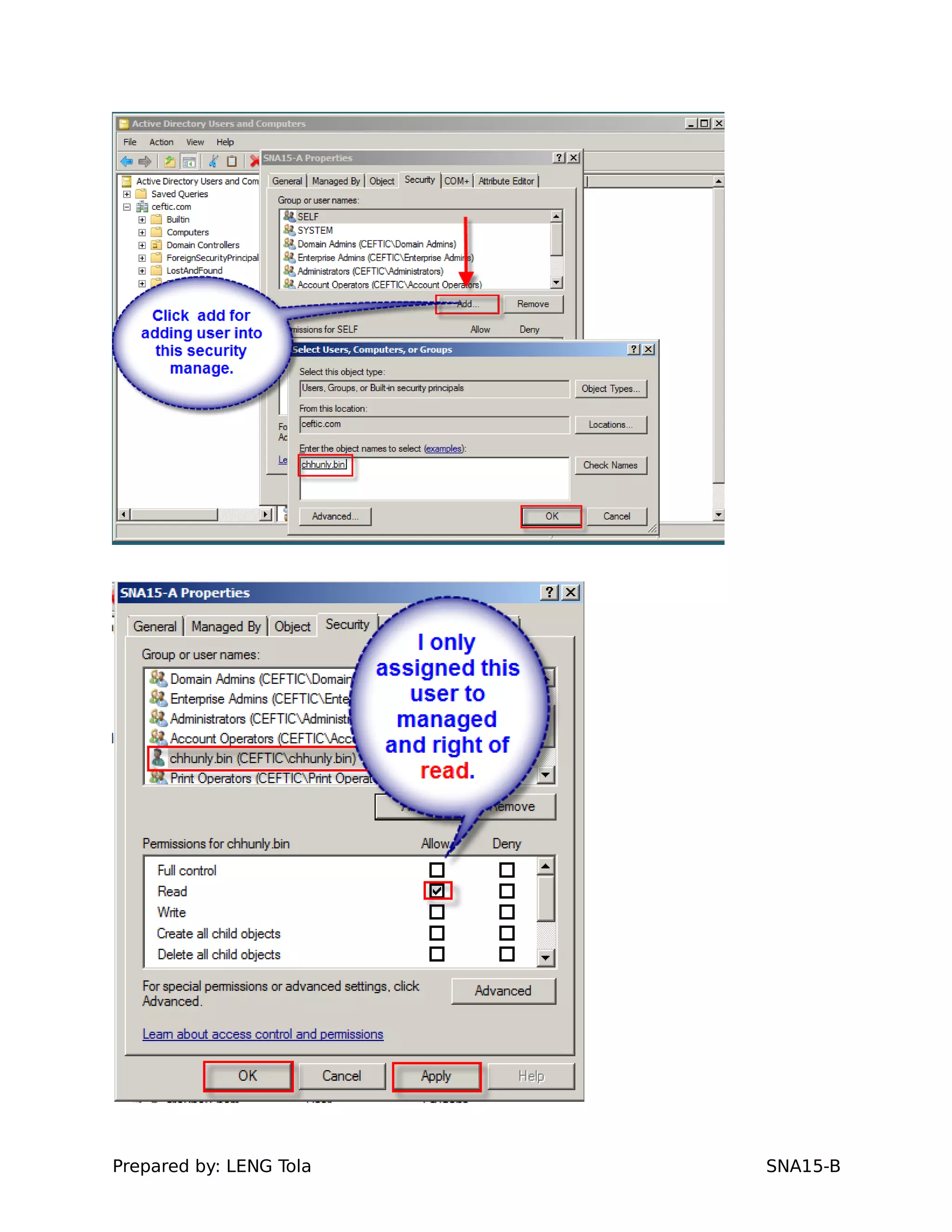
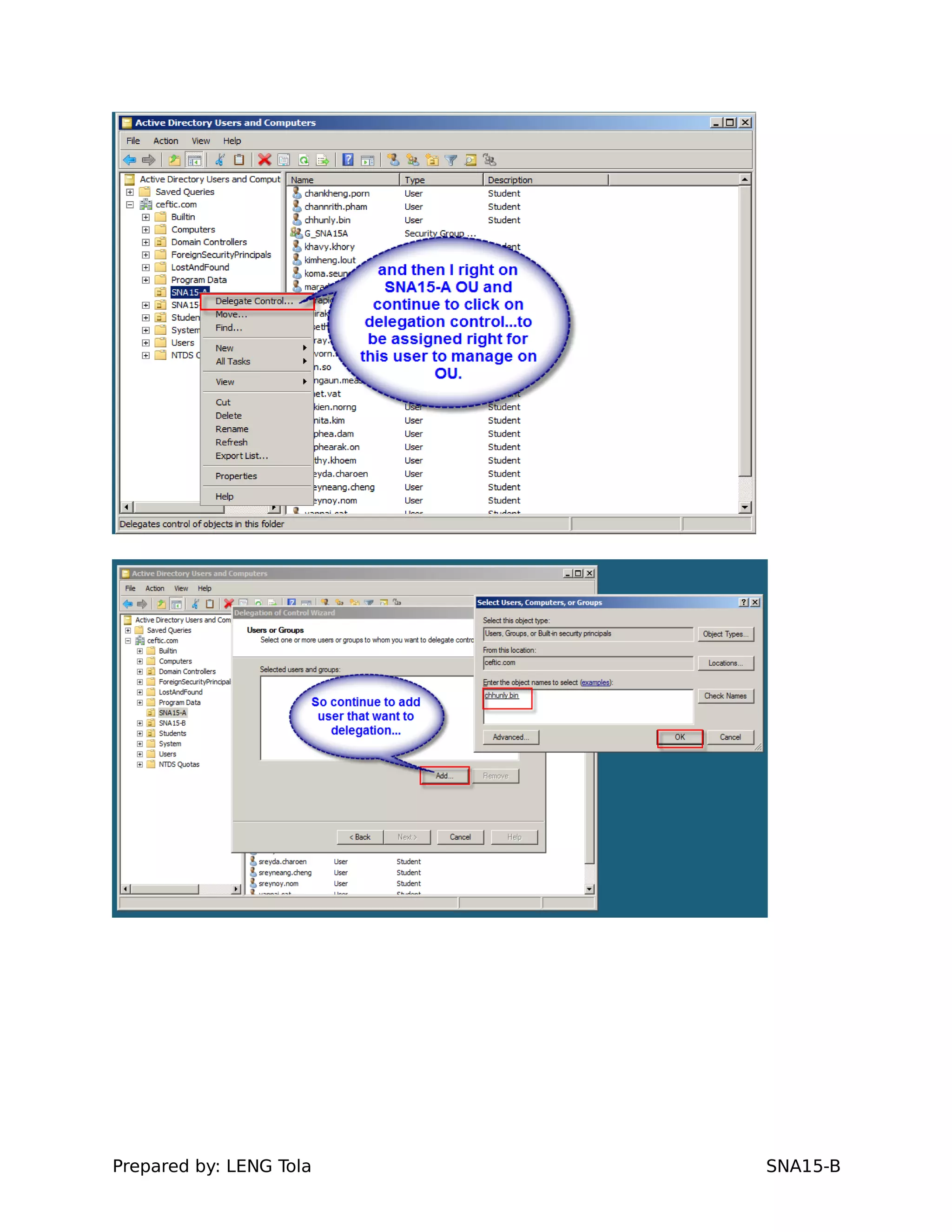
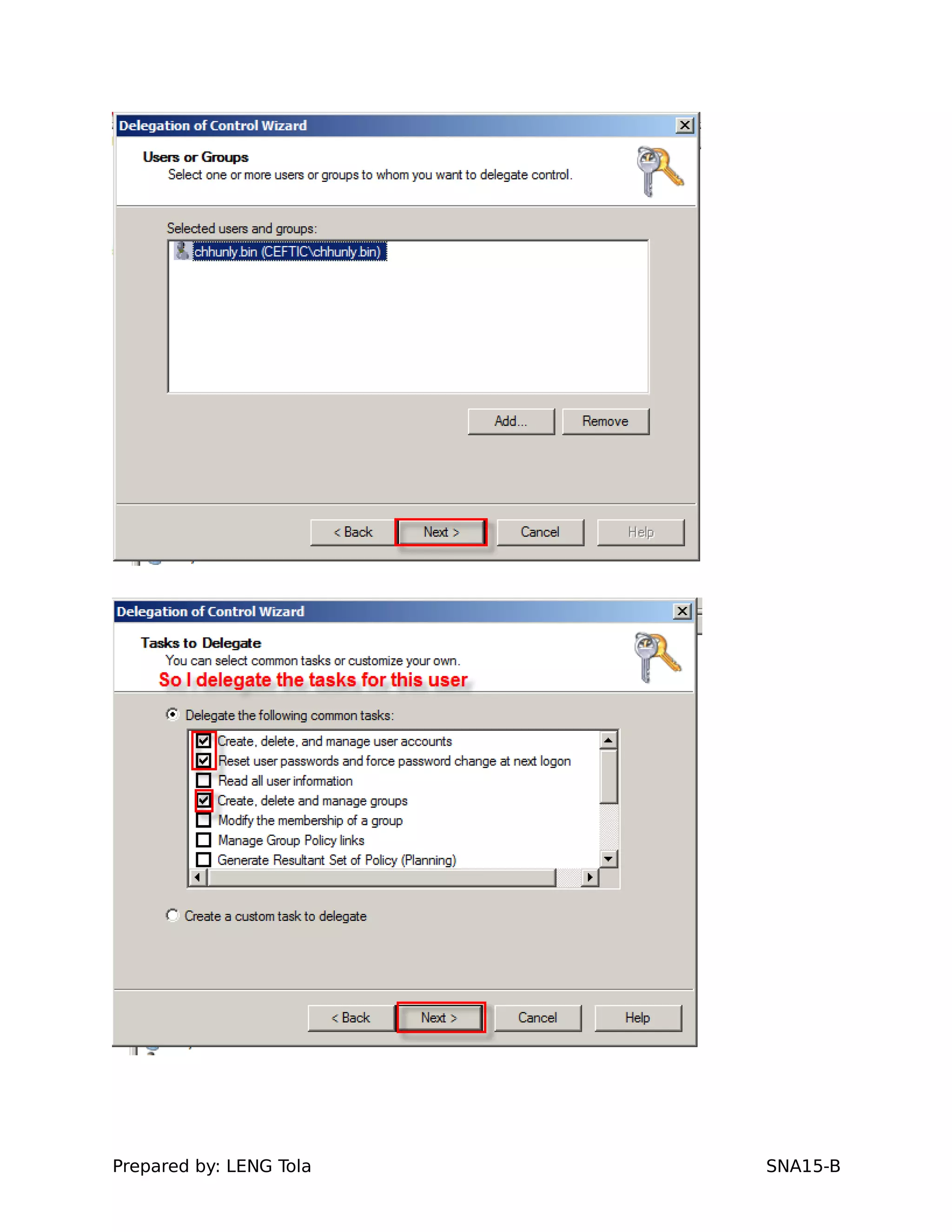
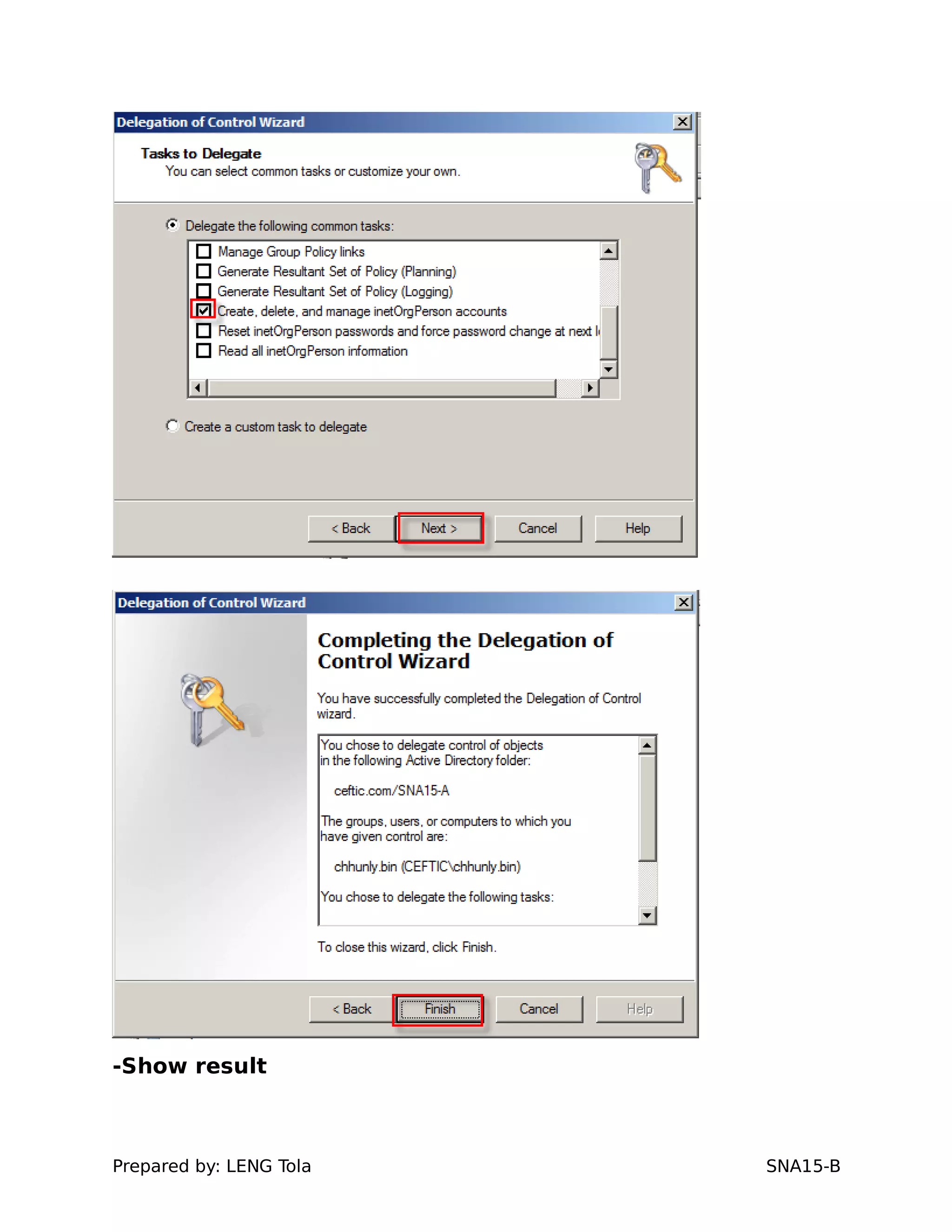
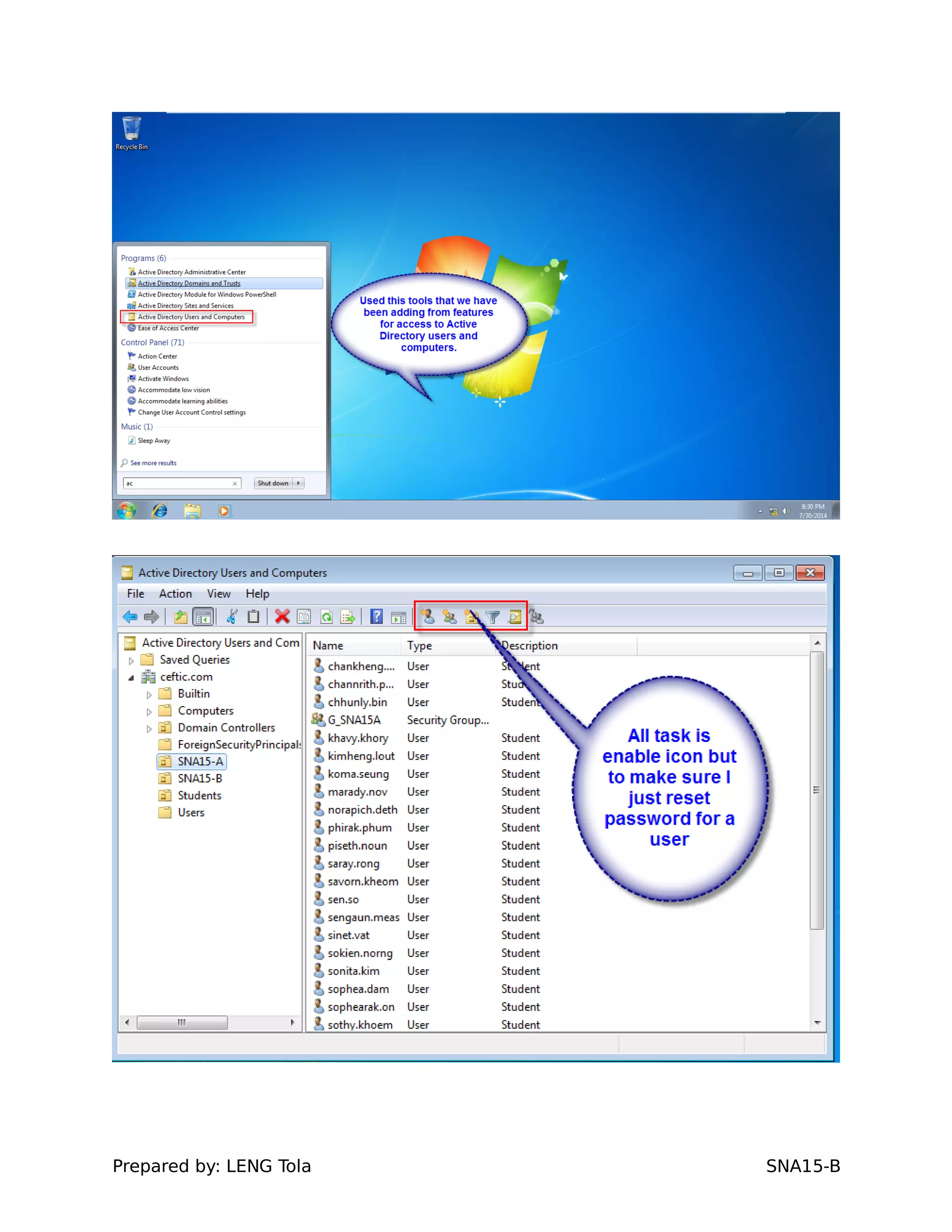
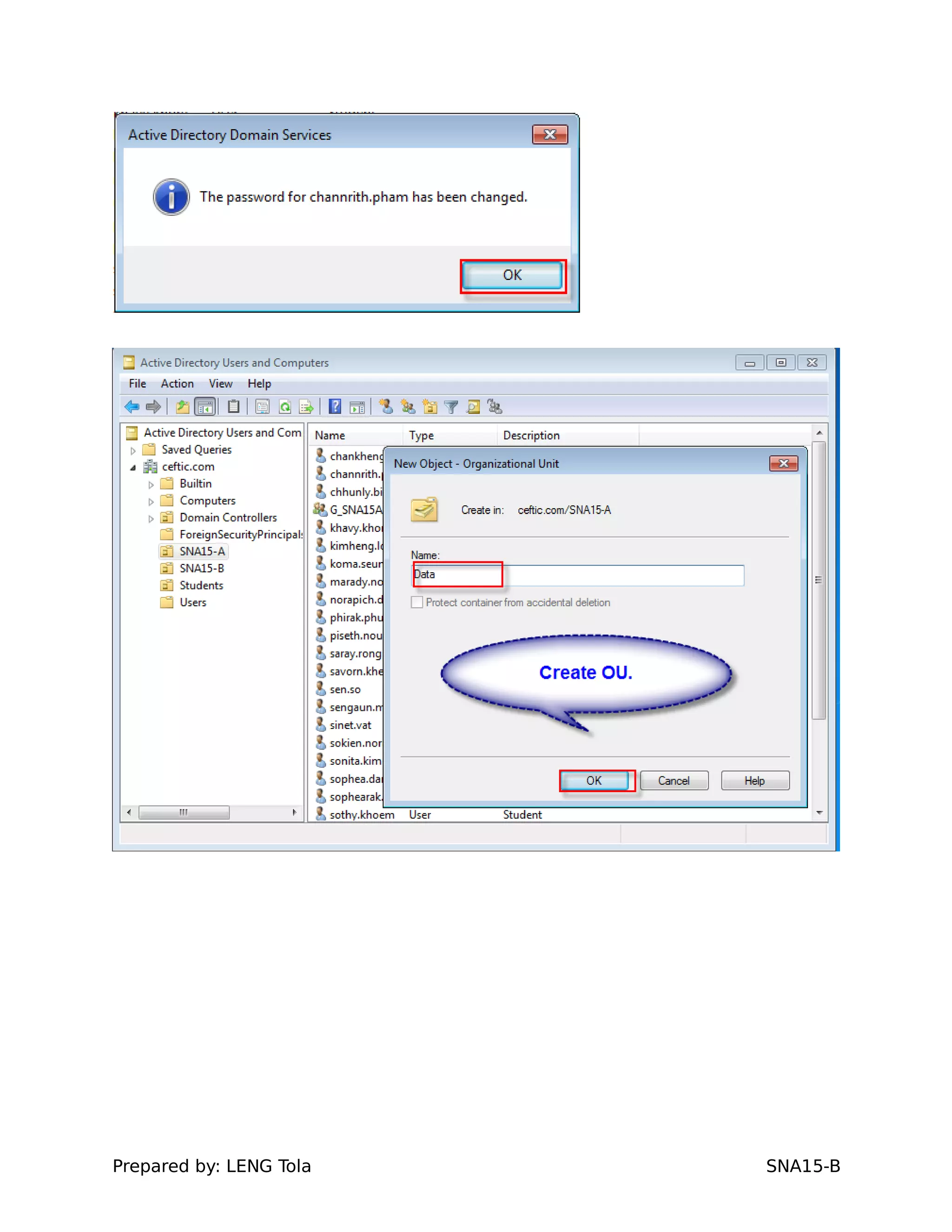
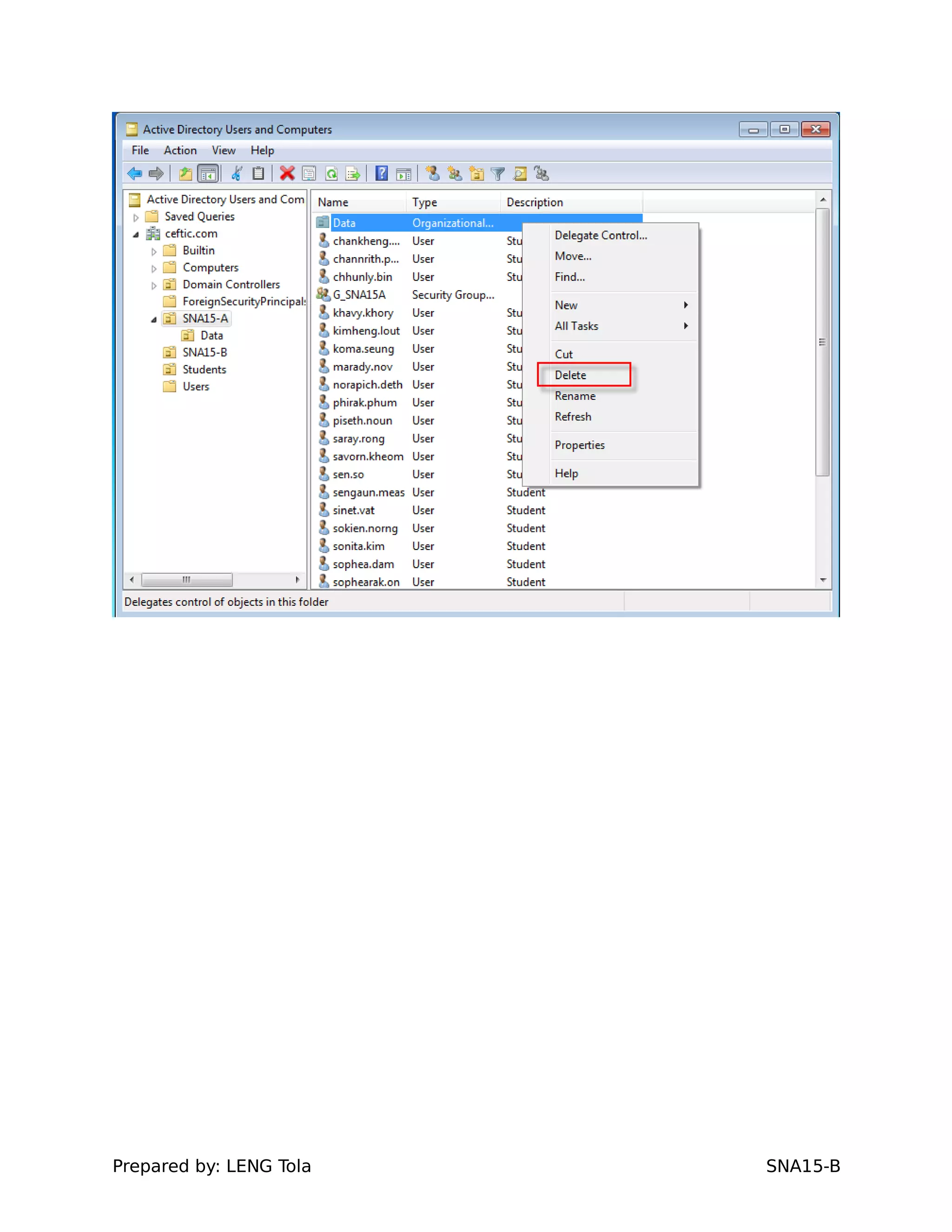
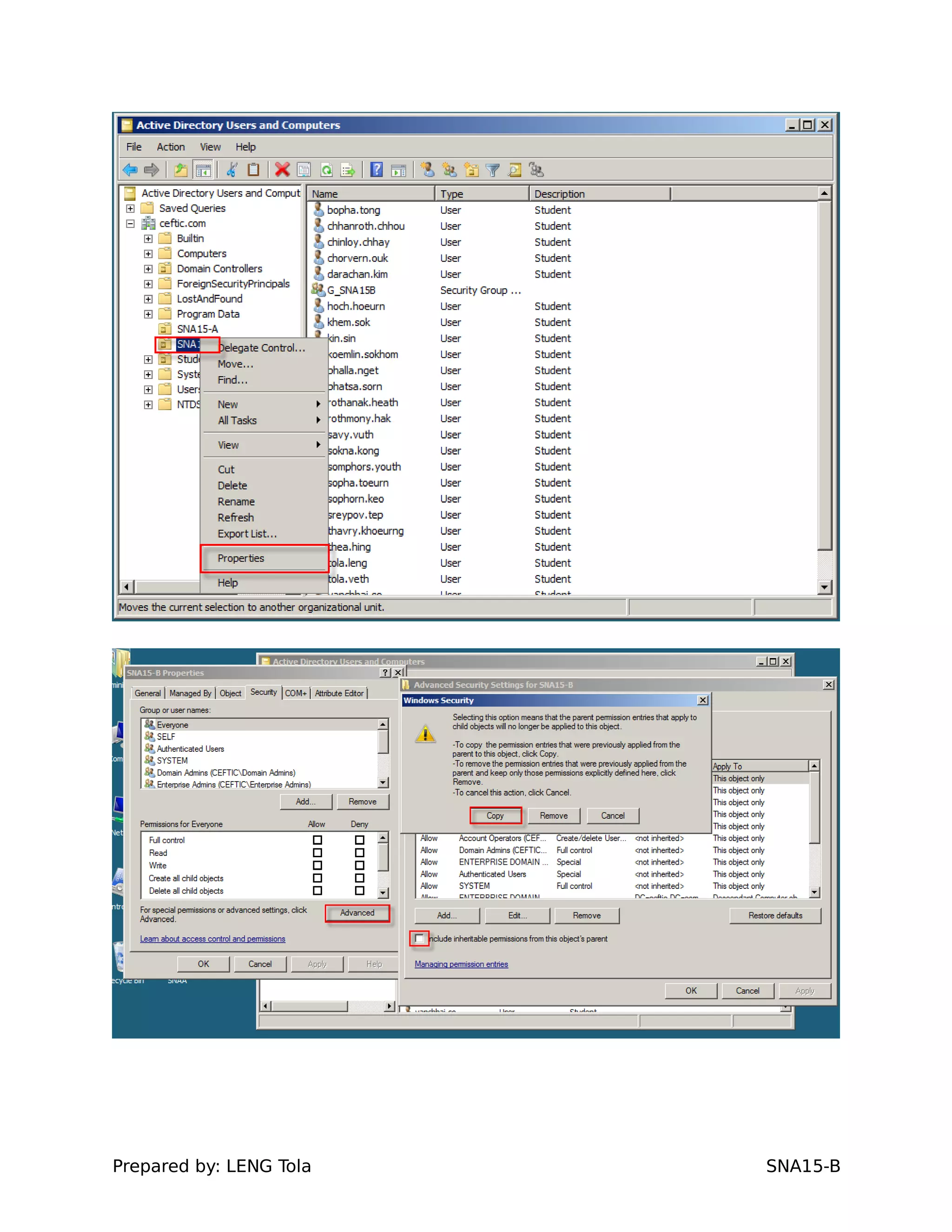
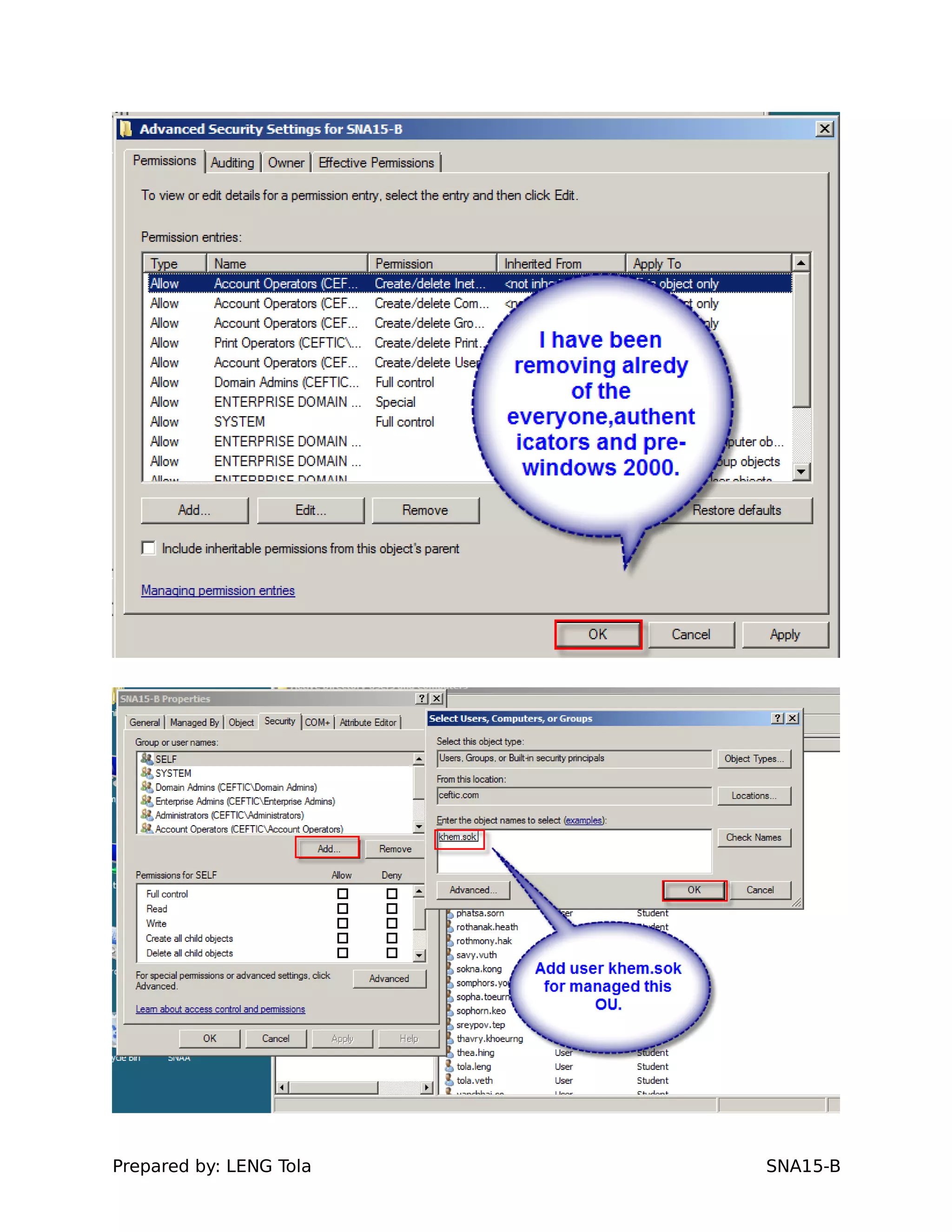
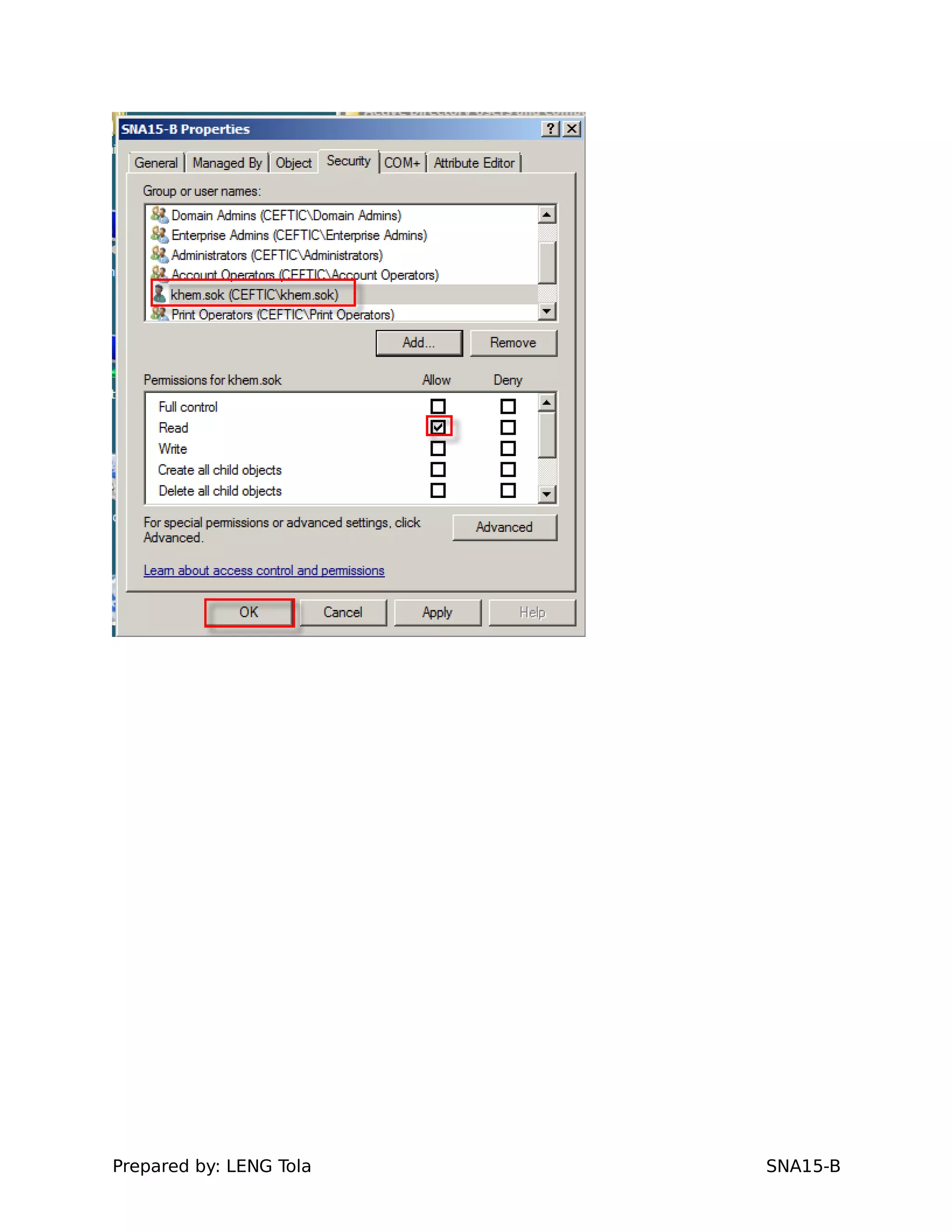
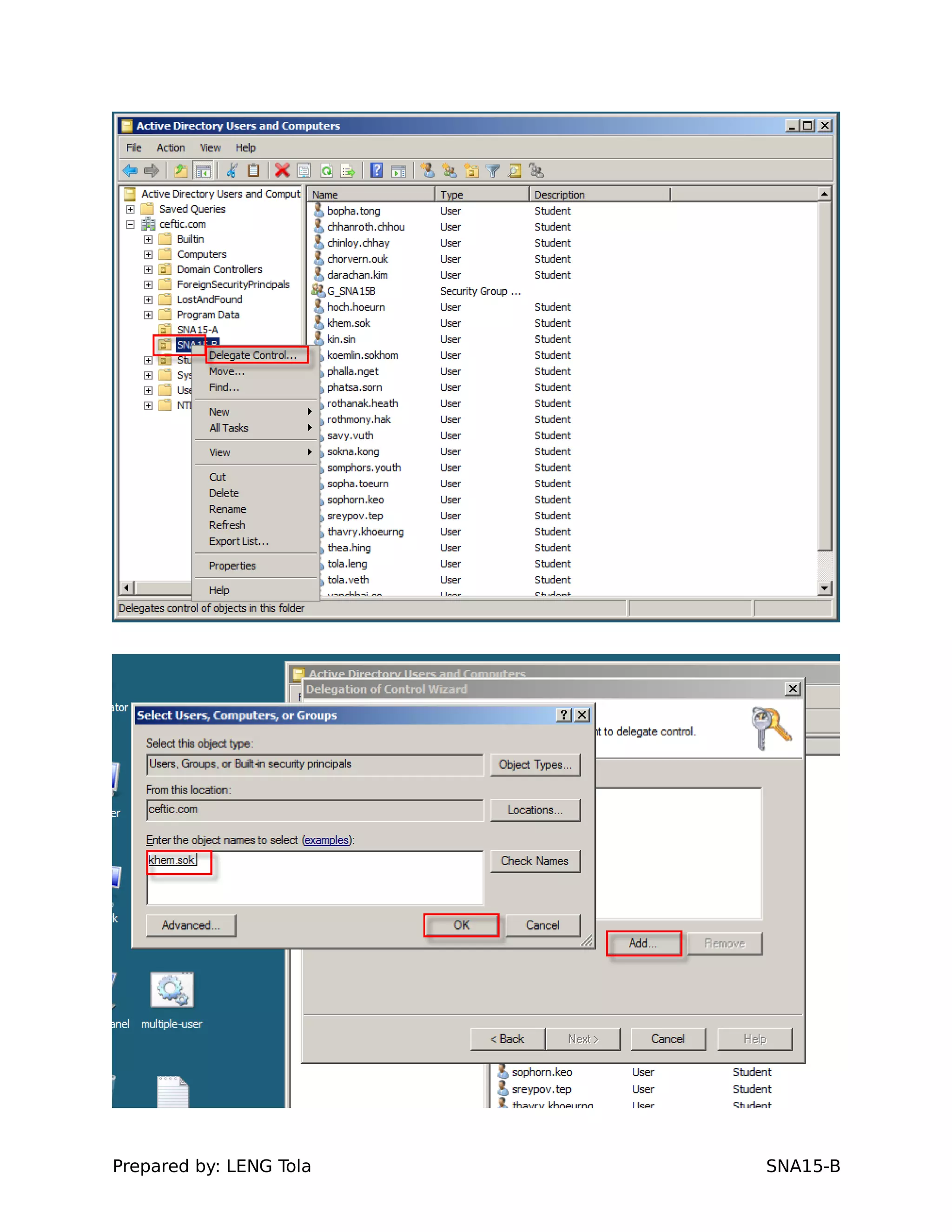
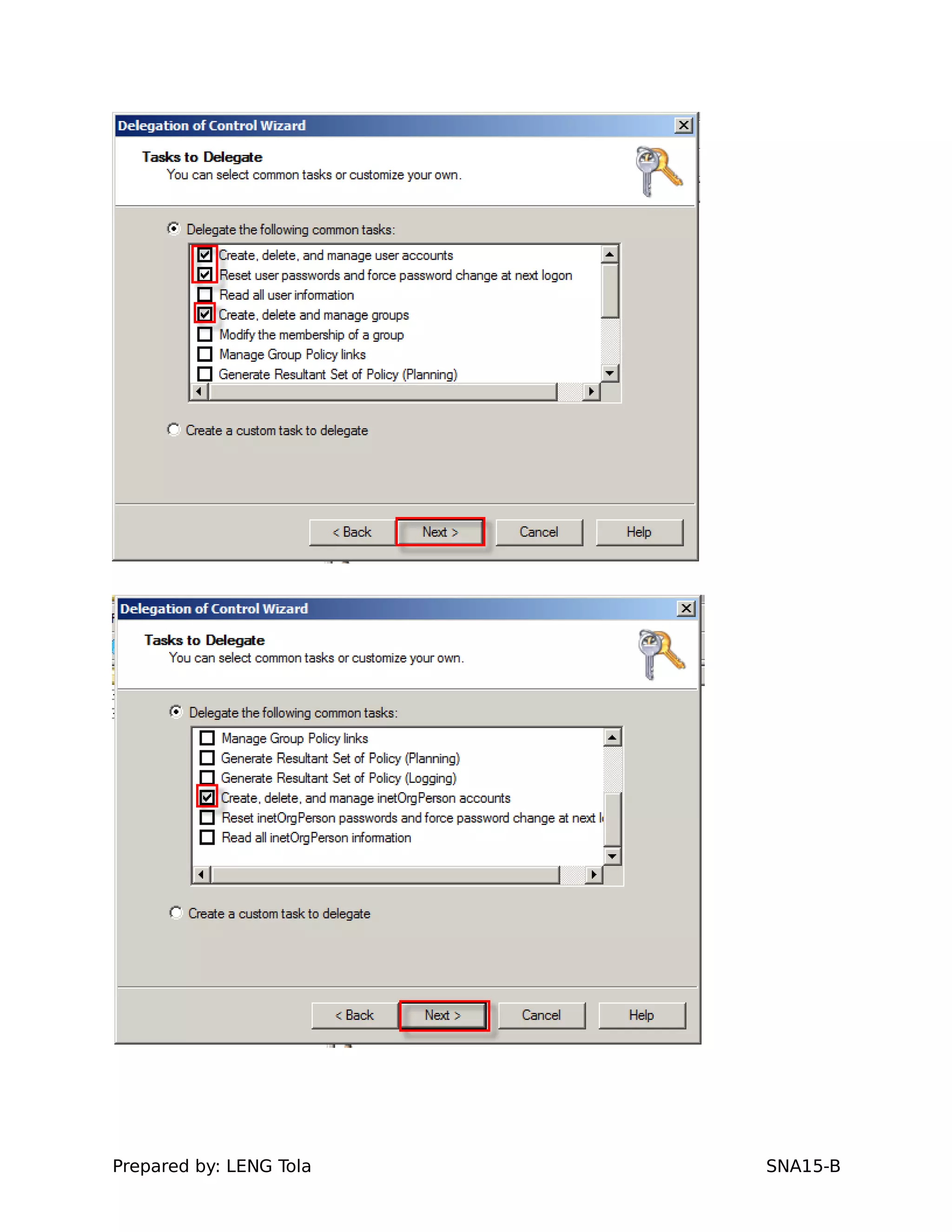
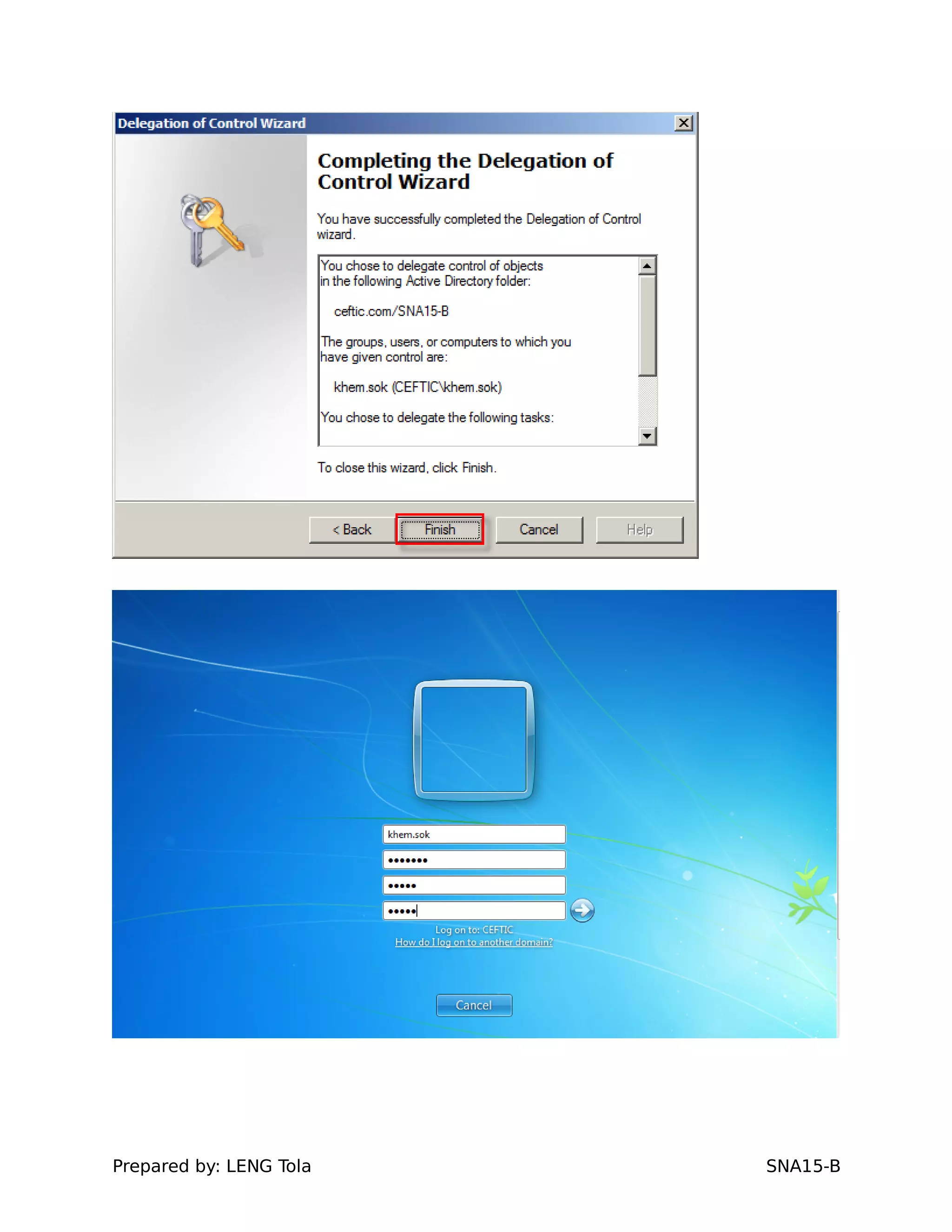
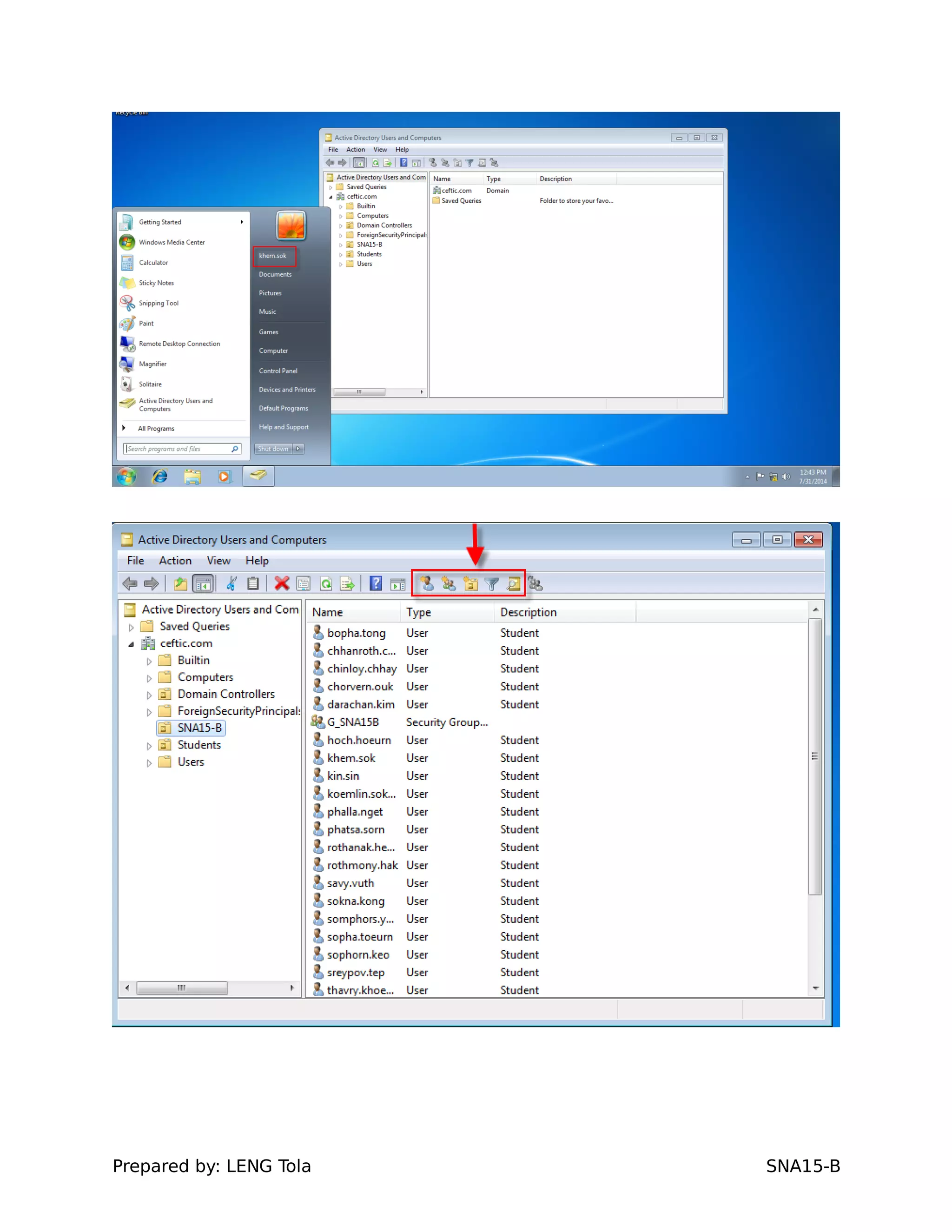
