Embed presentation
Download to read offline


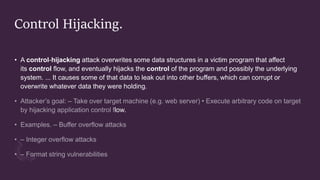
















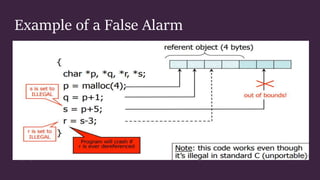


This document discusses control hijacking attacks and defenses against them. Control hijacking attacks overwrite data structures to hijack a program's control flow and take control of the underlying system. Defenses include run-time checking that validates data types and array bounds to prevent buffer overflows from corrupting memory and hijacking control. While run-time checking prevents attacks, it can also generate false alarms, so more accurate techniques are needed.




















