This document provides an overview of basic computer components and functions, including:
- The mouse and keyboard are used to control the computer and type.
- Operating systems like Windows 7 or Vista run the main programs. These need regular updates.
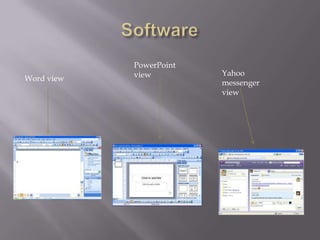
- Software programs like Word and PowerPoint can be installed to perform tasks.
- Files are saved internally or to external storage like hard drives in case of computer crashes.
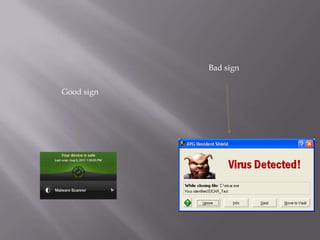
- Anti-virus software should be used to protect against viruses and updated regularly.
- Hyperlinks on webpages and emails provide shortcuts to other online locations.
- Email allows communication between individuals and with companies by creating an account with a secure password.