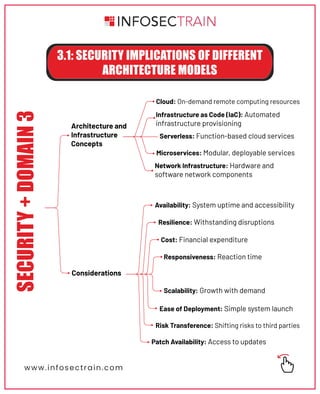
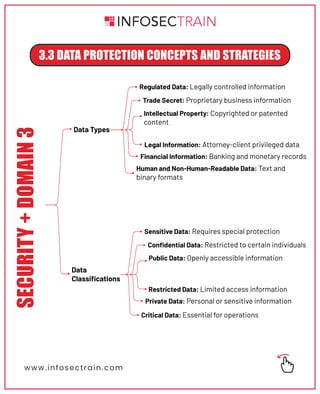
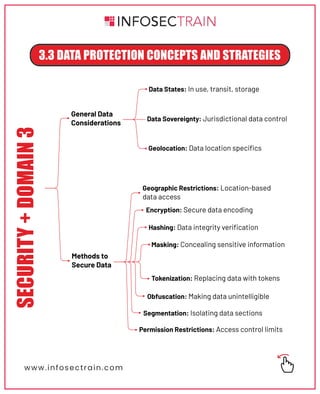
The document outlines key architecture and infrastructure concepts related to availability, security, and data protection. It discusses various models such as cloud services and microservices, alongside strategies for data classification and protection. The content also covers resilience and recovery strategies to ensure continuous operation and security in enterprise infrastructure.