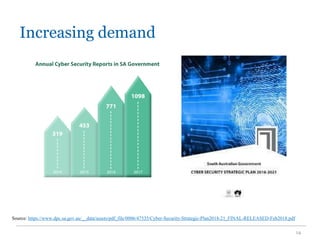
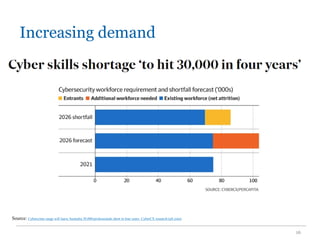
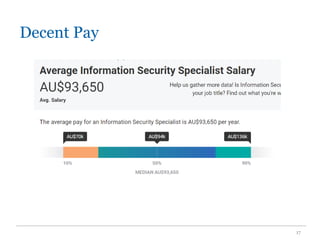
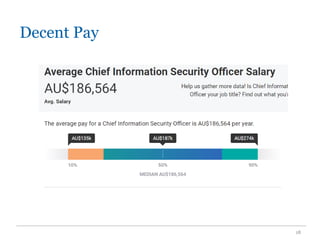
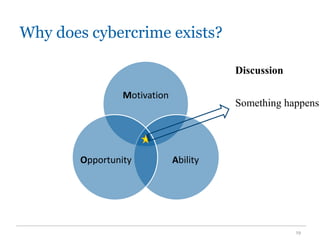
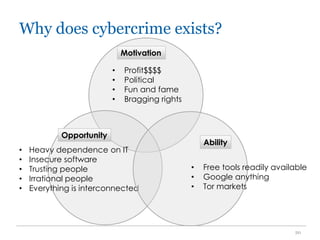
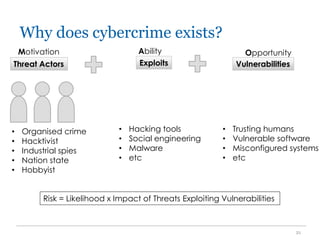
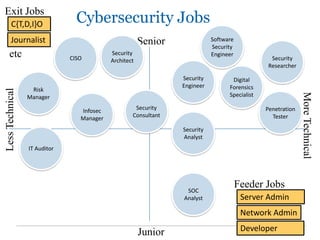
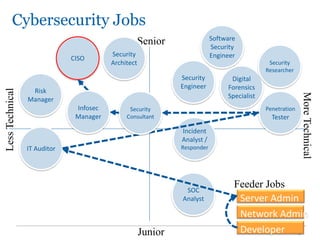
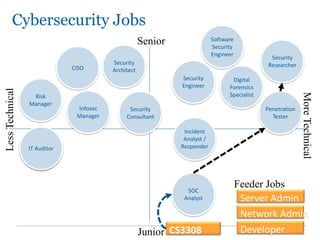
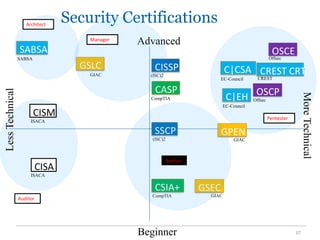
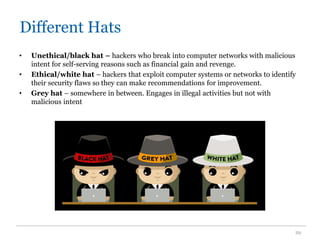
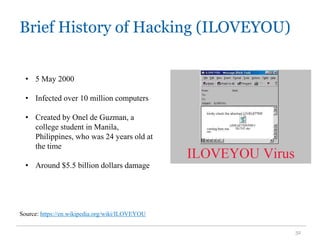
The document outlines the course COMP SCI 7328: Concepts in Cyber Security, led by Dr. Faheem Ullah, covering course structure, learning objectives, assessments, and career paths in cybersecurity. It highlights the increasing demand for cybersecurity professionals, the challenges posed by cybercrime, and the skills necessary for students pursuing a career in this field. The document also discusses the historical context of hacking and the critical role of cybersecurity in responding to evolving threats.