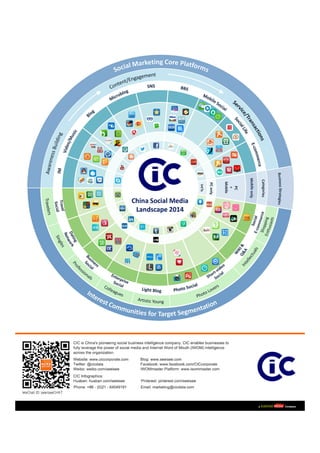
CIC 2014 China Social Media Landscape
•
2 likes•1,681 views
CIC has witnessed dynamic changes in the China Social Media Landscape for the 6th year. In the past year, we have seen that different social and digital platforms offer different marketing value propositions, and the rapid surge in access of mobile internet has generated a much faster and deeper impact in China, compared to other western markets. Read more: http://lnkd.in/bQhKsNC
Report
Share
Report
Share
Download to read offline
Recommended
CIC 2014 中国社会化媒体格局概览

CIC根据各平台的营销价值将整体社媒体平台划分为“社会化营销核心平台”和“消费者细分兴趣社区”两大类,同时对桌面和移动端平台进行了划分。中国社媒体格局会进一步呈现移动、细分、服务、交易、数据整合等趋势。
CIC联合奥美公关发布《2013微时代危机管理白皮书》

随着消费者维权意识的增强,“3.15”消费者权益保护日成为企业和品牌危机集中曝光的时期,往往引发较大的讨论声量和舆论关注。基于此,CIC再度联合奥美公关发布《2013微时代危机管理白皮书》,针对2013年度20个微博品牌危机管理案例进行统计分析,指出危机爆发后企业应不过早对事件下结论,但需第一时间诚恳表达对事件的关注并迅速开展行动。白皮书作为危机管理的指导手册,力图帮助企业深入理解社会化媒体时代的危机管理要则,从容应对。
Why multinationals turn to sina weibo

Most of the largest foreign firms have already started promoting their brand on sina weibo in China.
Among them Siemens, Electrolux, Microsoft, Unilever, etc.
In this presentation, given to the GlobalCOM meeting in Bangalore, I explain the benefits and features of using sina weibo for marketing in China.
By Christian Dougoud, EASTWEST PR
China luxury social media marcello coppa

Mashable Social Media Day e’ una delle manifestazioni più importanti al mondo che celebra la rivoluzione digitale, le dinamiche, le potenzialità dei social network e gli impatti da questi generate.
ltre 40 eccellenze in campo digitale hanno raccontato come ottenere risultati di successo attraverso l’utilizzo dei principali strumenti in ambito social media.
CIC & Ogilvy PR China released the latest whitepaper “2013 Crisis Management ...

To help companies better prevent and manage potential crises on World Consumer Rights Day, CIC and Ogilvy Public Relations ("Ogilvy PR") China launched their latest white paper "2013 Crisis Management in the Social Era" that analyzes the top 20 crises on Chinese microblogs last year. Advising companies to refrain from publicly jumping to conclusions at the outbreak of a crisis, the study recommends companies to immediately communicate their awareness of the crisis at hand and to promise a thorough investigation. The white paper serves as a guide in helping brands to better organize and fine-tune their crisis communication, especially on social media.
Recommended
CIC 2014 中国社会化媒体格局概览

CIC根据各平台的营销价值将整体社媒体平台划分为“社会化营销核心平台”和“消费者细分兴趣社区”两大类,同时对桌面和移动端平台进行了划分。中国社媒体格局会进一步呈现移动、细分、服务、交易、数据整合等趋势。
CIC联合奥美公关发布《2013微时代危机管理白皮书》