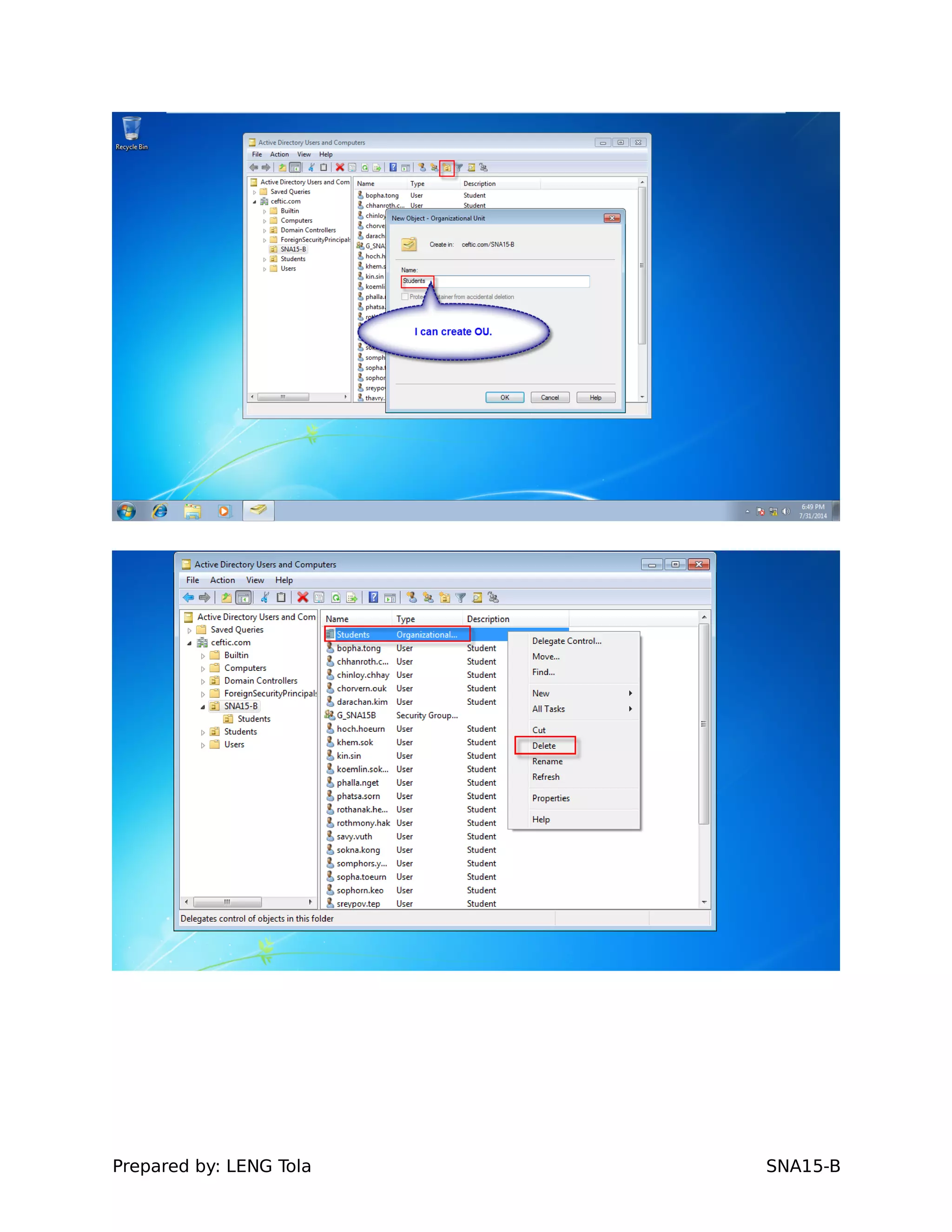
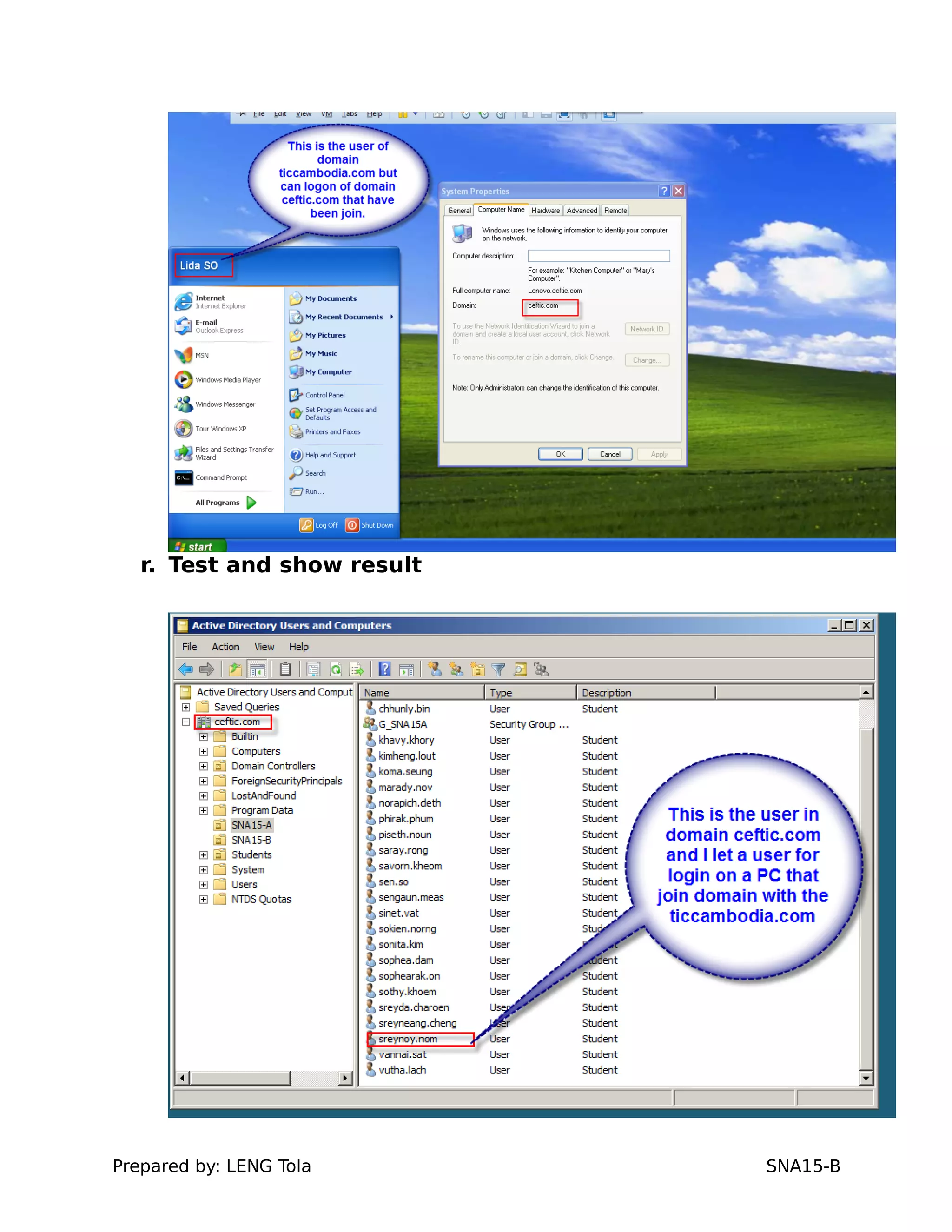
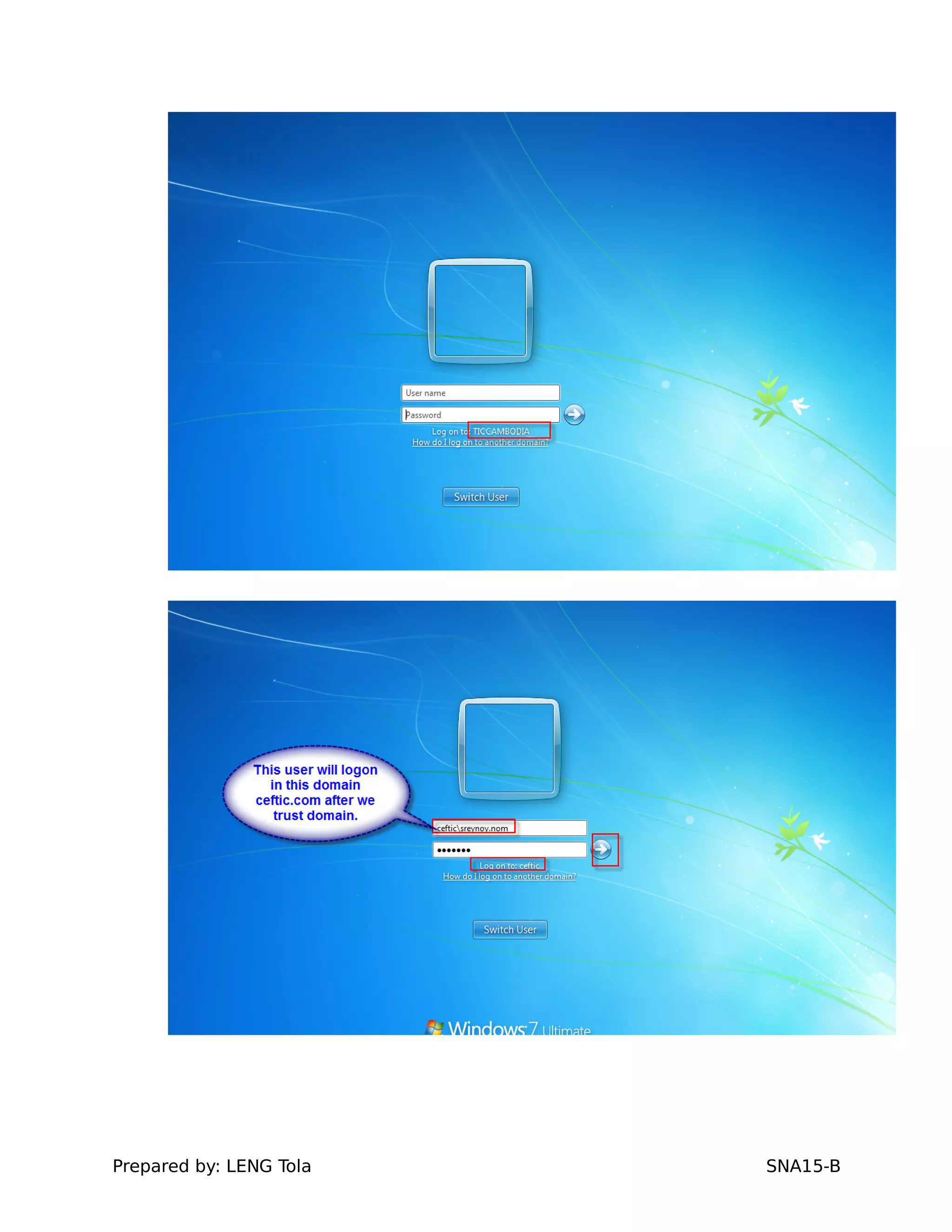
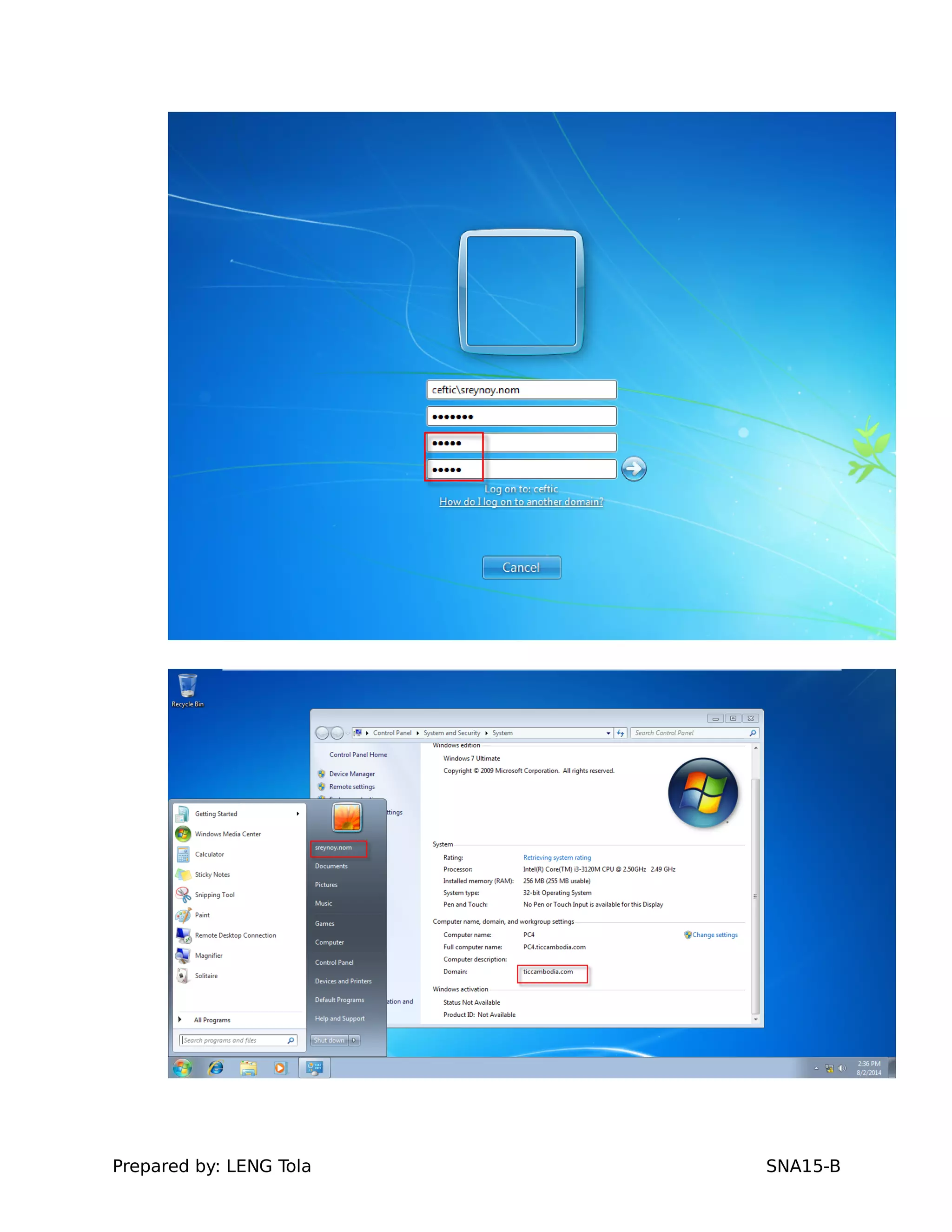
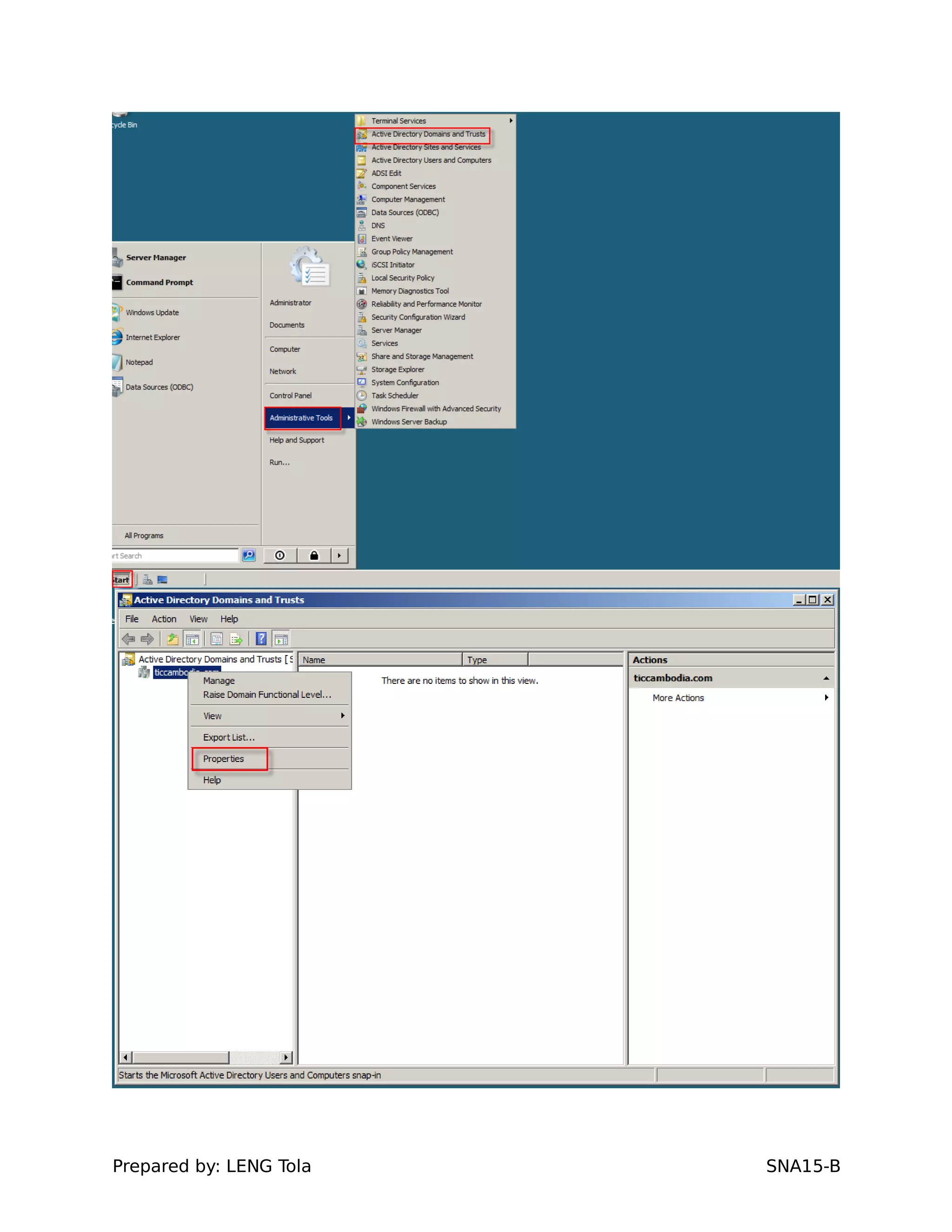
The document outlines steps for configuring an Active Directory environment, including:
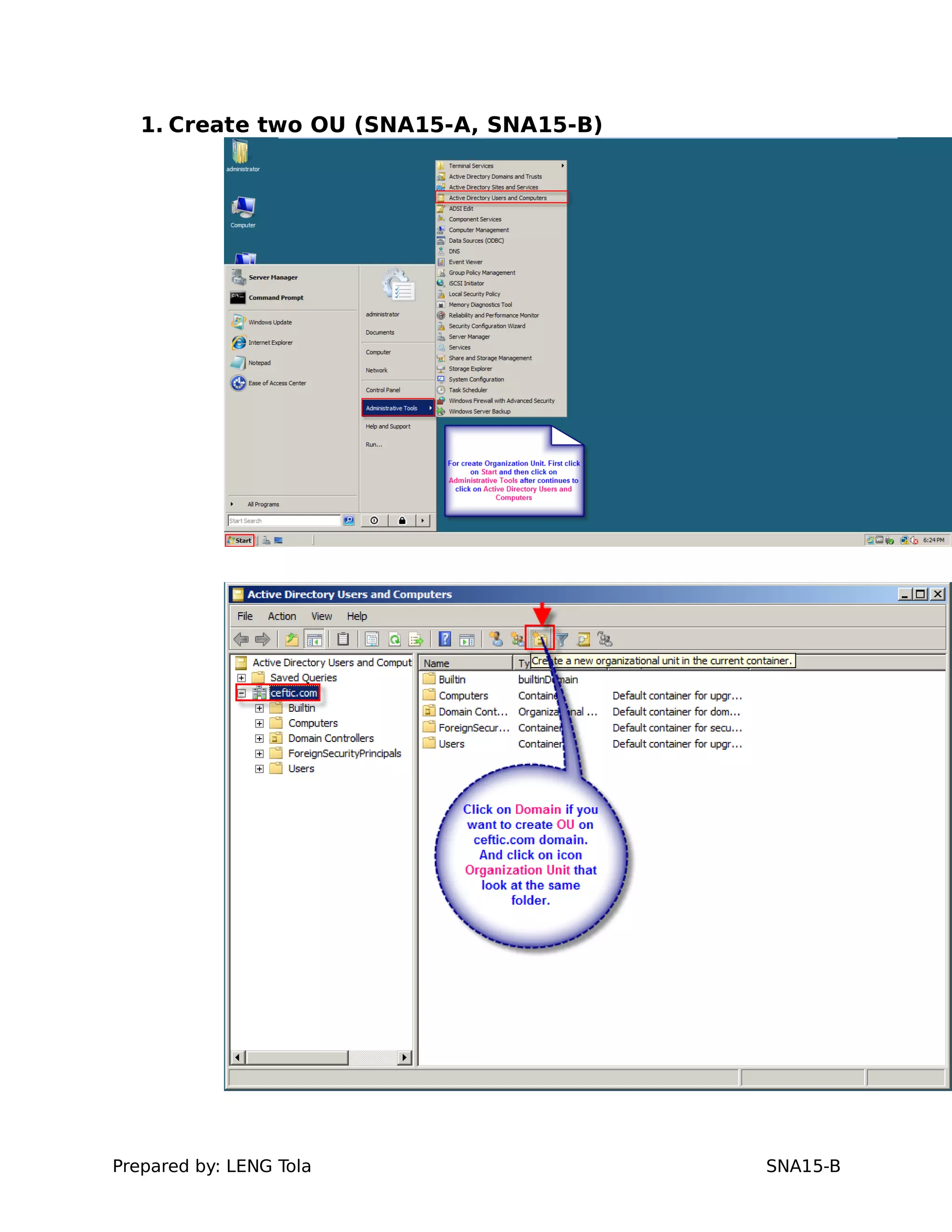
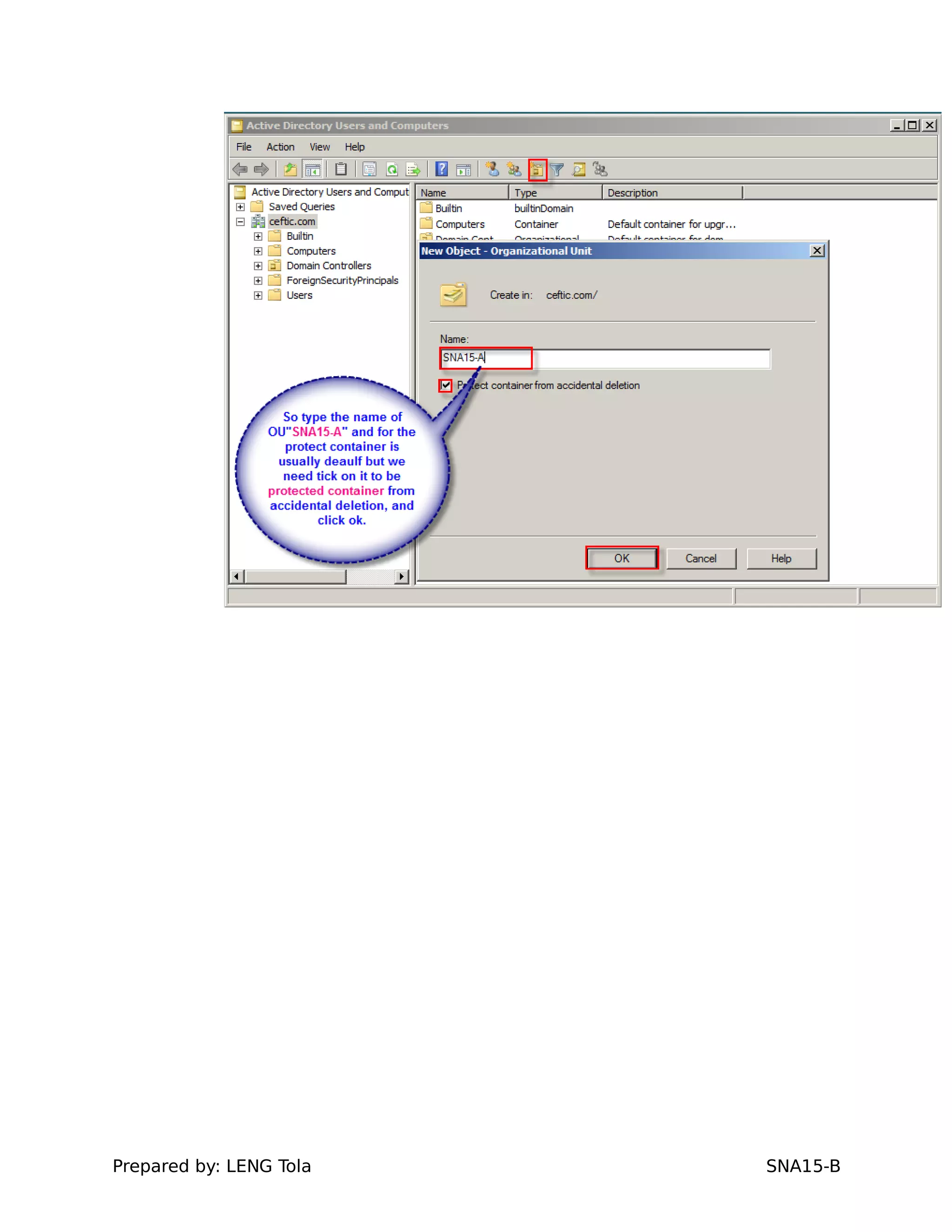
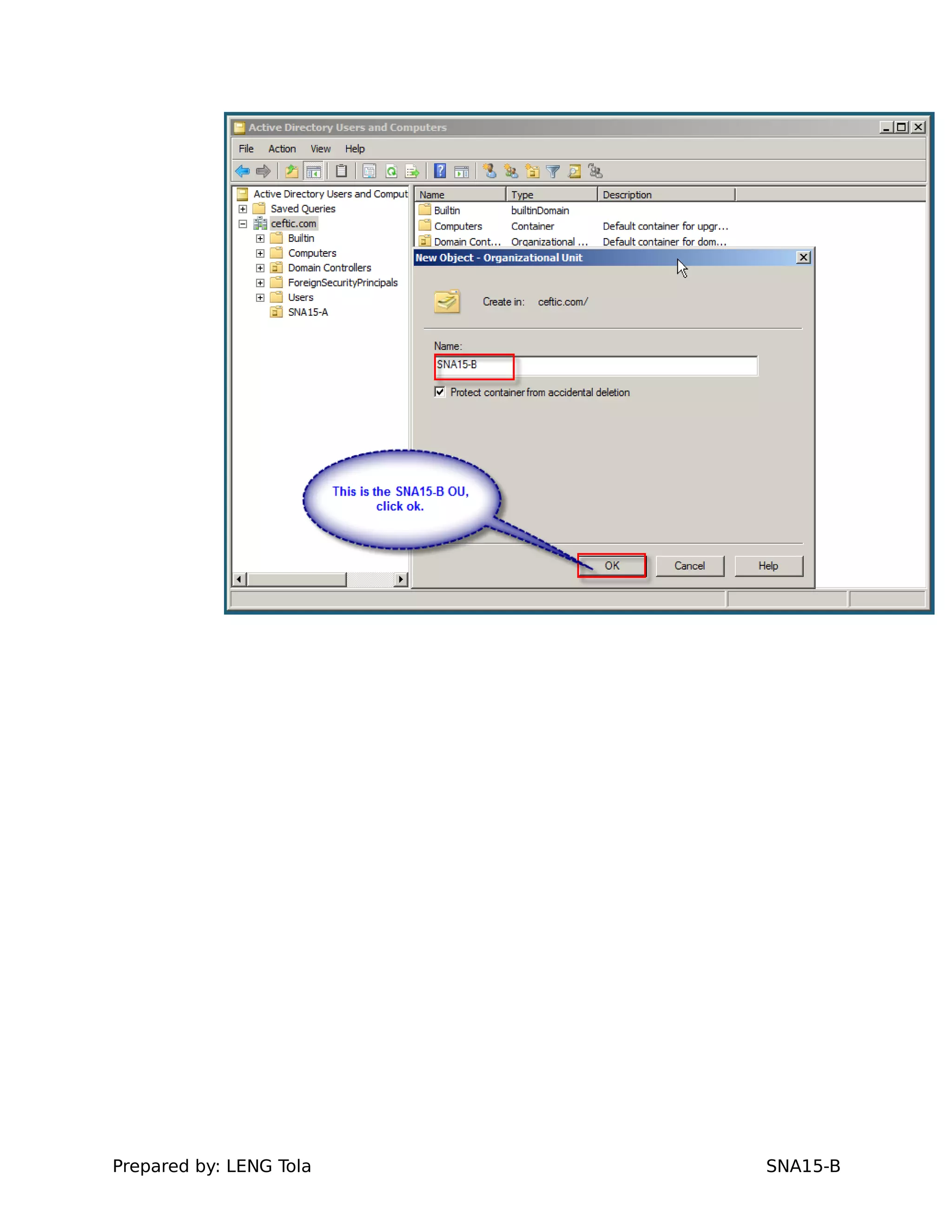
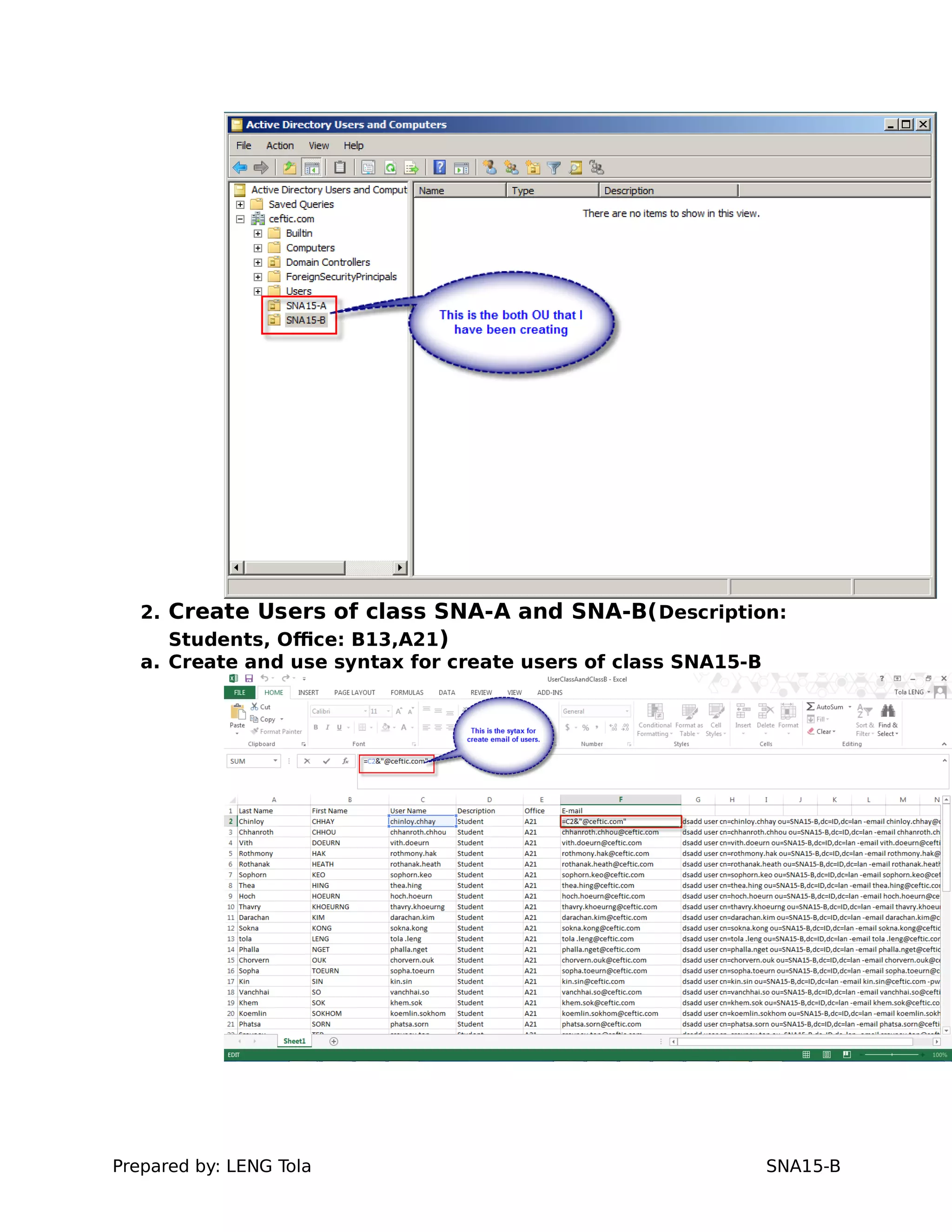
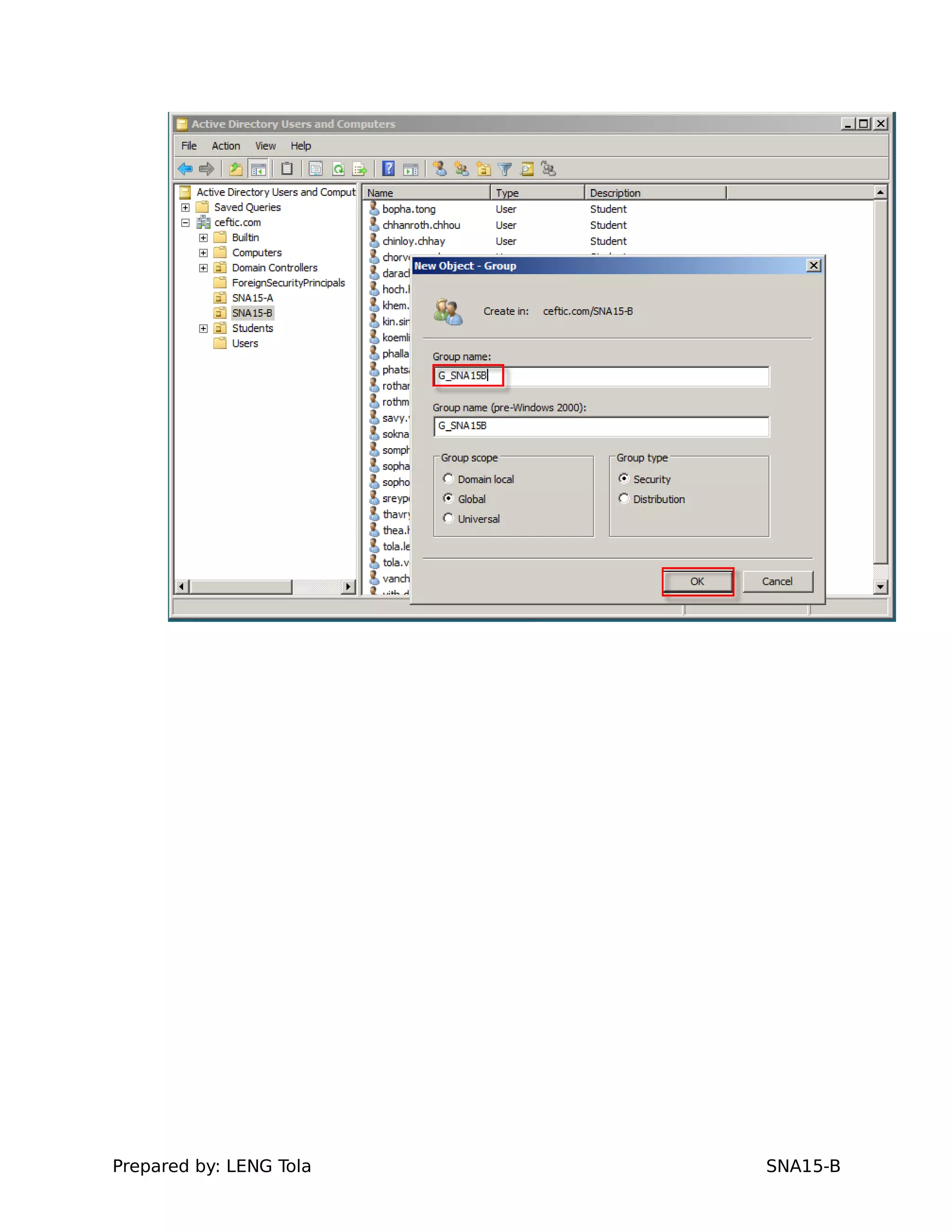
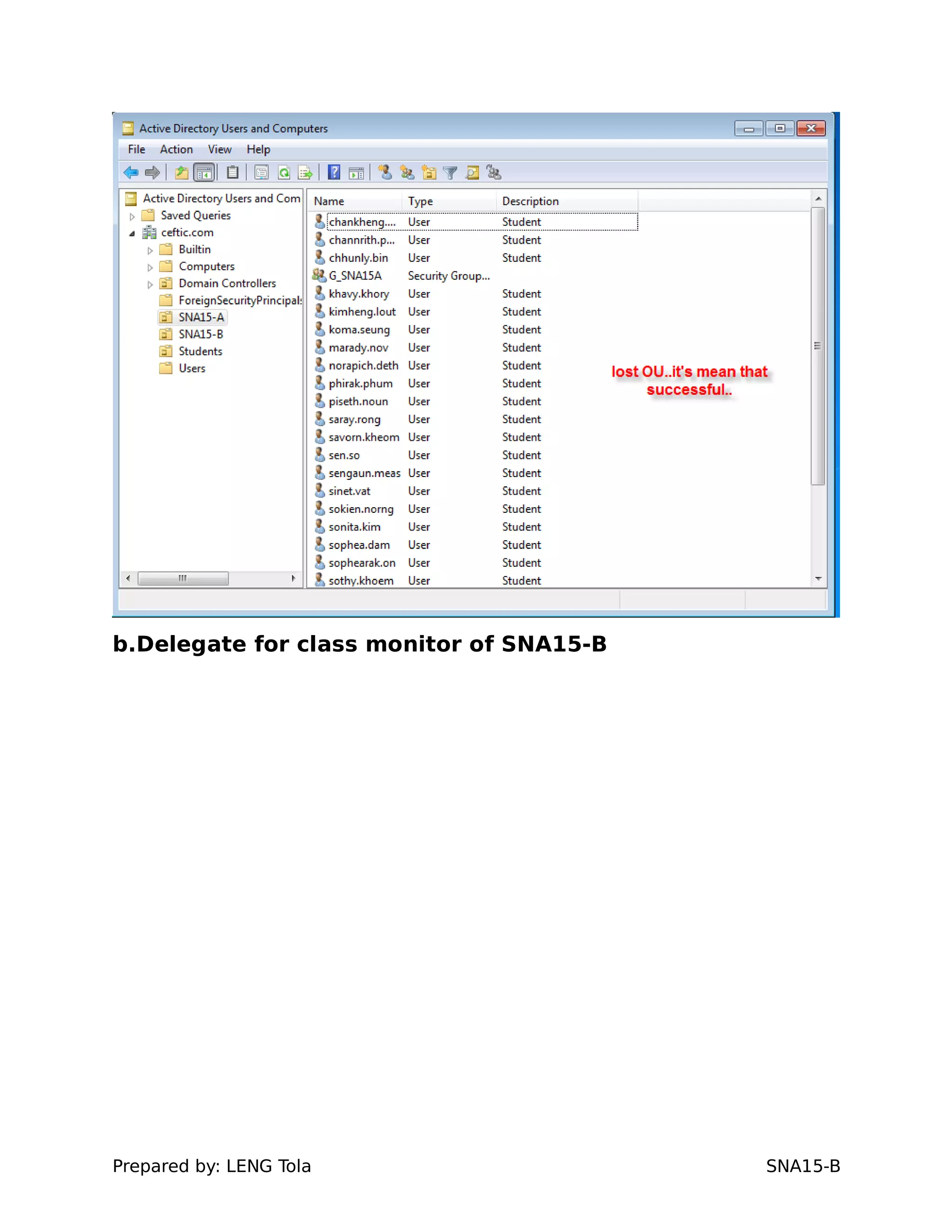
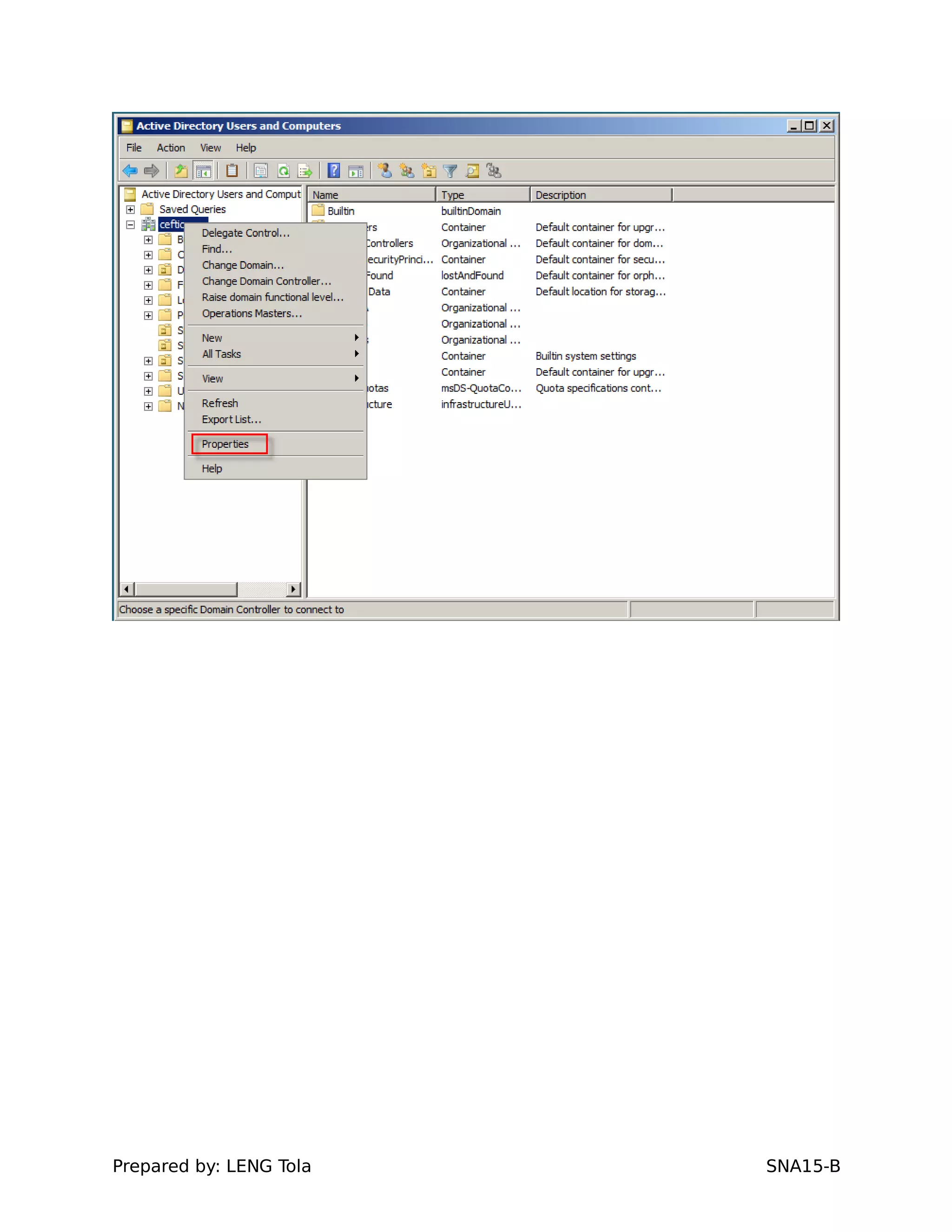
