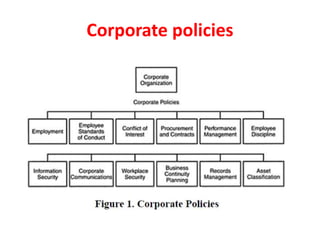
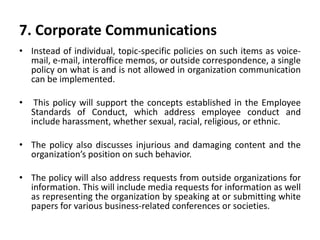
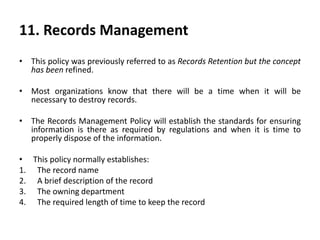
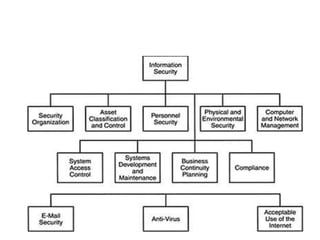
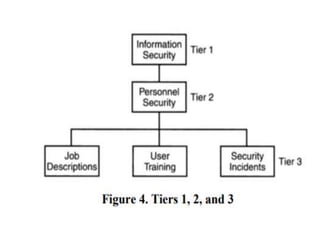
This document discusses cyber laws and ethics as well as information security policies and procedures. It covers 11 tier 1 corporate policies including employment practices, standards of conduct, conflict of interest, and information security. It also discusses developing topic specific tier 2 policies for areas like electronic communications, internet security, and anti-virus. The goal of information security policies is to protect the integrity, confidentiality, and availability of information as an organizational asset.