随着消费者维权意识的增强,“3.15”消费者权益保护日成为企业和品牌危机集中曝光的时期,往往引发较大的讨论声量和舆论关注。基于此,CIC再度联合奥美公关发布《2013微时代危机管理白皮书》,针对2013年度20个微博品牌危机管理案例进行统计分析,指出危机爆发后企业应不过早对事件下结论,但需第一时间诚恳表达对事件的关注并迅速开展行动。白皮书作为危机管理的指导手册,力图帮助企业深入理解社会化媒体时代的危机管理要则,从容应对。
Why multinationals turn to sina weibo

Most of the largest foreign firms have already started promoting their brand on sina weibo in China.
Among them Siemens, Electrolux, Microsoft, Unilever, etc.
In this presentation, given to the GlobalCOM meeting in Bangalore, I explain the benefits and features of using sina weibo for marketing in China.
By Christian Dougoud, EASTWEST PR
China luxury social media marcello coppa

Mashable Social Media Day e’ una delle manifestazioni più importanti al mondo che celebra la rivoluzione digitale, le dinamiche, le potenzialità dei social network e gli impatti da questi generate.
ltre 40 eccellenze in campo digitale hanno raccontato come ottenere risultati di successo attraverso l’utilizzo dei principali strumenti in ambito social media.
CIC & Ogilvy PR China released the latest whitepaper “2013 Crisis Management ...

To help companies better prevent and manage potential crises on World Consumer Rights Day, CIC and Ogilvy Public Relations ("Ogilvy PR") China launched their latest white paper "2013 Crisis Management in the Social Era" that analyzes the top 20 crises on Chinese microblogs last year. Advising companies to refrain from publicly jumping to conclusions at the outbreak of a crisis, the study recommends companies to immediately communicate their awareness of the crisis at hand and to promise a thorough investigation. The white paper serves as a guide in helping brands to better organize and fine-tune their crisis communication, especially on social media.
Deve se substituir um solenóide sempre que o código de falhas acusar defeito ...

Diagnóstico Cambio automático defeito eletroválvula com DTC, deve ser trocado sempre a válvula?
2014 from social business to big data white paper insights from cic's 2013-20...

Kantar Media CIC published “From Social Media to Social Business” white paper series from 2011, which helped enterprises develop their understanding of Chinese social media and ultimately realize their social business objectives. Nowadays, in order to promote enterprises’ implement of social business, Kantar Media CIC officially releases Social Business white paper, From Social Business to Big Data: Insights from Kantar Media CIC’s 2013-2014 China Enterprise Social Business Survey.This book conducts an online survey by distributing questionnaires among more than 390 respondents who come from over 30 industries, to collect extensive attitudes and perceptions towards social business from professionals of various functional departments,and provides suggestions for the organizations which are (or will be) undergoing social business changes.
Digital Jungle Credentials - Cross Cultural Digital Marketing Agency

Digital Jungle is a cross cultural digital marketing Agency that works with Western organizations to market to a Chinese audience; living in China or abroad. This presentation outlines the Agency Credentials. A presentation that provides an overview of our Chinese focused digital marketing services including the digital channels used such as social, search, online media and email to amplify and echo key communication messages. Further, this presentation outlines the services, products and case studies.
Digital in 2017: Eastern Asia

All the stats, data, and trends you need to understand the state of the internet, social media, and mobile in Eastern Asia in 2017. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read all the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
Digital in 2017: Southern Europe

All the stats, data, and trends you need to understand the state of the internet, social media, and mobile in Southern Europe in 2017. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read all the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
2016 Digital Yearbook

This companion report to We Are Social's comprehensive new Digital in 2016 report presents headline internet, social and mobile data for 232 countries around the world. Each country snapshot is presented as its own infographic, ready to be copy-pasted direct into your own presentations or web content. For a more insightful analysis of the numbers in this report, please visit http://bit.ly/DSM2016ES.
2017 Digital Yearbook

A snapshot of internet, social media, and mobile use in every country in the world. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
Digital in 2017 Global Overview

A teaser of what's to come in We Are Social and Hootsuite's full Digital in 2017 report, which we'll be publishing very soon.
Digital in 2016