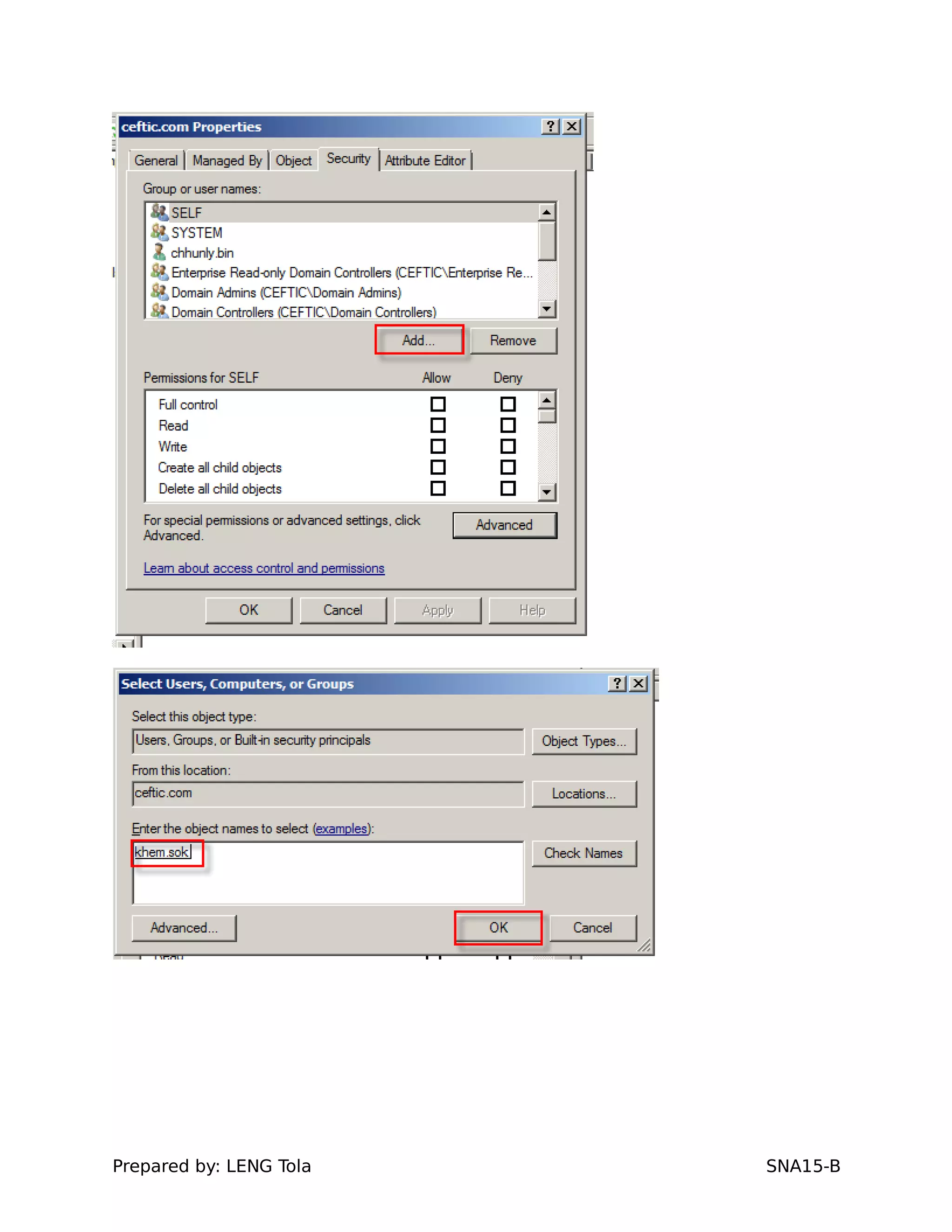
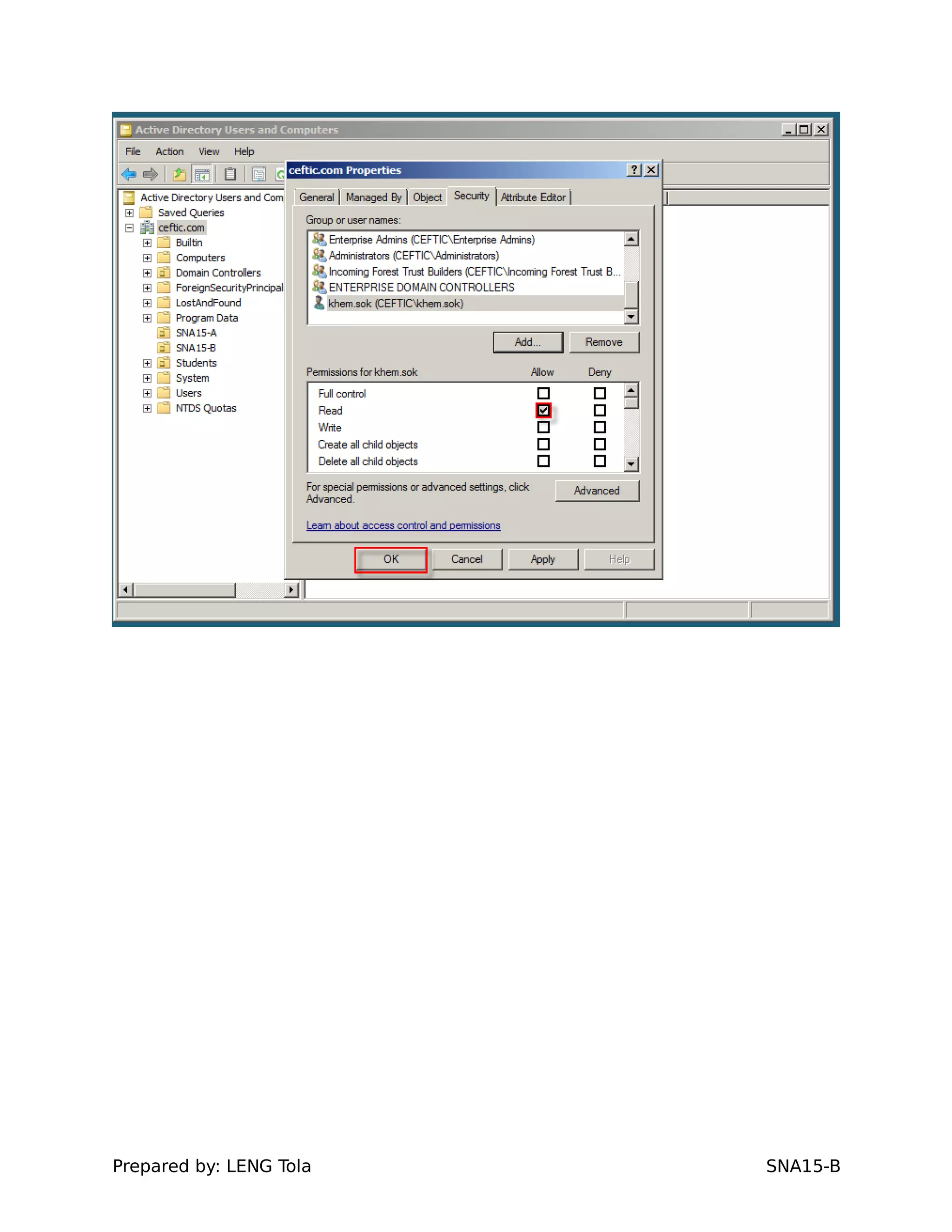
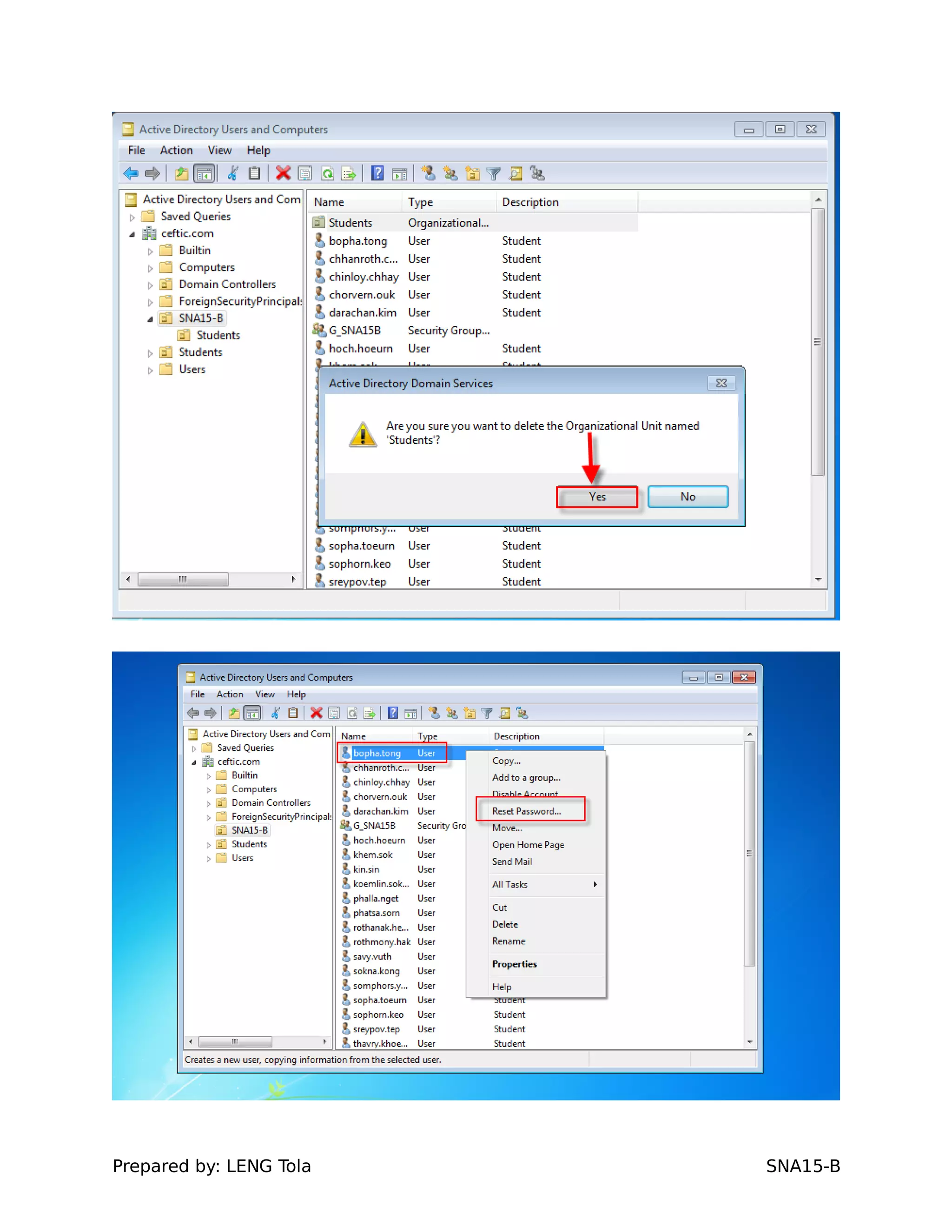
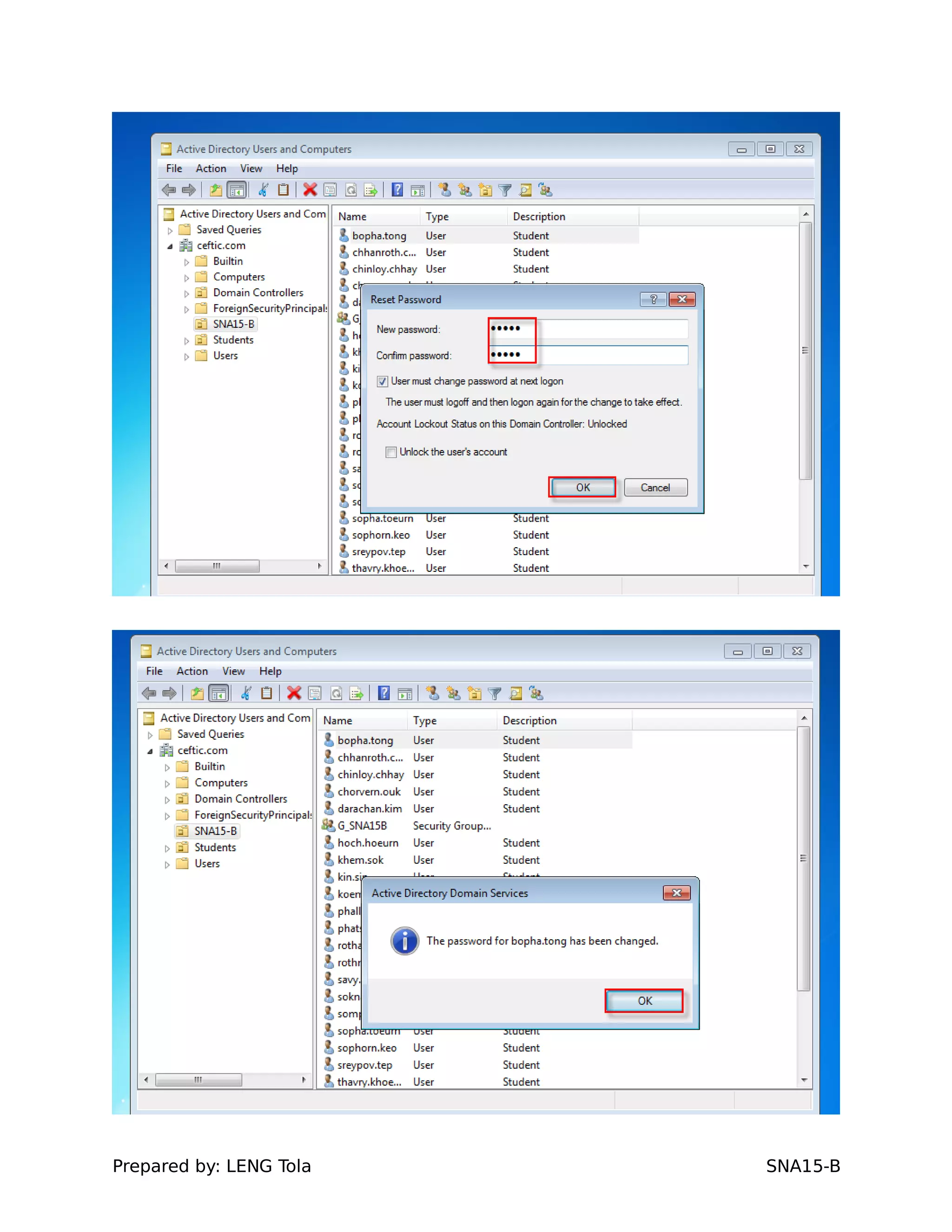
1. Creating OUs and user accounts
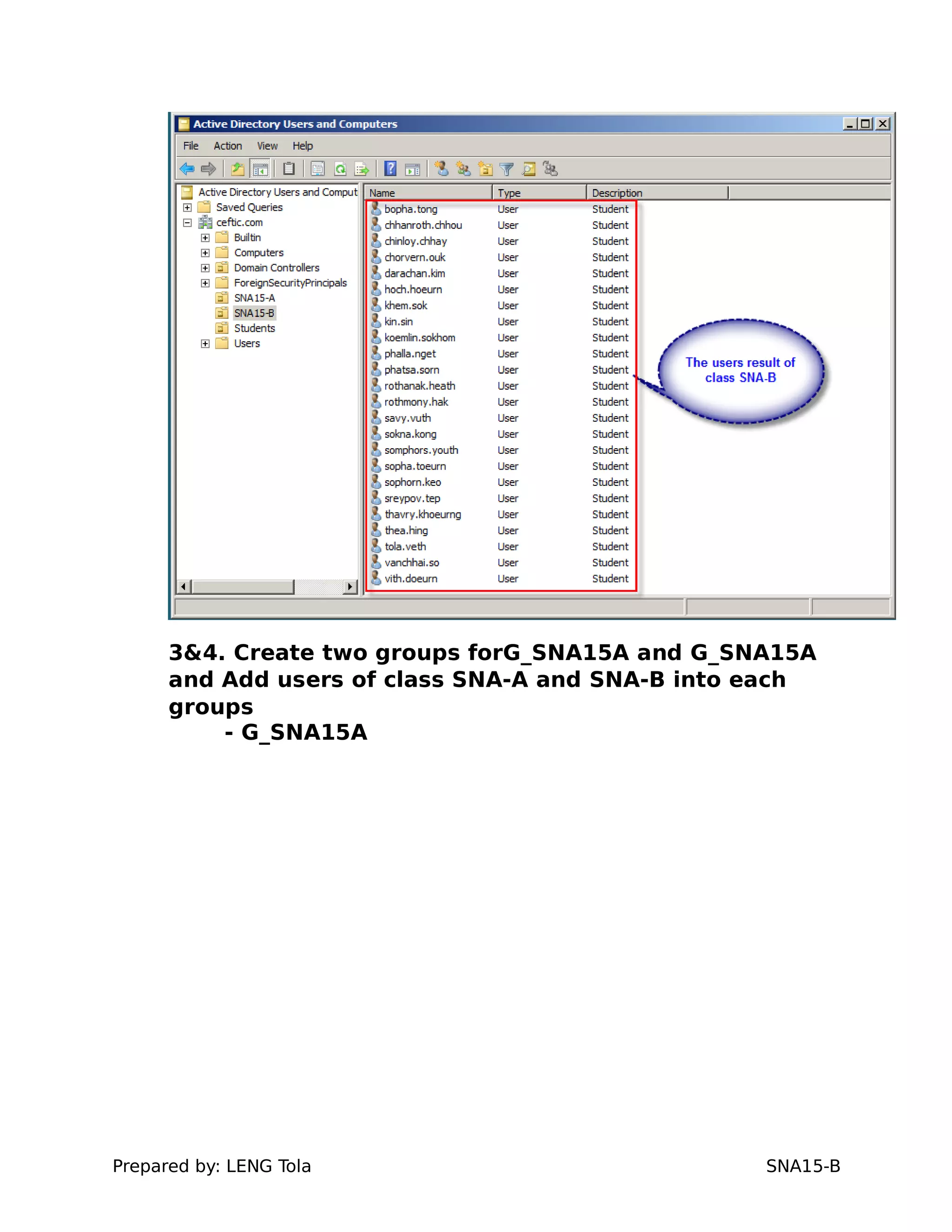
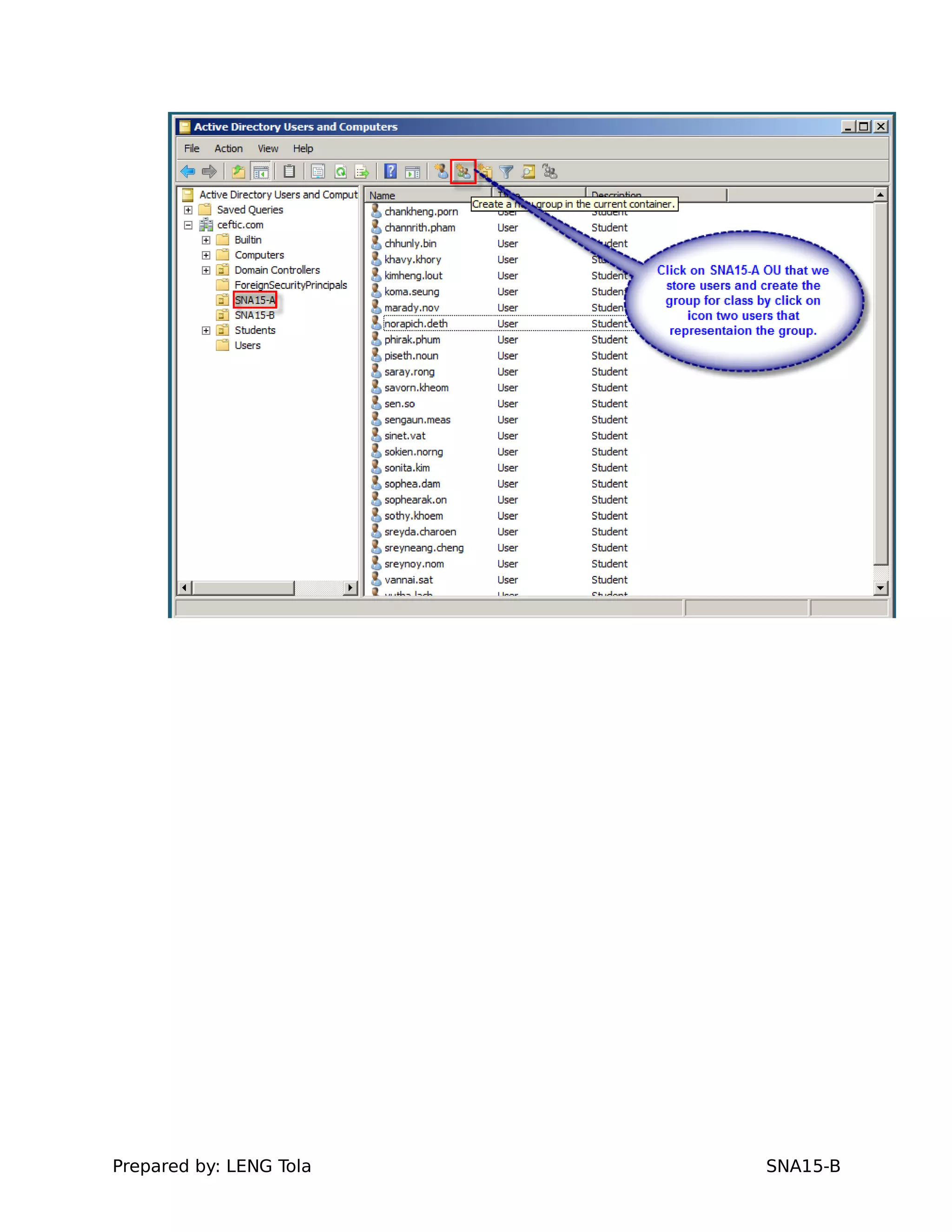
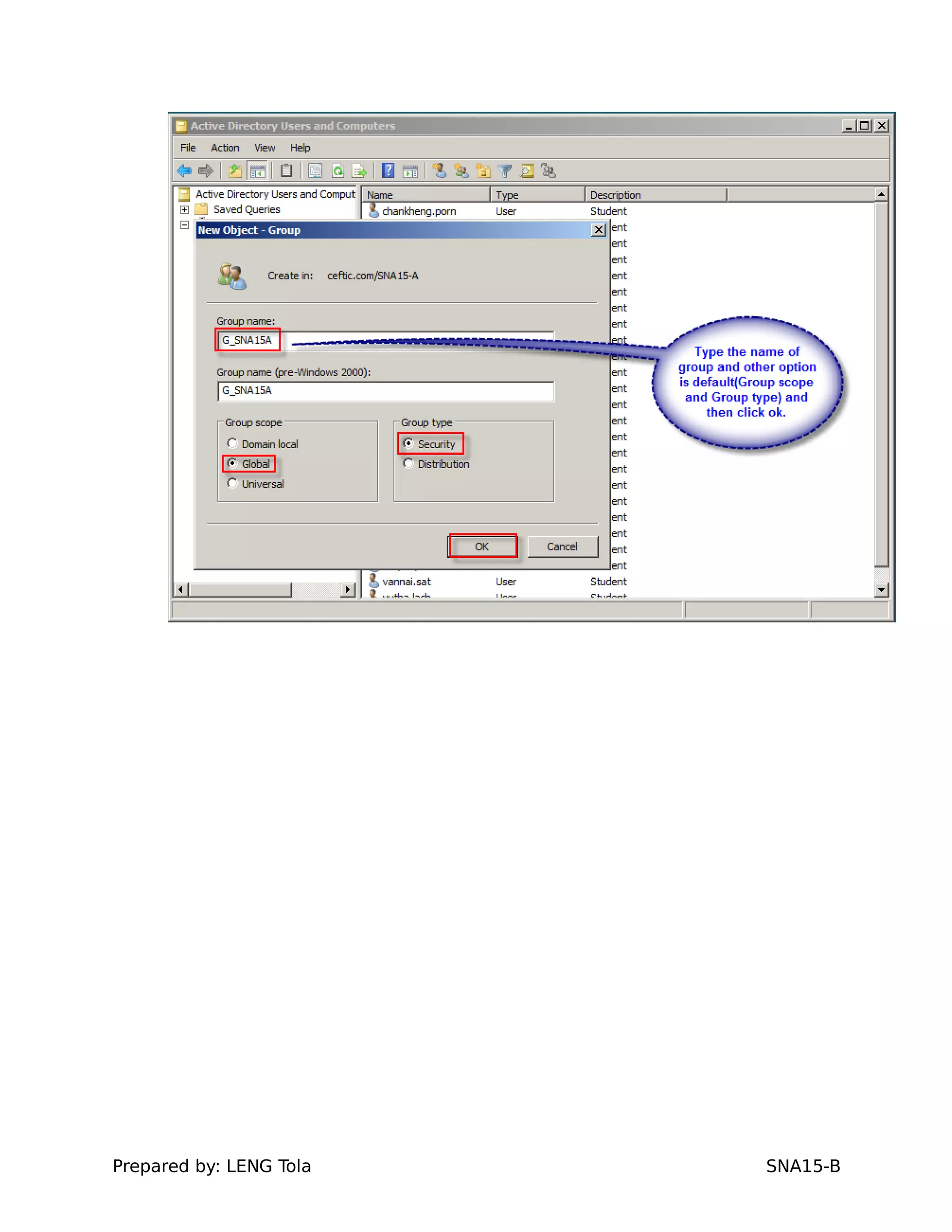
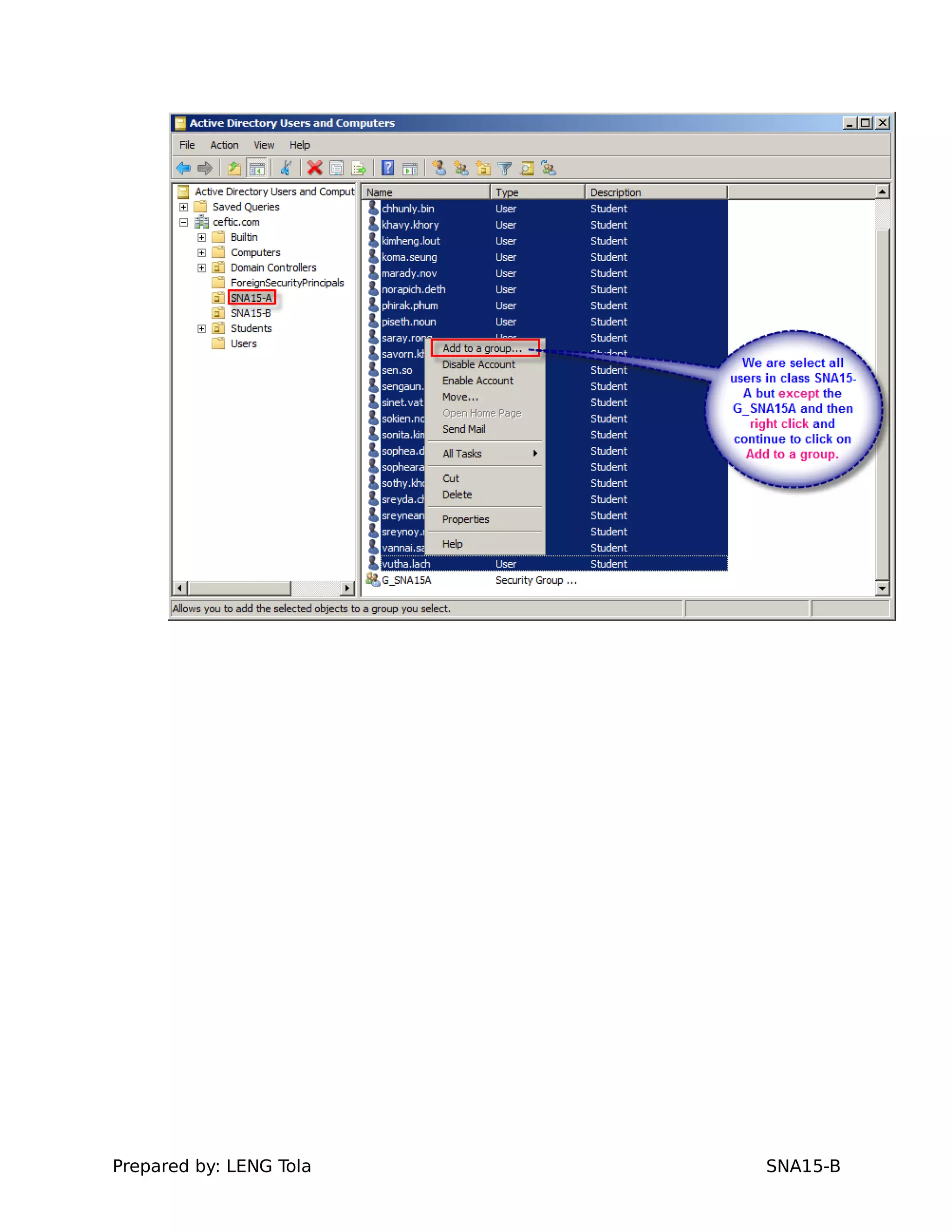
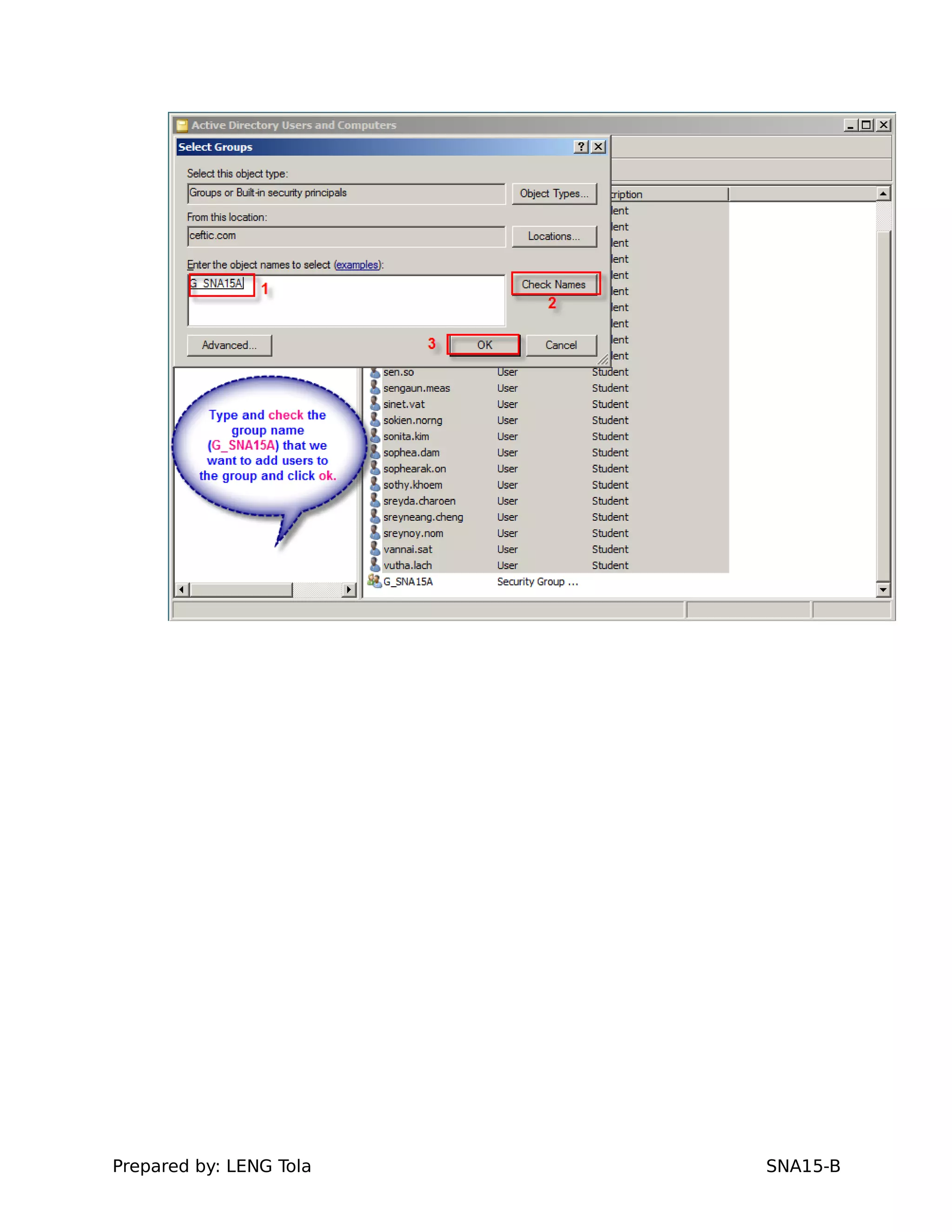
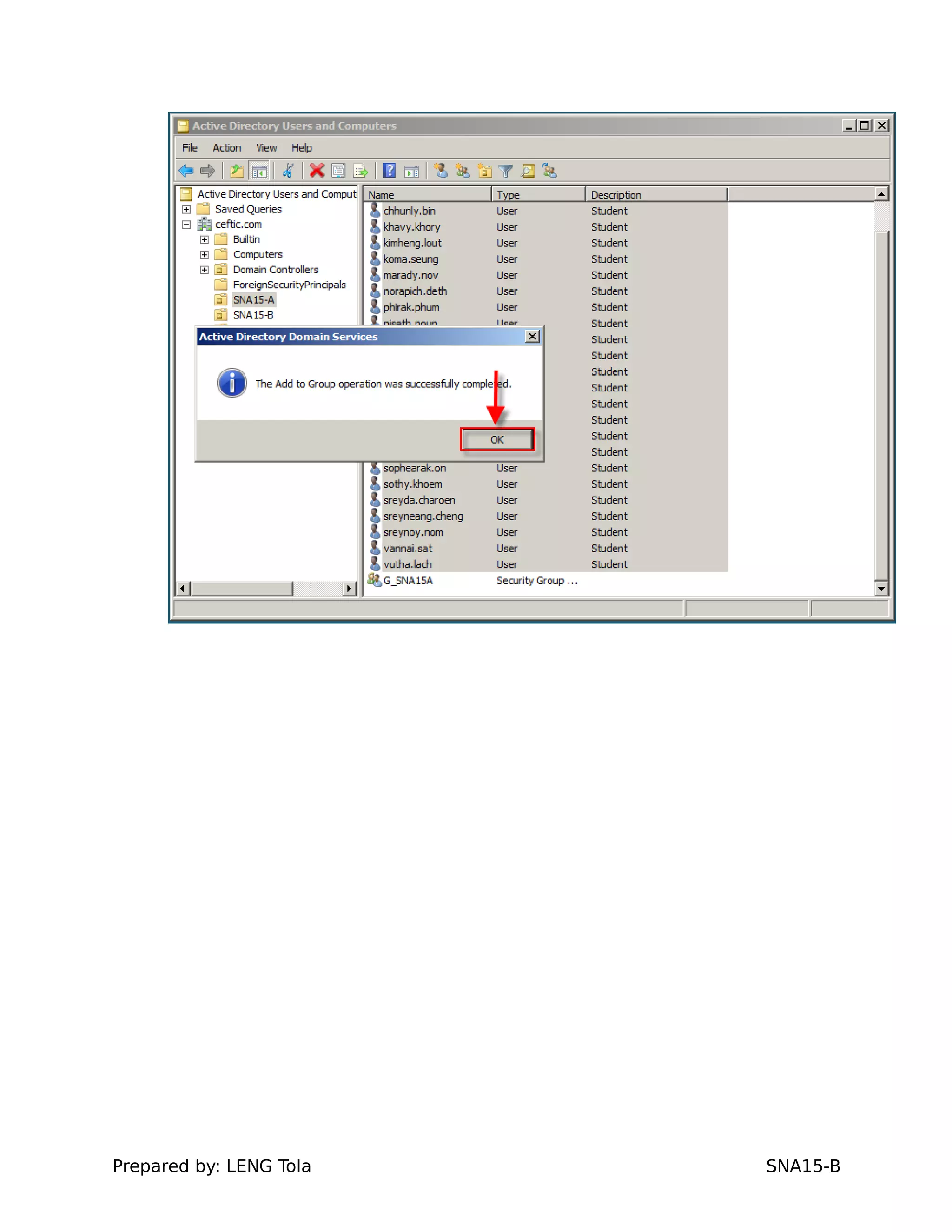
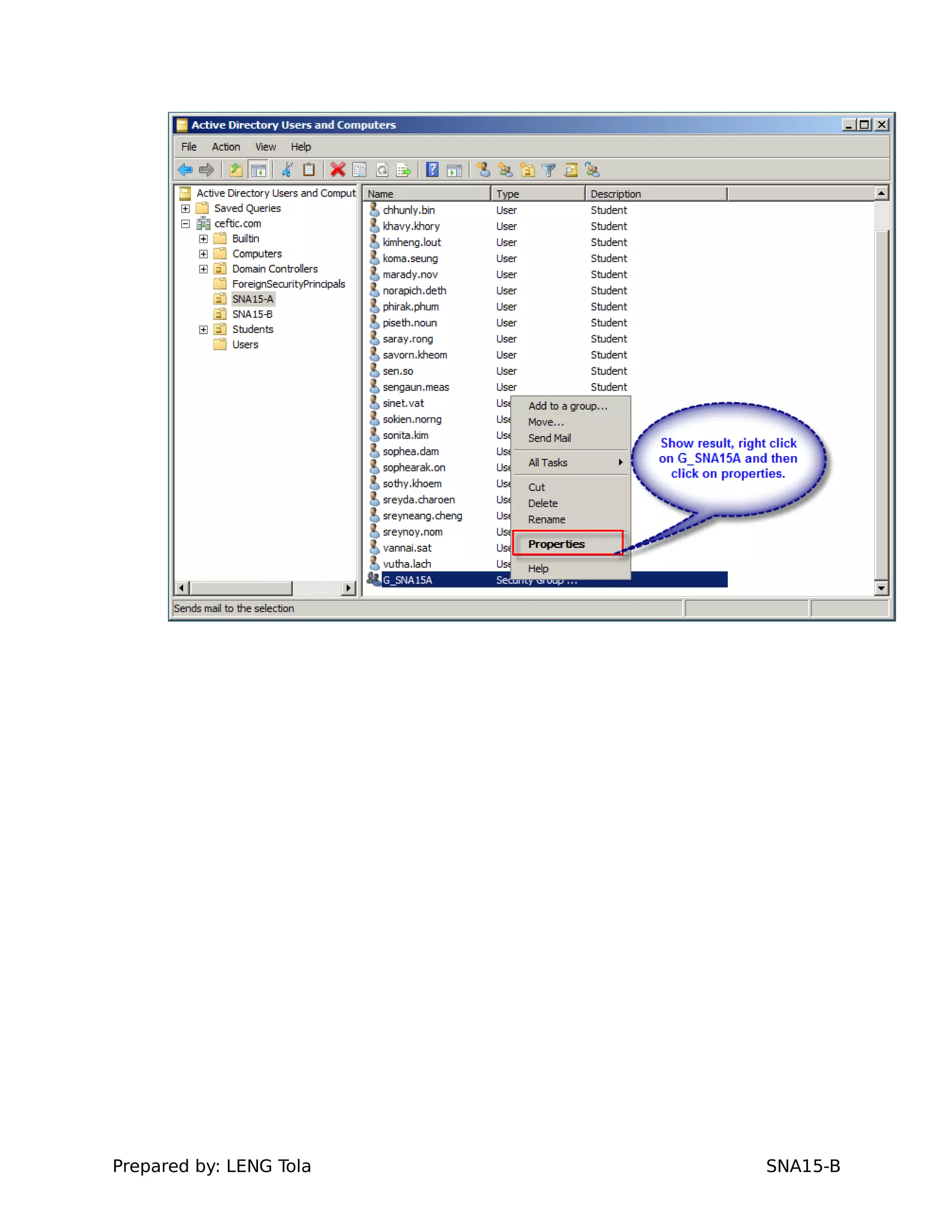
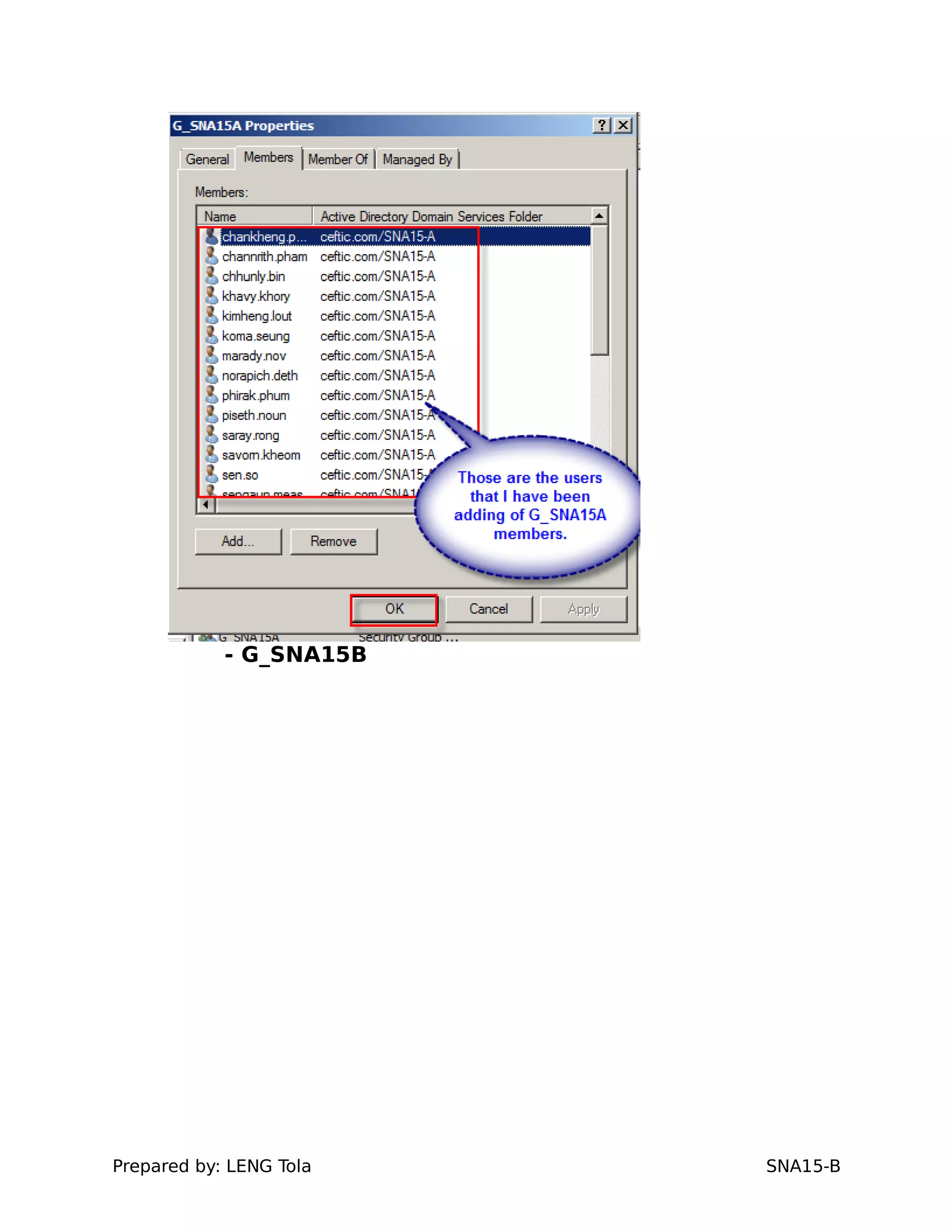
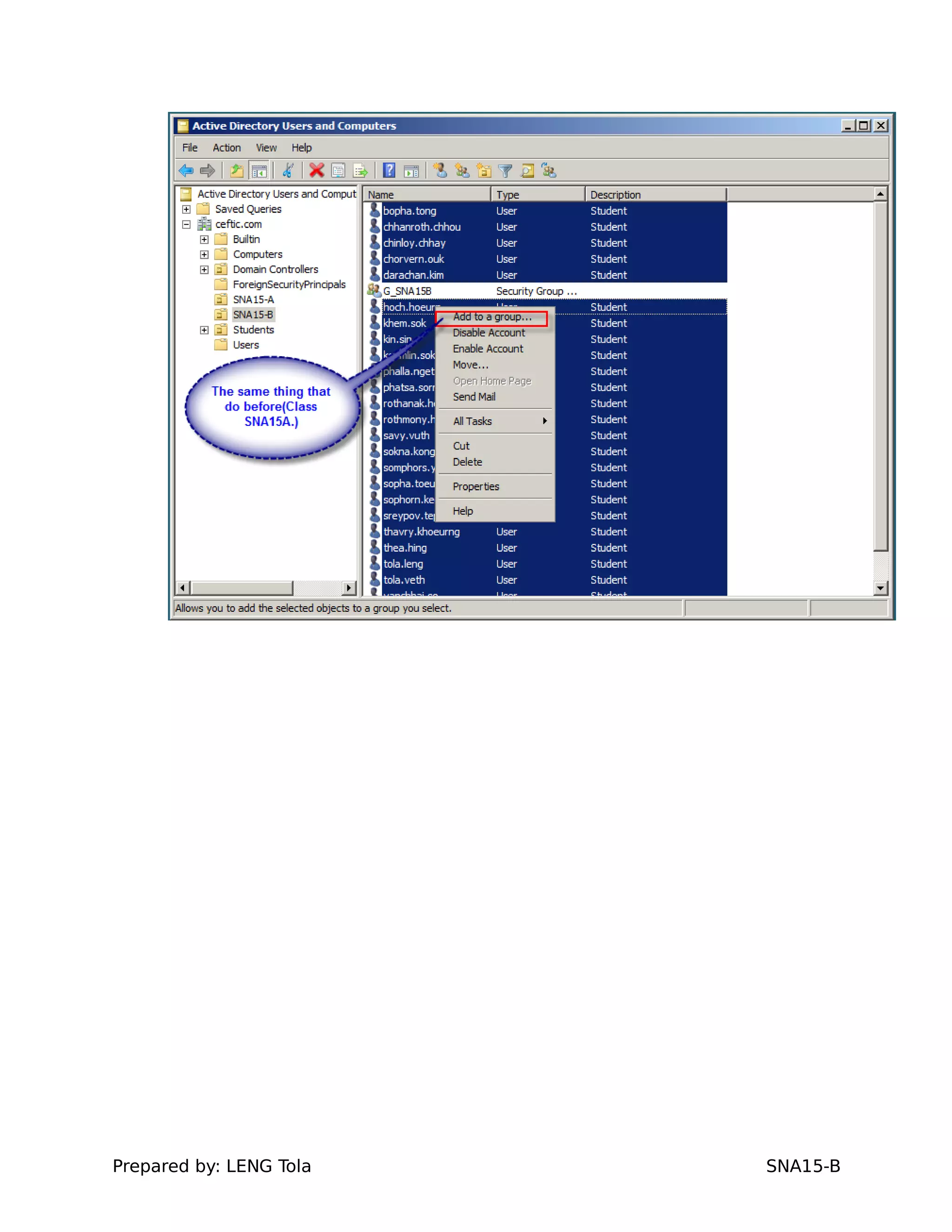
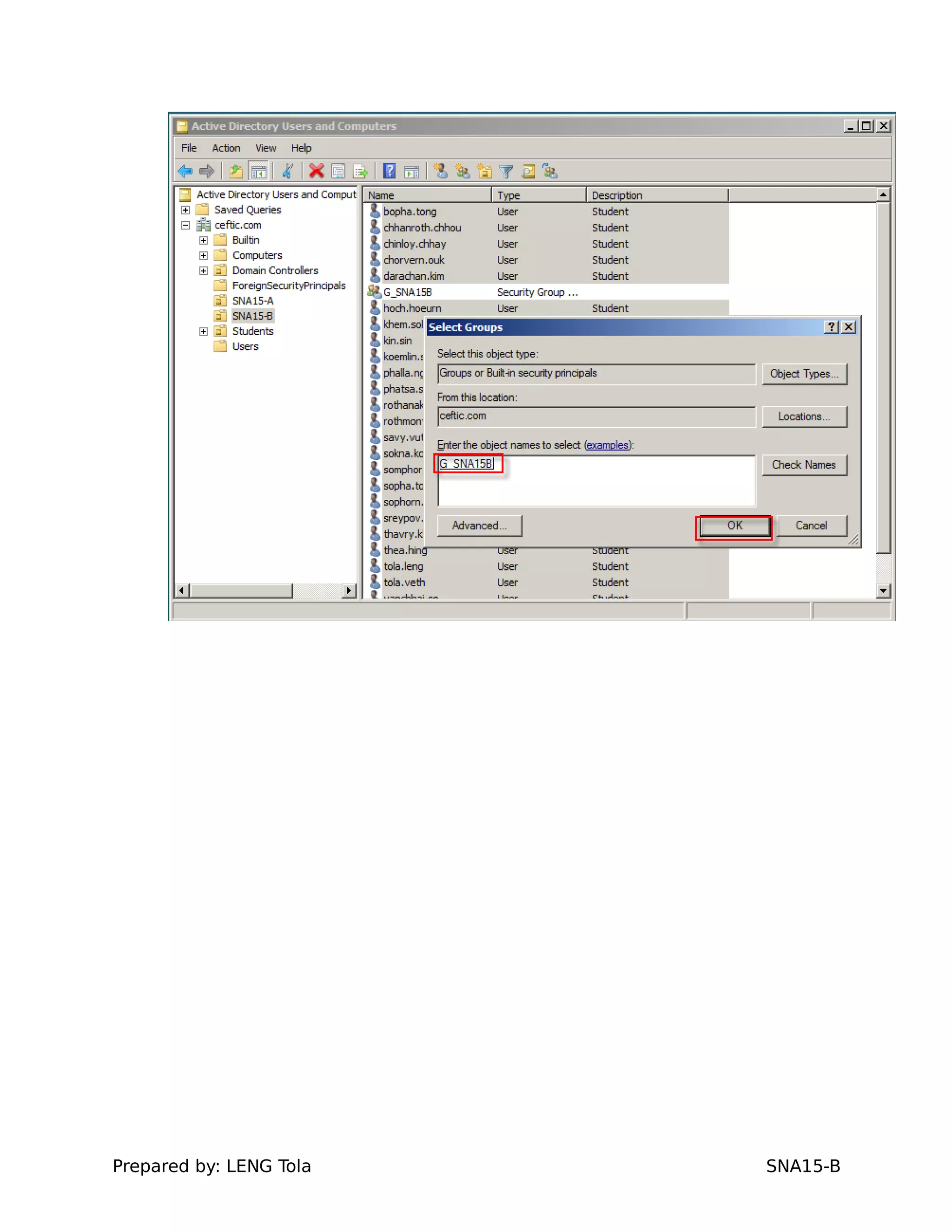
