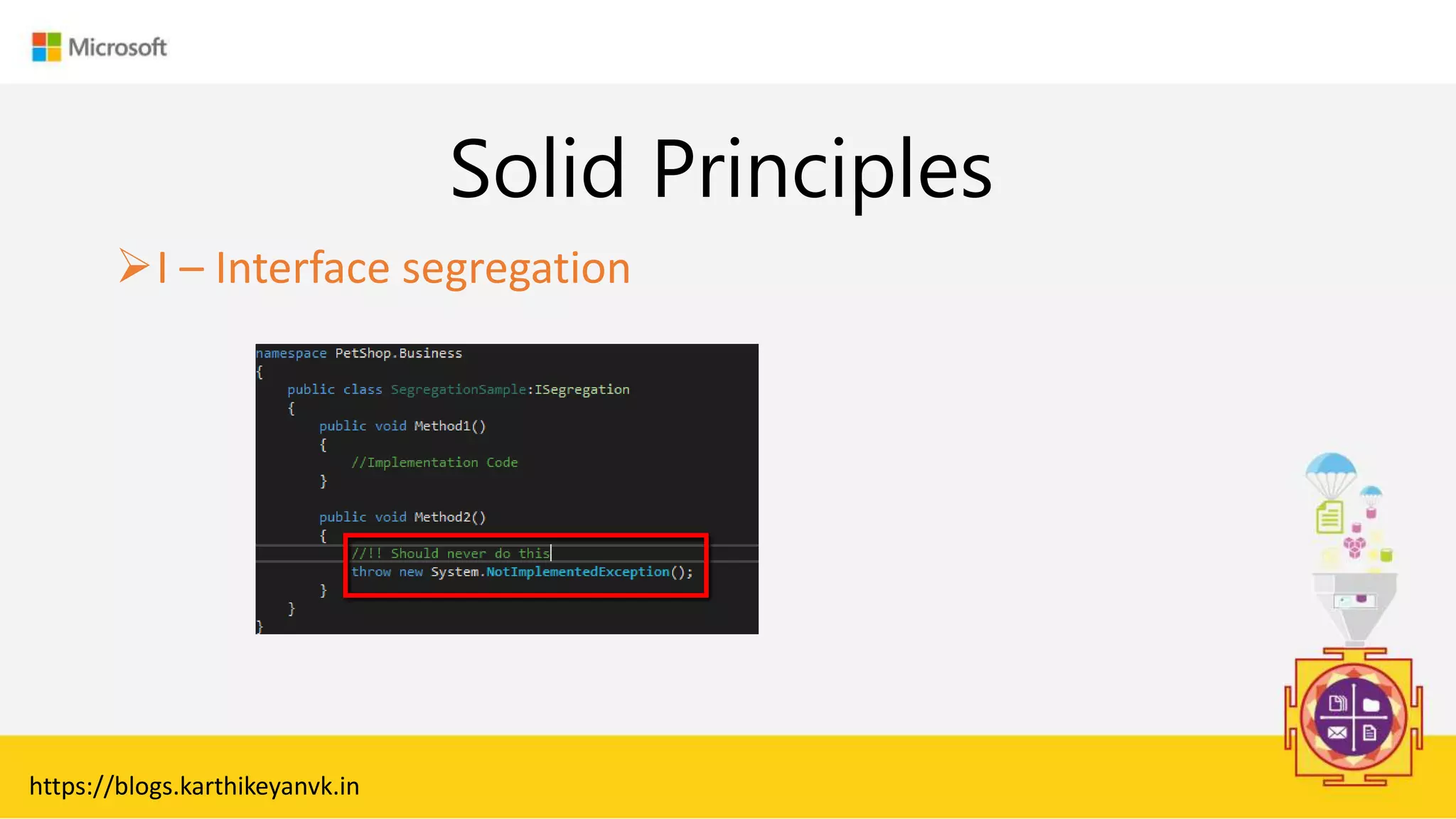
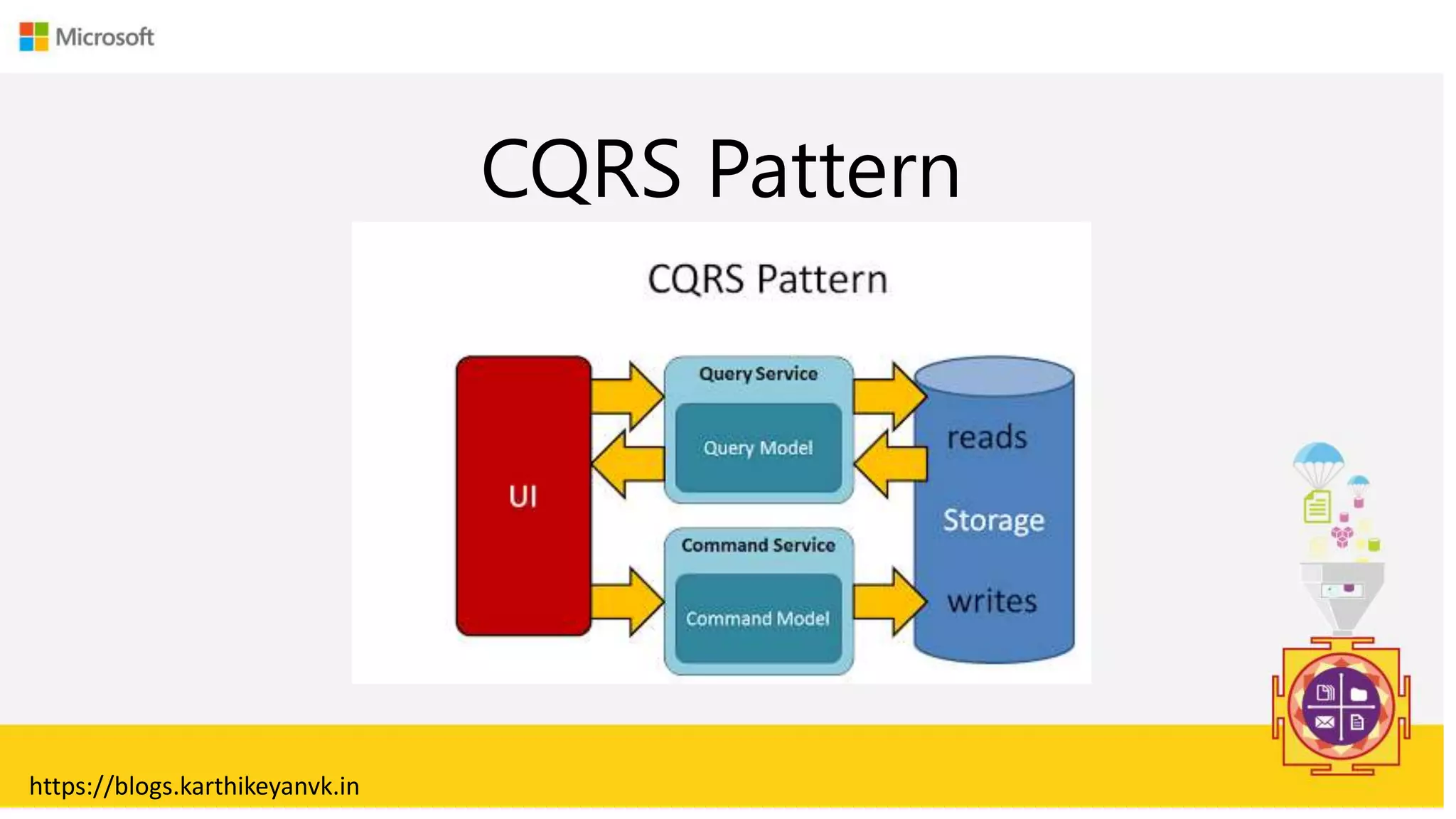
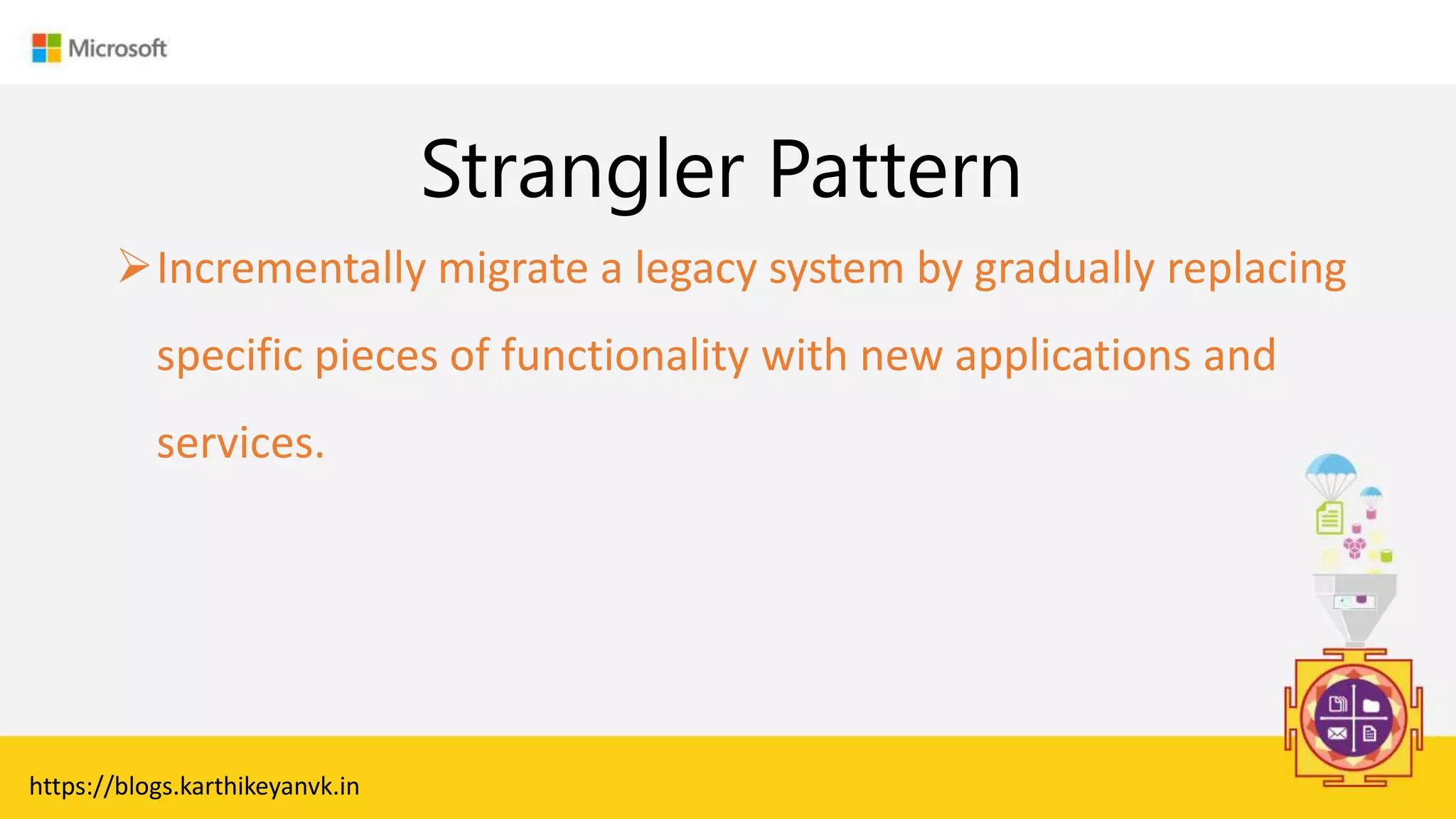
