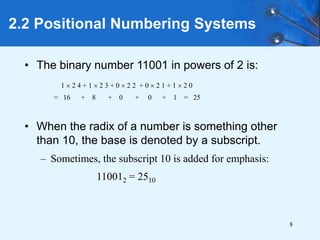
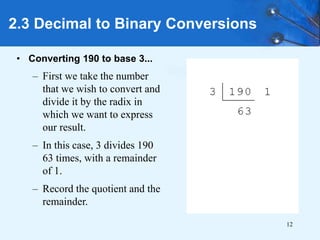
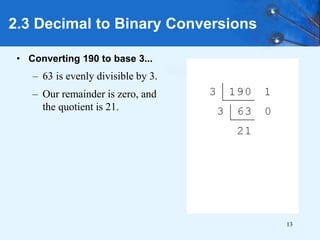
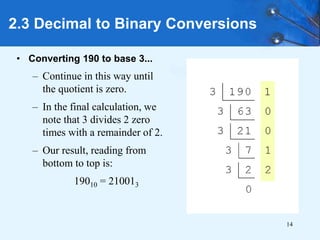
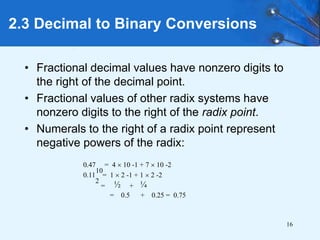
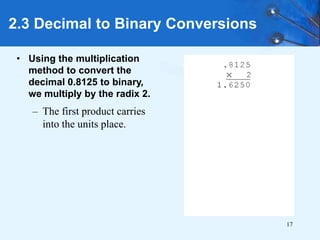
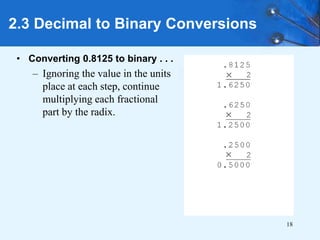
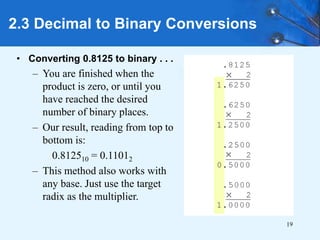
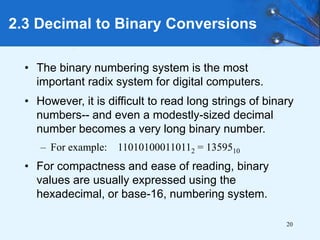
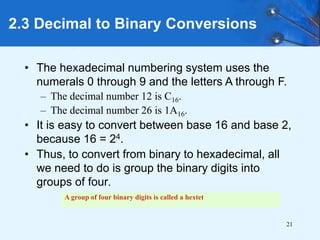
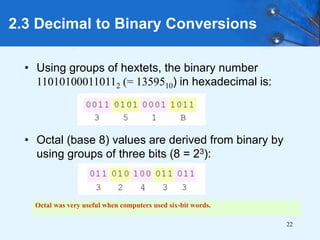
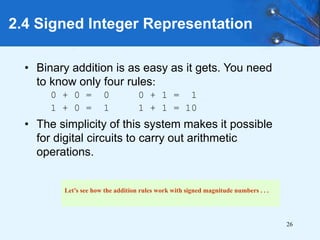
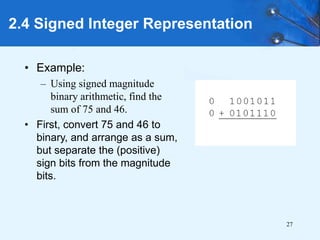
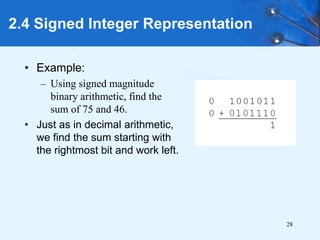
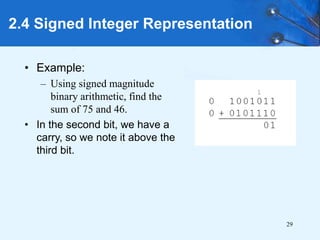
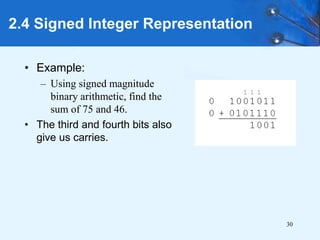
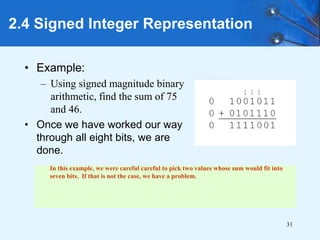
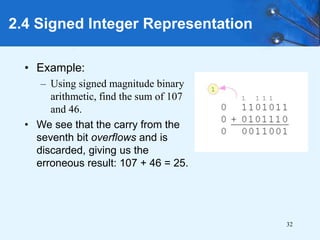
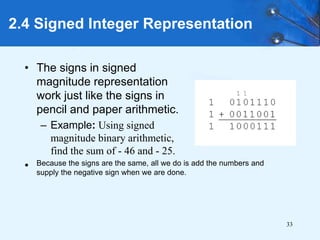
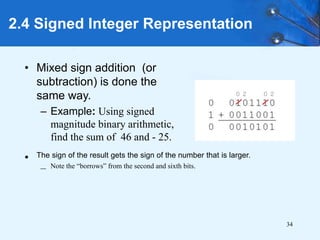
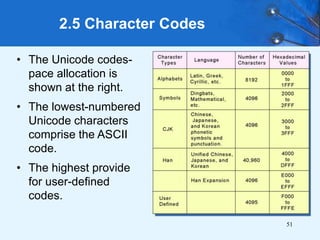
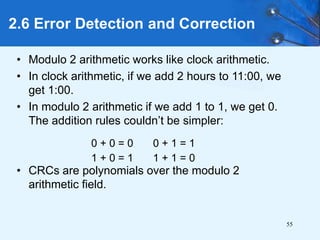
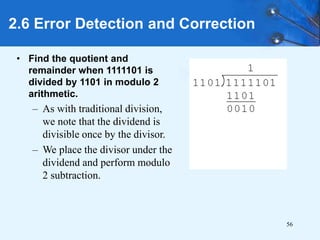