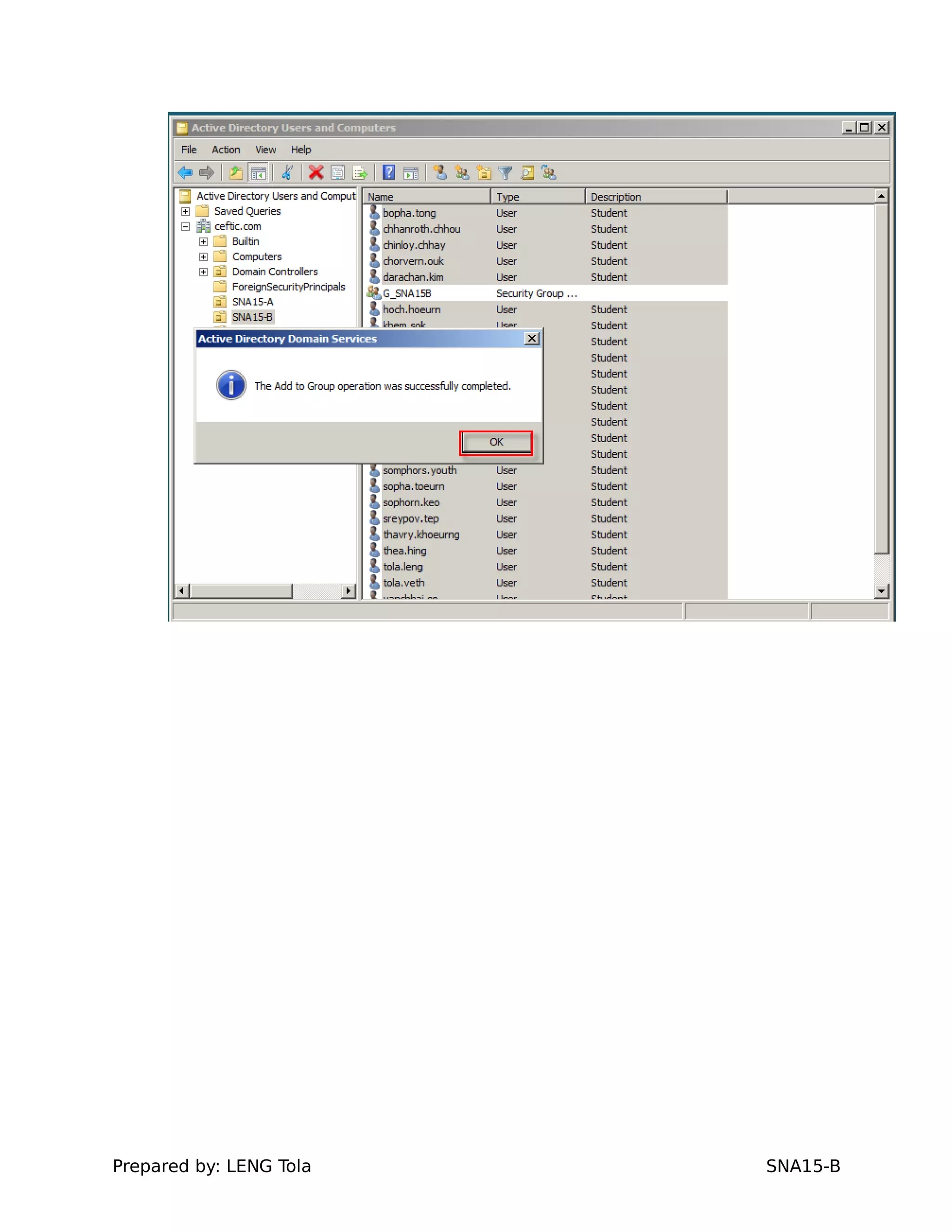
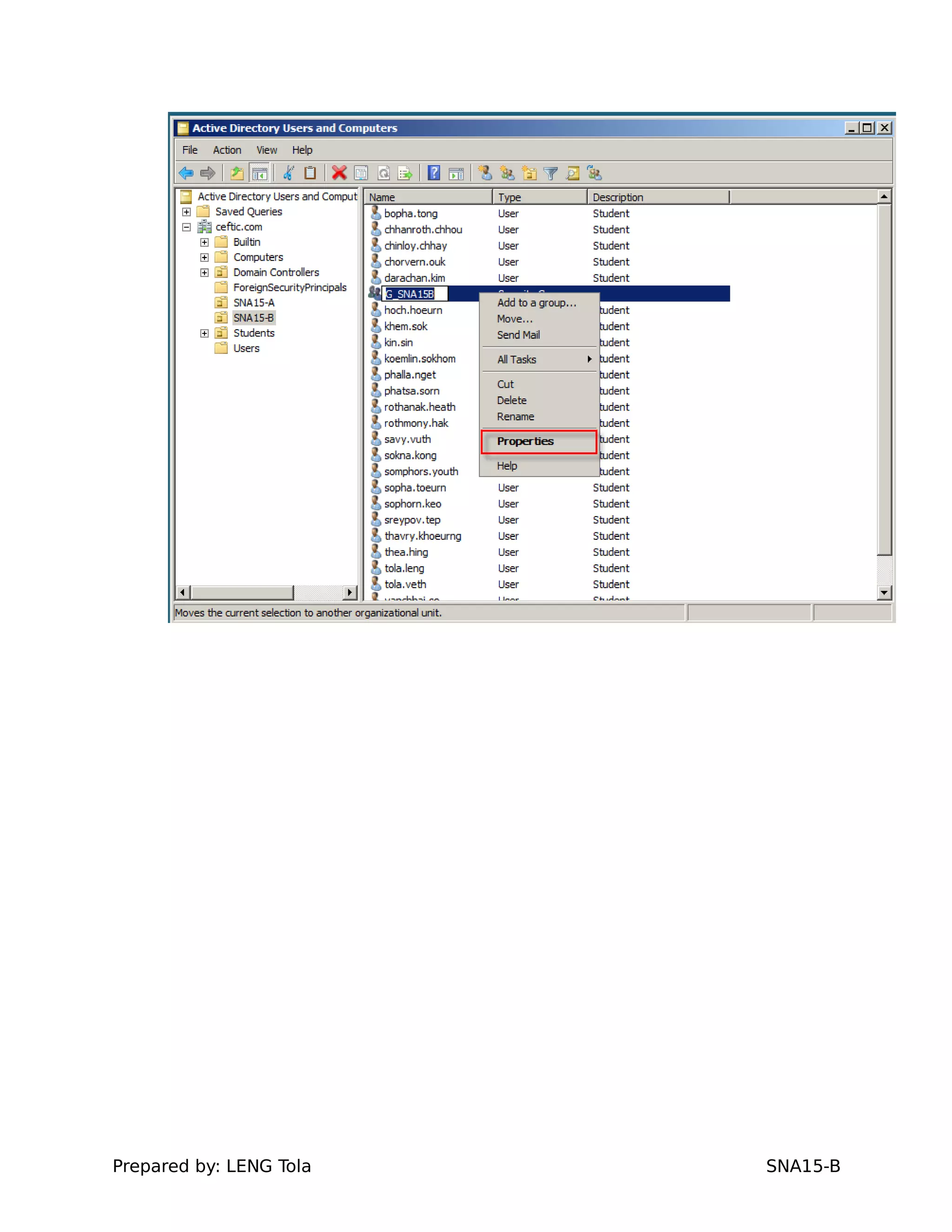
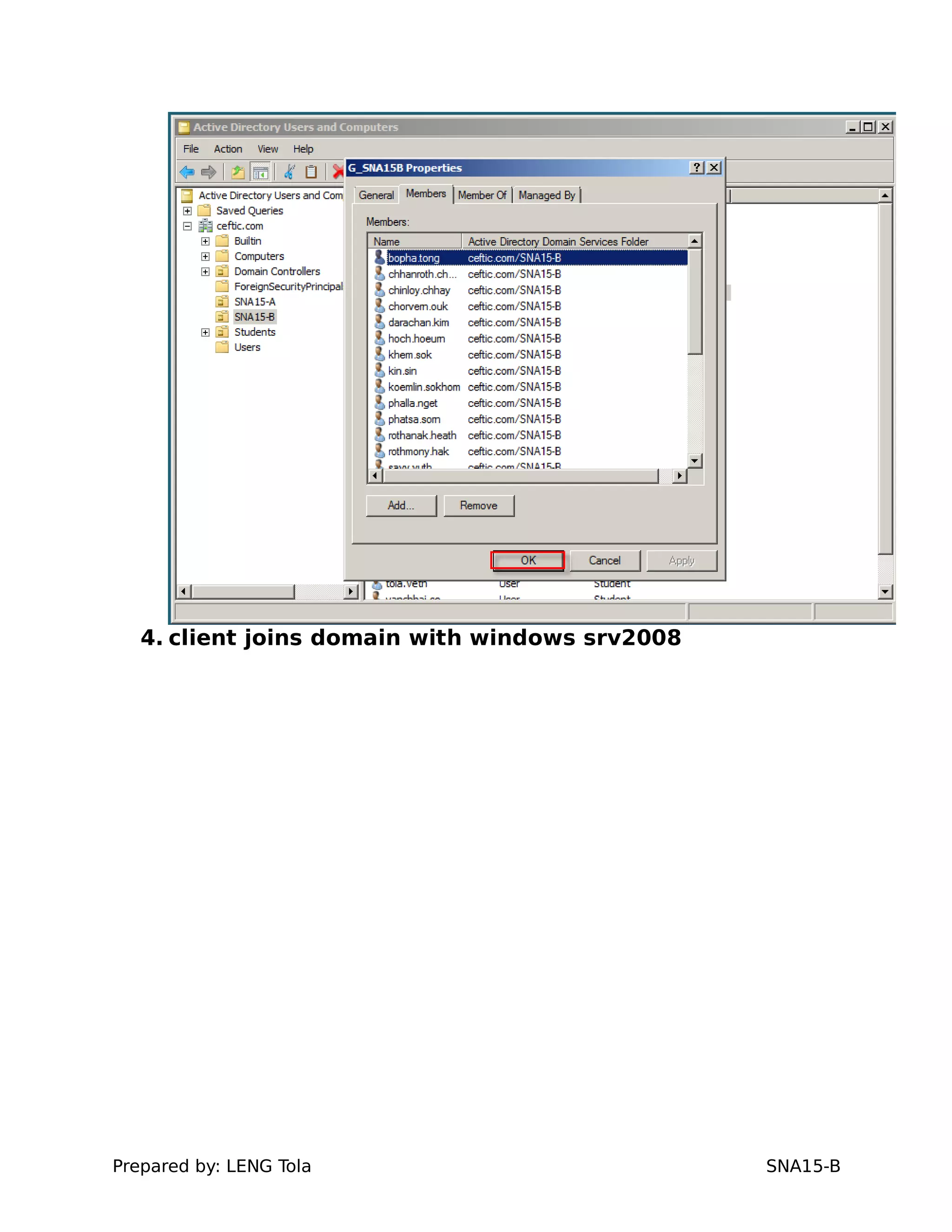
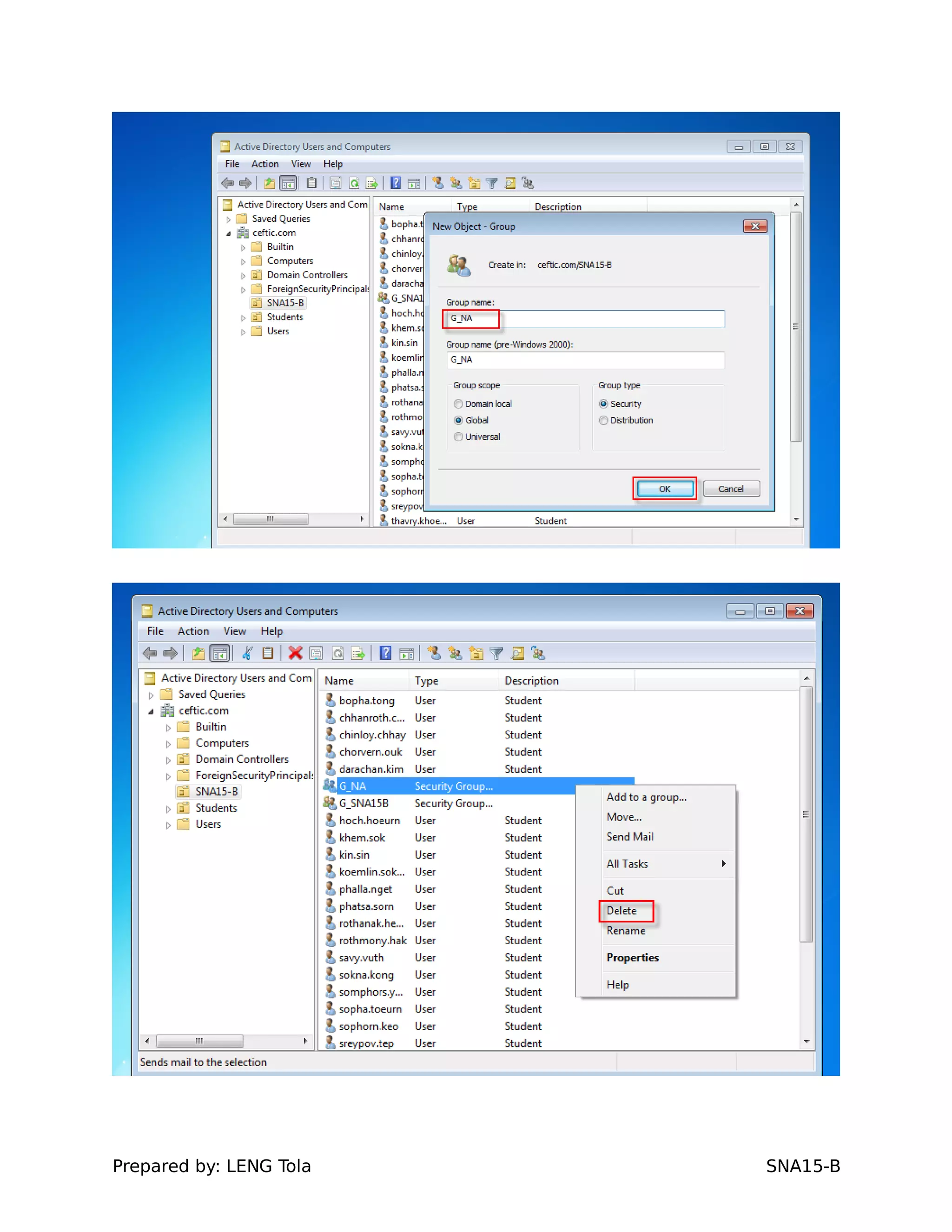
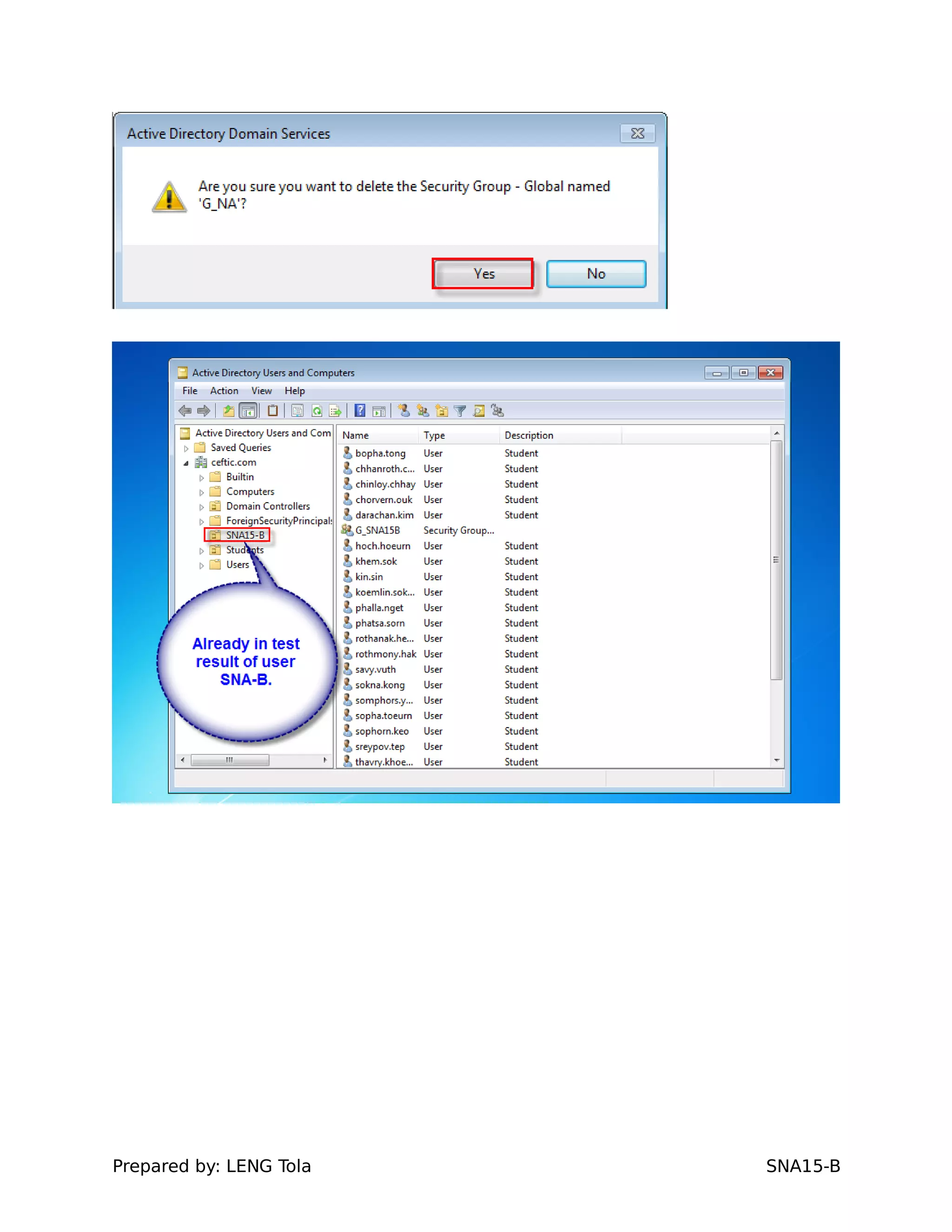
2. Adding users to security groups
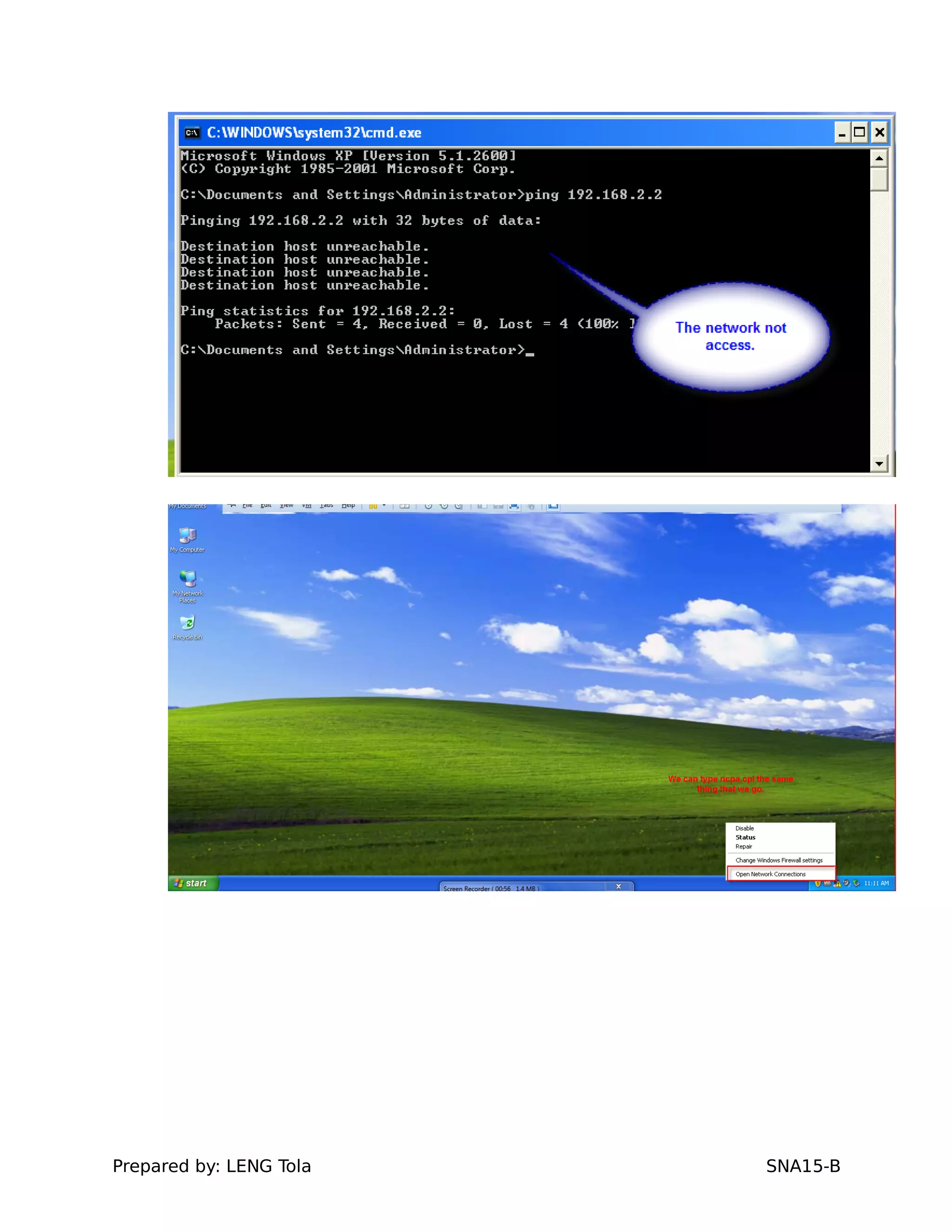
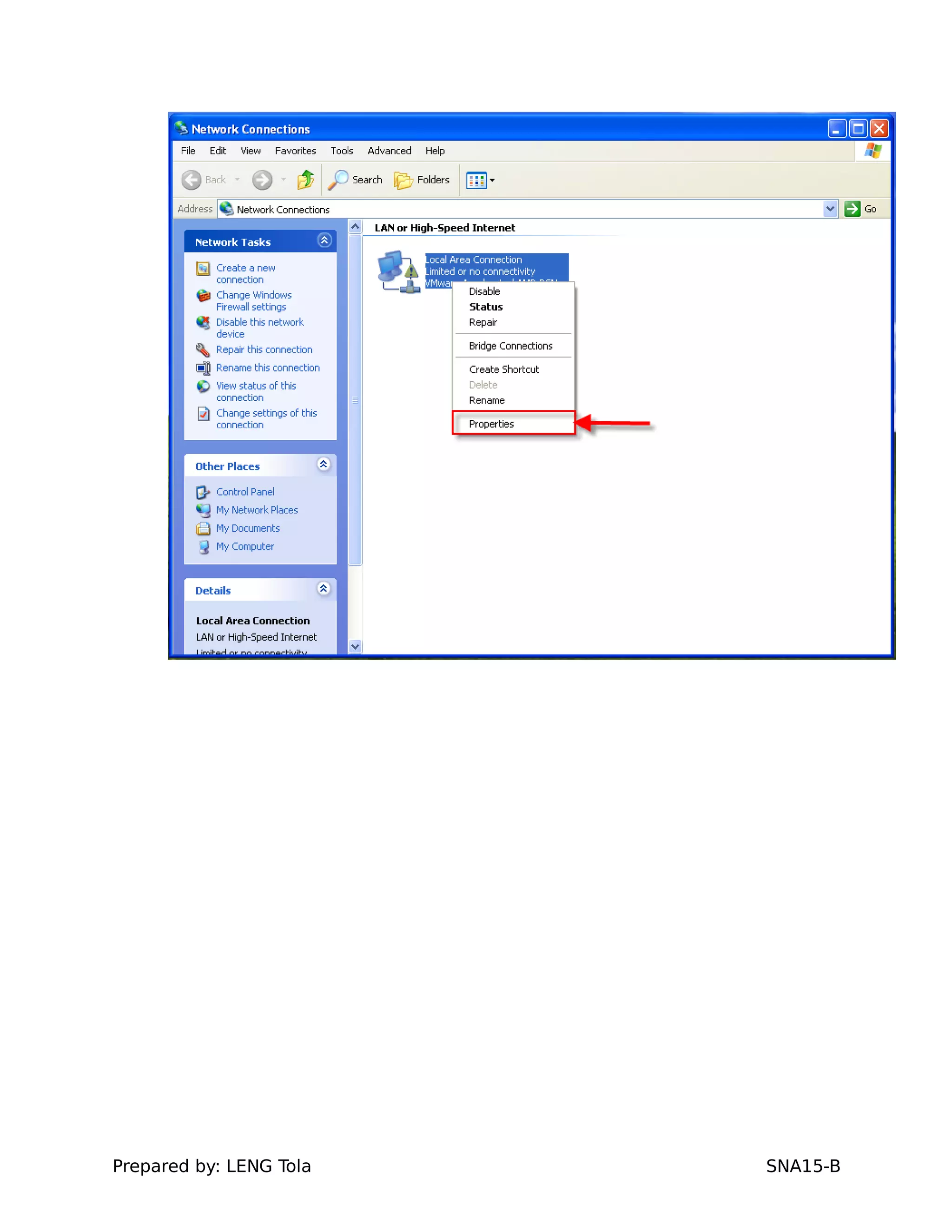
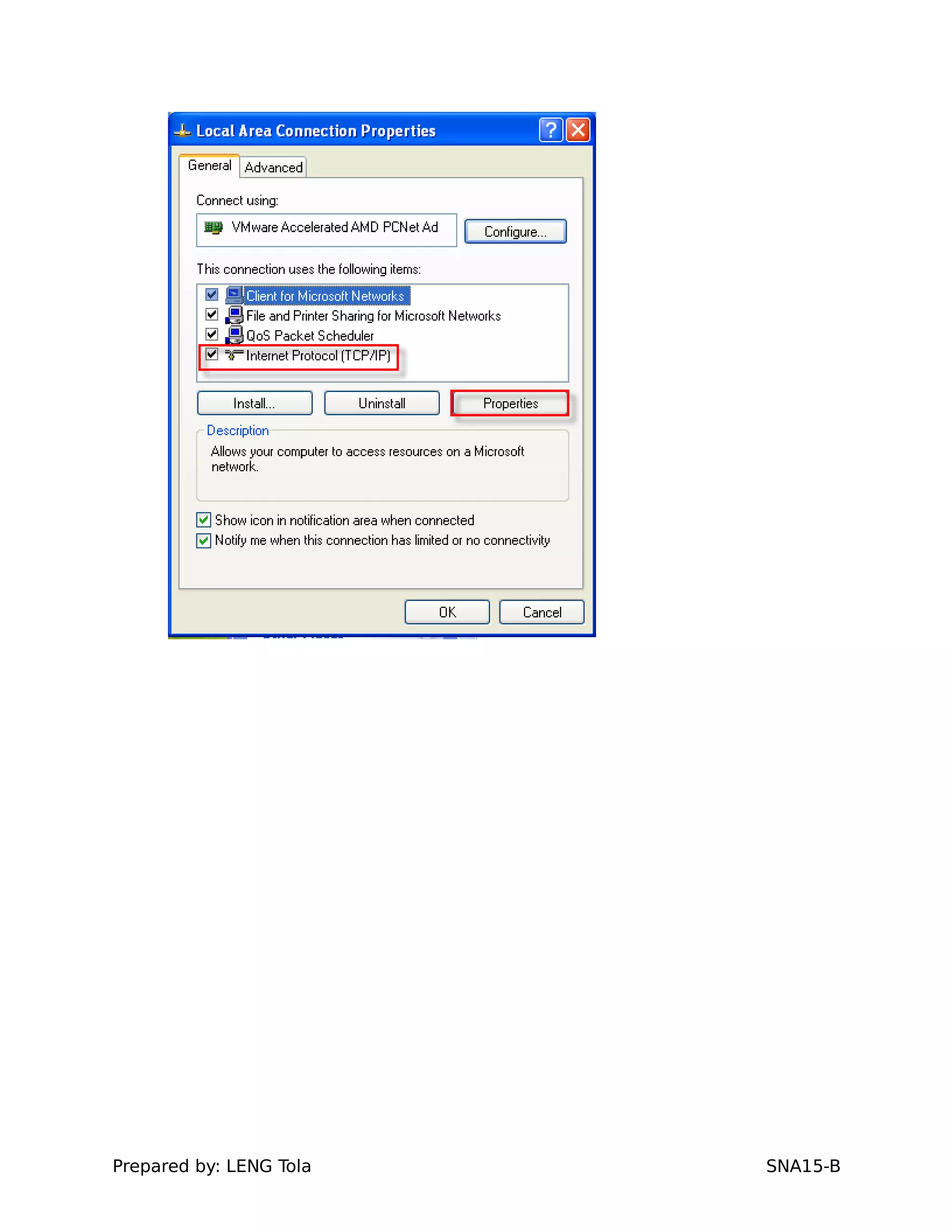
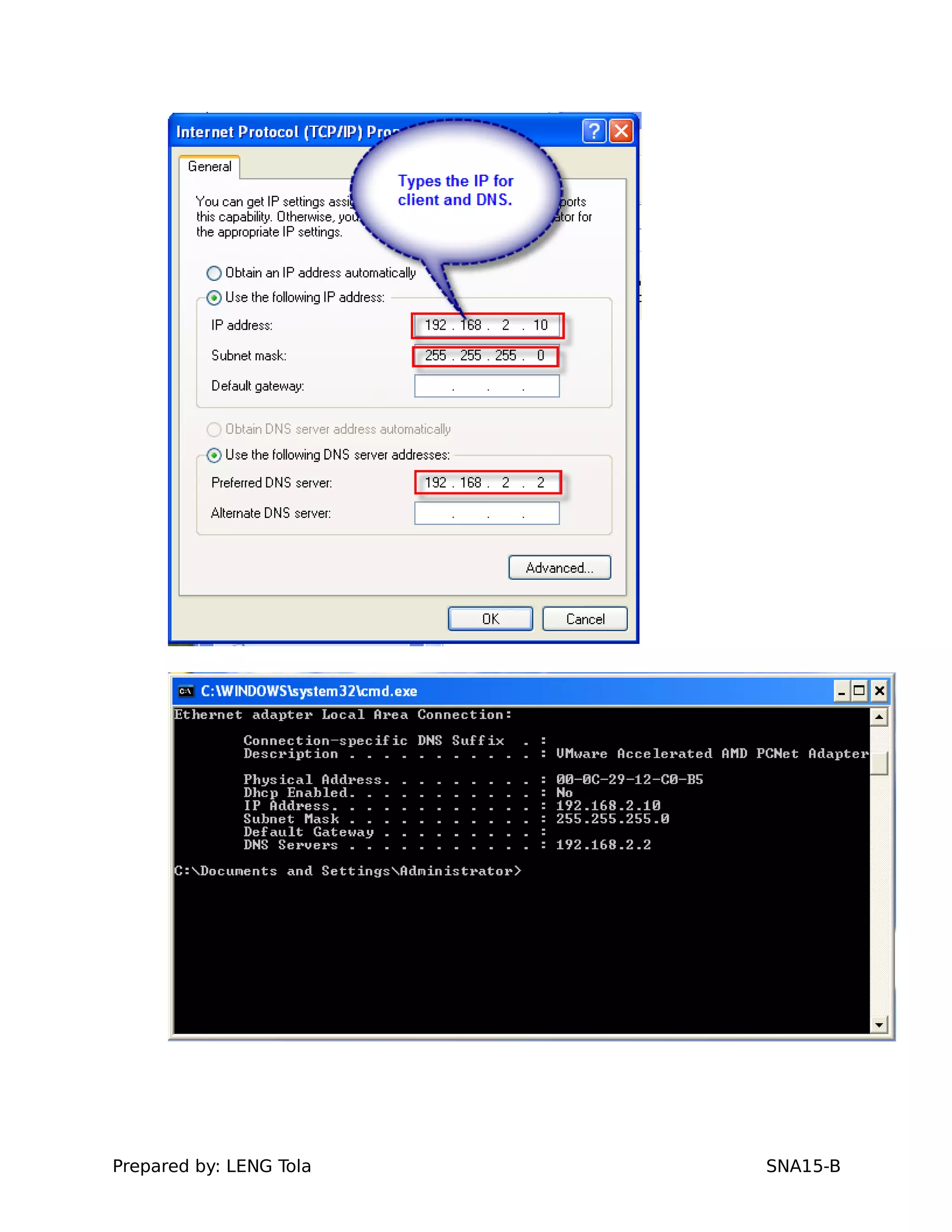
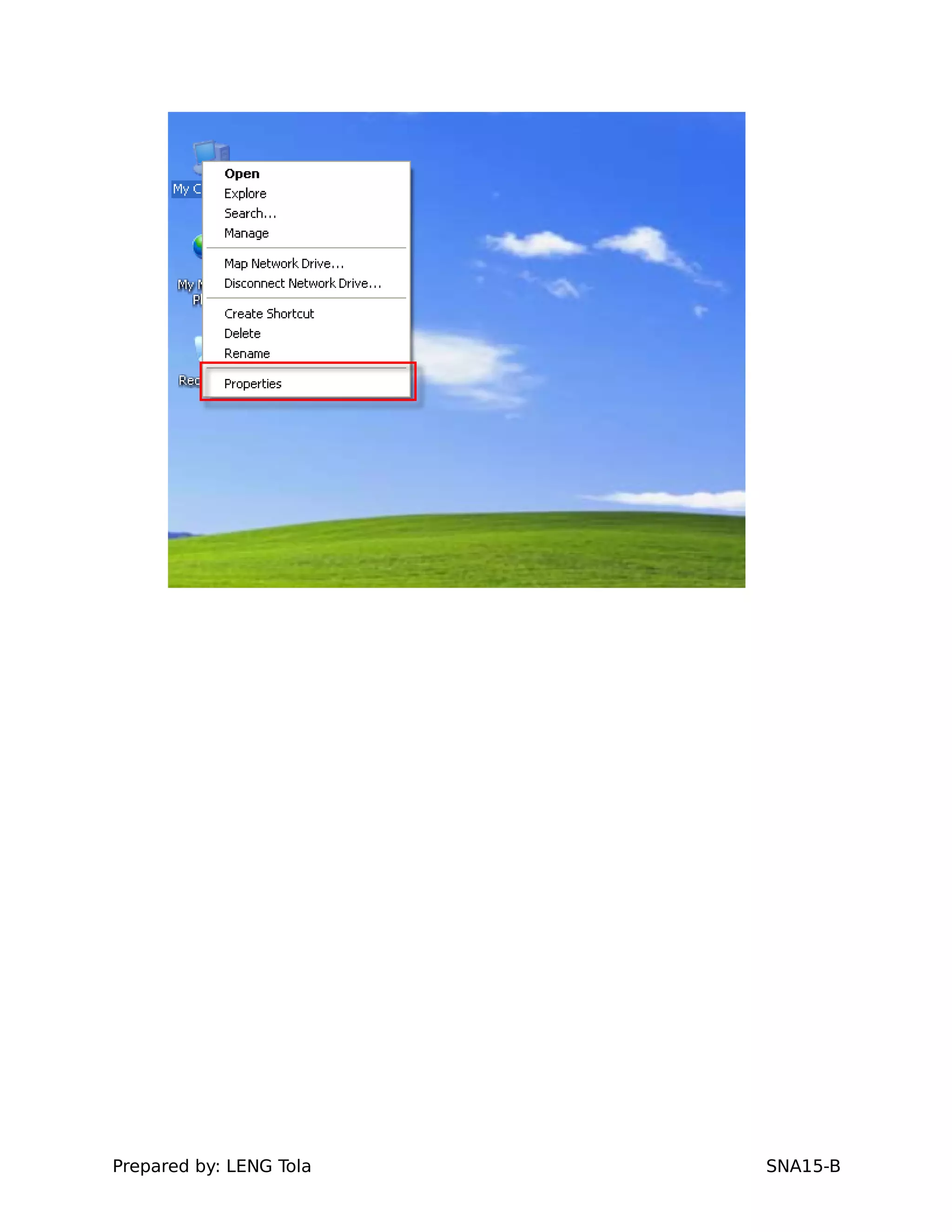
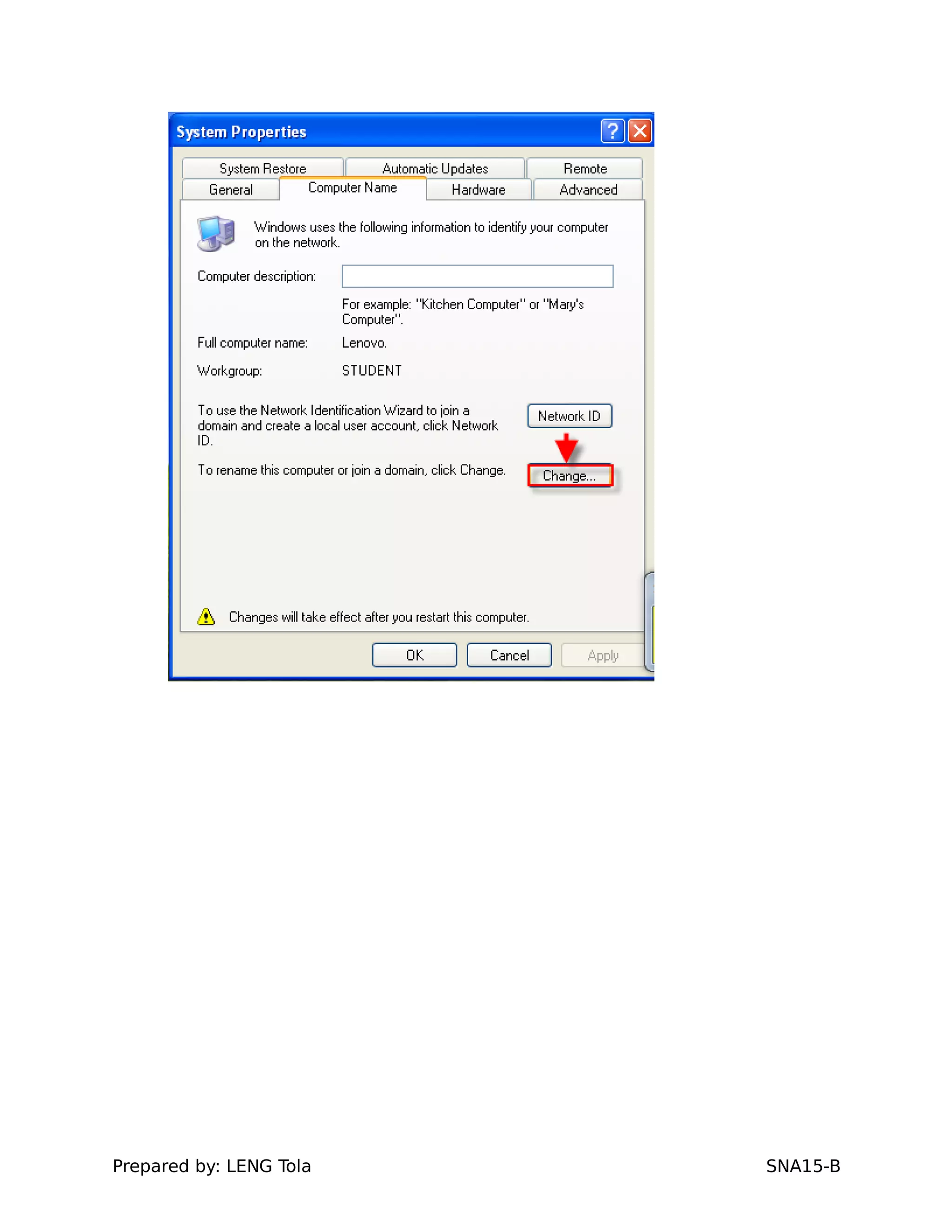
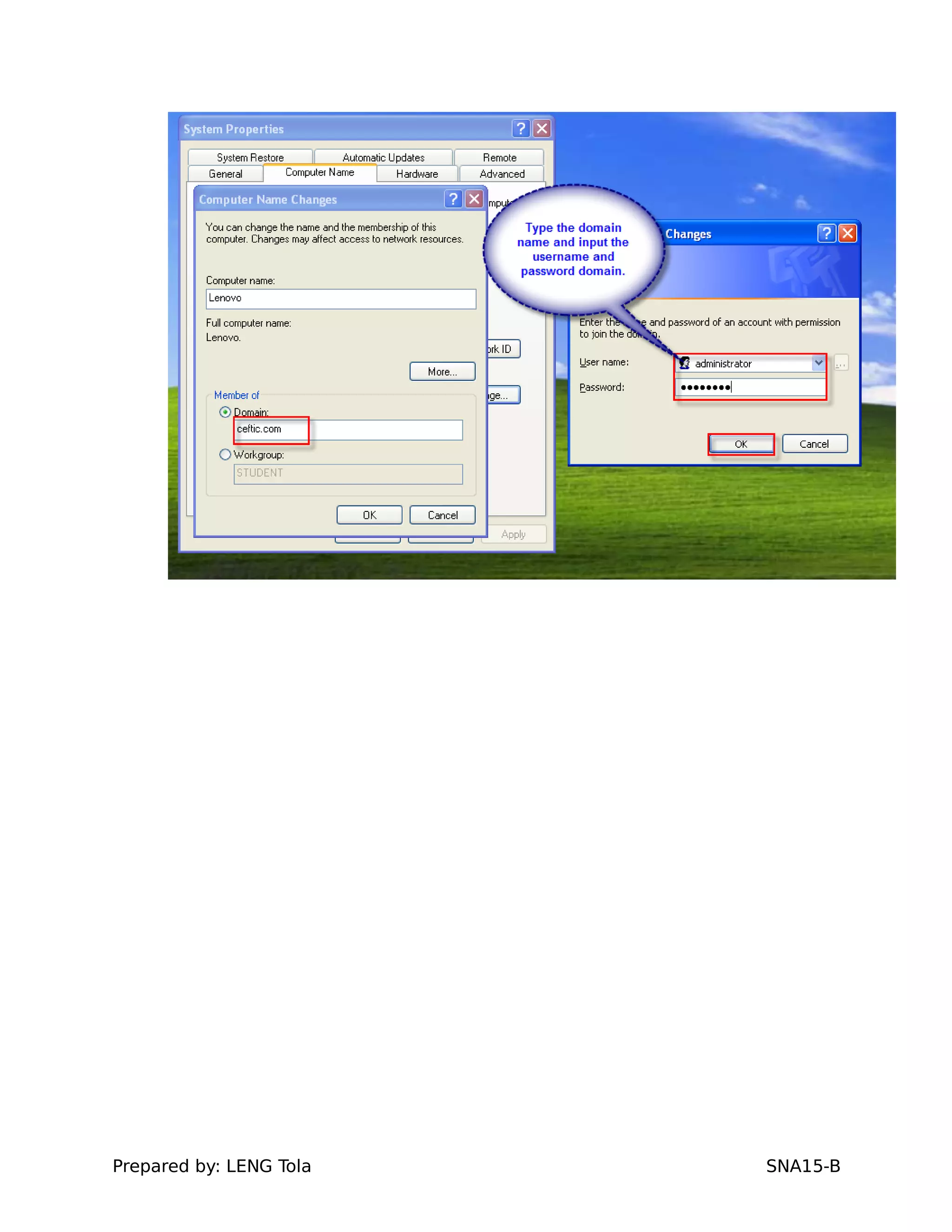
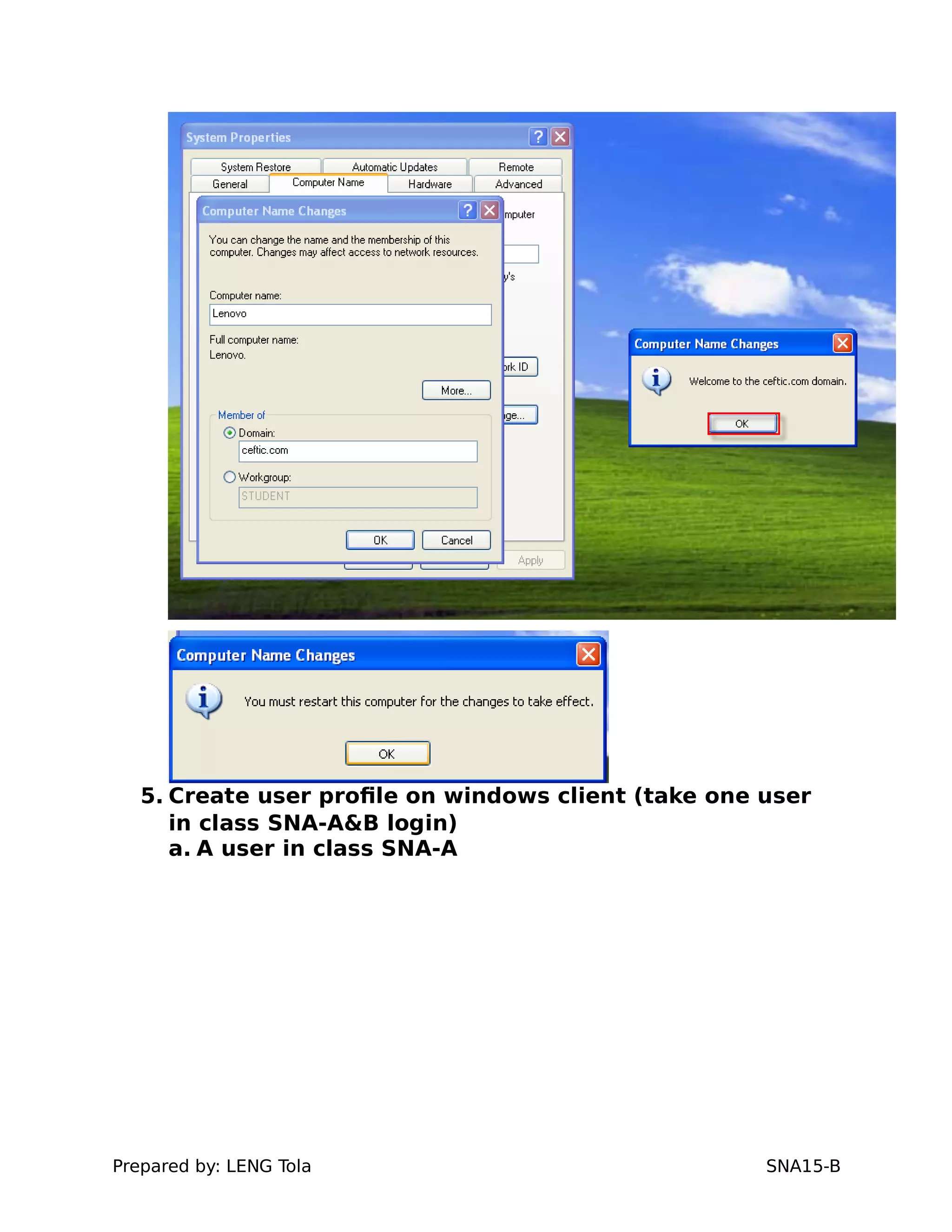