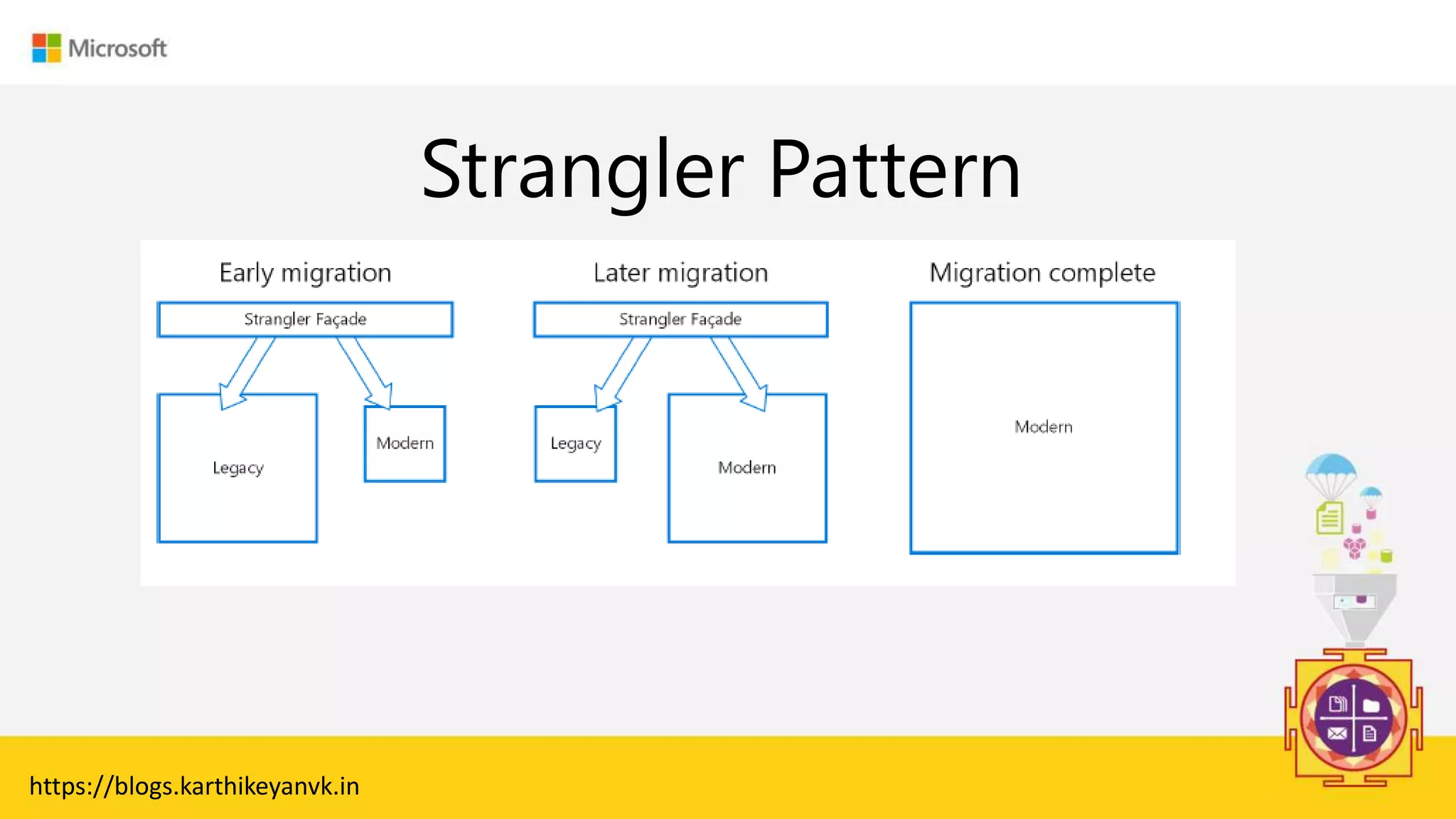
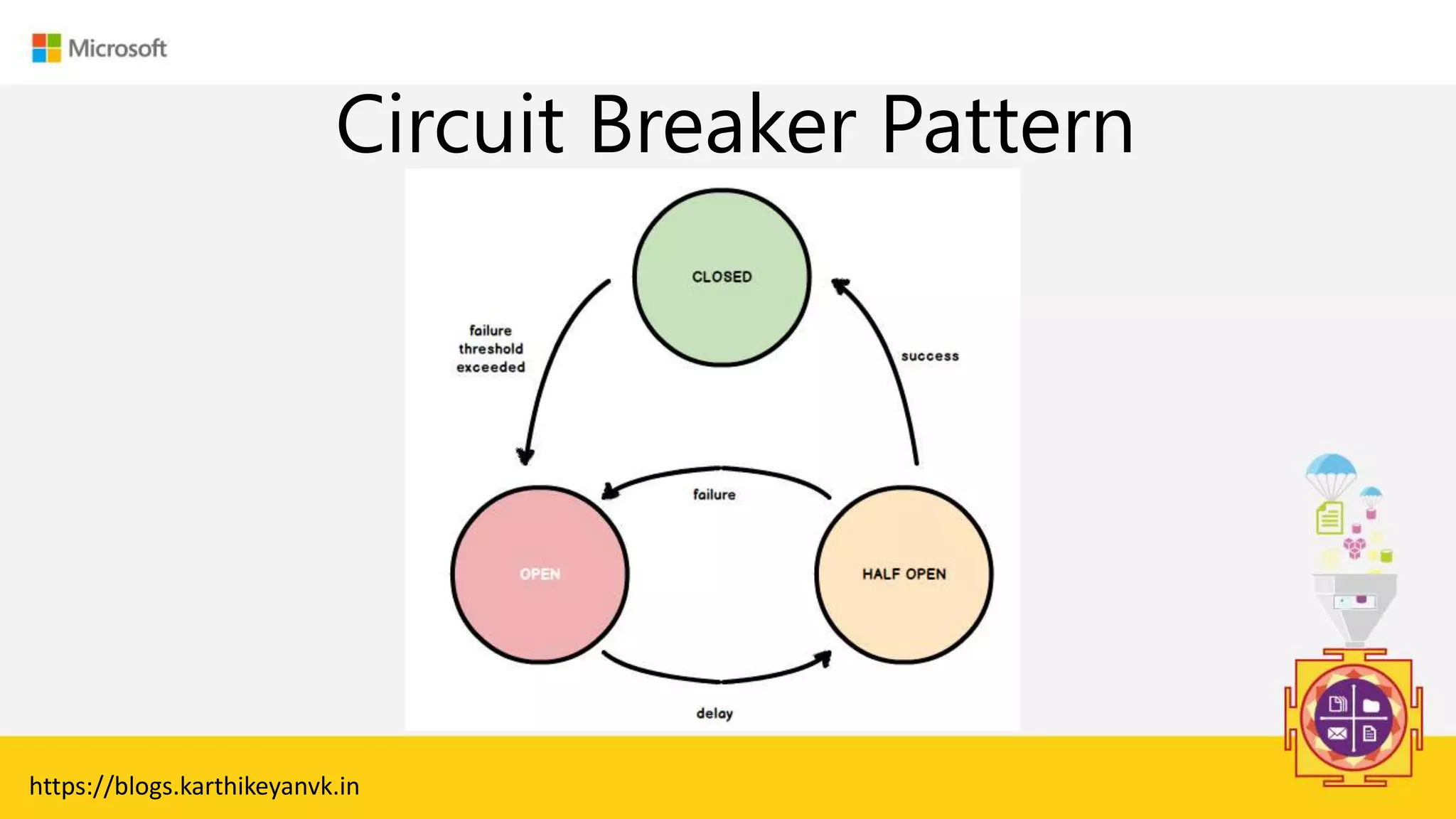
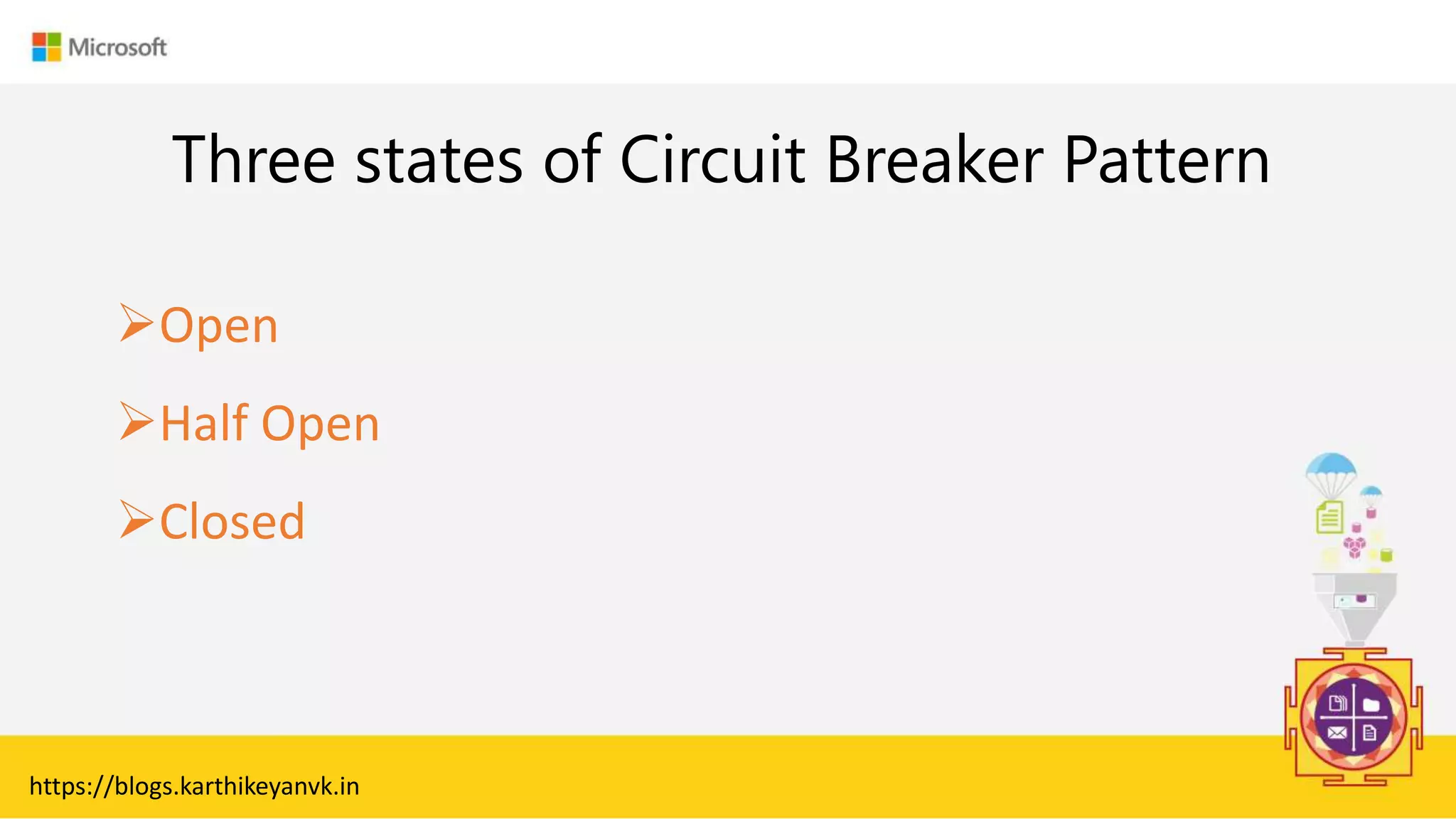
