Embed presentation

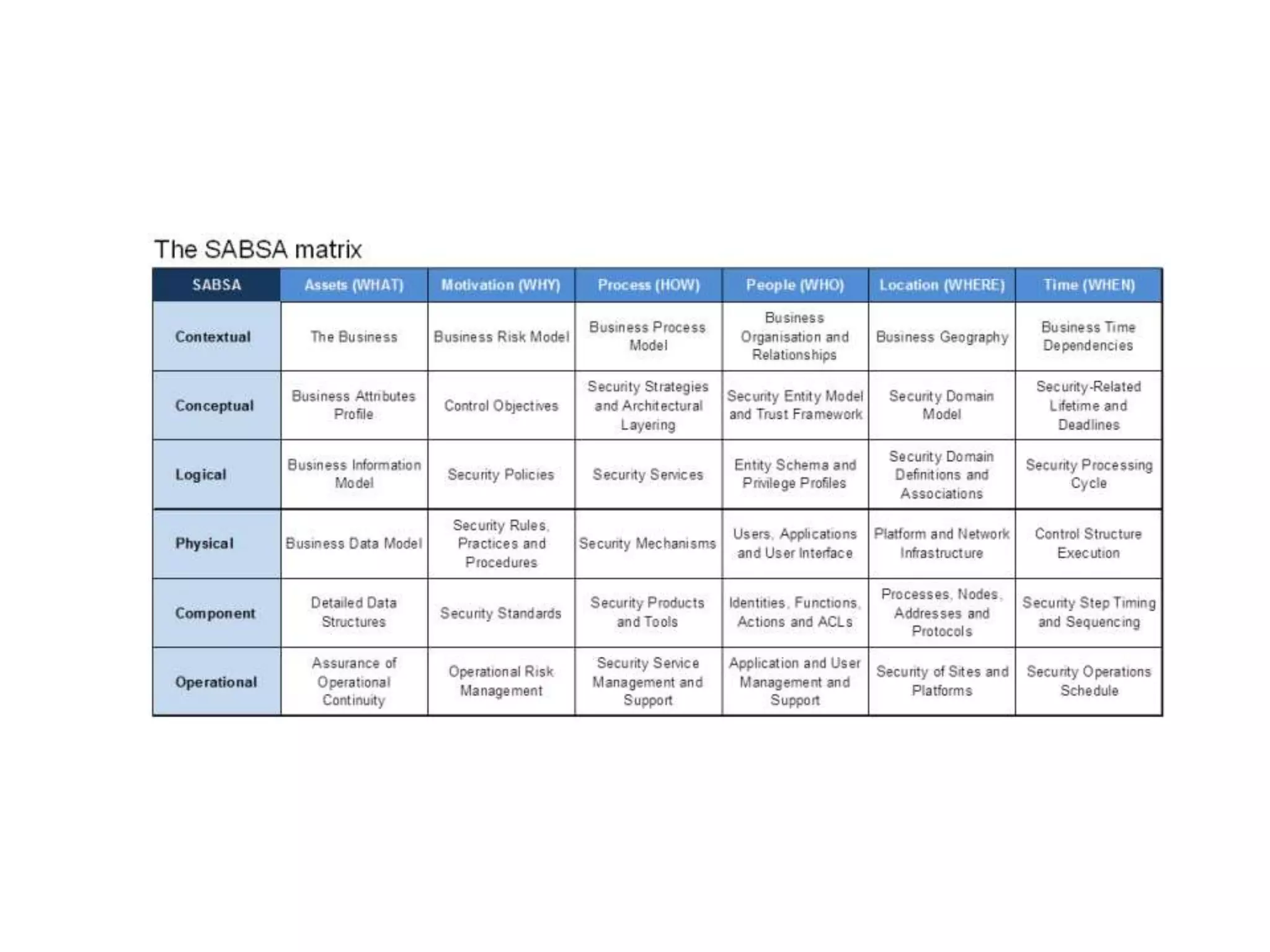




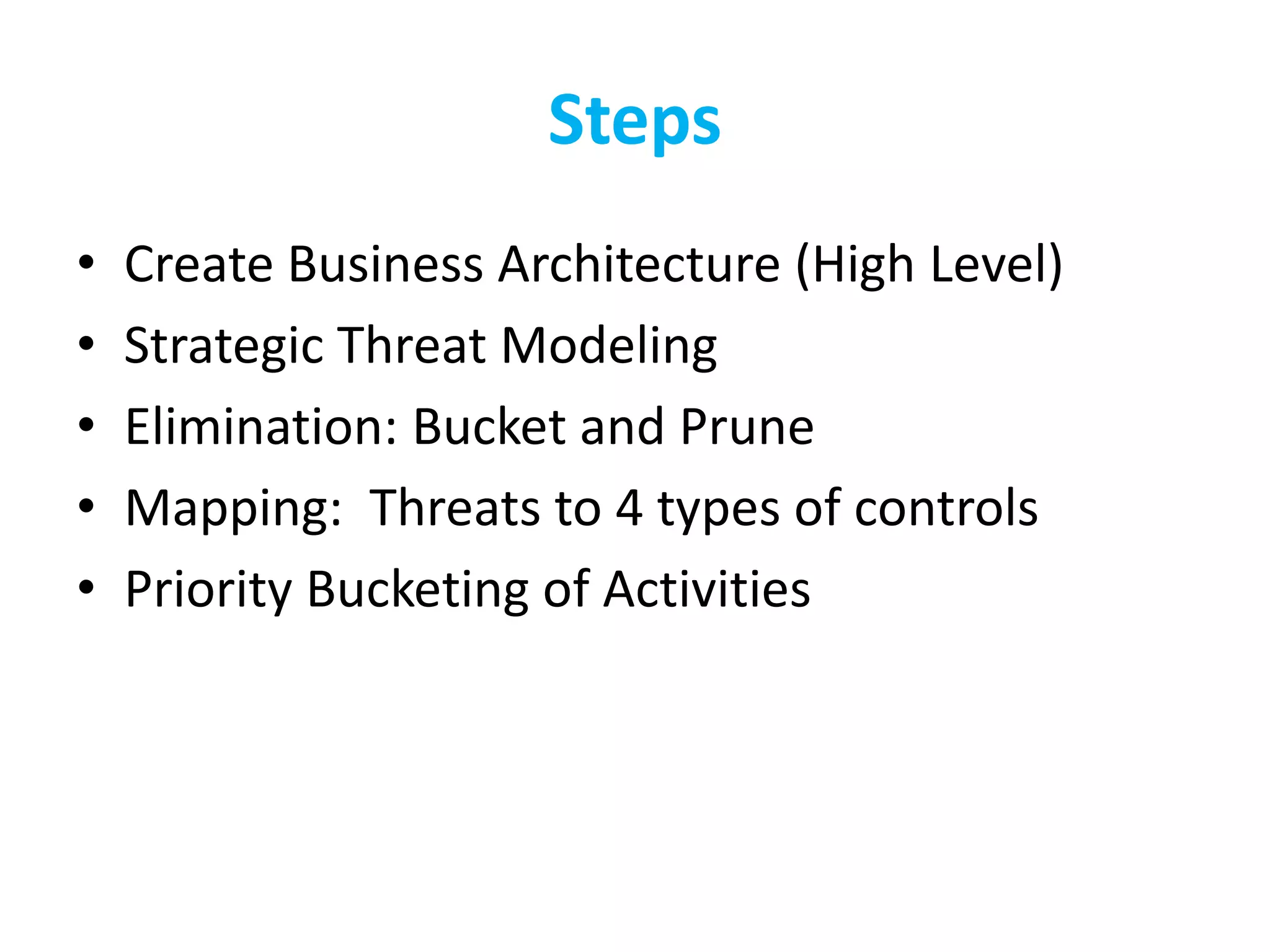



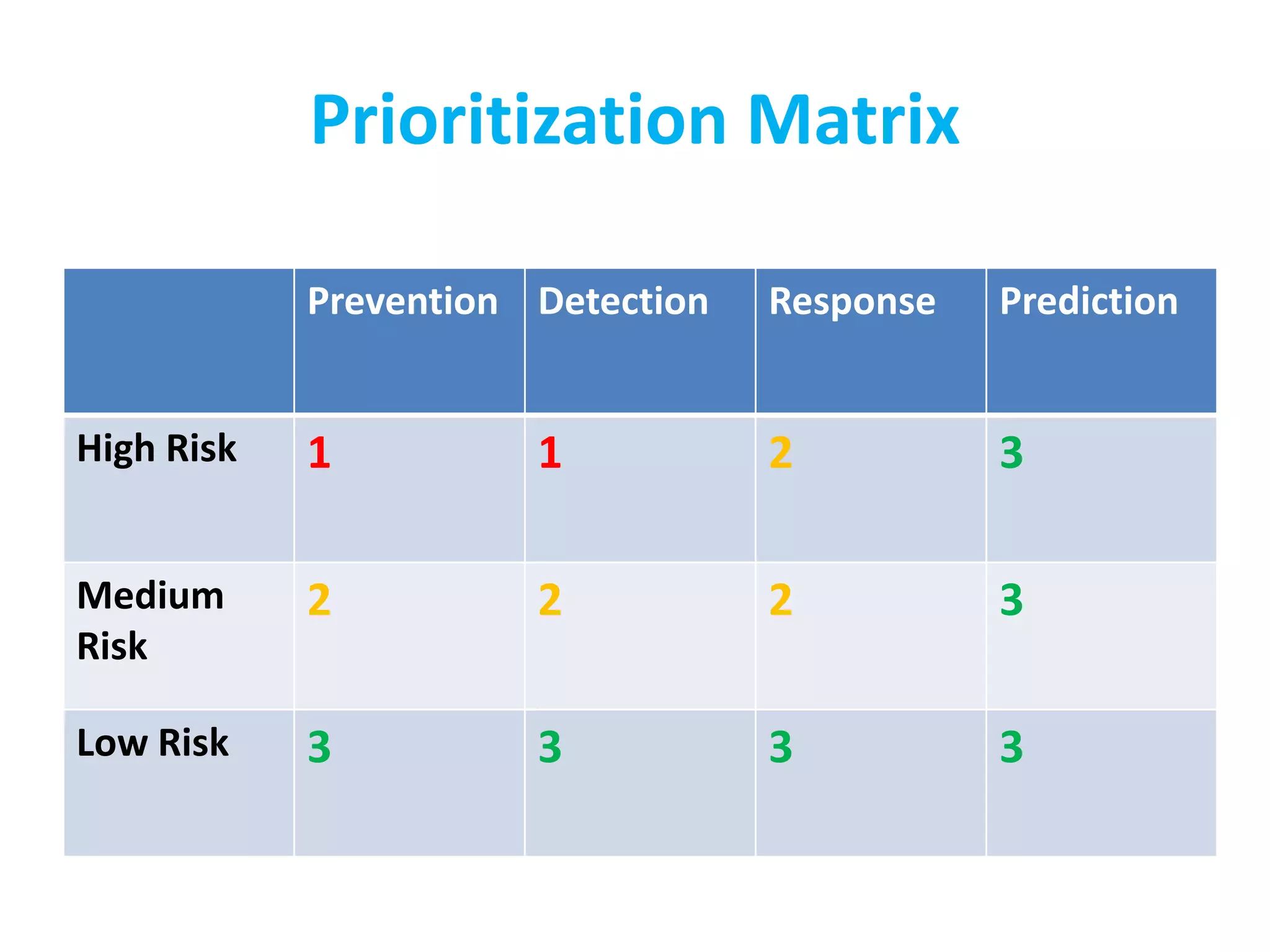


The document discusses the challenges of existing security models, highlighting their complexity and lack of prioritization. It introduces the CISO Platform Security Strategy Model (CP-SSM), which aims to offer a minimalist and focused approach to security strategy through threat modeling and prioritization. Key elements include a threat repository, prioritization guidelines, and a mapping between threats and controls.