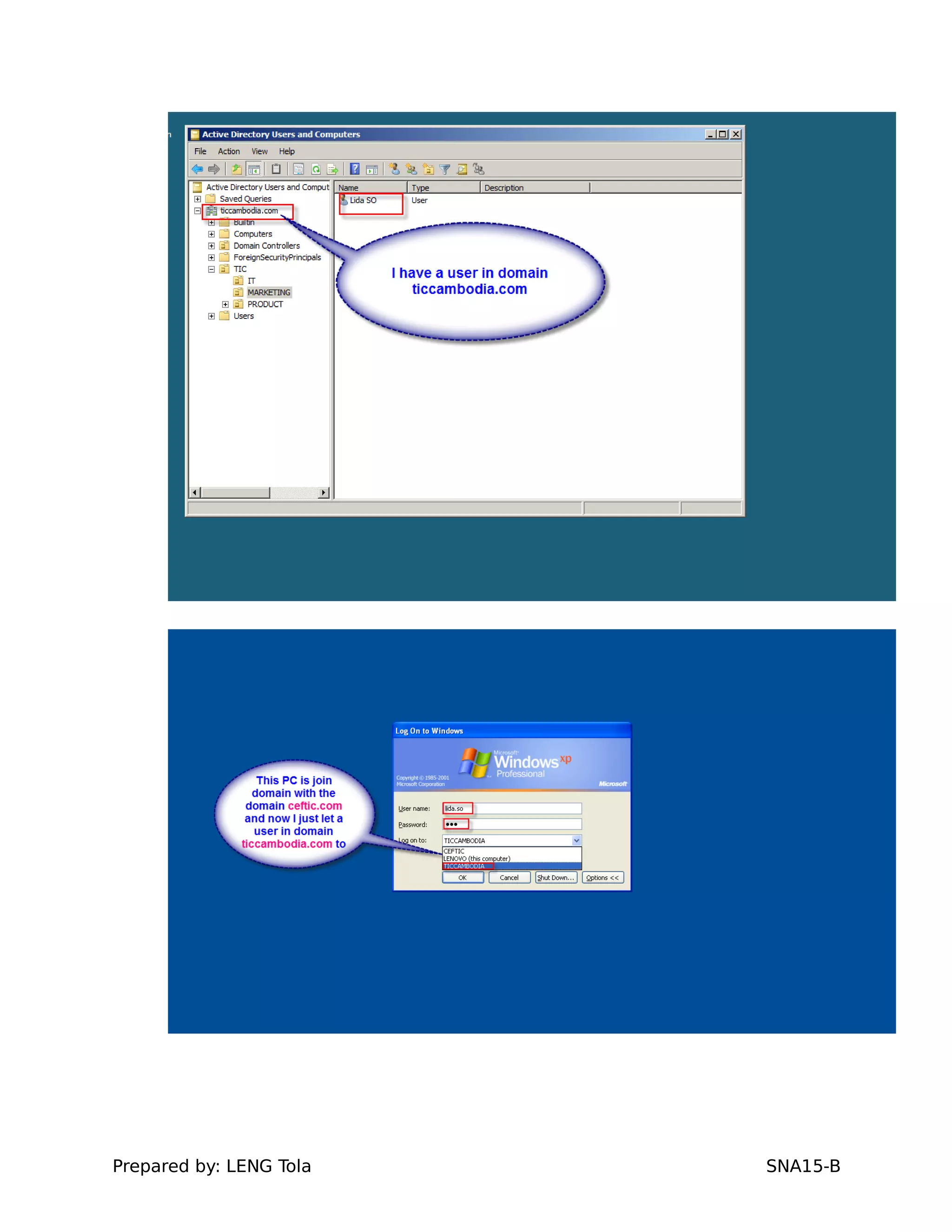
3. Joining a Windows client to the domain
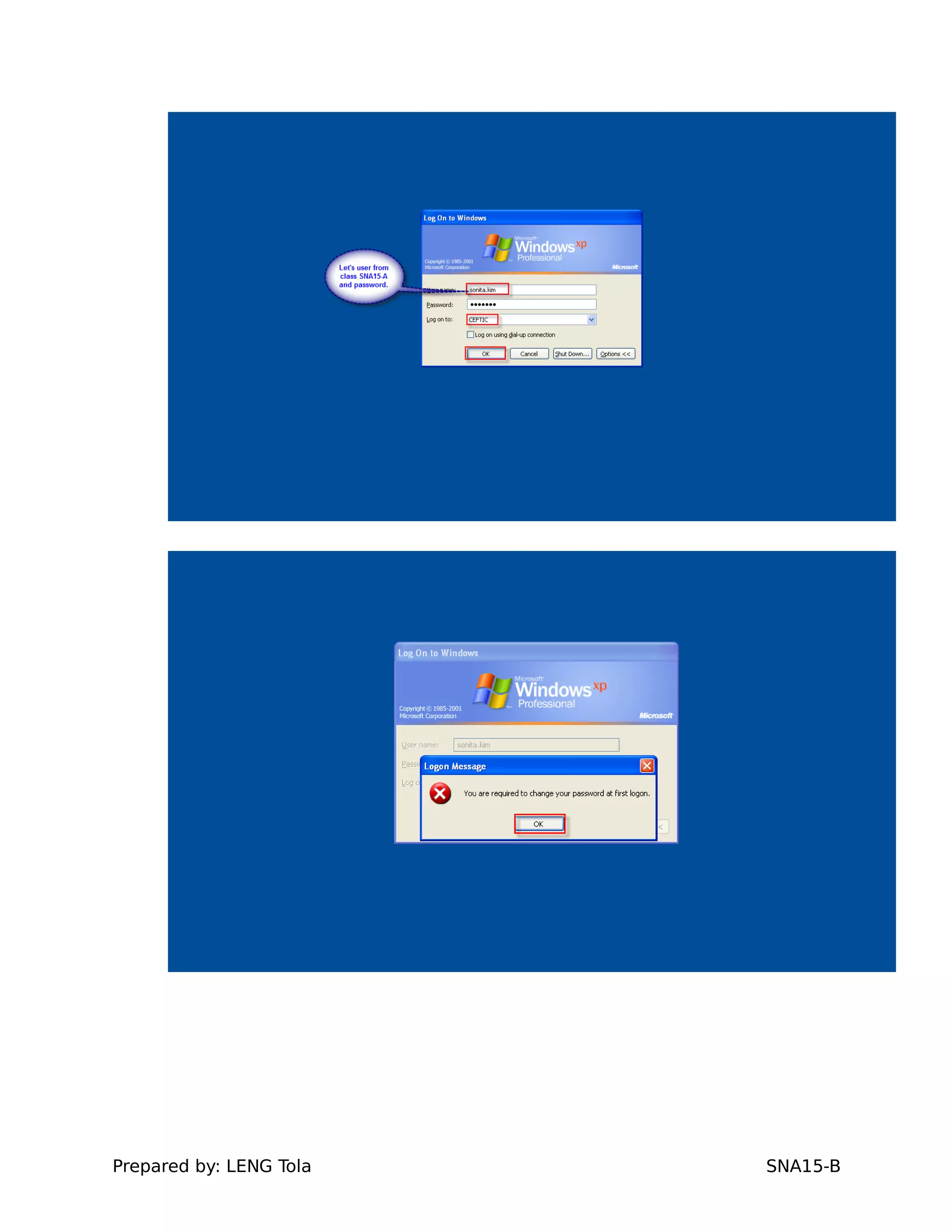
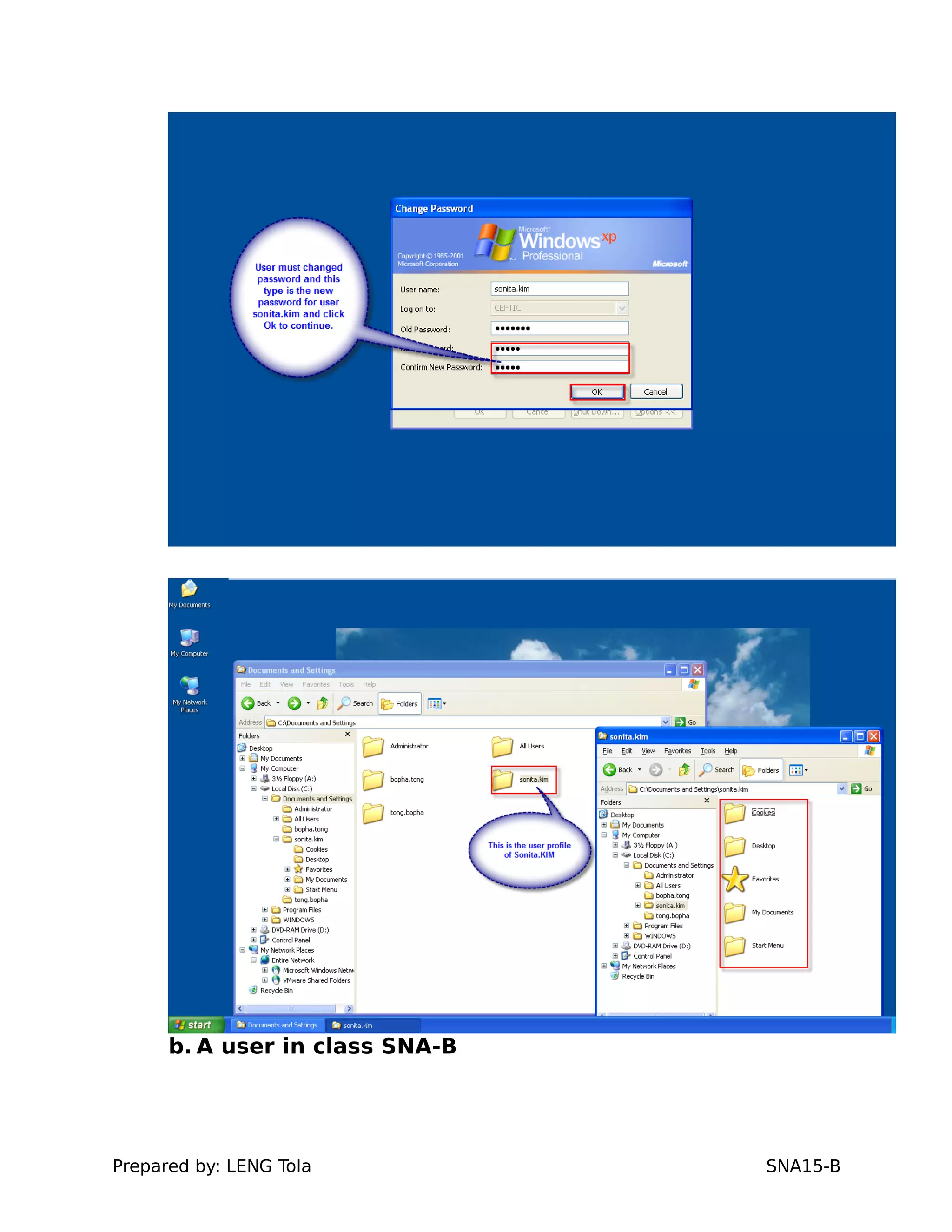
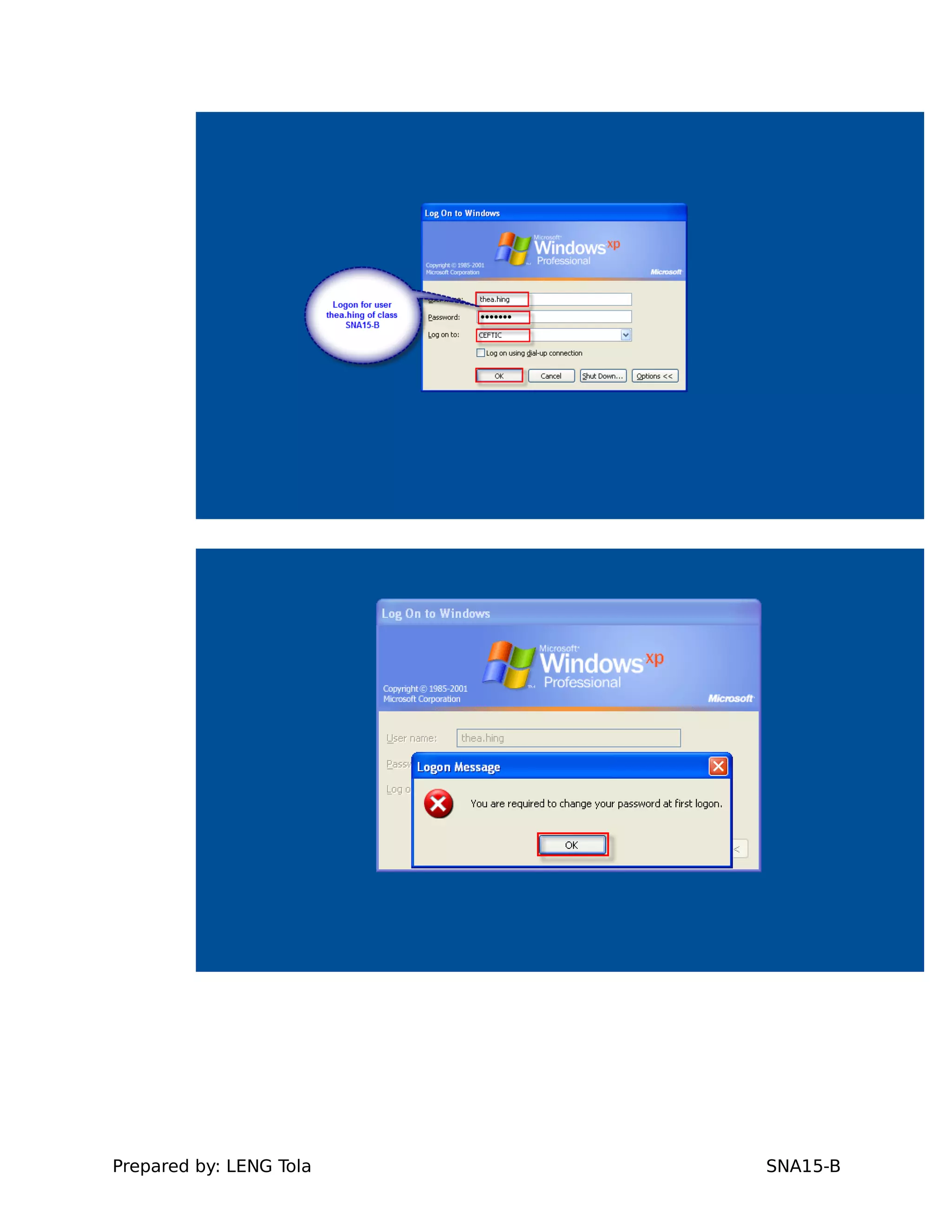
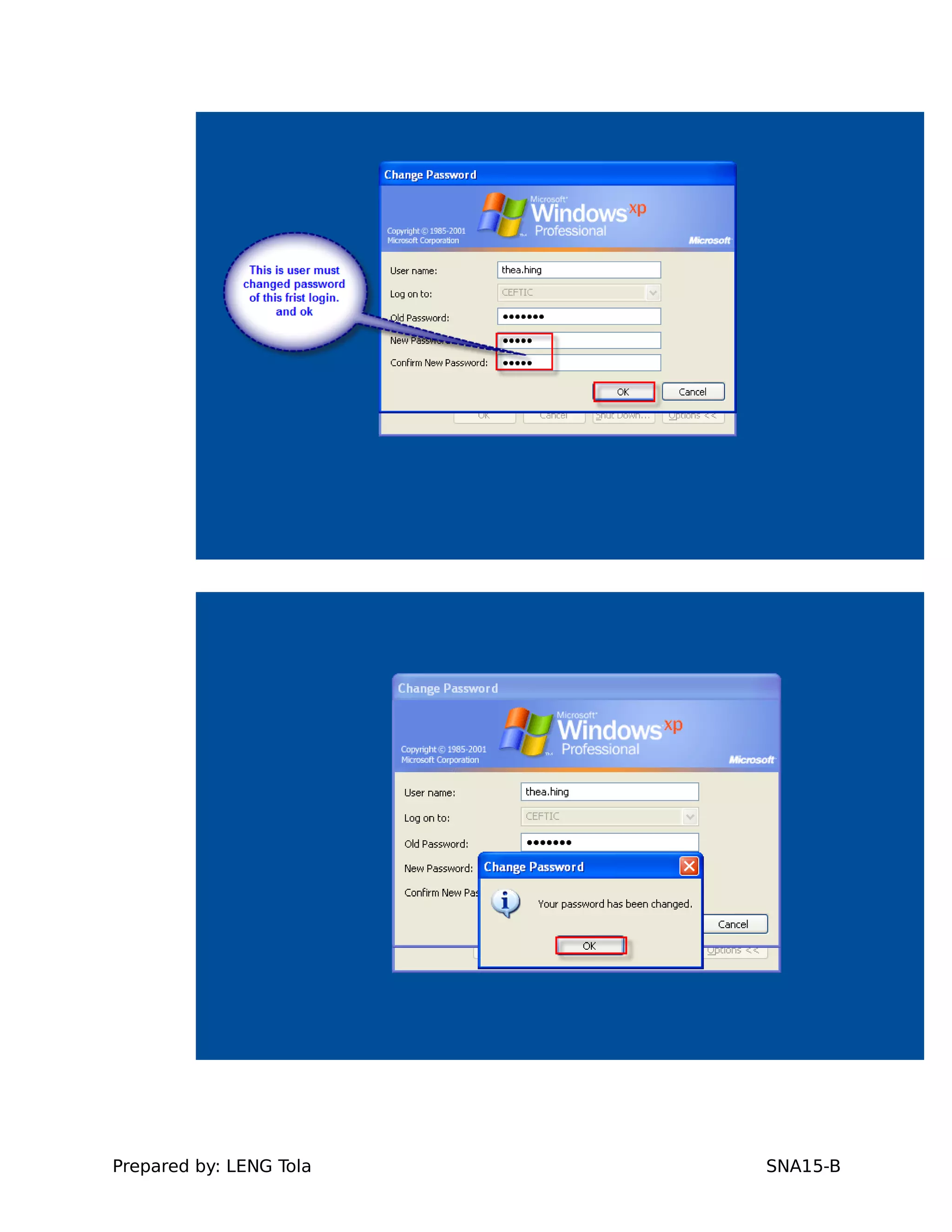
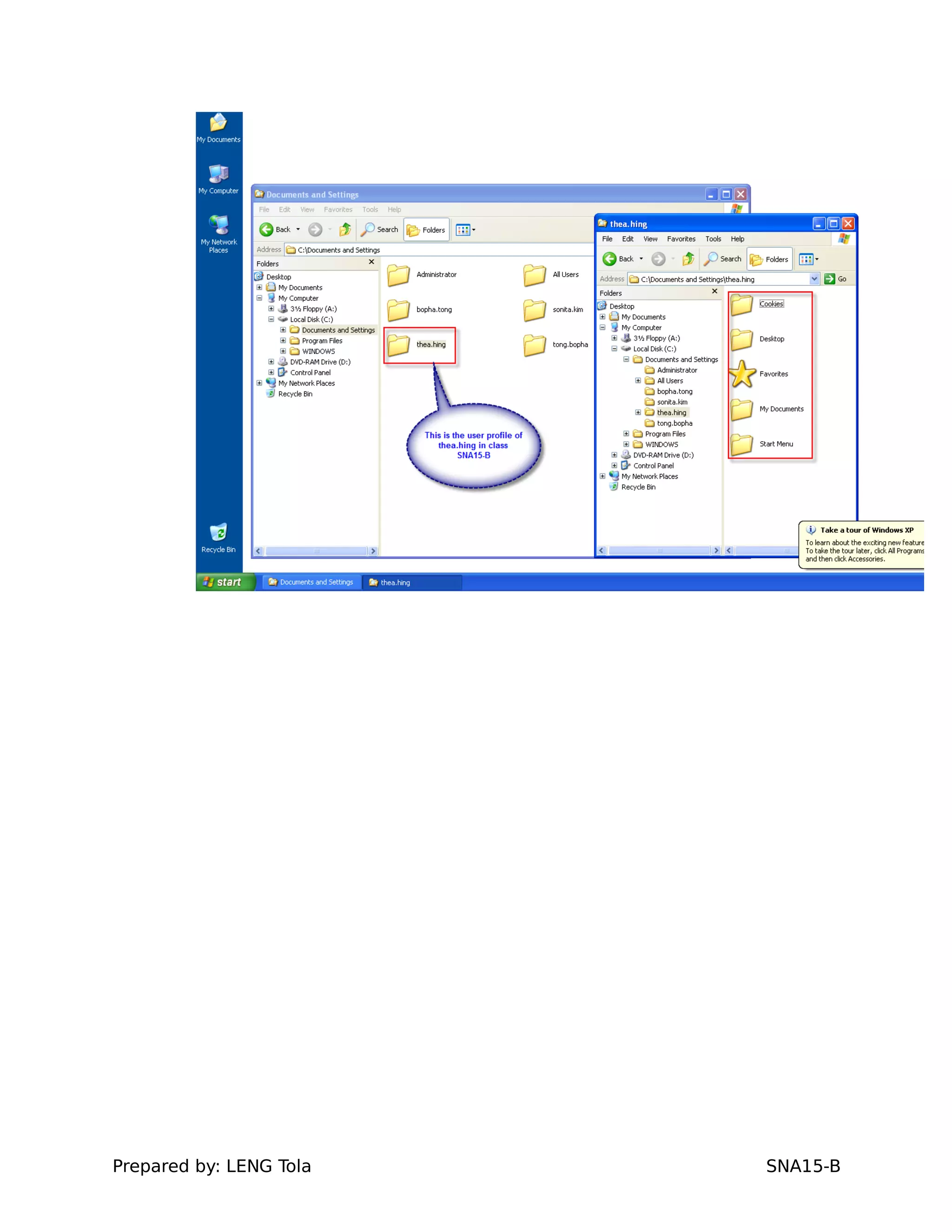
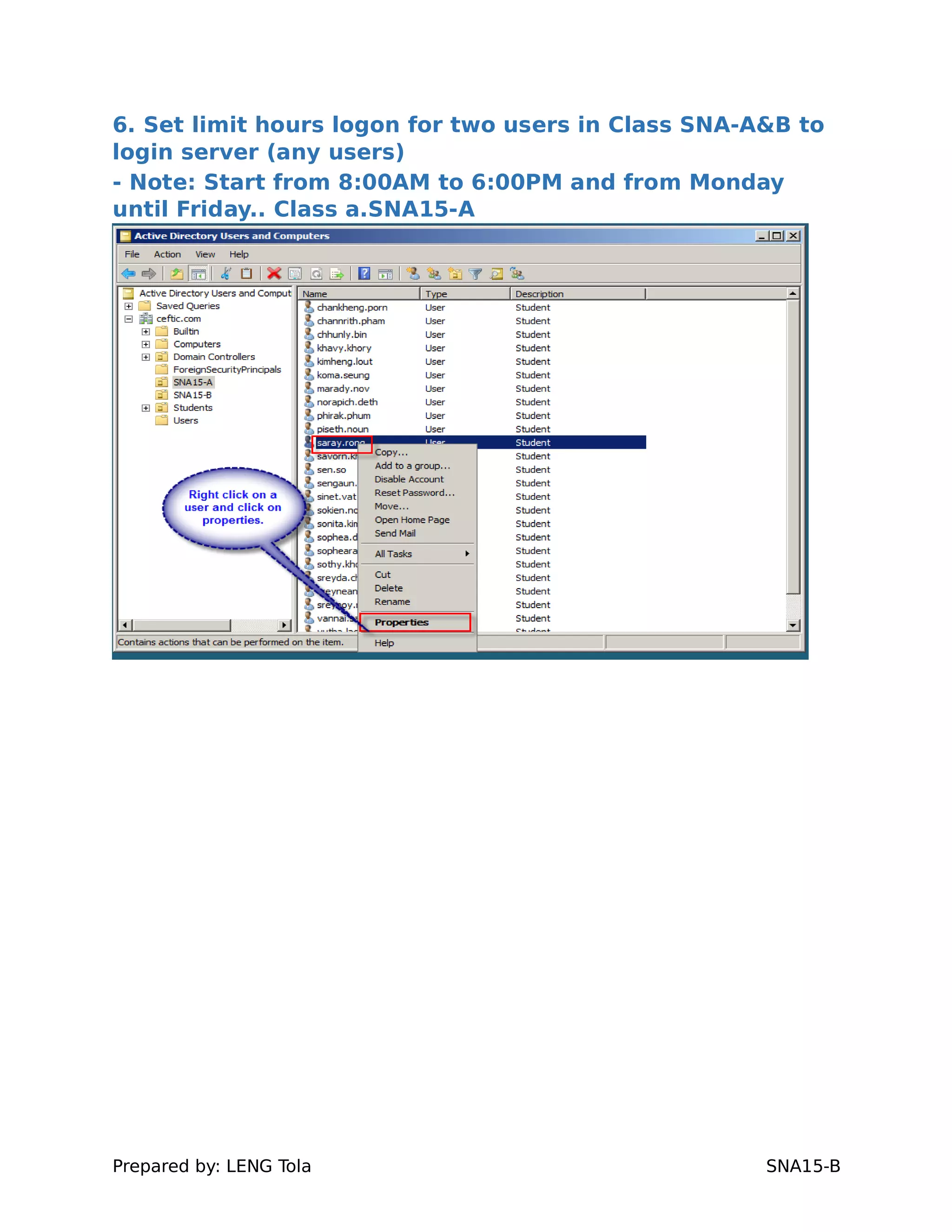
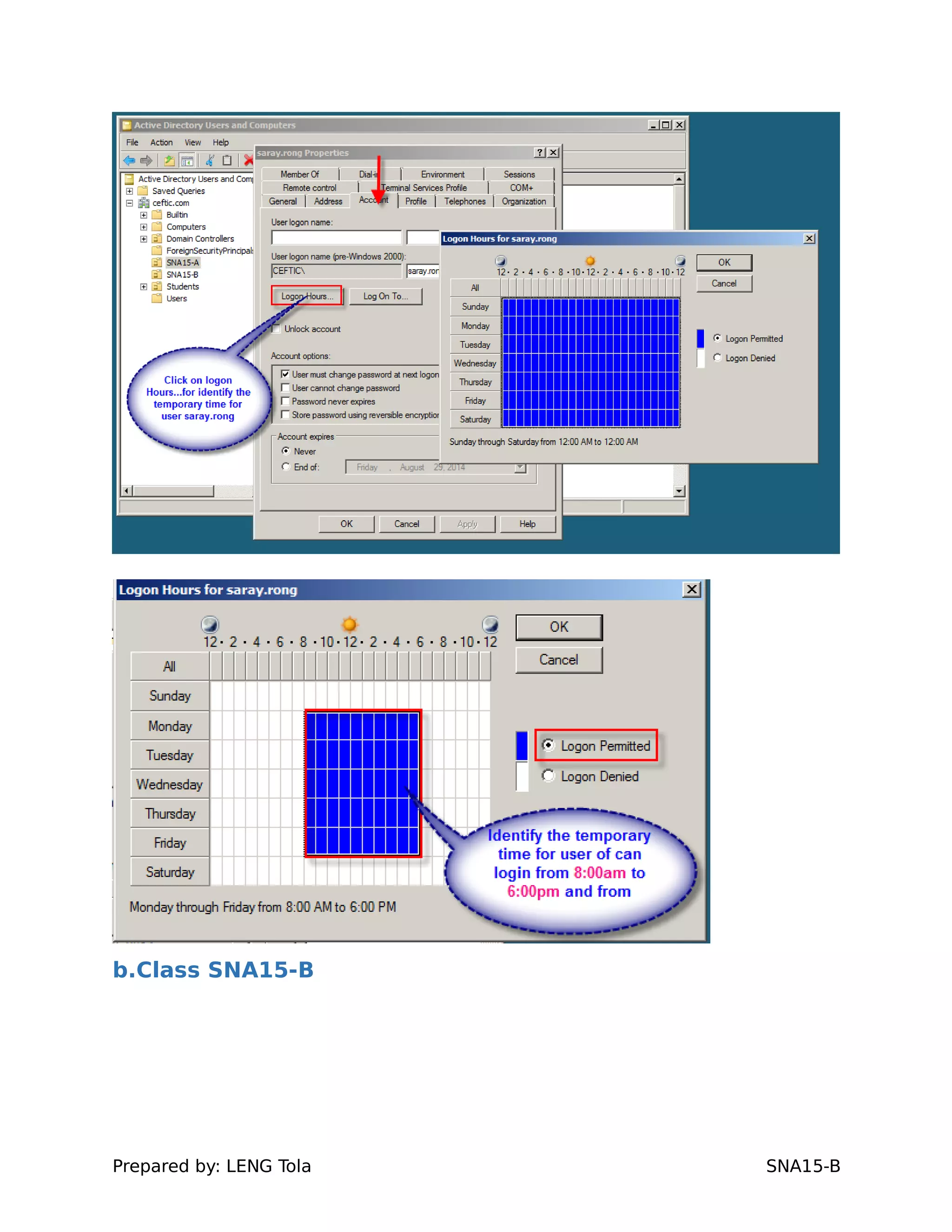
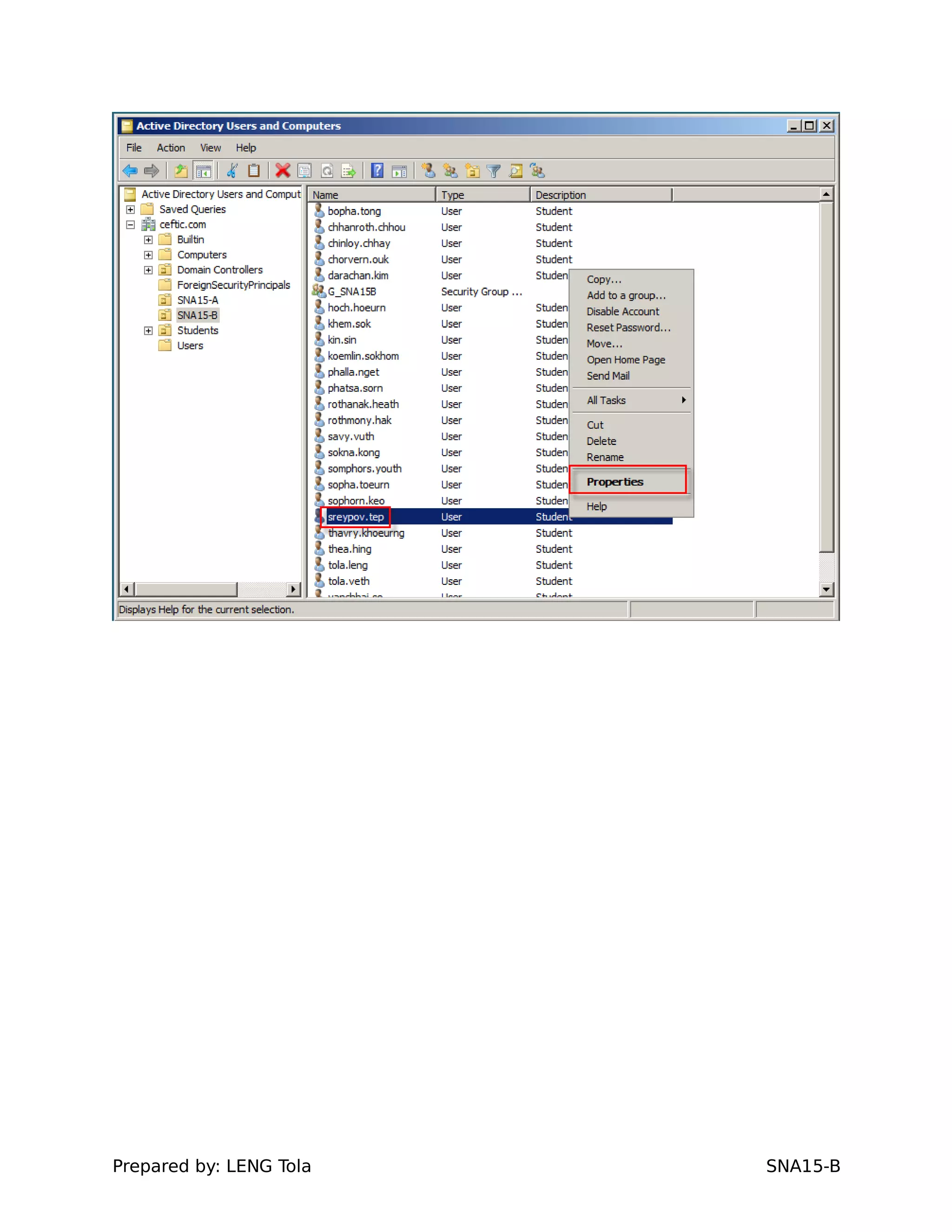
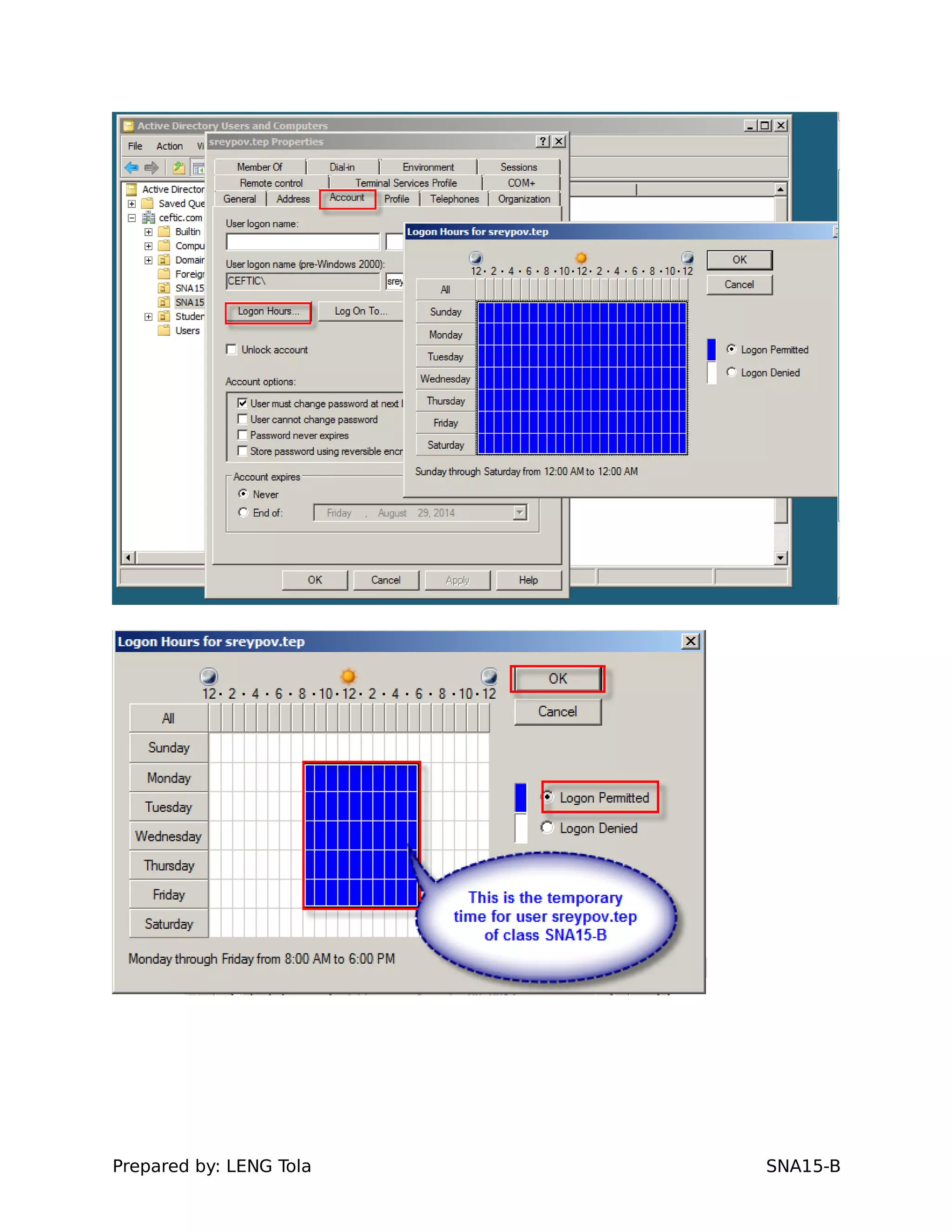
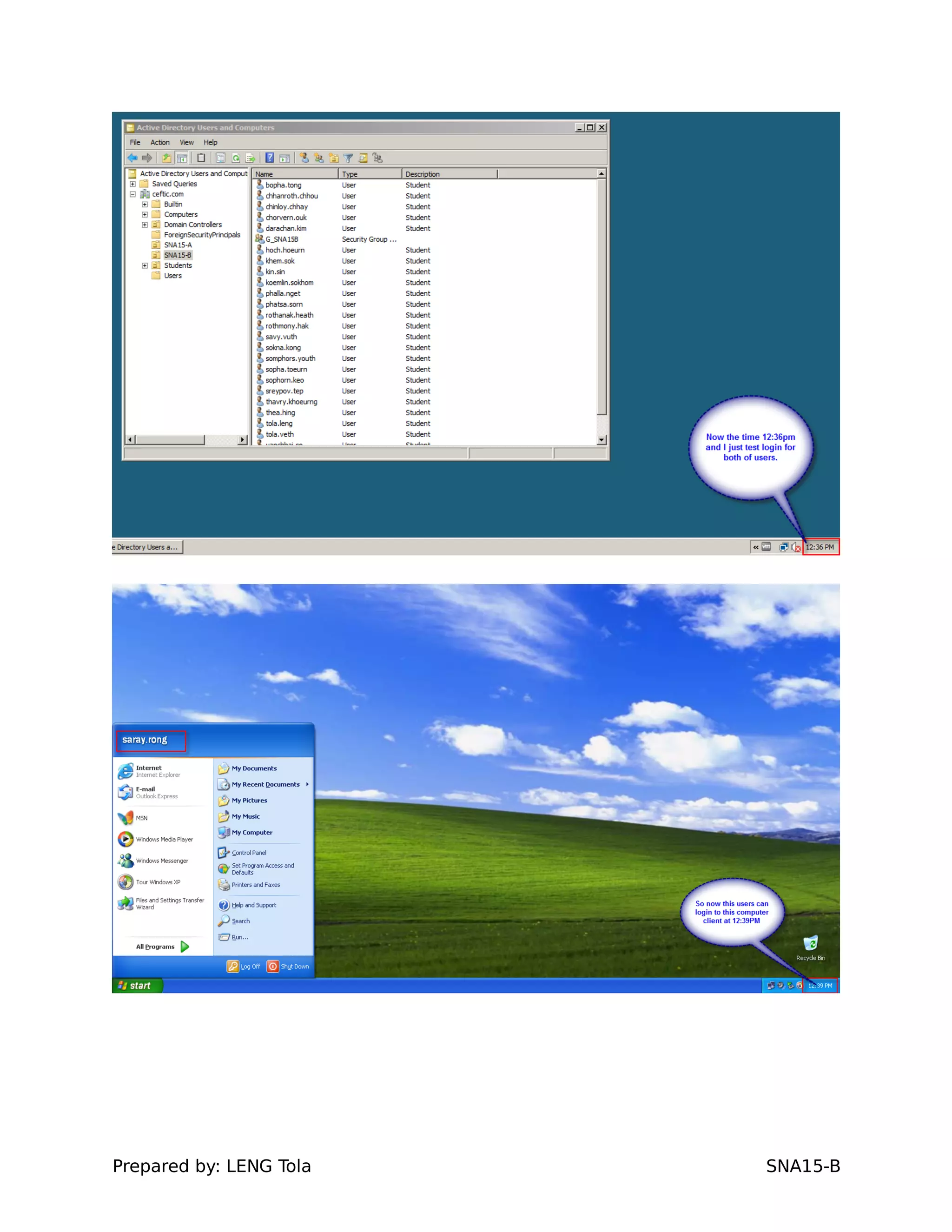
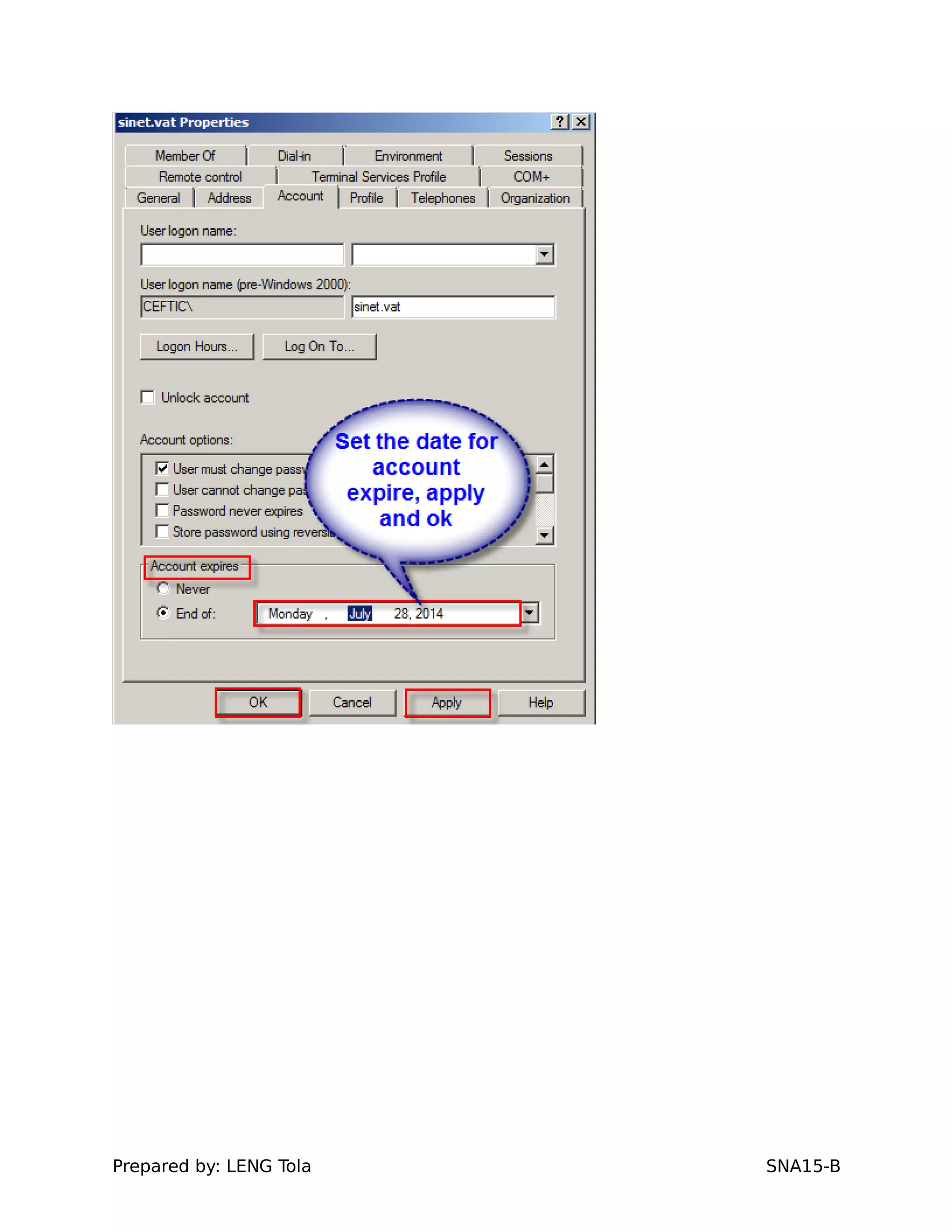
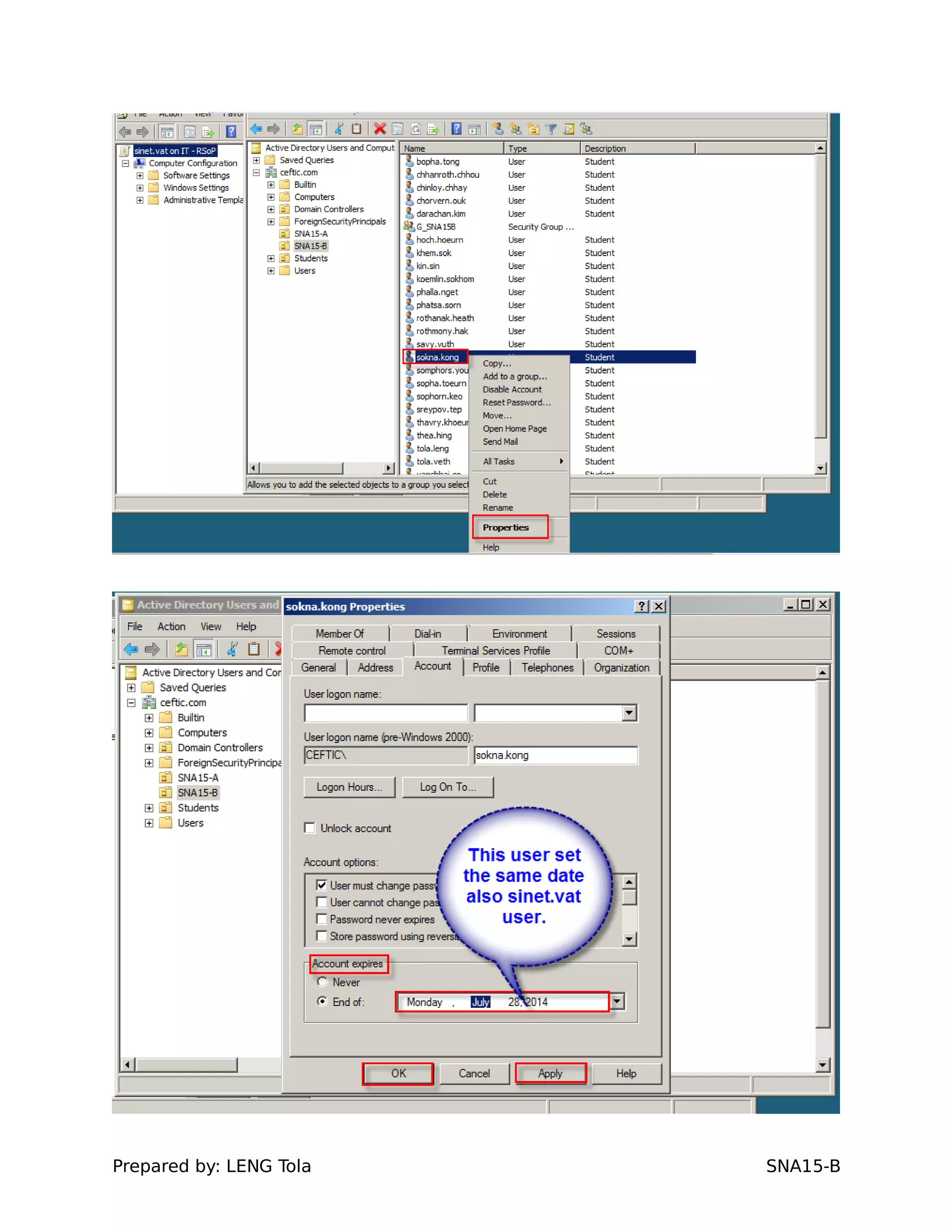
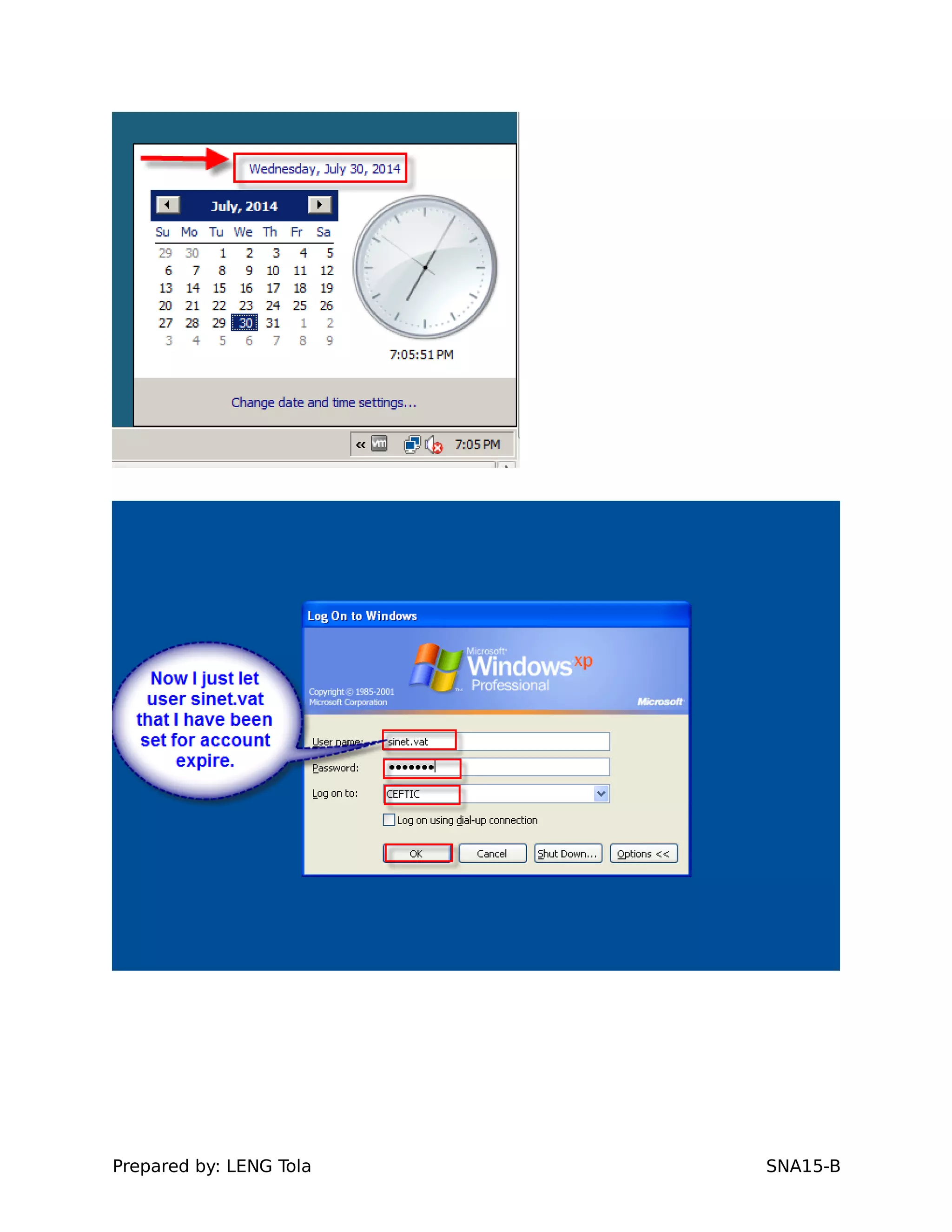