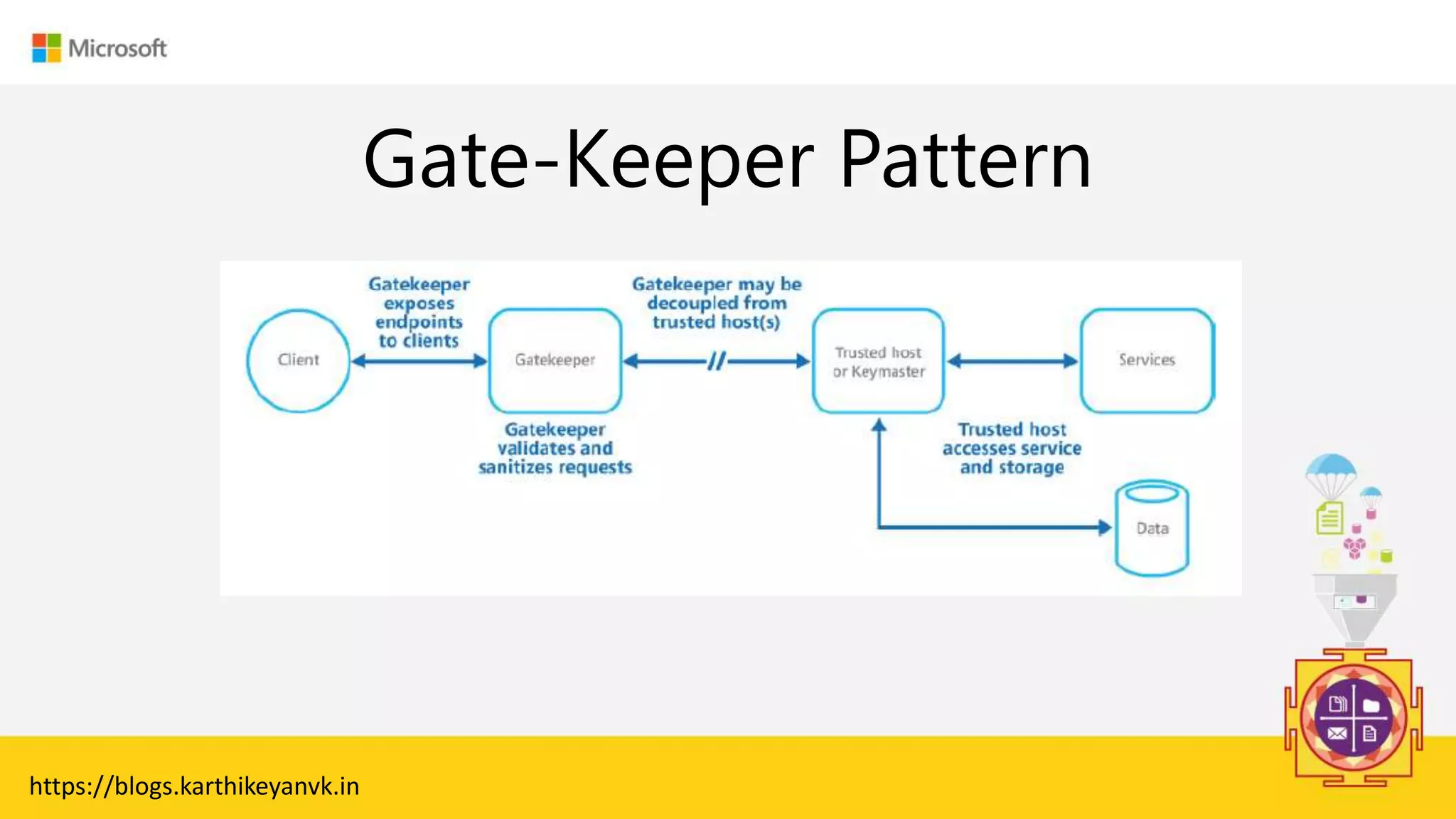
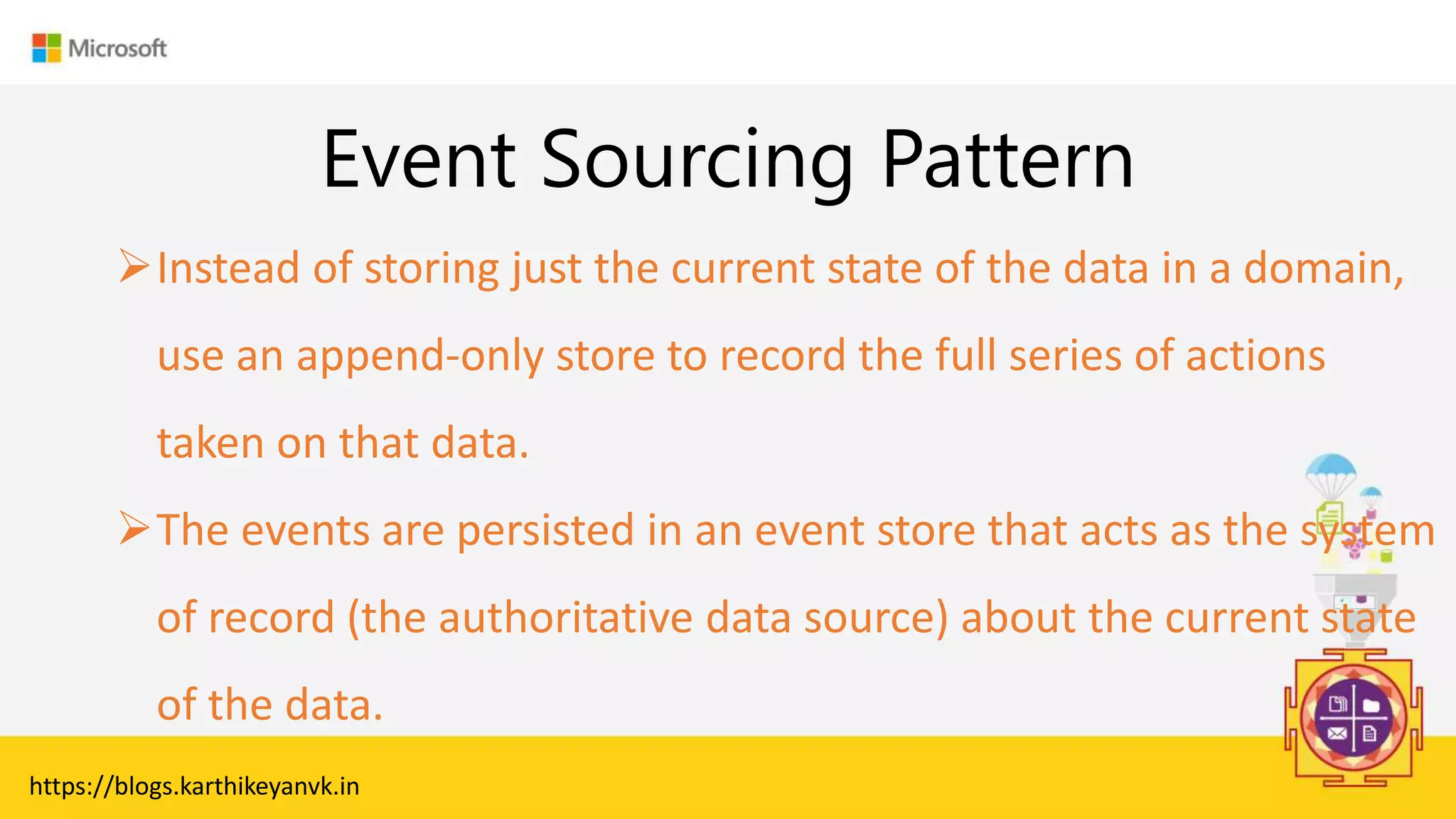
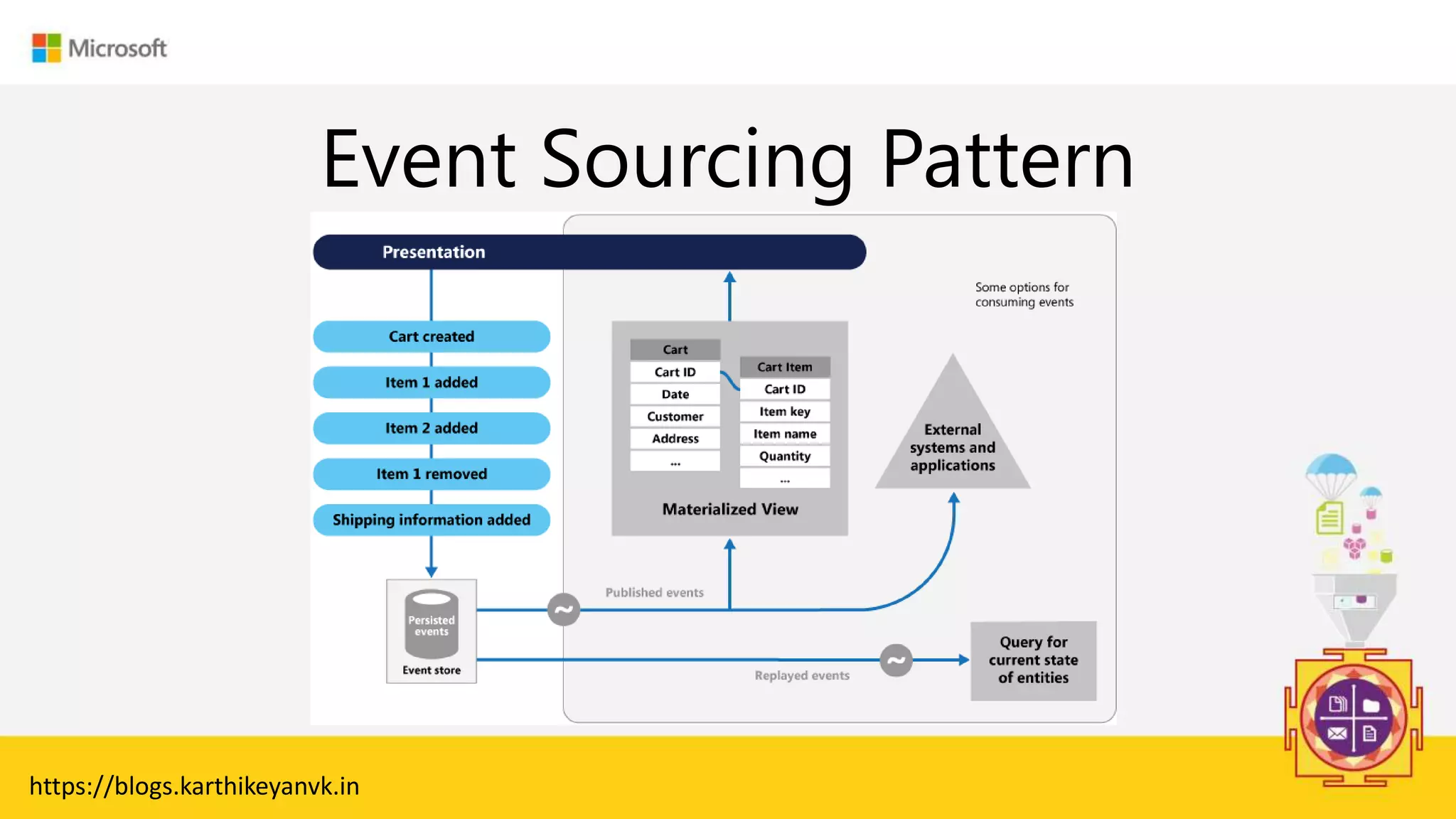
