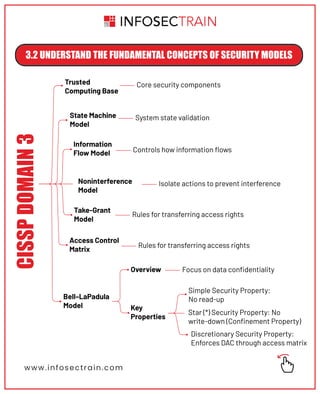
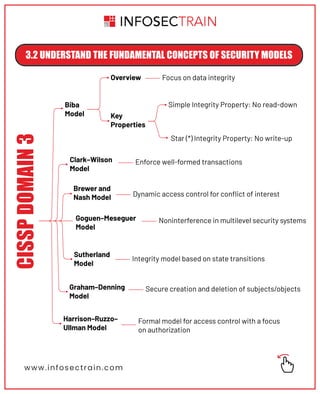
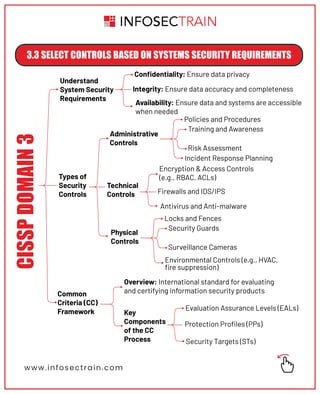
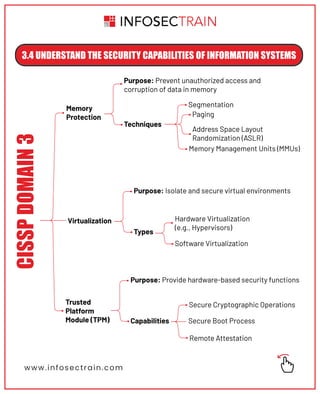
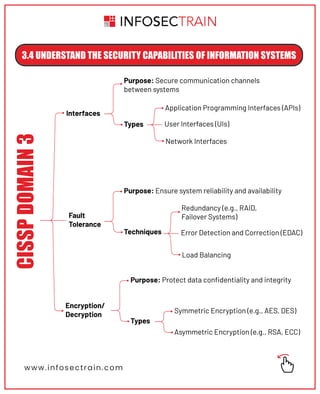
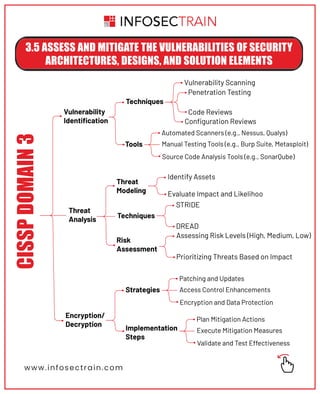
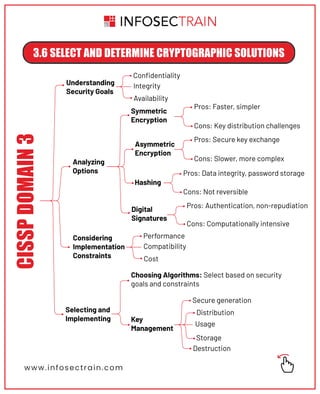
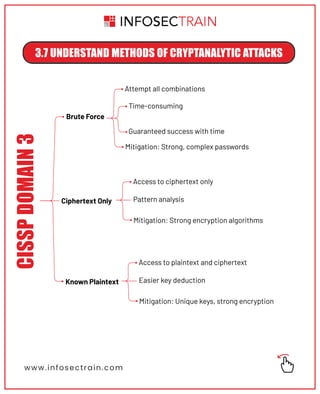
The document outlines key security principles and models relevant to engineering processes, focusing on areas such as threat modeling, vulnerability identification, and cryptographic solutions. It emphasizes risk assessment, security controls, and maintaining system integrity while also addressing site and facility security design. Various models and frameworks, including access control and security capabilities, are detailed to aid in understanding and implementing effective security measures.