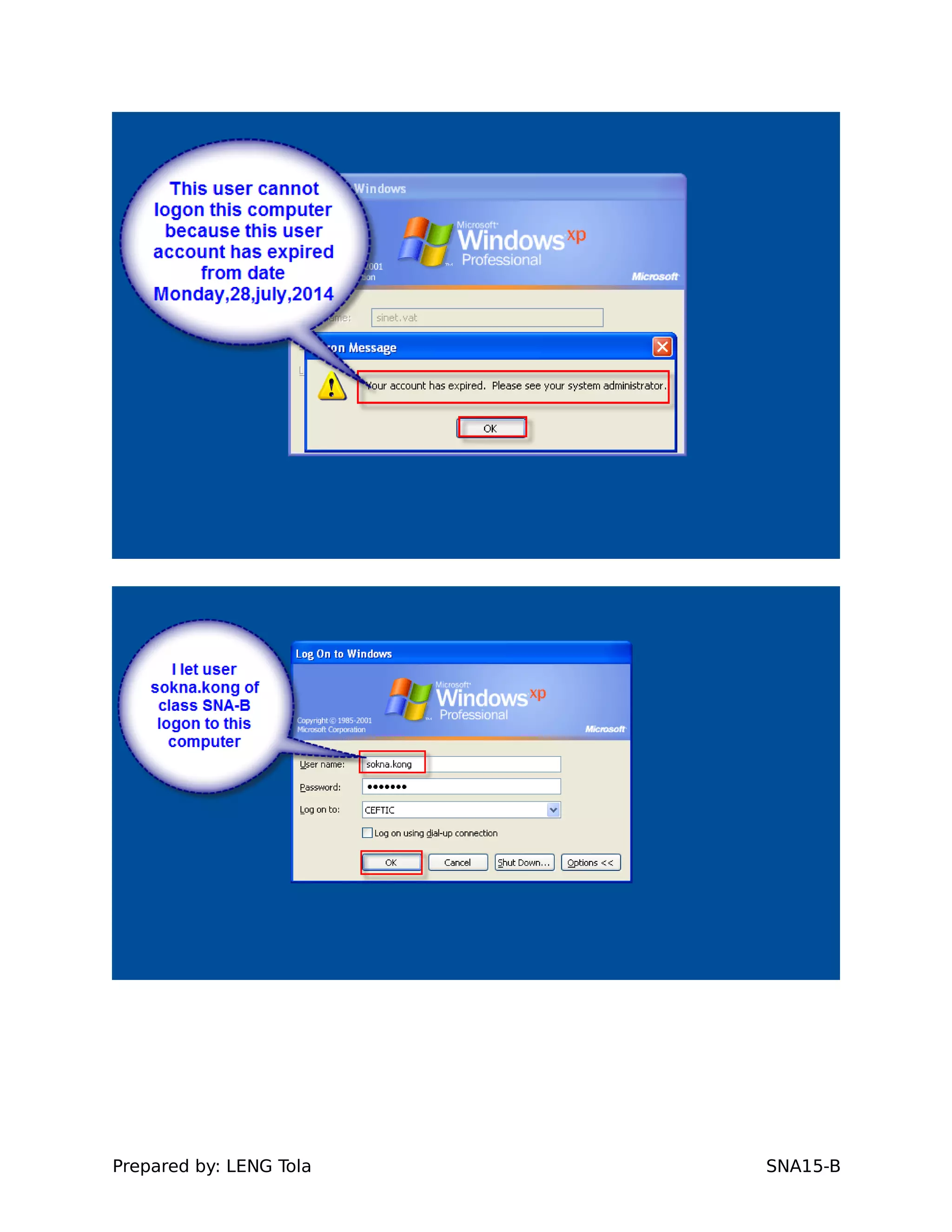
4. Setting user profile and login restrictions
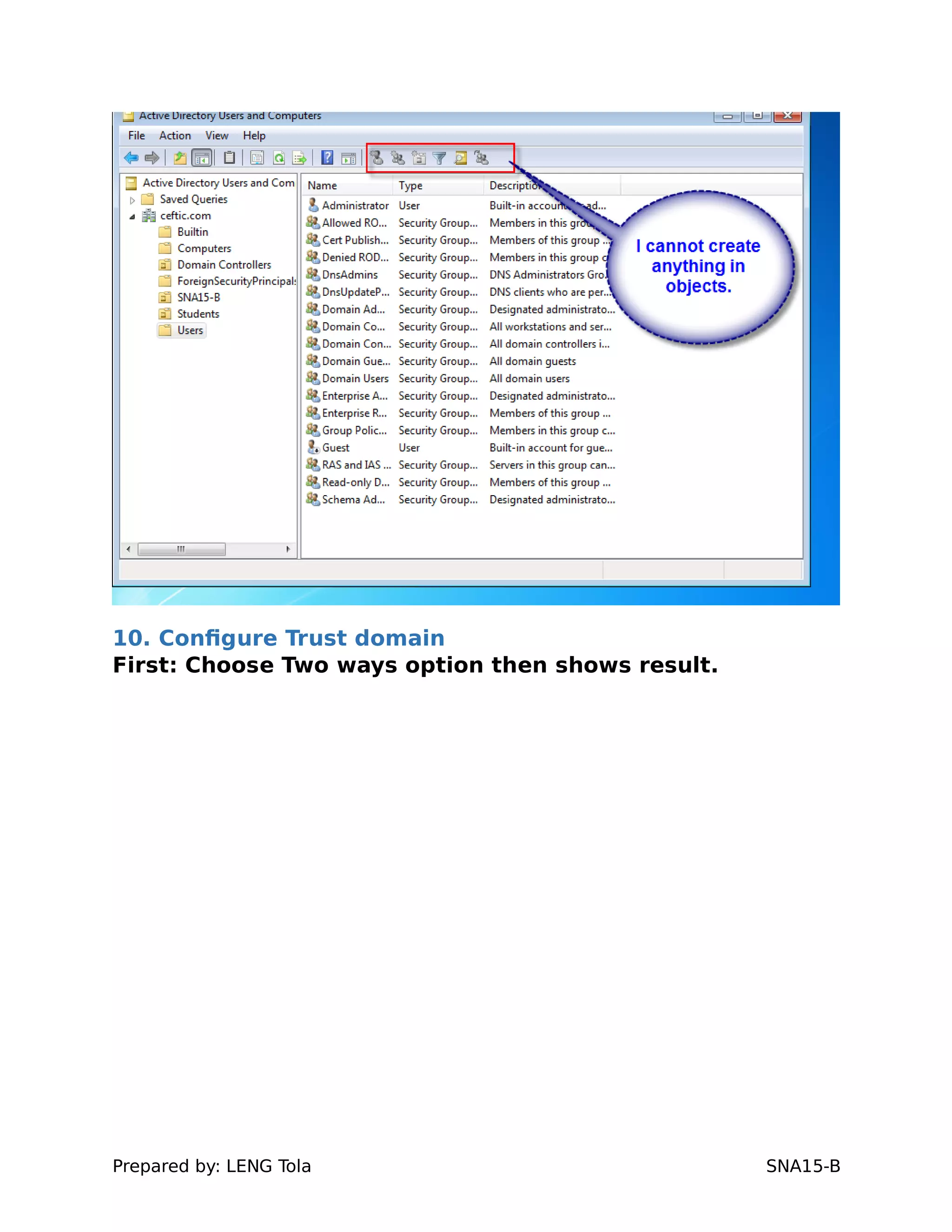
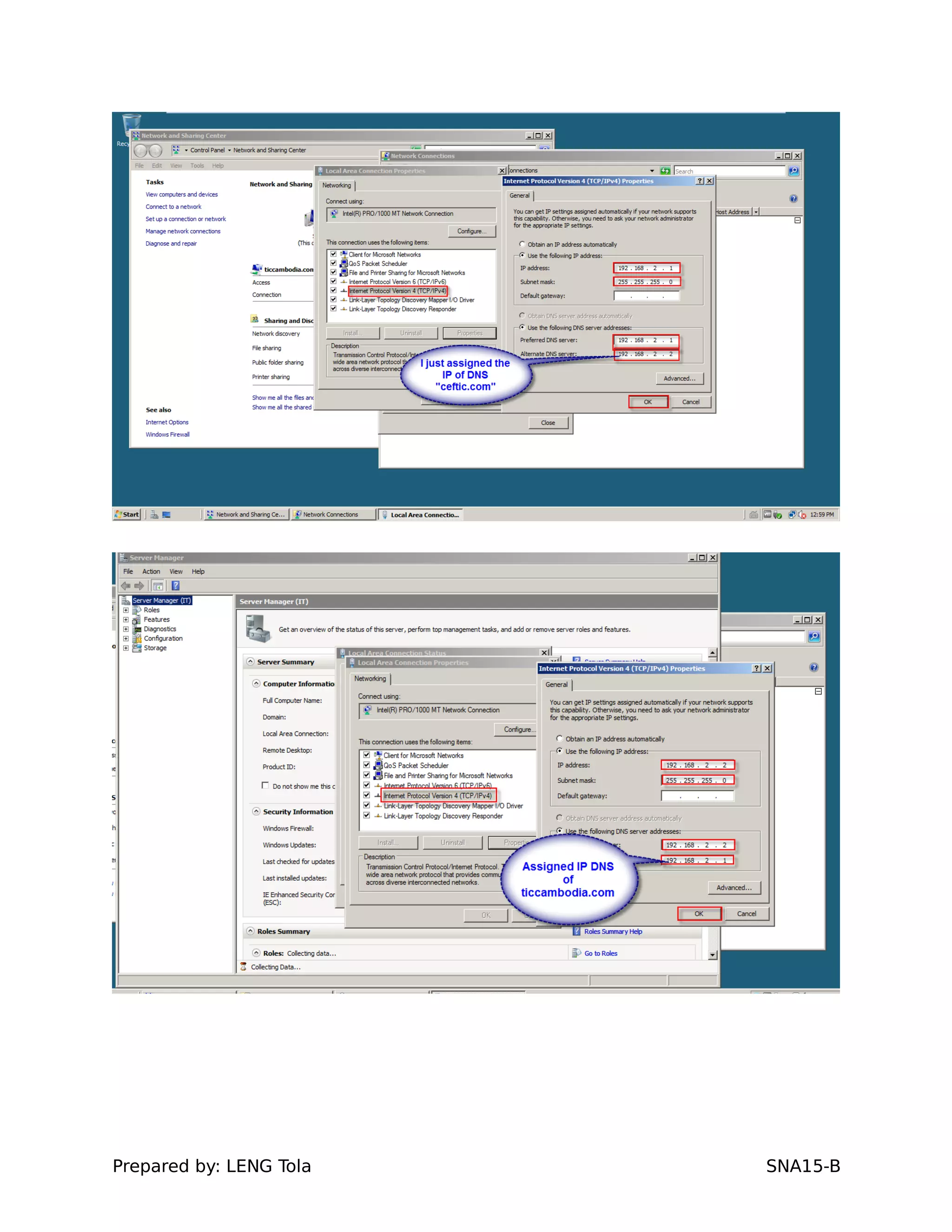
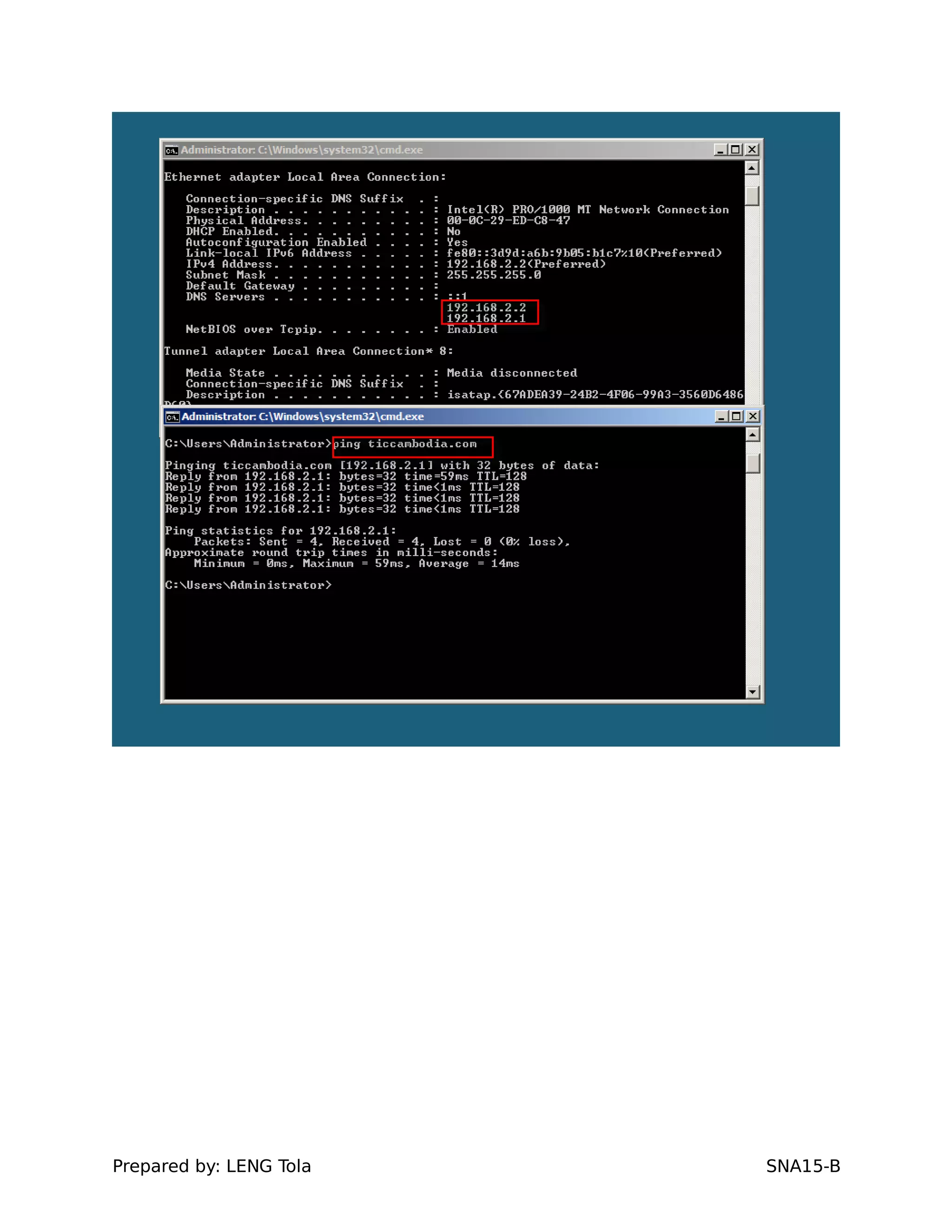
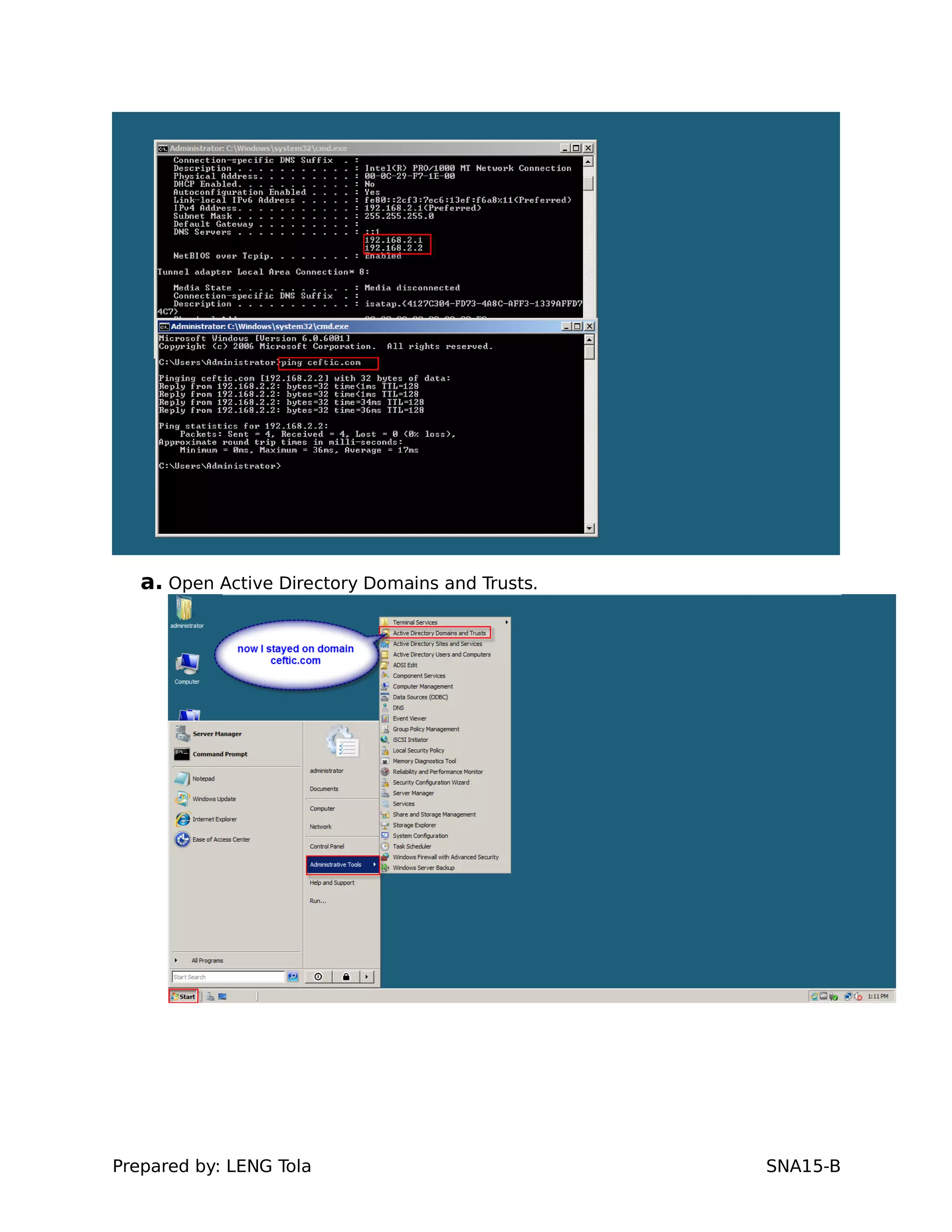
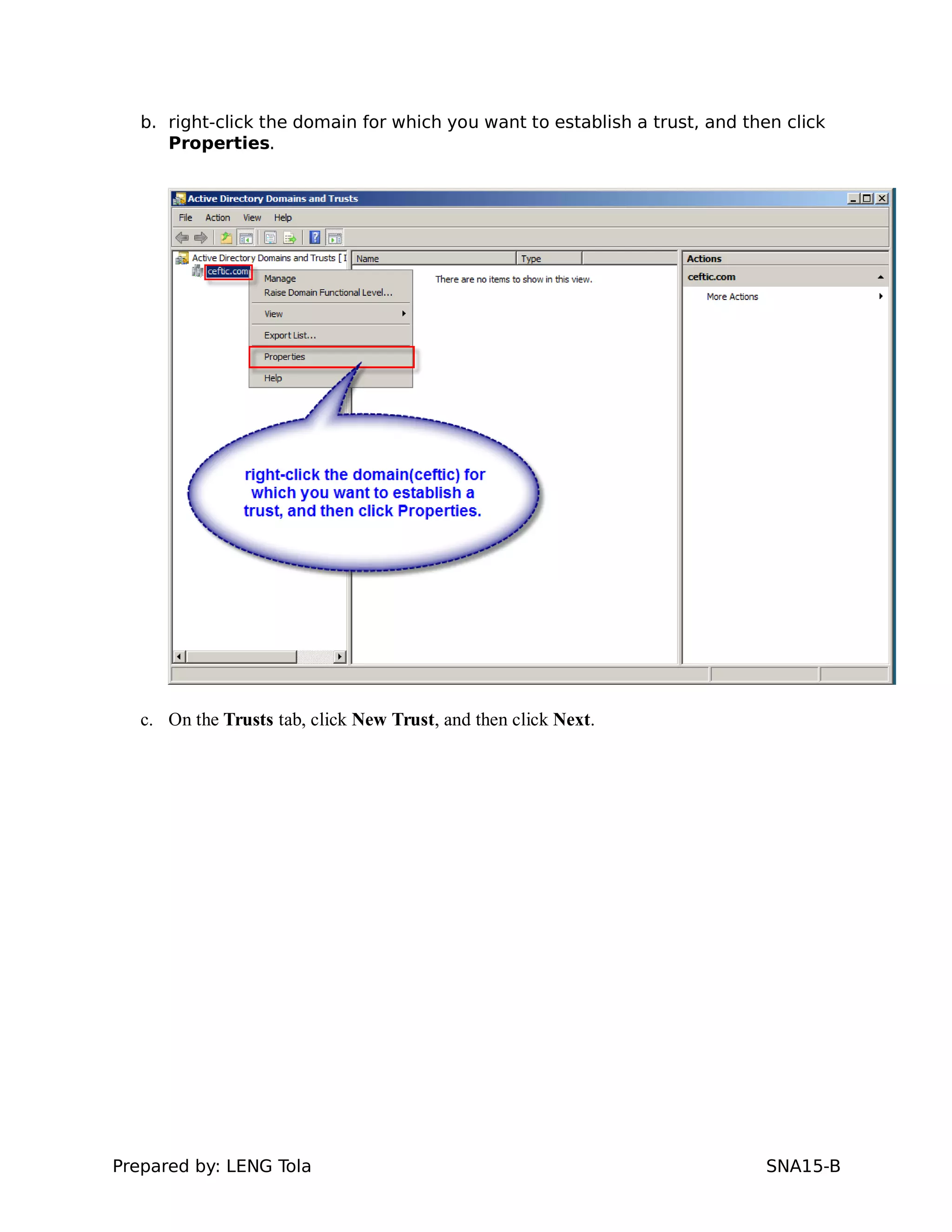
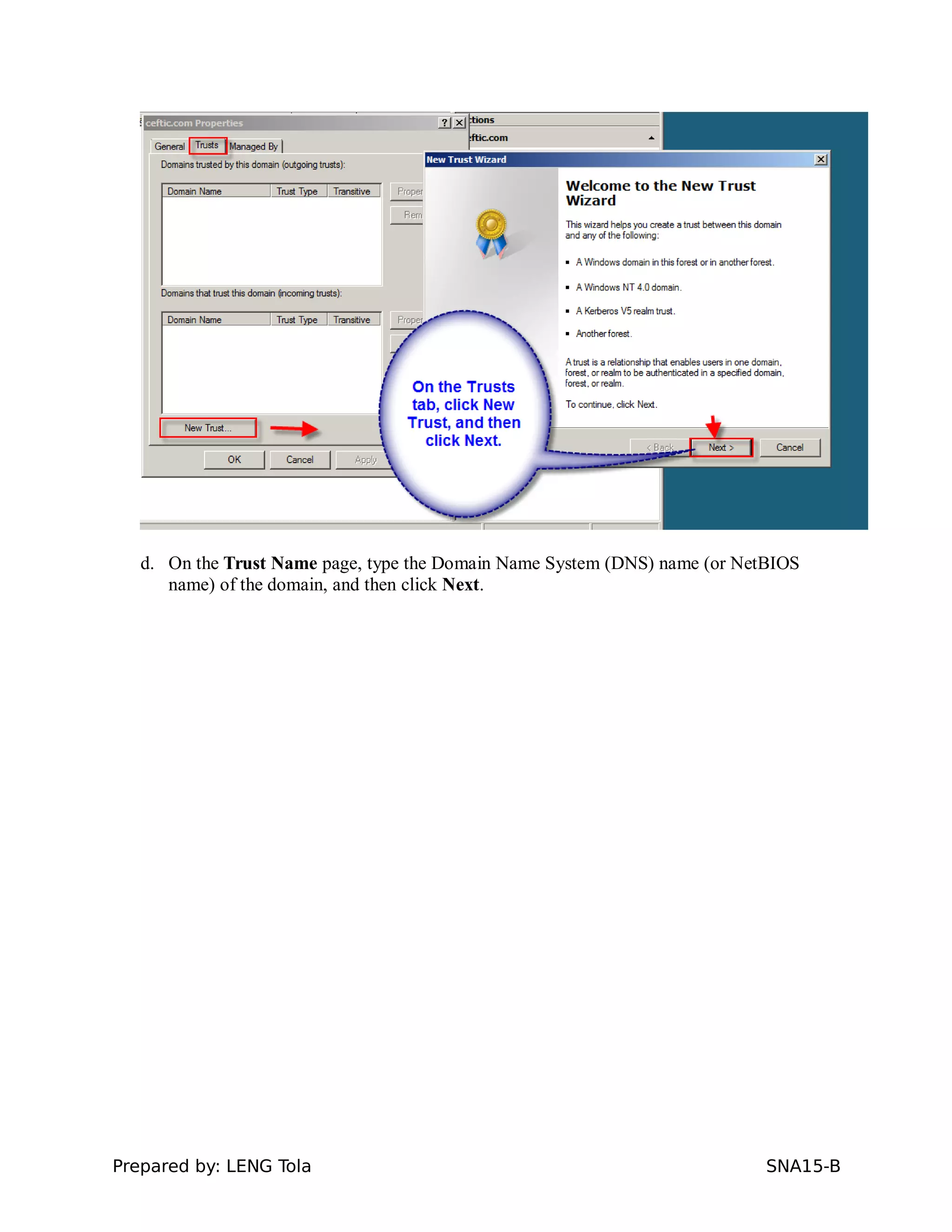
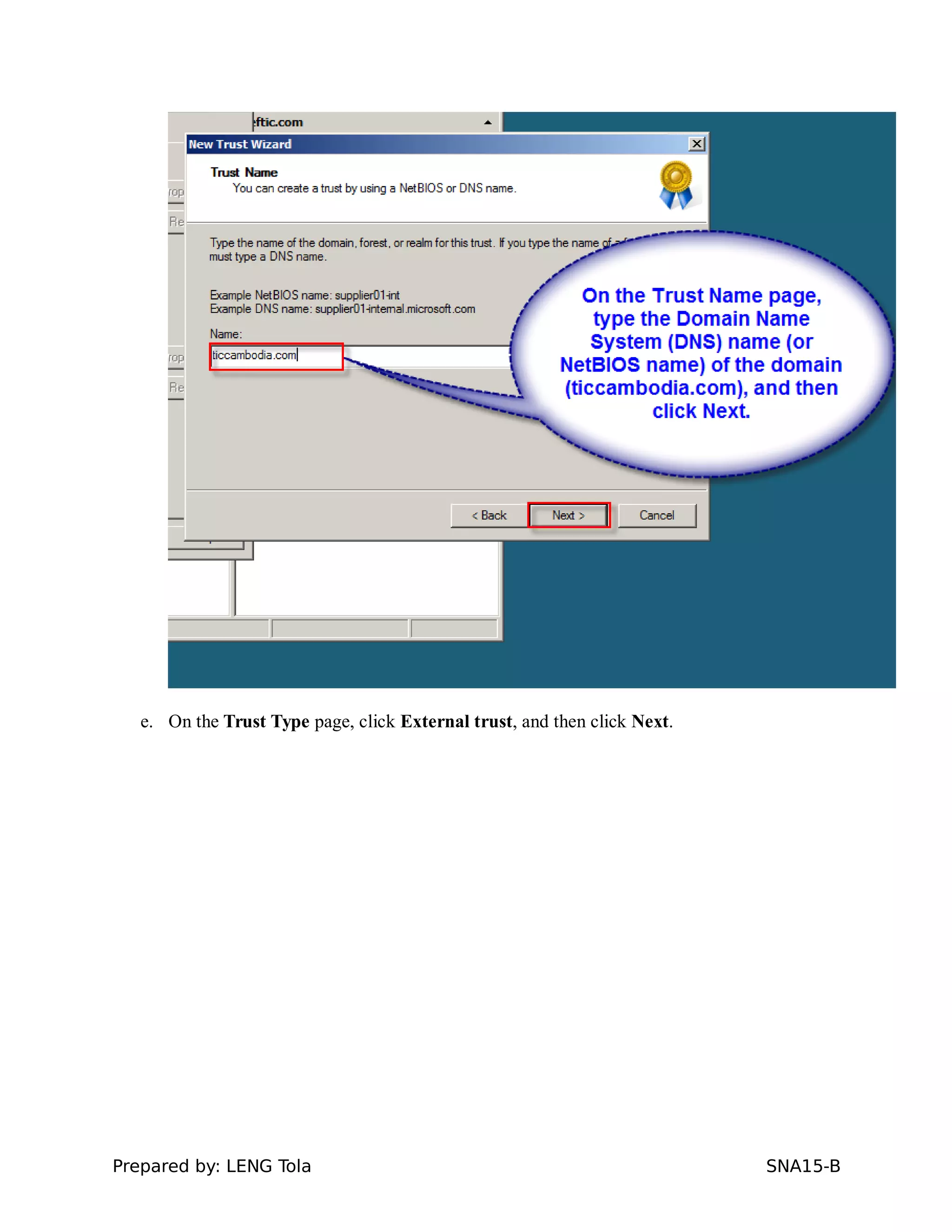
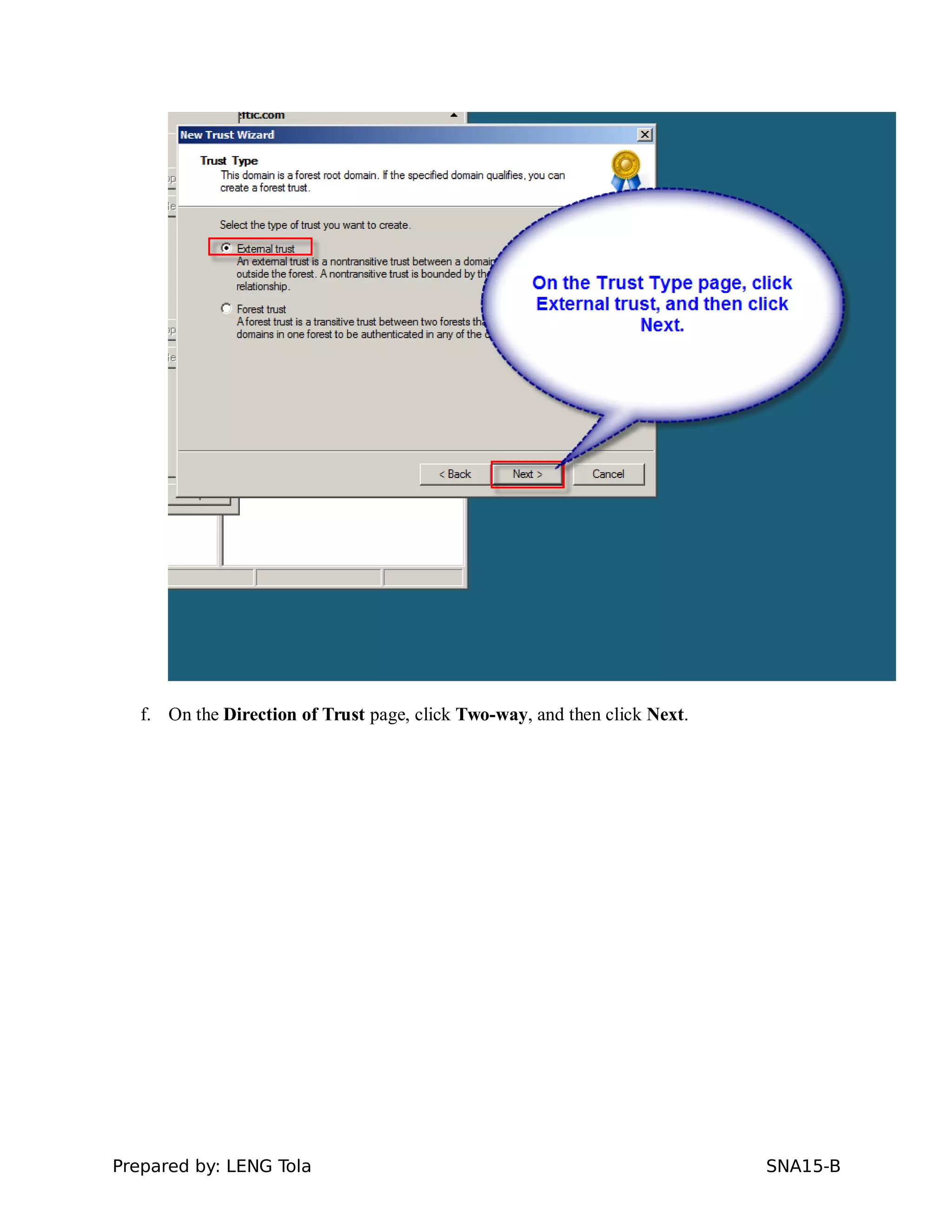
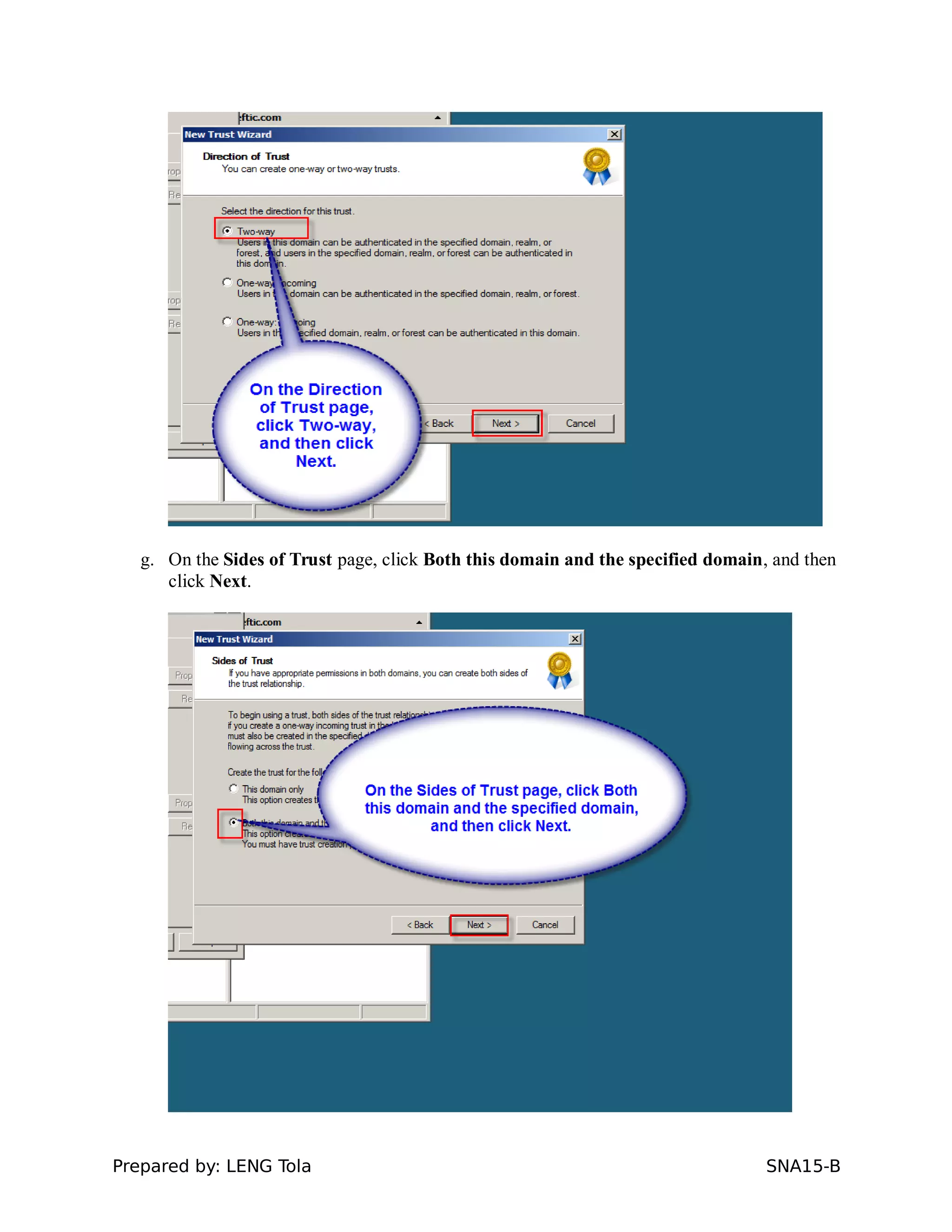
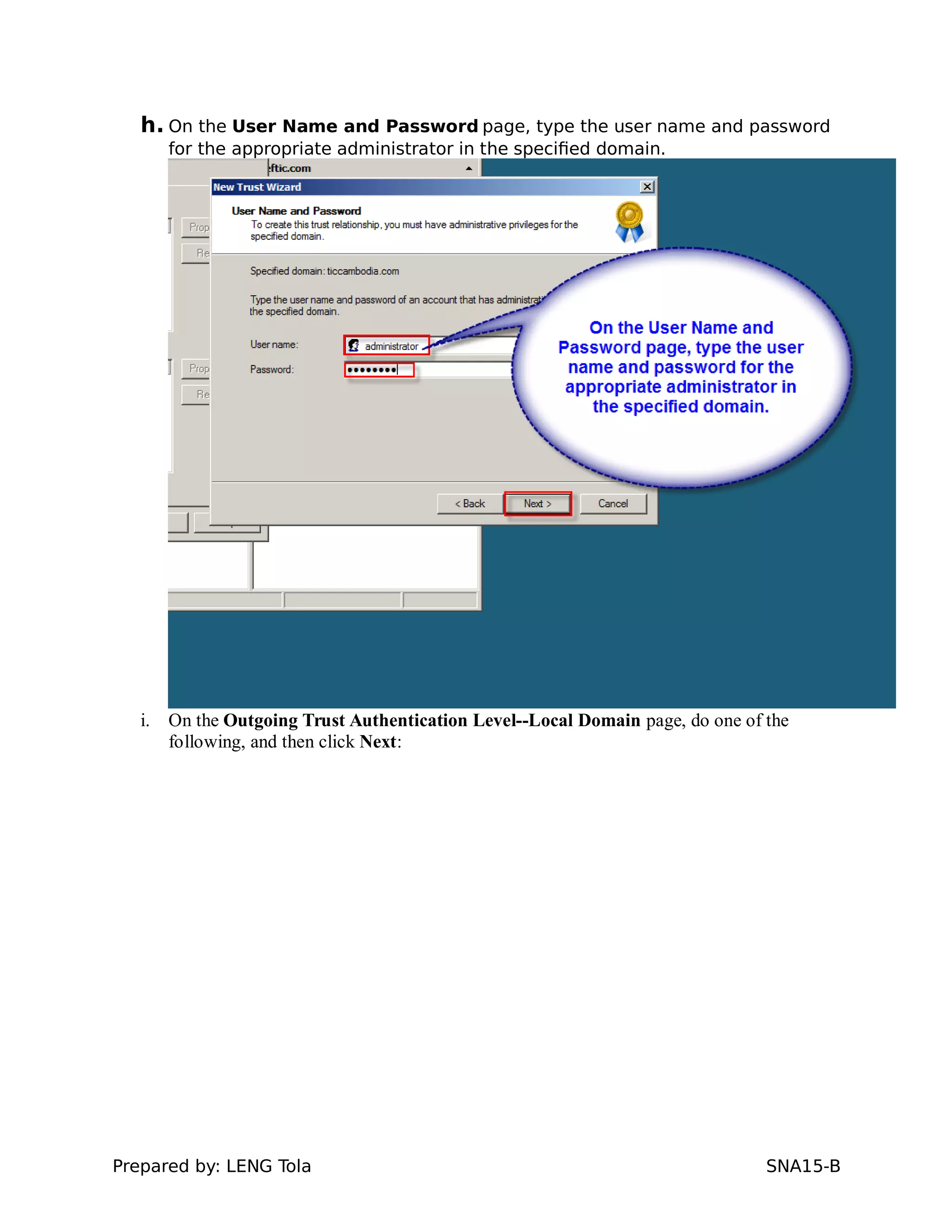
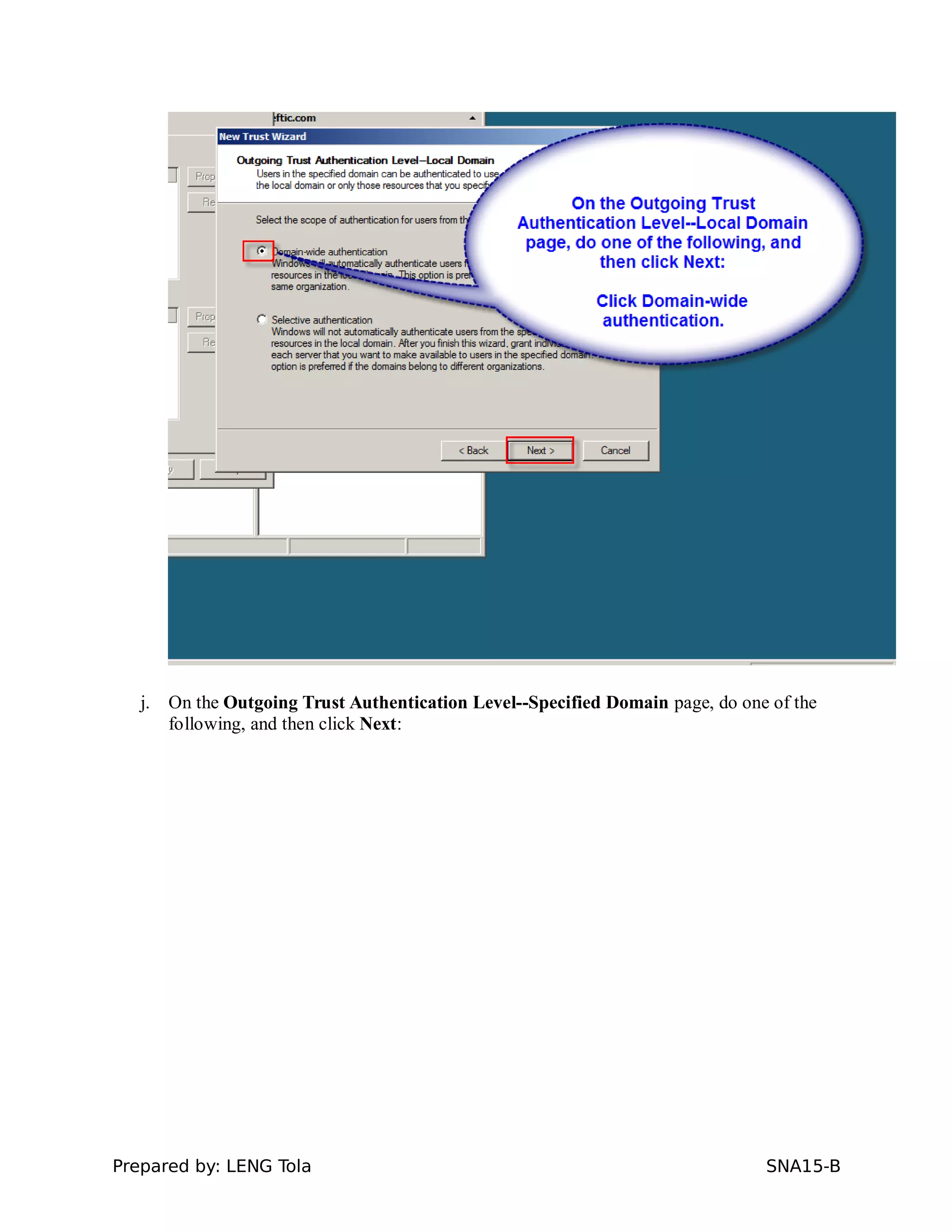
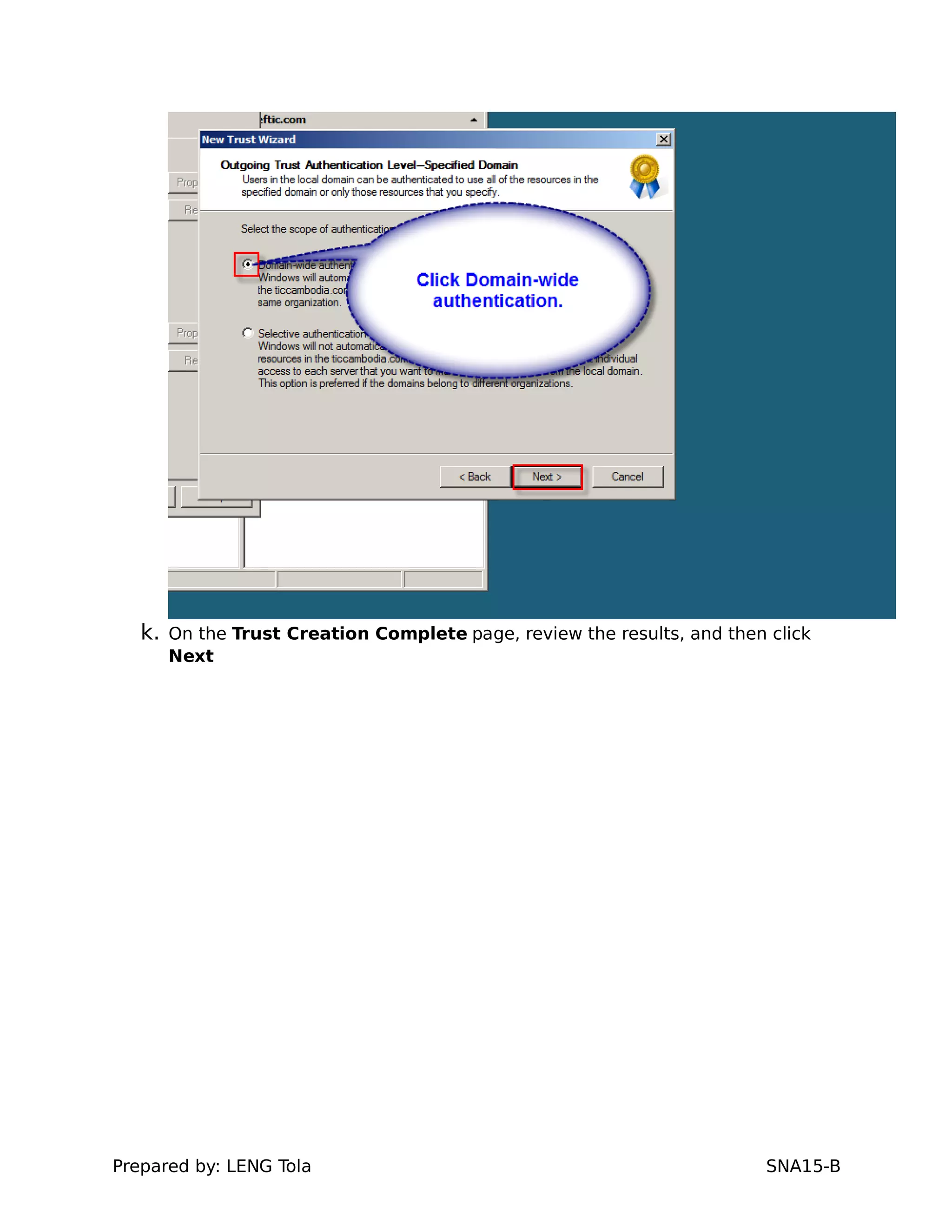