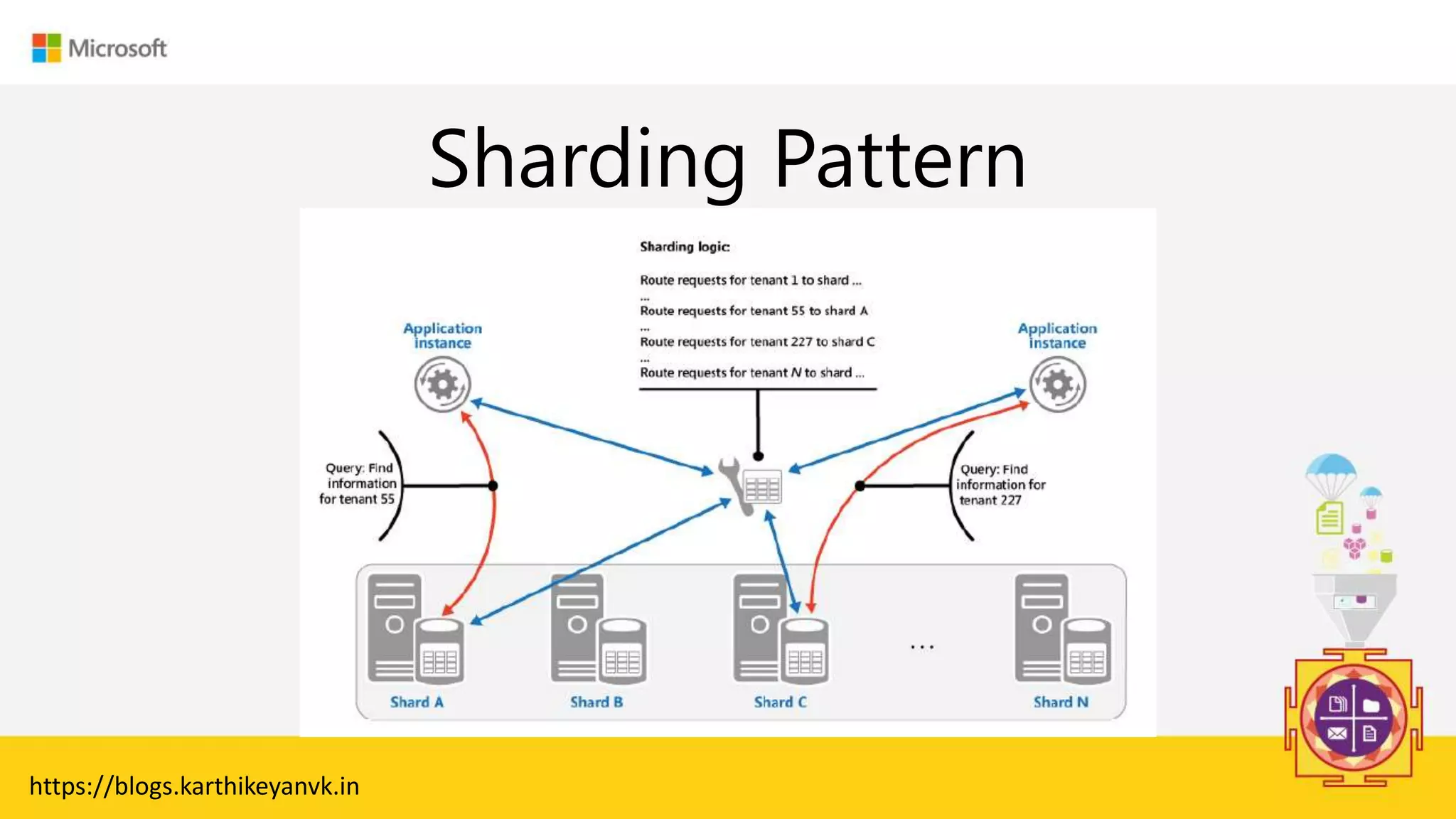
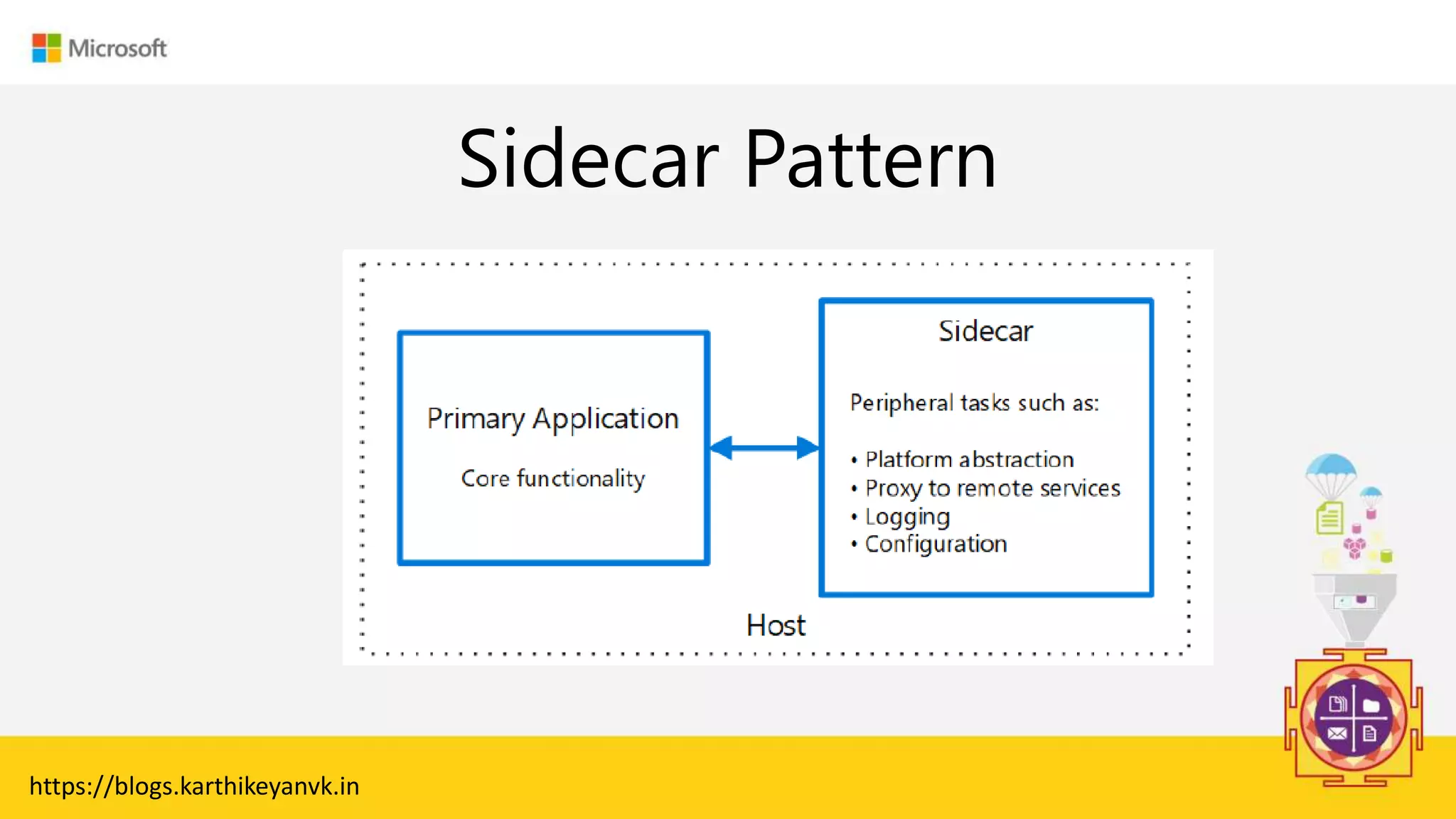
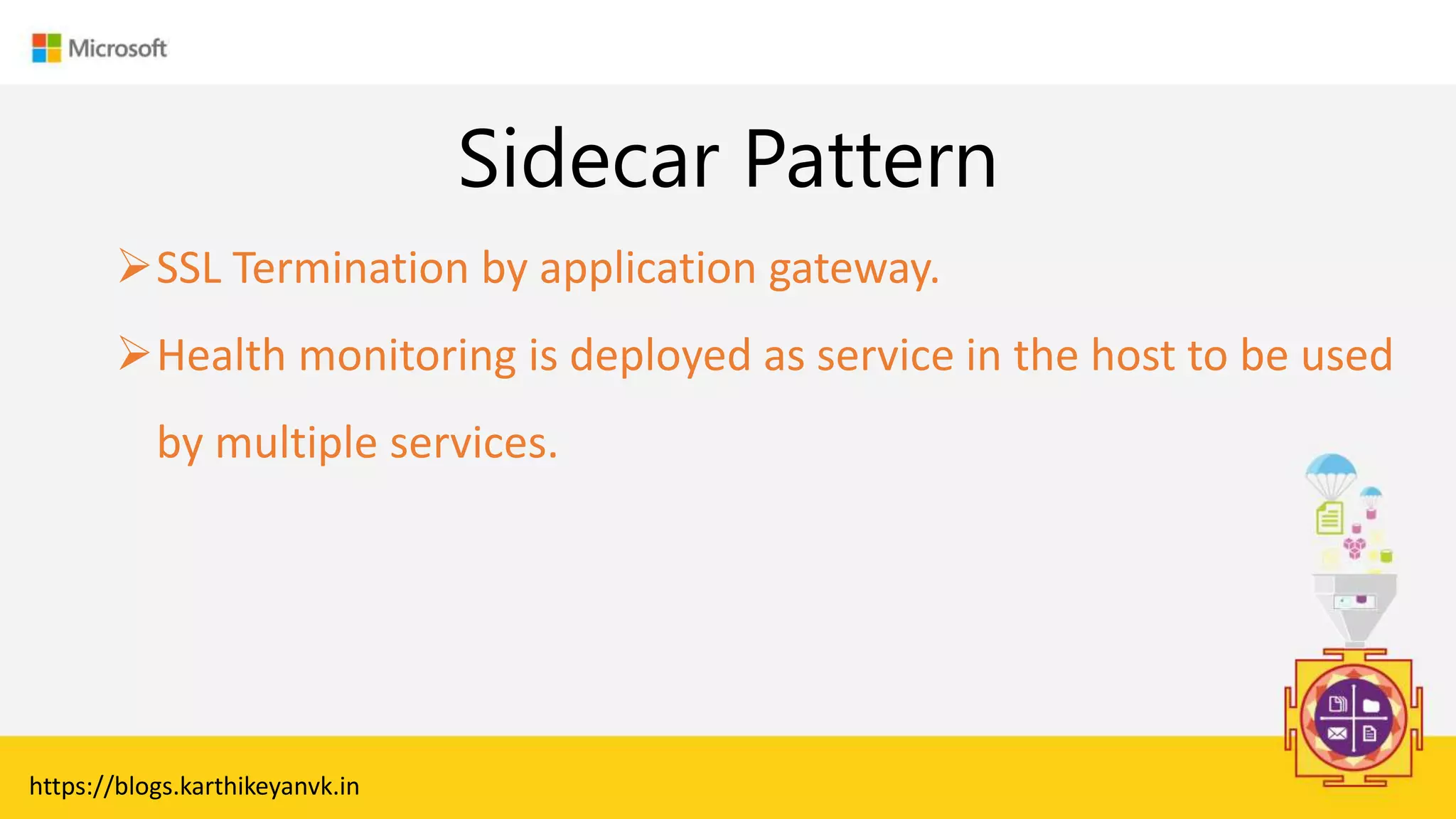
The document discusses various cloud design patterns, emphasizing the importance of availability, resilience, and performance in cloud applications. It outlines principles such as the SOLID principles, and describes specific patterns like the Circuit Breaker, Pipes and Filters, and Event Sourcing. Additionally, it addresses common anti-patterns and the significance of using design patterns to improve software architecture and facilitate decision-making.