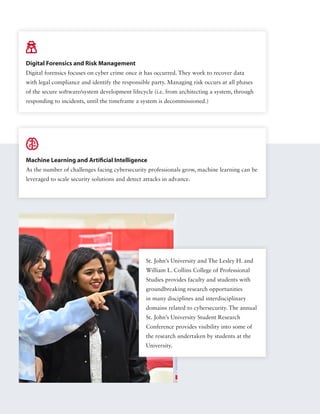
The document outlines the growing field of cybersecurity, emphasizing the rising demand for professionals due to increasing cyber threats. It details career opportunities for graduates of cyber and information security programs, the necessary skills, emerging trends, and the importance of advanced education in this sector. Additionally, it addresses the evolving cybersecurity regulations and technologies, such as AI, that impact the industry's landscape.