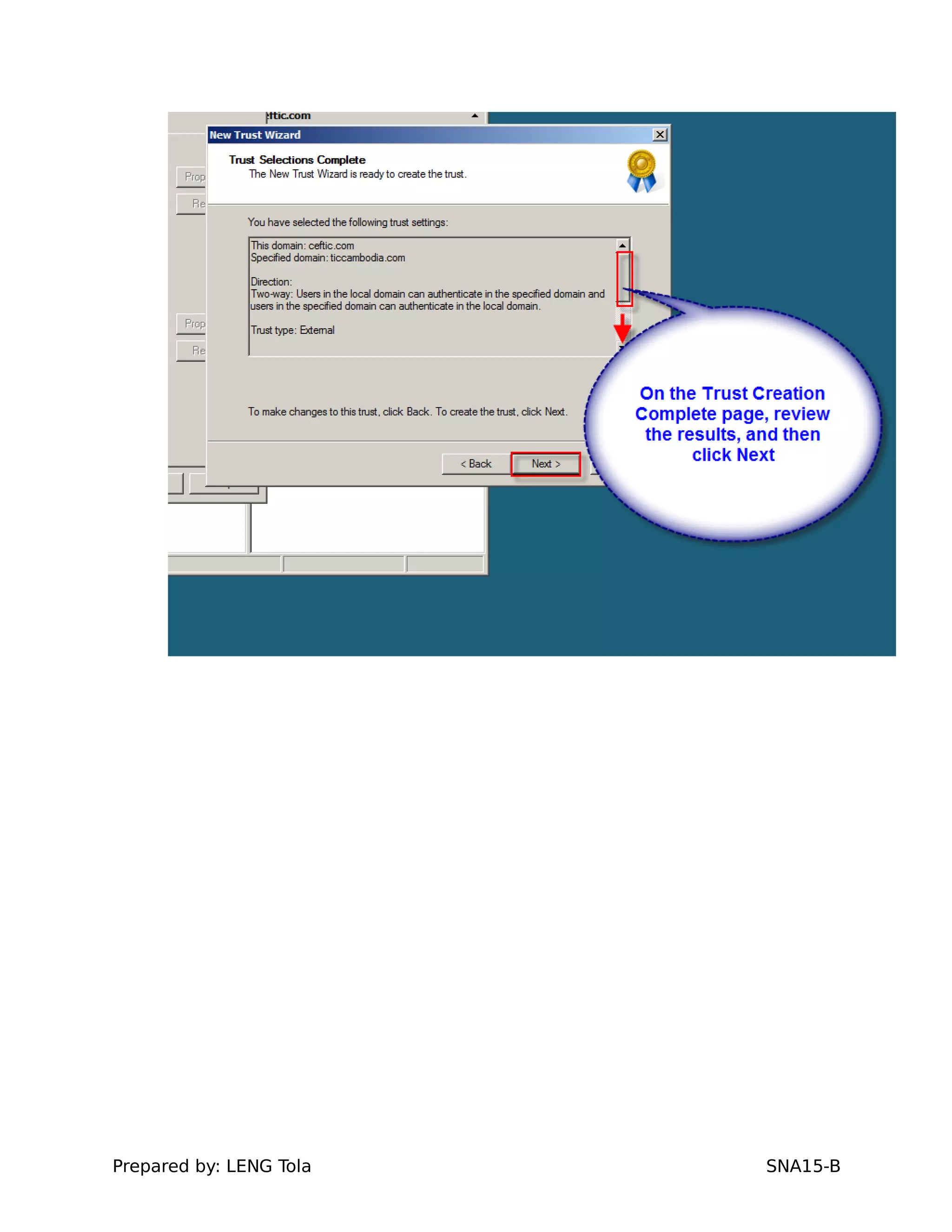
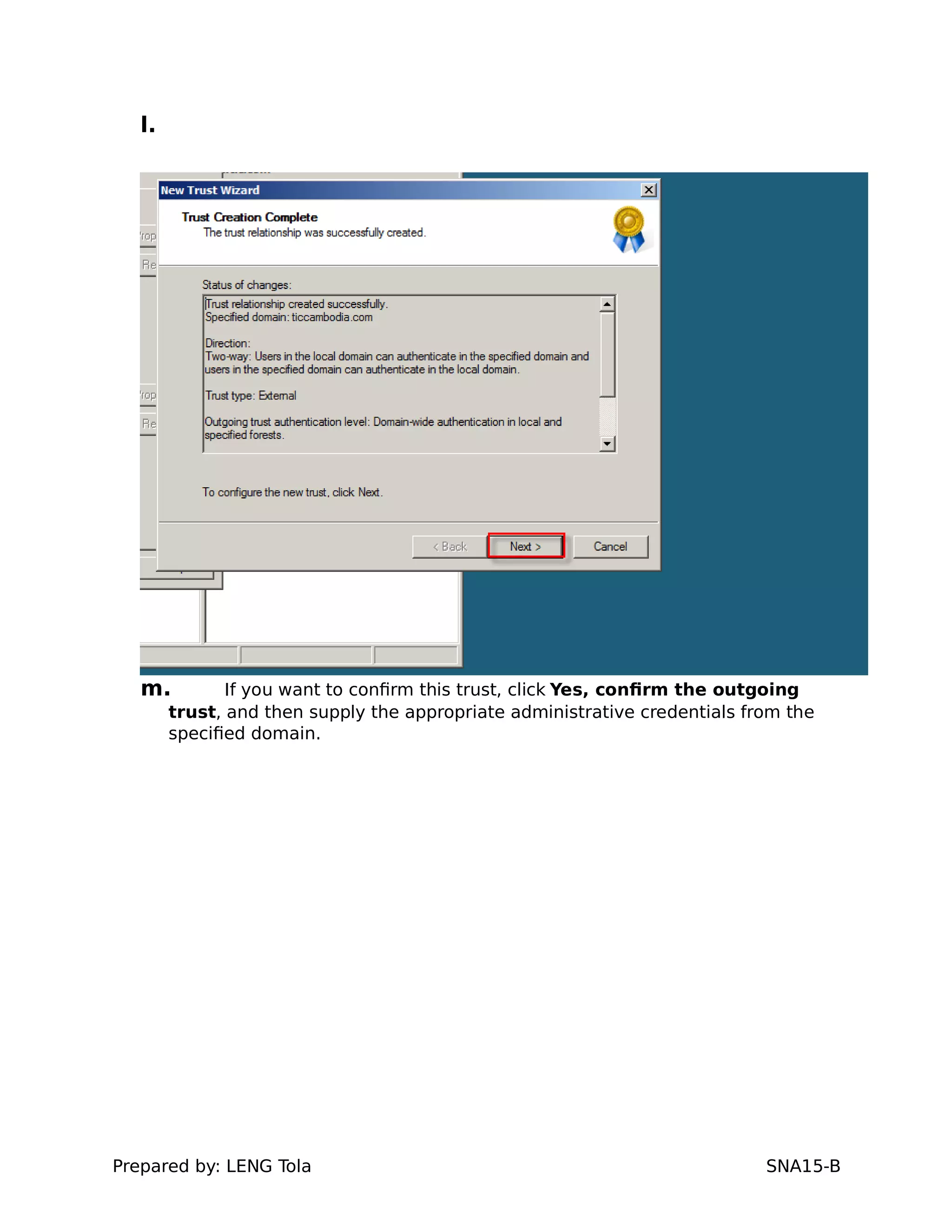
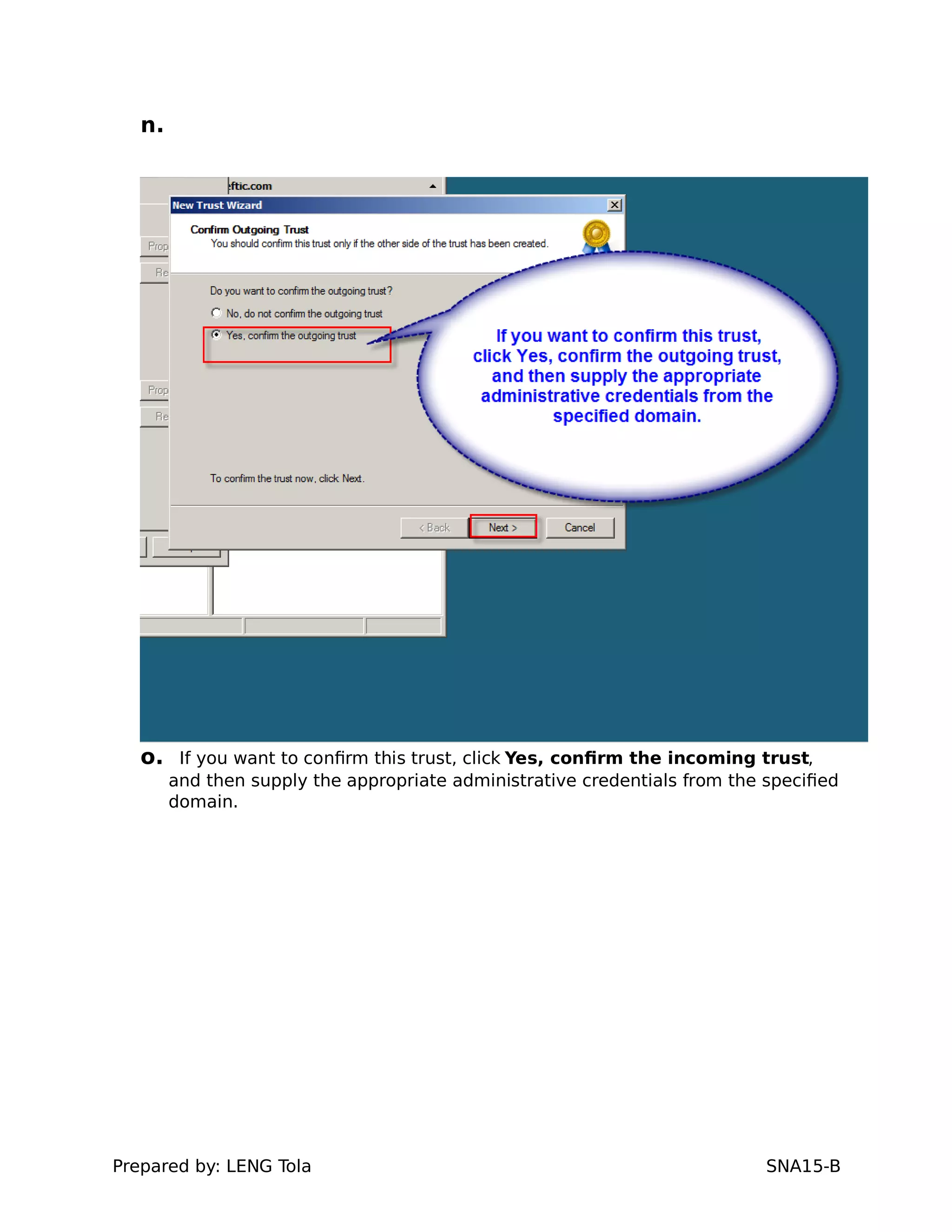
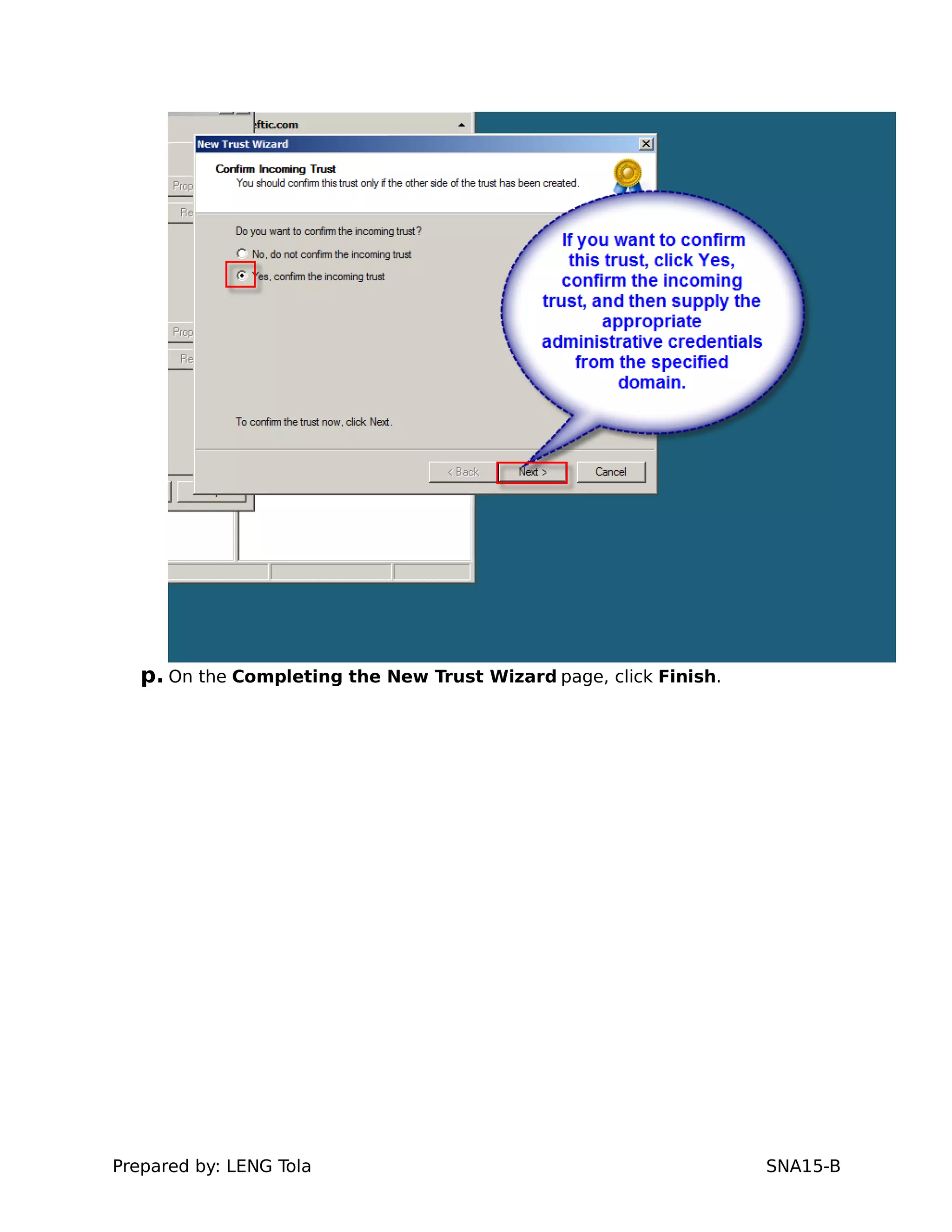
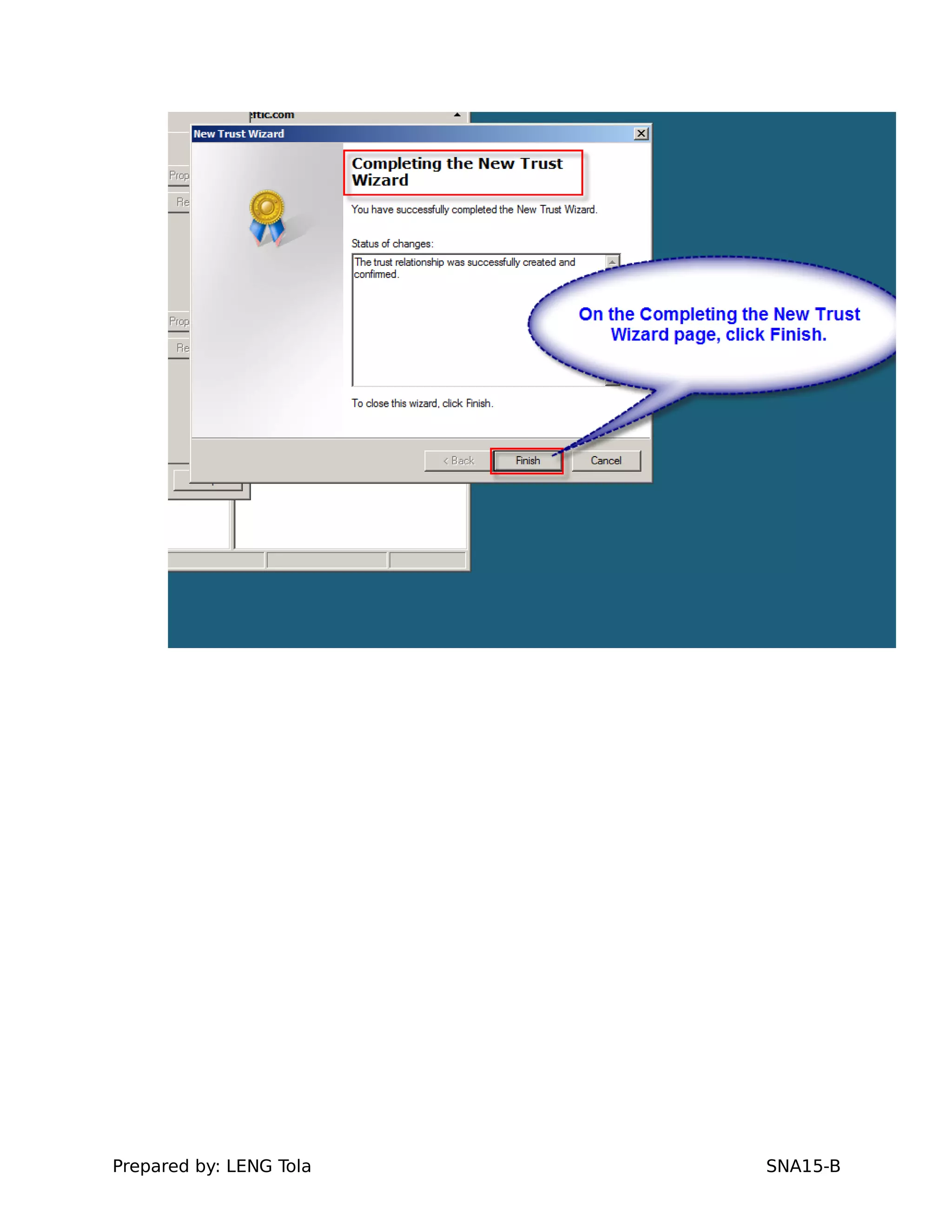
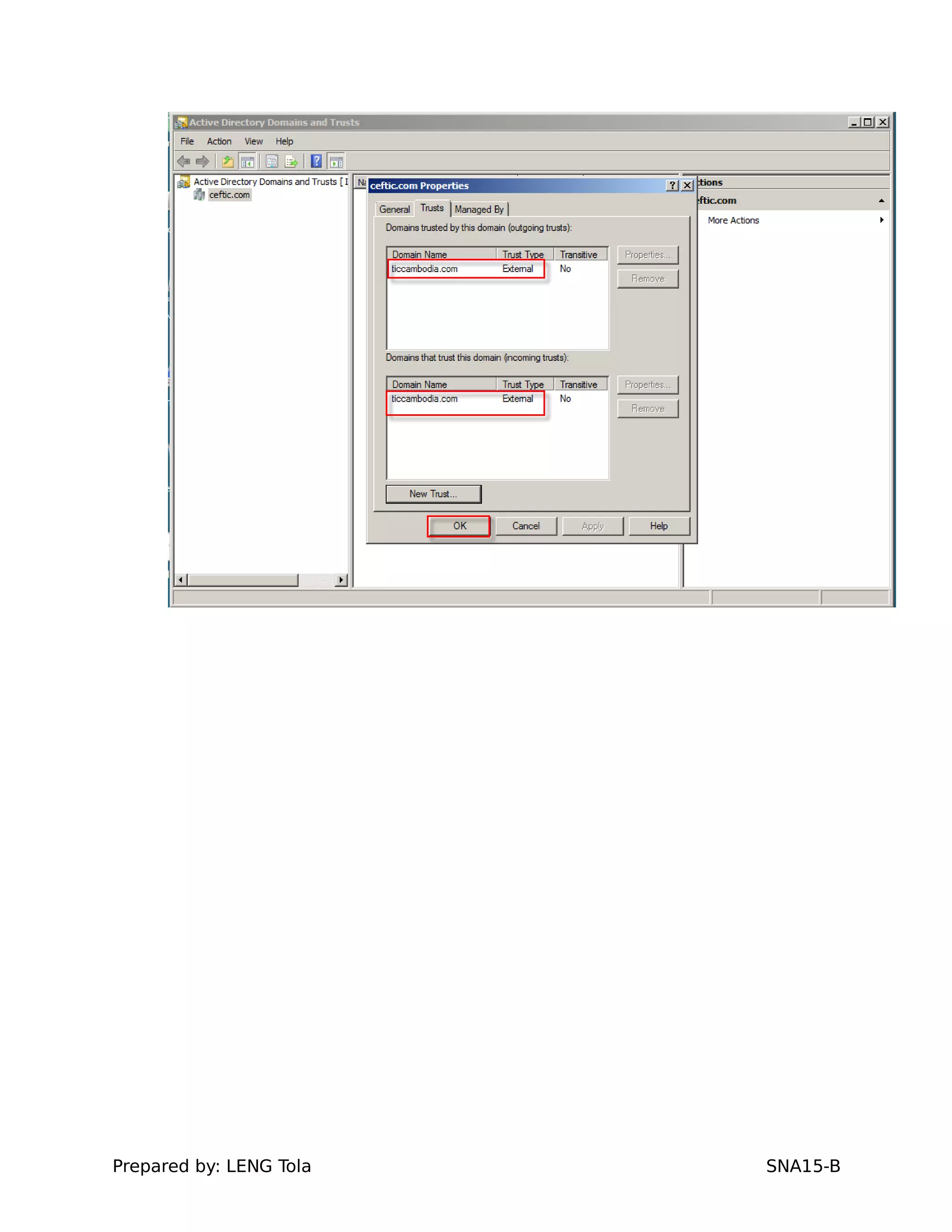
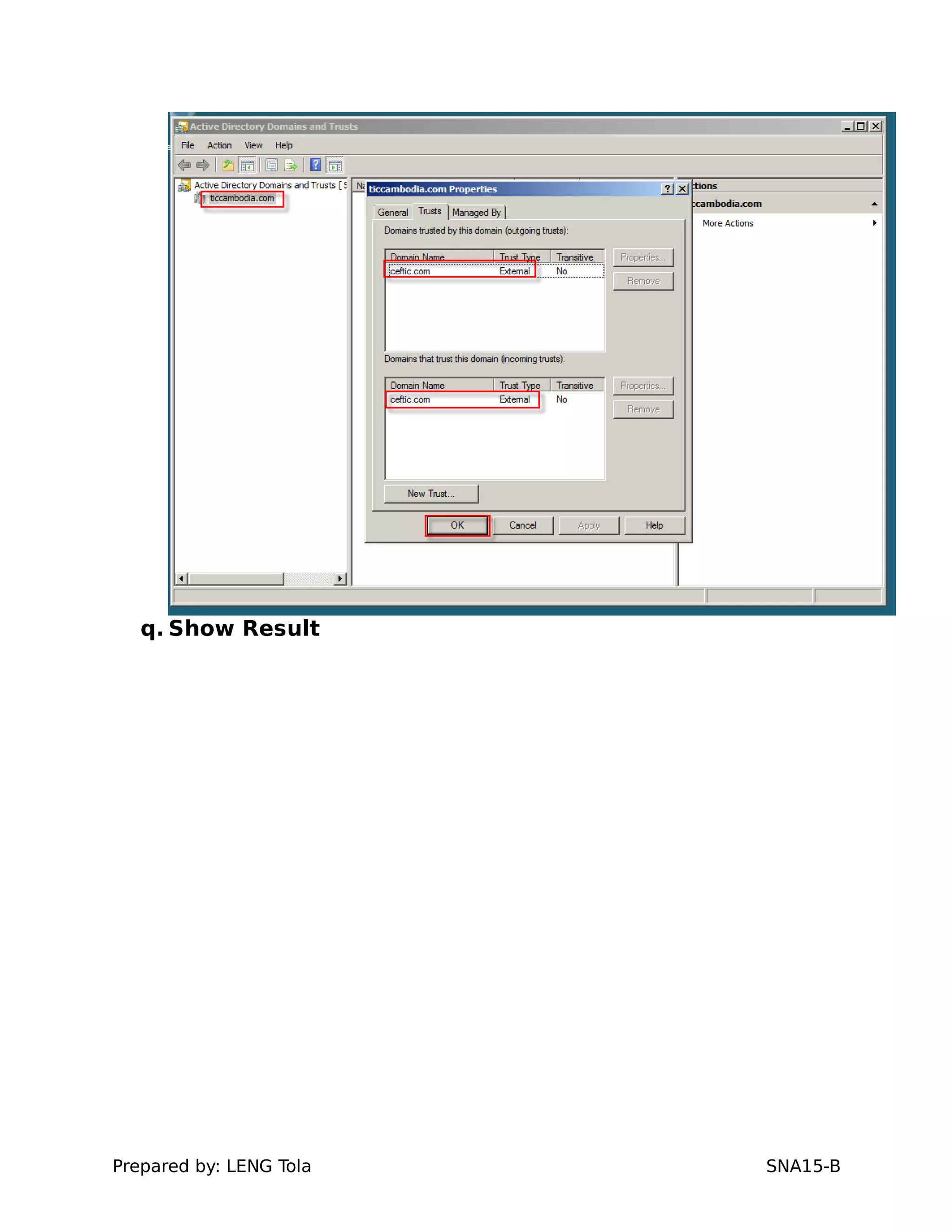
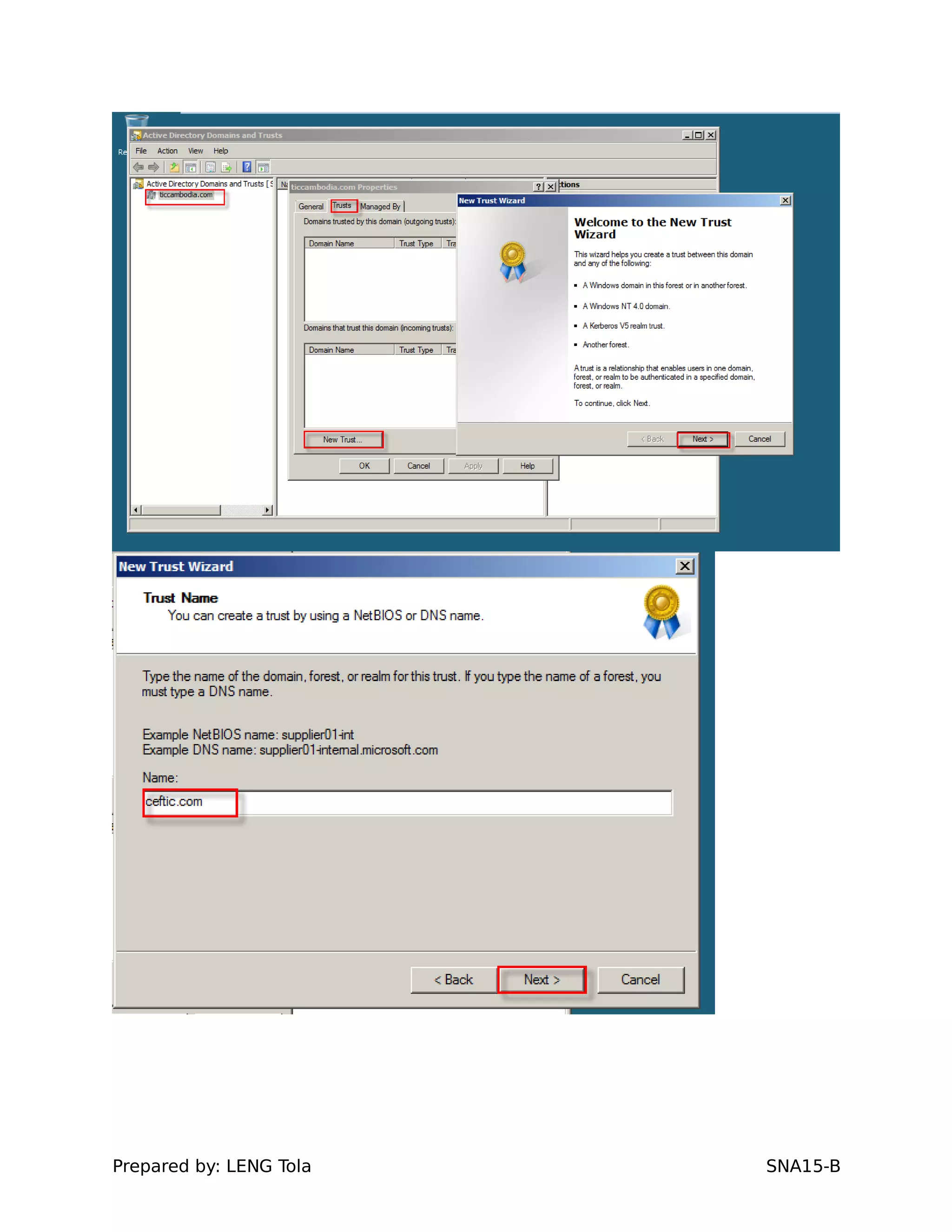
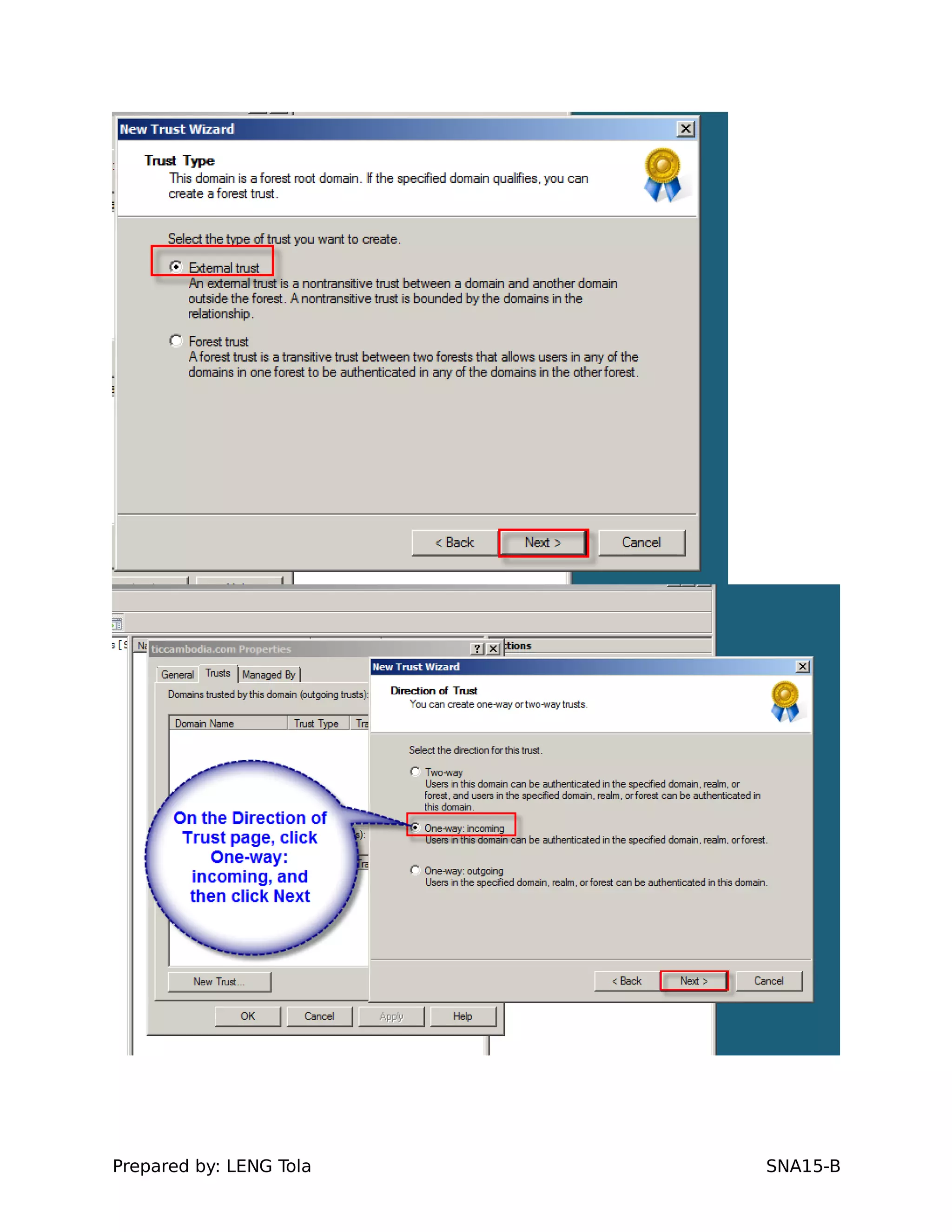
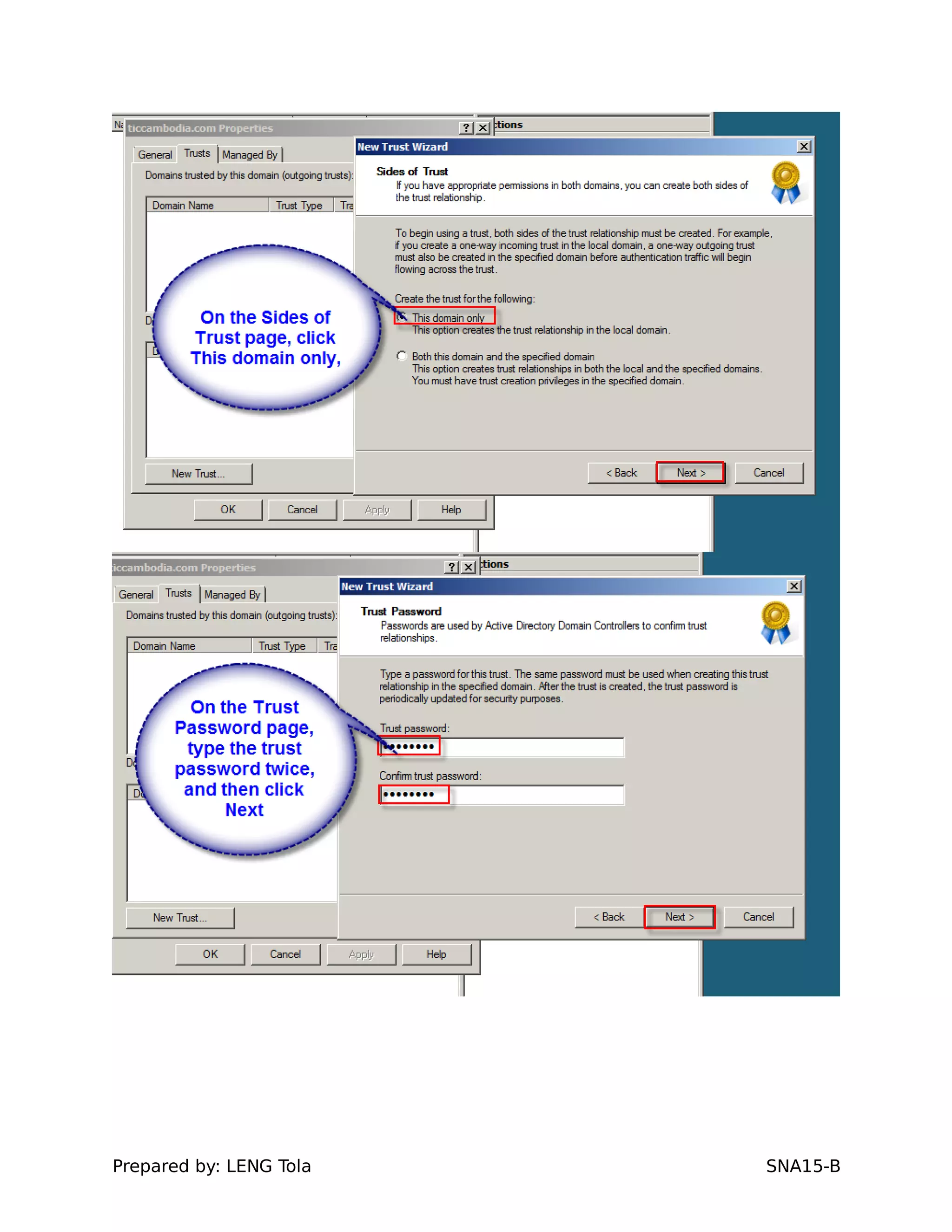
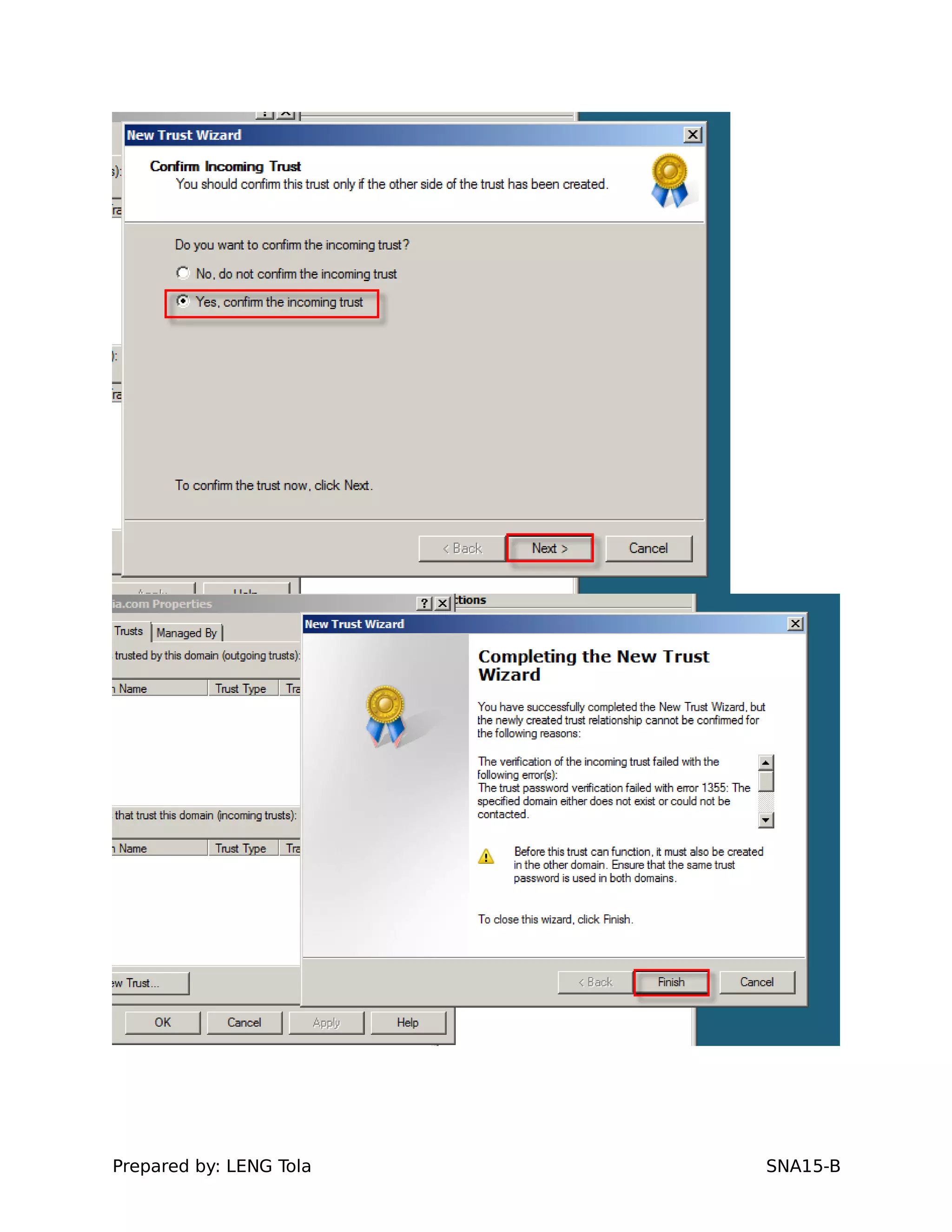
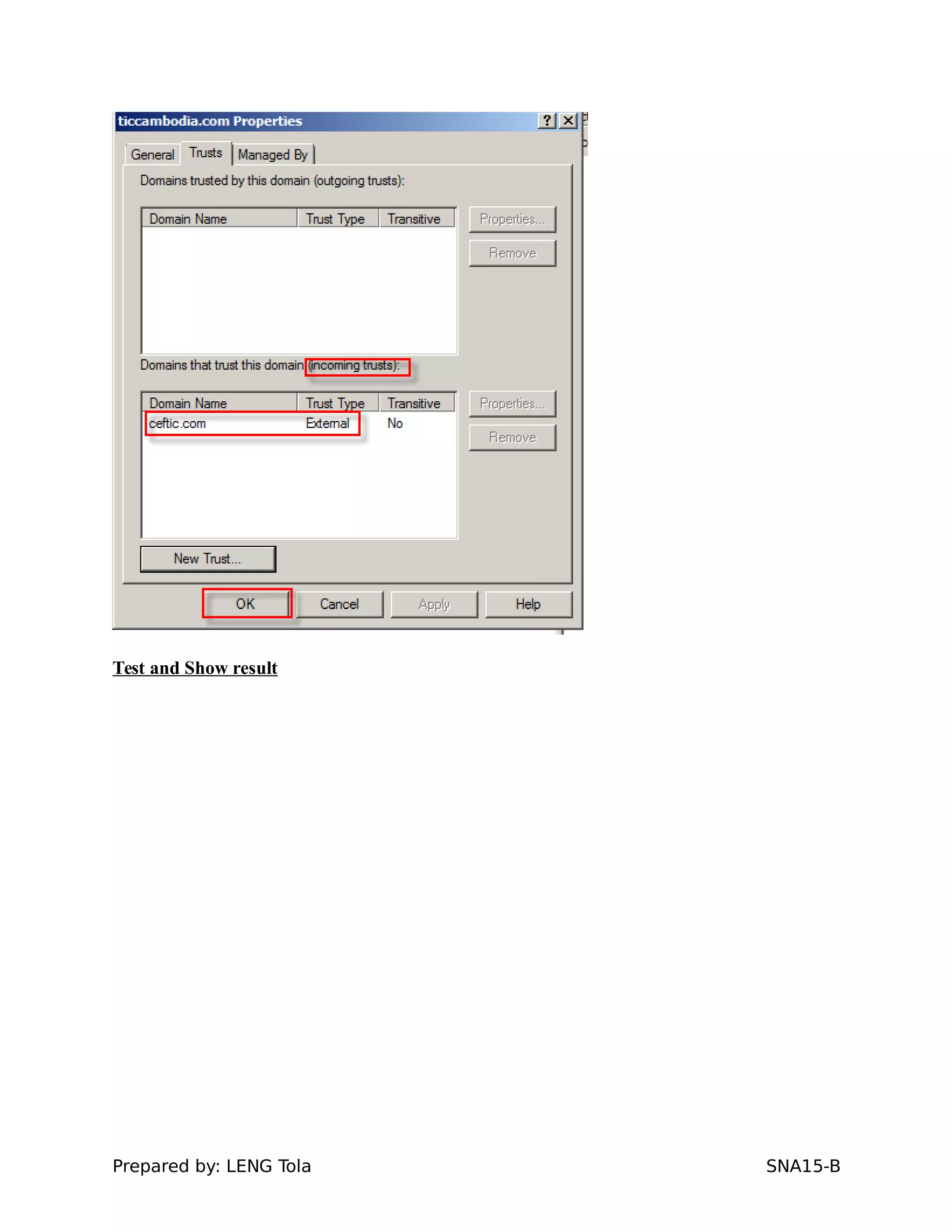
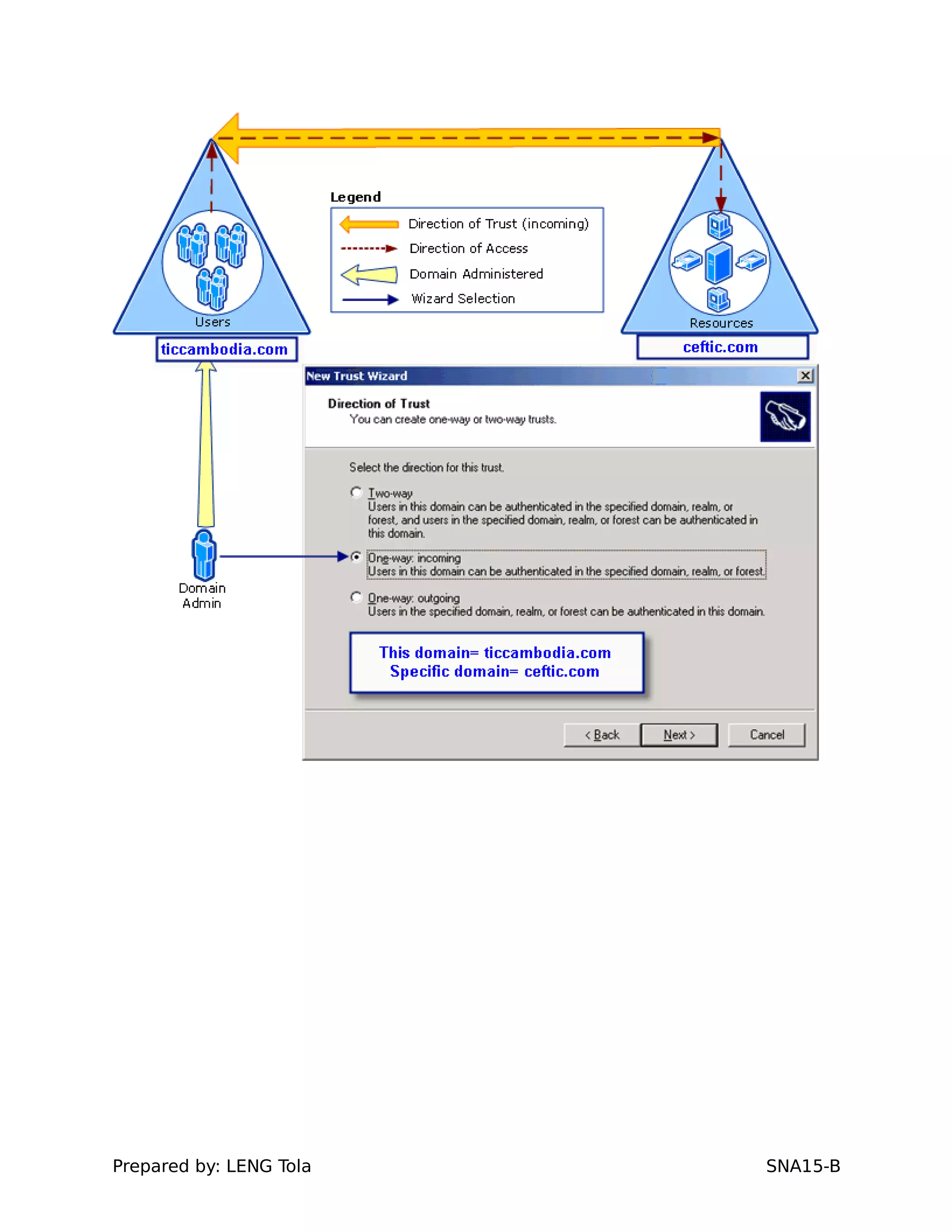
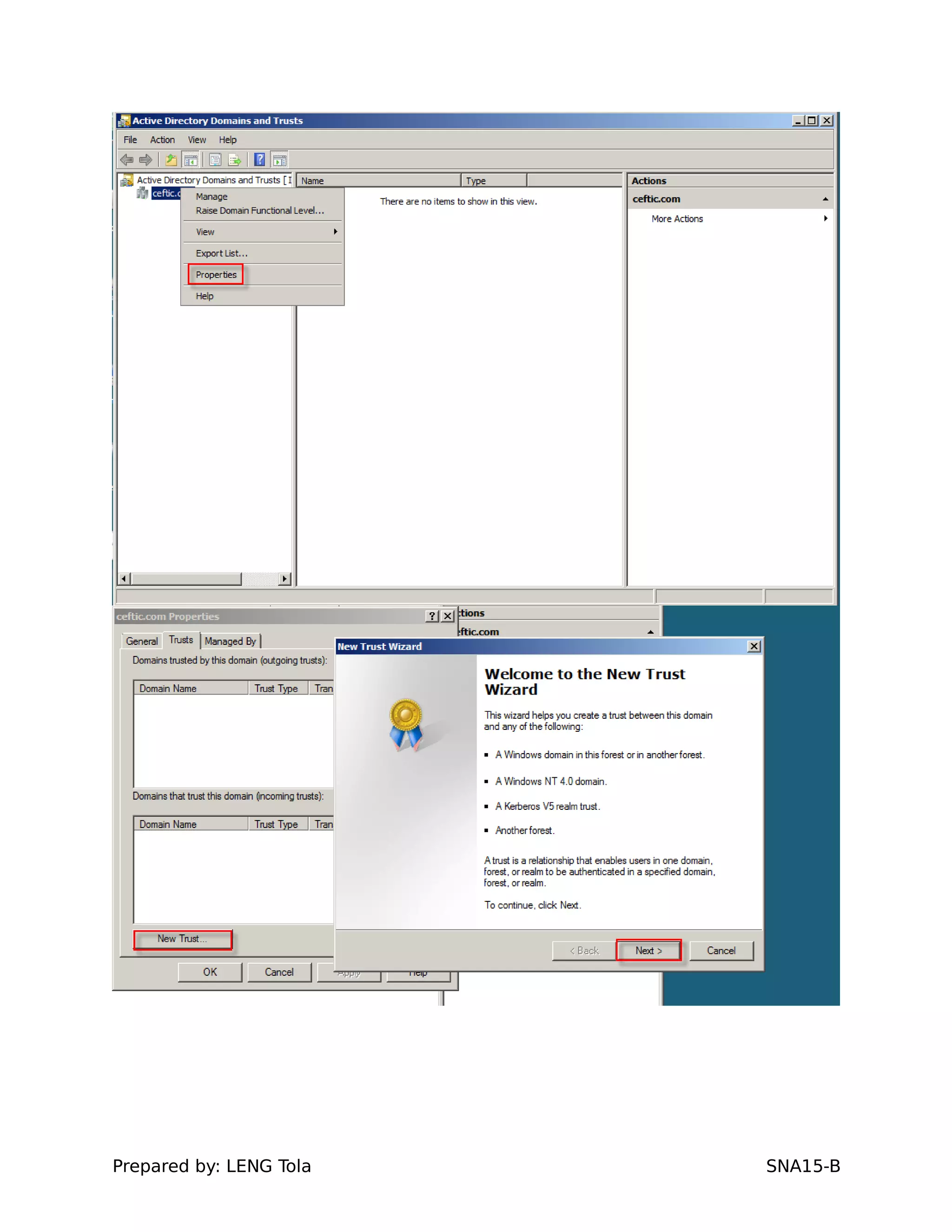
