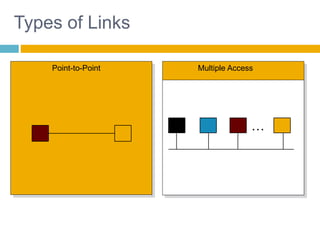
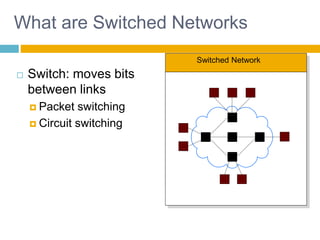
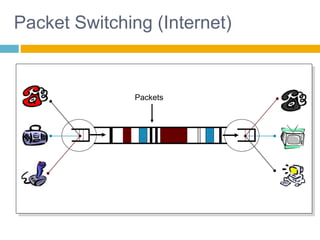
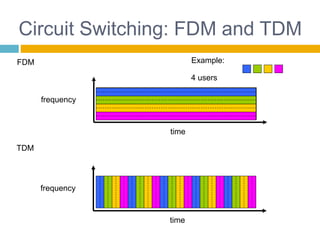
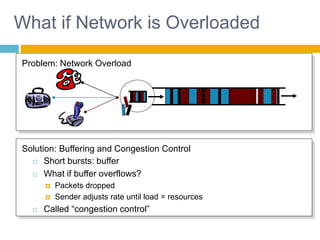
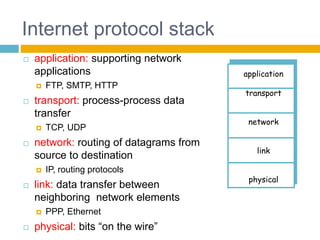
Shivangi submitted a topic paper on "Computer Networking" for her Computer Science and Engineering department. The 3-page paper discusses the objectives of networking, including enabling communication between applications on different computers and matching application requirements. It also covers the four steps of networking, including interconnecting multiple links, finding and routing data, and matching applications needs. Additionally, it defines key networking concepts like links, nodes, packet and circuit switching, congestion control, the layered Internet protocol stack, and considerations for security in computer networks.