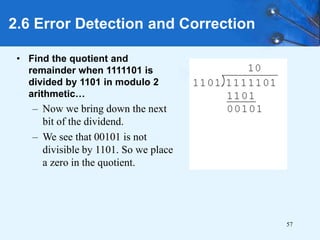
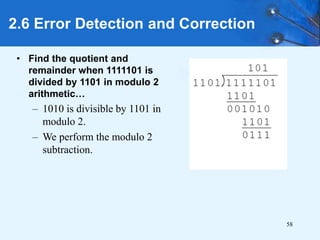
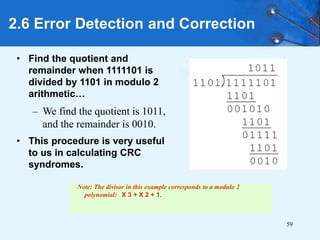
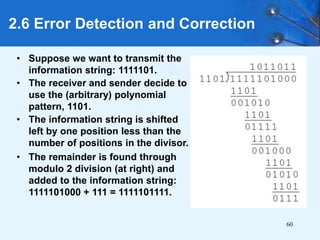
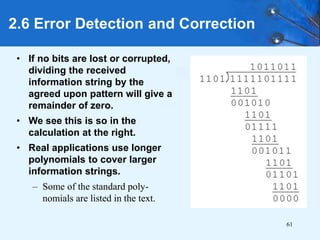
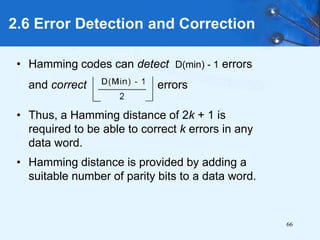
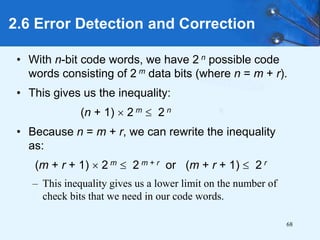
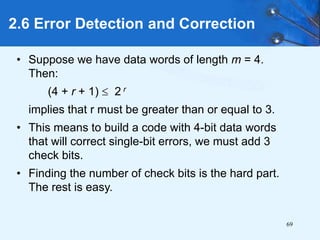
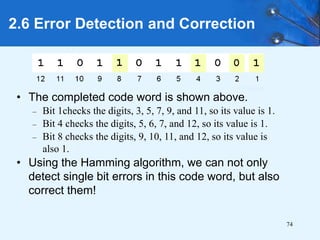
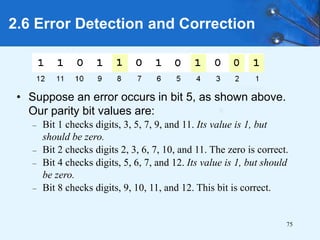
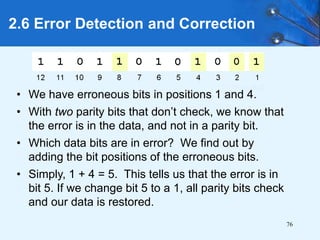
This document provides an overview of data representation in computer systems. It discusses the fundamentals of numerical data representation using binary and other numeral systems, including signed and unsigned integers. It also covers character codes for representing human-readable text in computers. Error detection and correction techniques are introduced. The goals are to understand how computers store and manipulate numeric and character data internally.