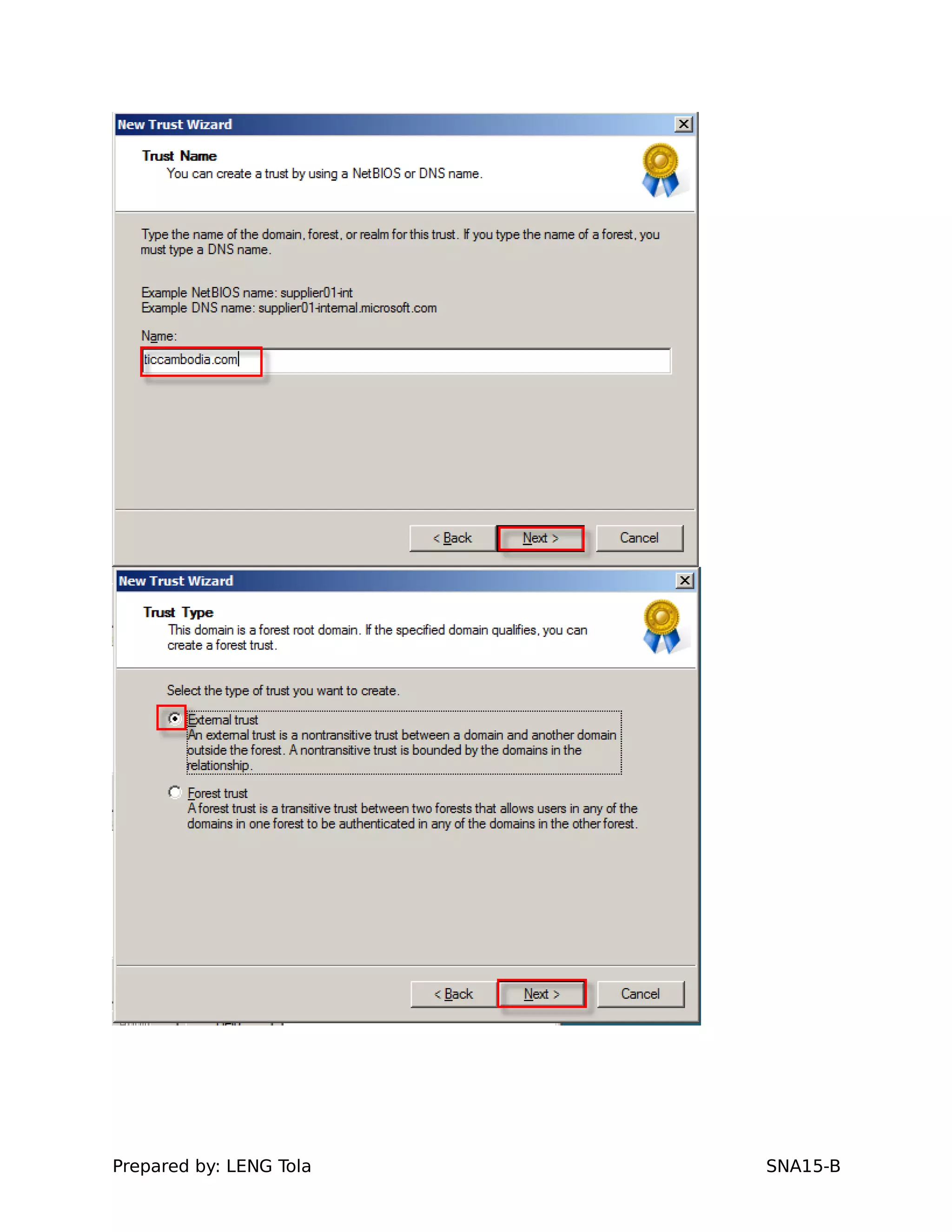
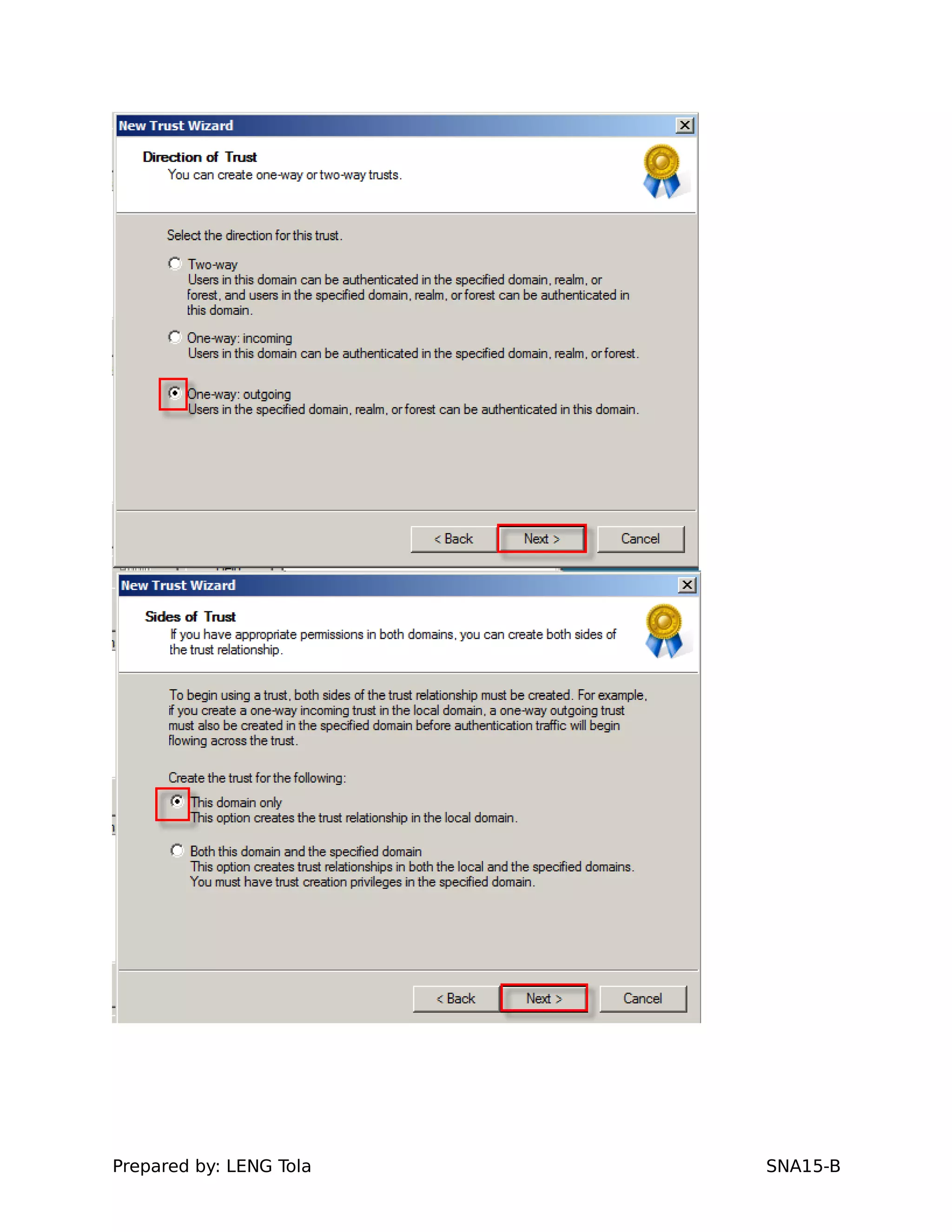
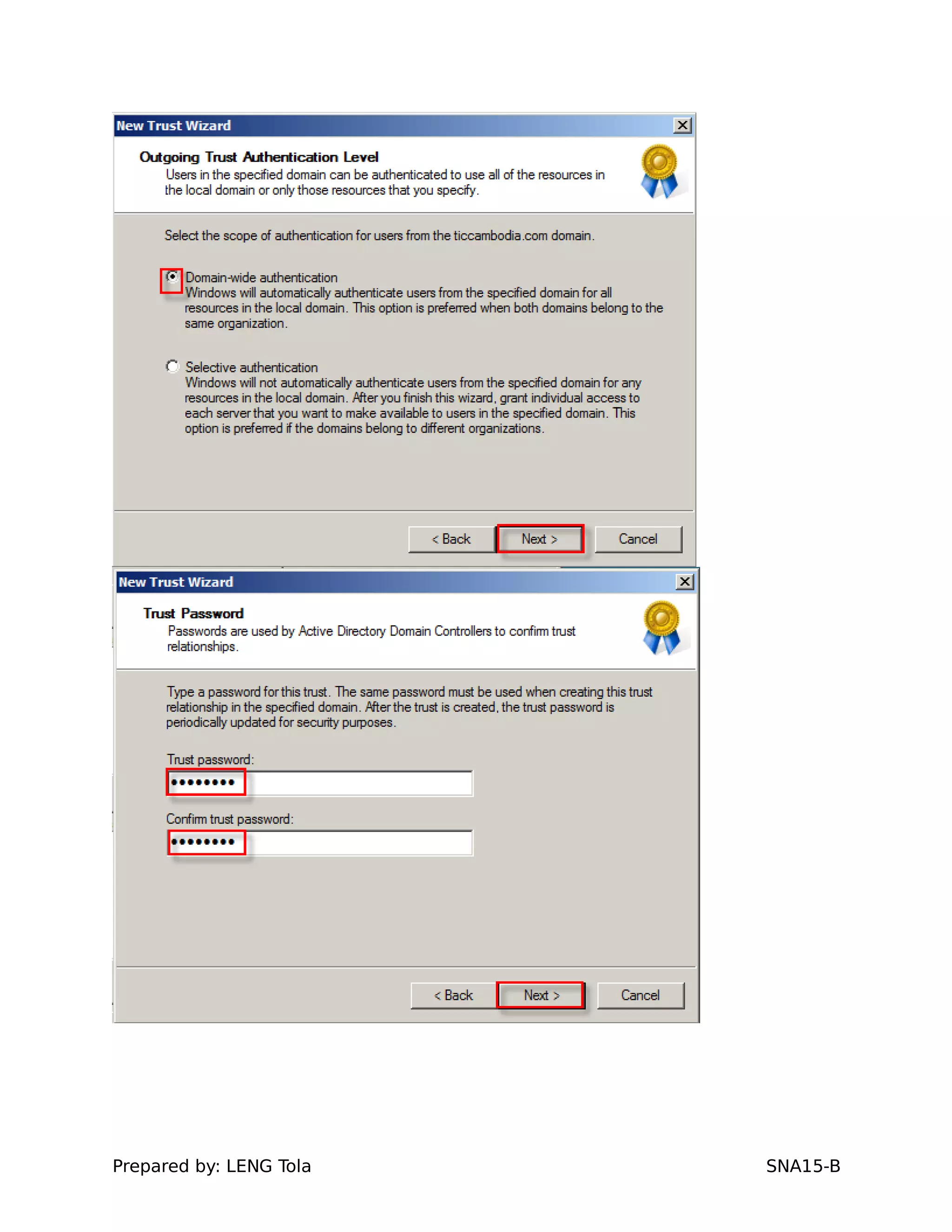
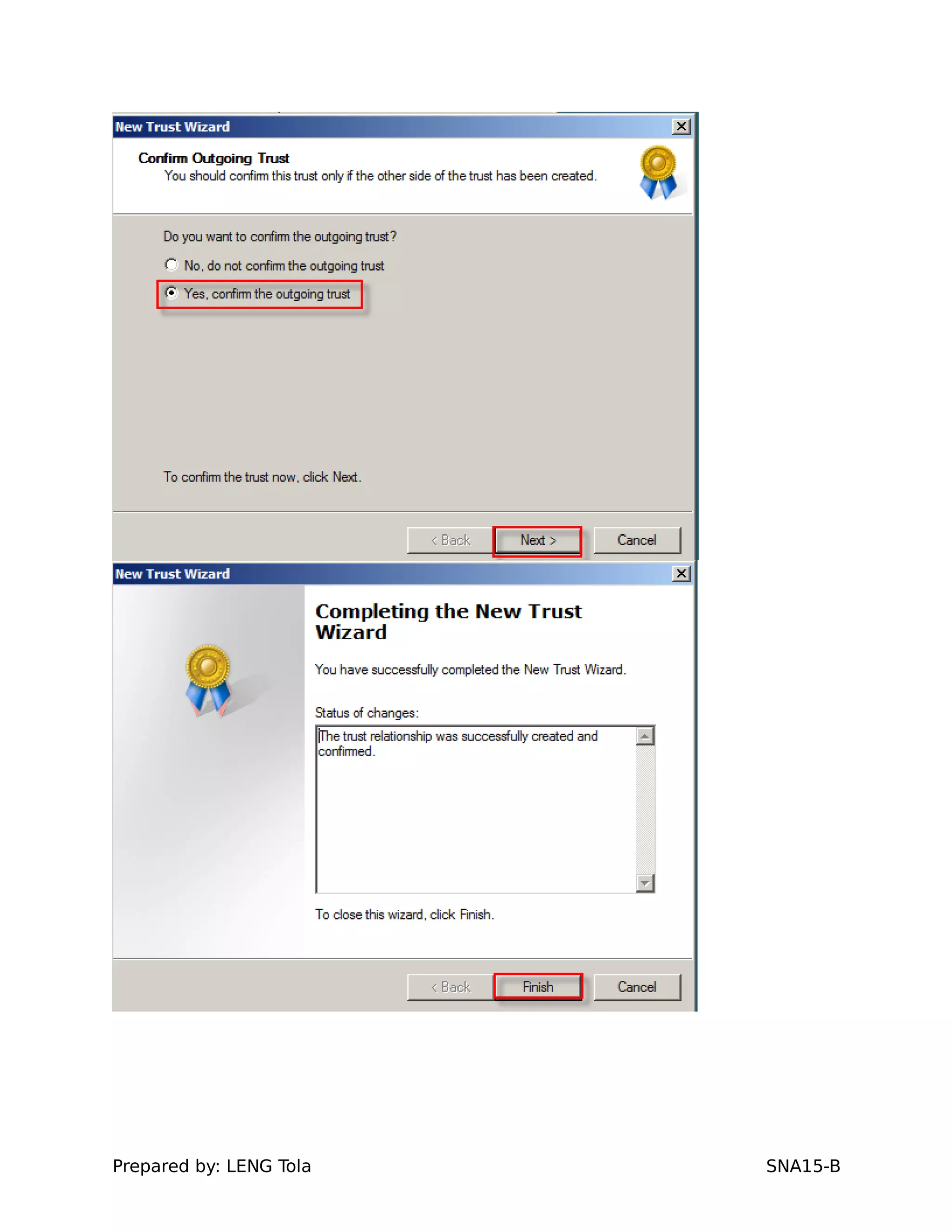
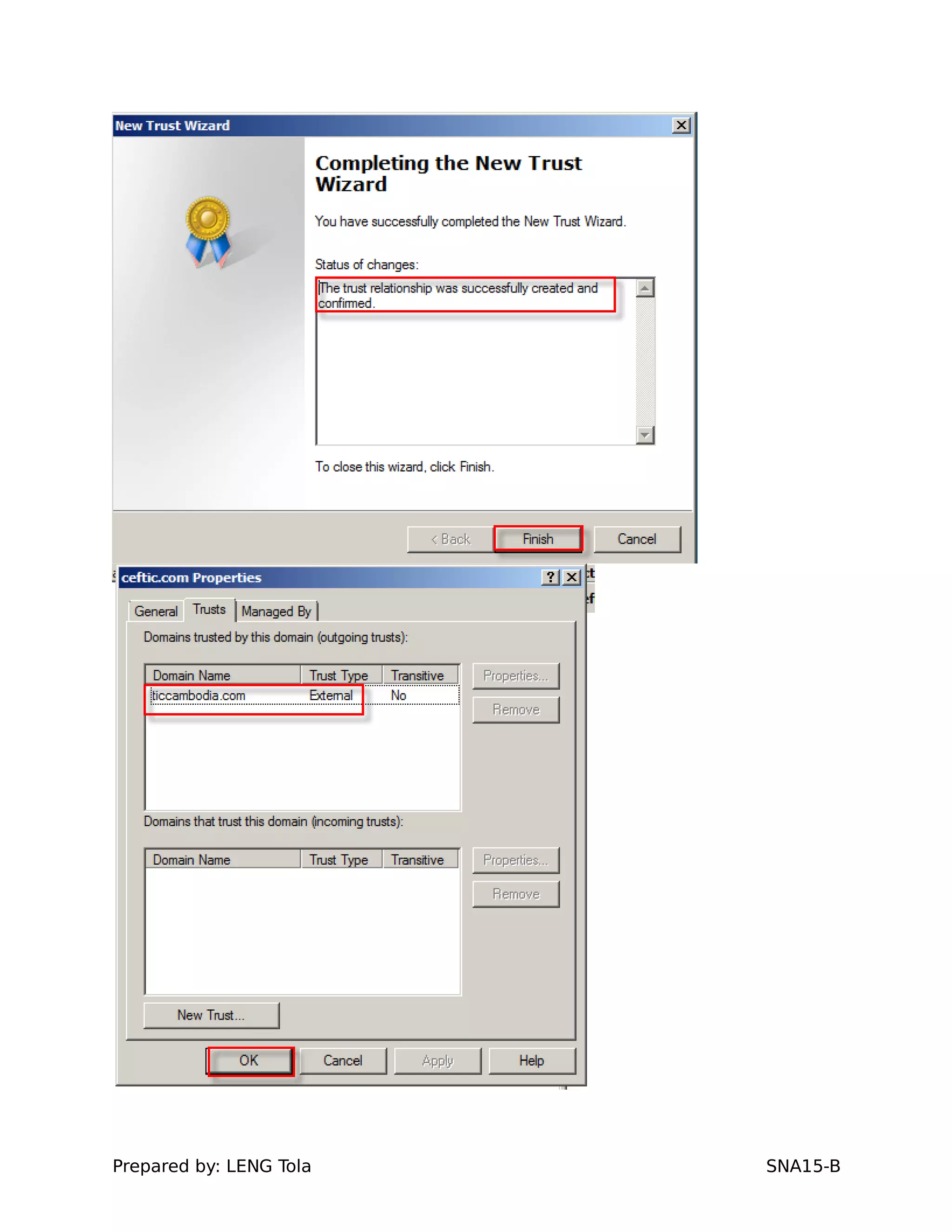
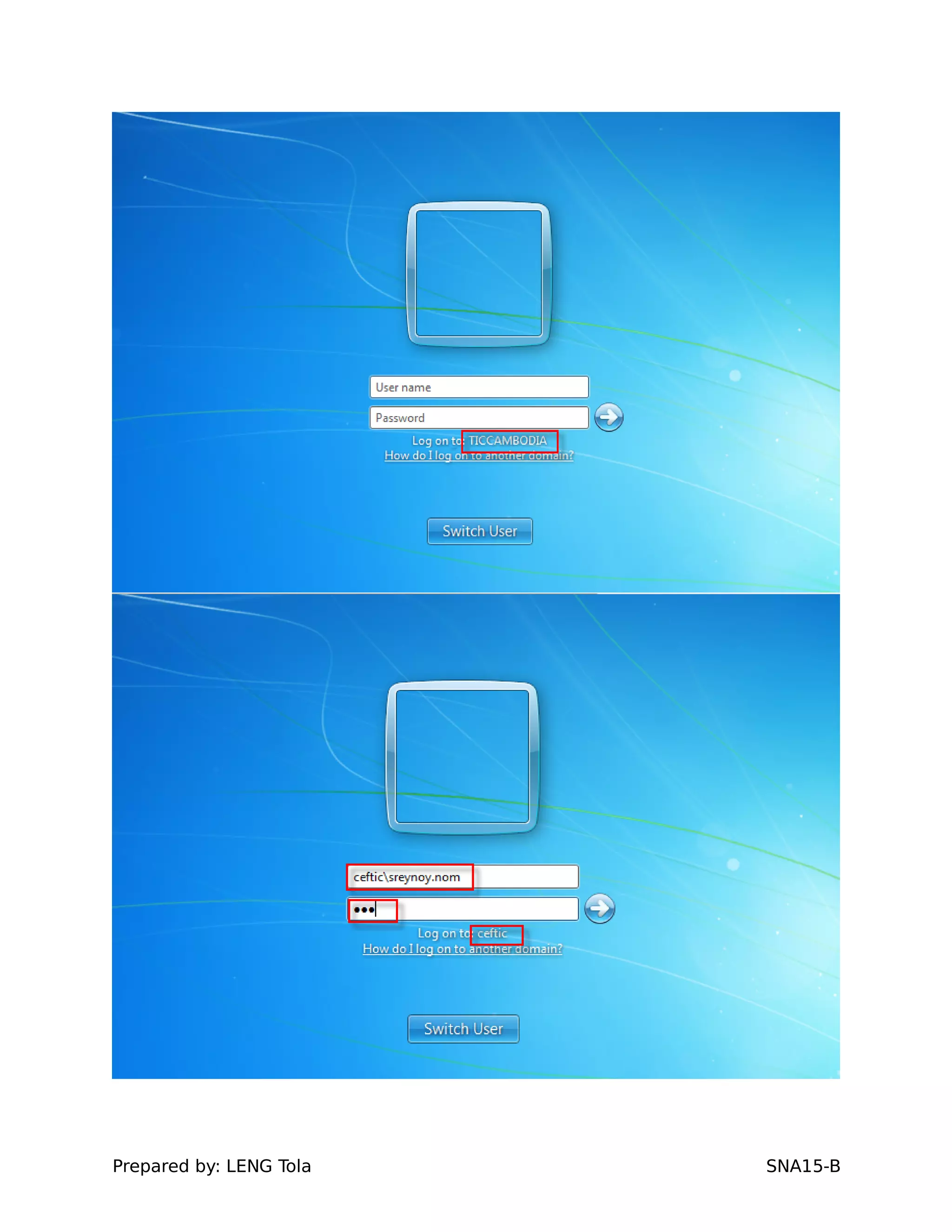
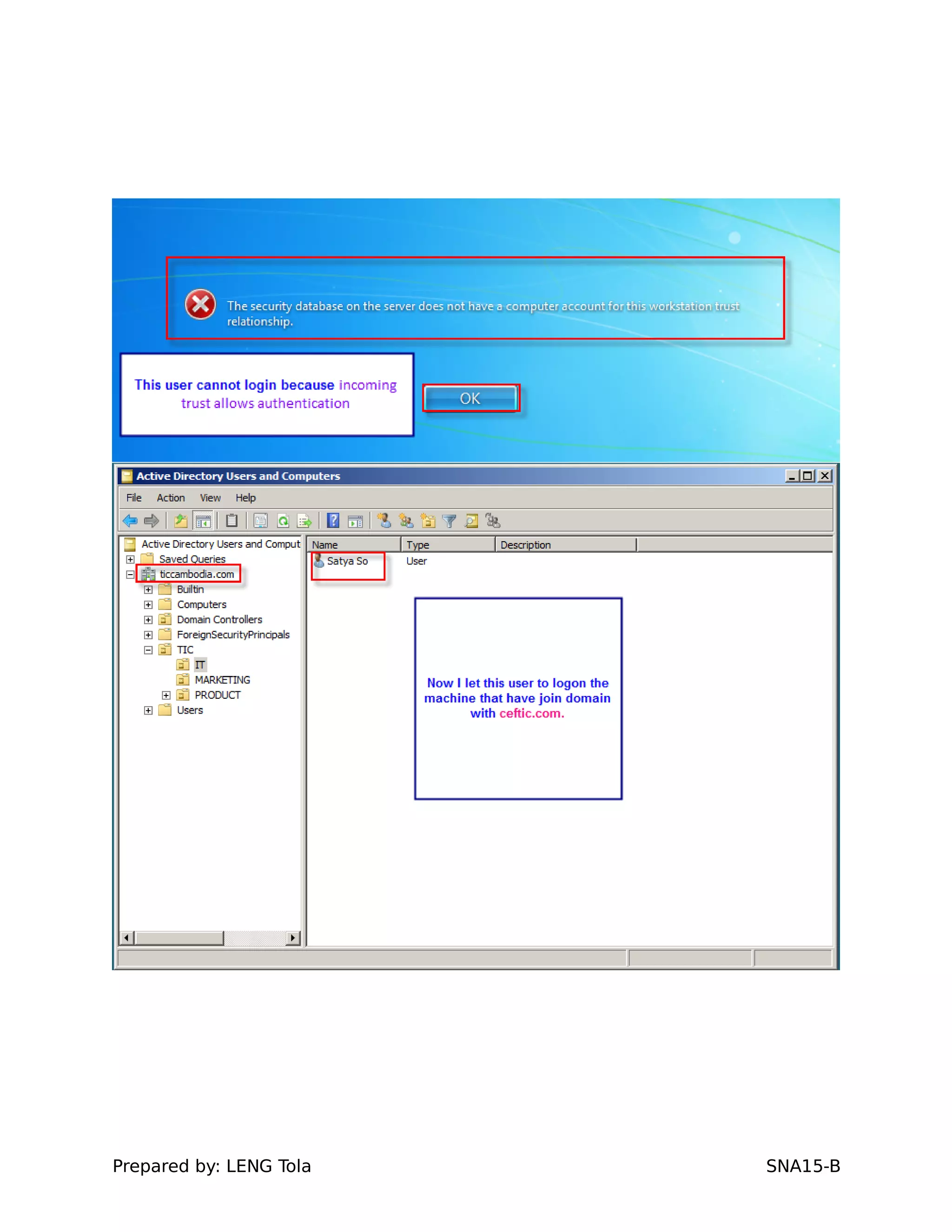
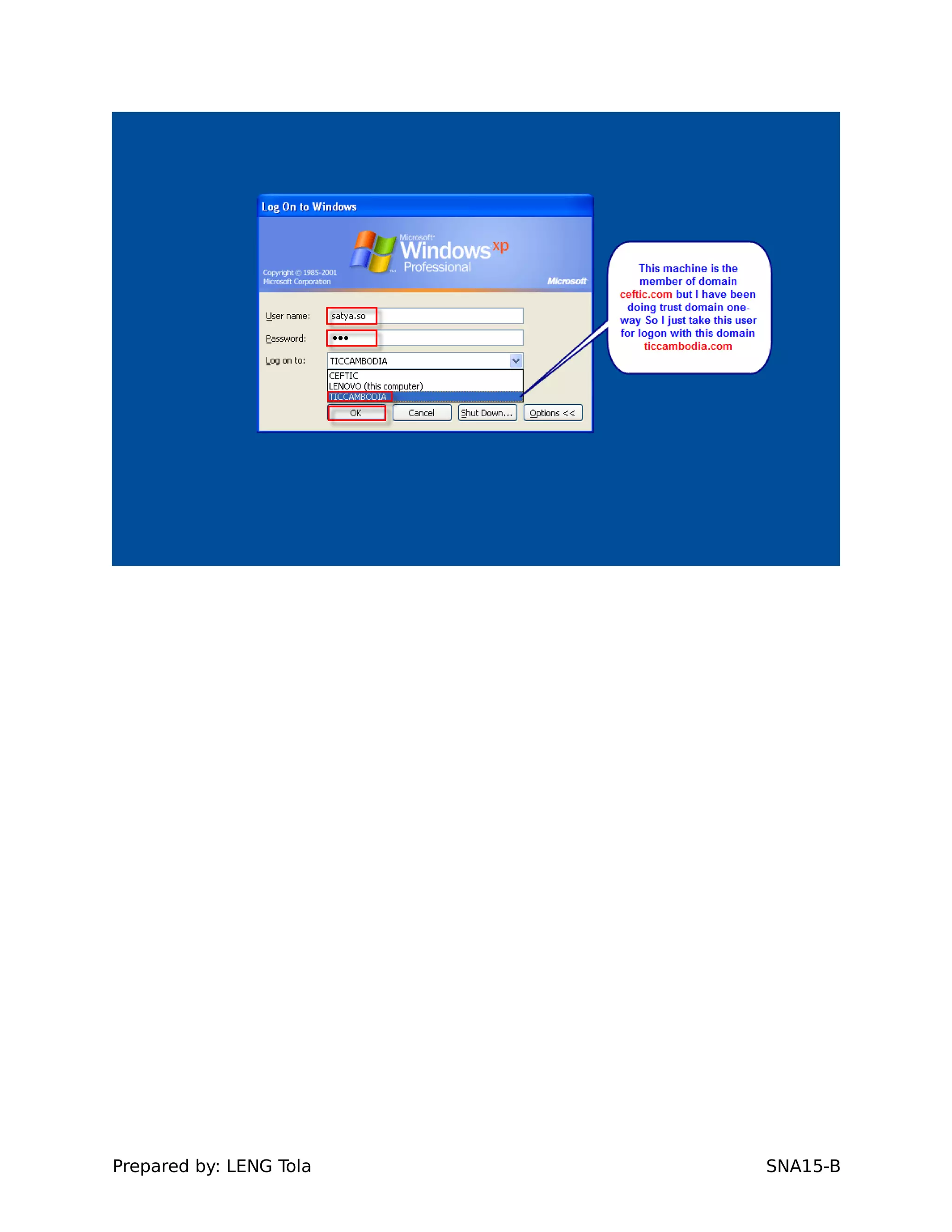
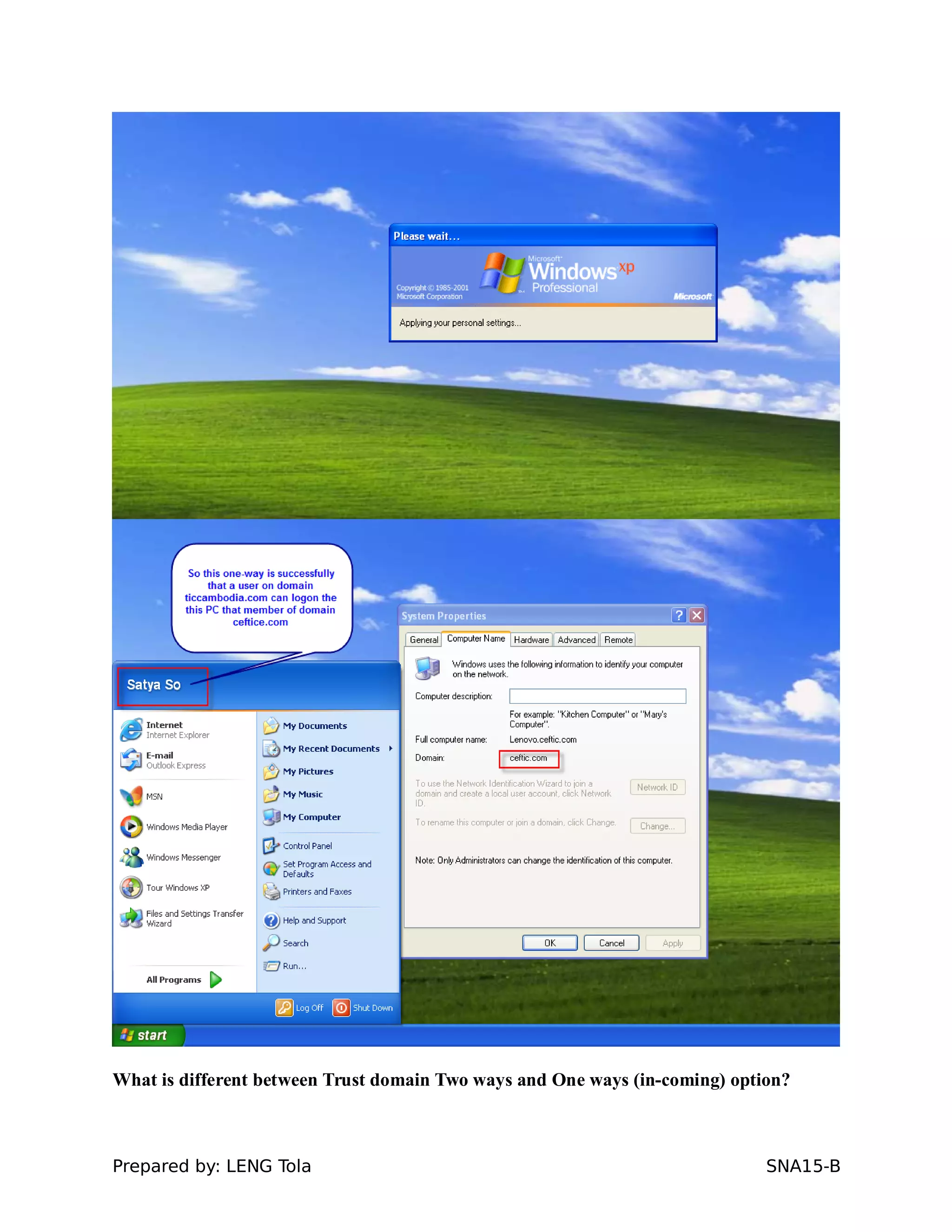
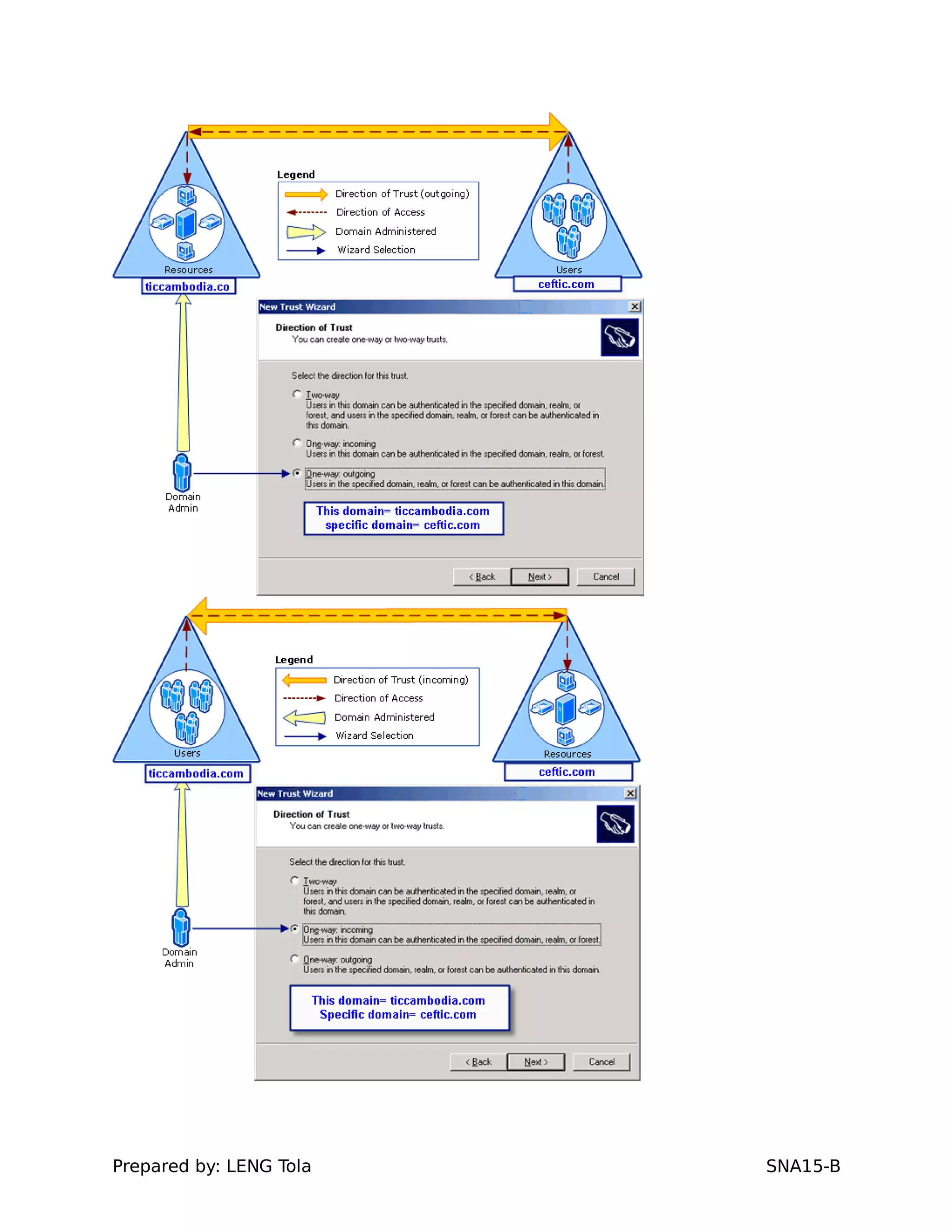
5. Configuring a trust between two domains with either a two-way or one-way trust relationship
The prepared by line indicates the tasks were completed by LENG Tola from the SNA15-B class.