We Are Social's comprehensive new Digital in 2016 report presents internet, social media, and mobile usage statistics and trends from all over the world. It contains more than 500 infographics, including global data snapshots, regional overviews, and in-depth profiles of the digital landscapes in 30 of the world's key economies. For a more insightful analysis of the numbers contained in this report, please visit http://bit.ly/DSM2016ES.
8 Tips for Scaling Mobile Users in China by Edith Yeung

8 tips for scaling mobile users in china and what can we learn from Uber growth in China. Presented at Launch Festival 2016.
Mobile Is Eating the World (2016)

In this update of his past presentations on Mobile Eating the World -- delivered most recently at The Guardian's Changing Media Summit -- a16z’s Benedict Evans takes us through how technology is universal through mobile. How mobile is not a subset of the internet anymore. And how mobile (and accompanying trends of cloud and AI) is also driving new productivity tools.
In fact, mobile -- which encompasses everything from drones to cars -- is everything.
2014 从社会化商业迈向大数据白皮书 来自2013-2014中国企业社会化商业调研的洞察

Kantar Media CIC继11年始,连续三年推出《社会化商业白皮书》,帮助企业从无到有建立起对中国社会化媒体和社会化商业的理解。而现在,为了帮助更多企业具象化地了解如何实施社会化商业,Kantar Media CIC正式发布《从社会化商业迈向大数据》白皮书---来自2013-2014中国企业社会化商业调研的洞察,通过对390多个覆盖超过30个行业的受访者进行在线调研,将企业各职能部门人士对社会化商业的态度和理解做出深入分析,也给正在或者即将处于社会化商业变革下的组织提供商业化进阶的建议。
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released “2013 White Paper on Travellers - The Rise of Social Travel ” today. This white paper collects and analyzes the information related to social media, maps out five types of travellers active on social media - business travellers, self-drive travellers, package tourists, luxury shopping travellers and backpackers, and has identified their unique attitudes to travel and different consumption behaviours, aiming to help brand marketers develop more effective and targeted marketing strategies.
CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》

CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》。该白皮书通过收集和深入分析社交媒体讨论以及相关信息,将中国旅行者分为五大类型:商旅人群、跟团客、自驾族、奢侈购物游人群和背包客(按在线讨论热烈程度由低到高排列),并对他们对旅行的不同的态度和差异化的消费行为特征进行了分析,旨在帮助品牌更加精准地制定市场战略。
CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》

CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》。该白皮书通过收集和深入分析社交媒体讨论以及相关信息,将中国旅行者分为五大类型:商旅人群、跟团客、自驾族、奢侈购物游人群和背包客(按在线讨论热烈程度由低到高排列),并对他们对旅行的不同的态度和差异化的消费行为特征进行了分析,旨在帮助品牌更加精准地制定市场战略。
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released “2013 White Paper on Travellers - The Rise of Social Travel ” today. This white paper collects and analyzes the information related to social media, maps out five types of travellers active on social media - business travellers, self-drive travellers, package tourists, luxury shopping travellers and backpackers, and has identified their unique attitudes to travel and different consumption behaviours, aiming to help brand marketers develop more effective and targeted marketing strategies.
Viral Video Cinema vol.20:Stop Motion Animation Collection

In a digital age, there’s something quite satisfying about seeing traditional techniques put into practice.
In this collection, we’ve listed the top 6 stop-motion animation ads for your viewing pleasure.
More Related Content
Viewers also liked
Deve se substituir um solenóide sempre que o código de falhas acusar defeito ...

Diagnóstico Cambio automático defeito eletroválvula com DTC, deve ser trocado sempre a válvula?
2014 from social business to big data white paper insights from cic's 2013-20...

Kantar Media CIC published “From Social Media to Social Business” white paper series from 2011, which helped enterprises develop their understanding of Chinese social media and ultimately realize their social business objectives. Nowadays, in order to promote enterprises’ implement of social business, Kantar Media CIC officially releases Social Business white paper, From Social Business to Big Data: Insights from Kantar Media CIC’s 2013-2014 China Enterprise Social Business Survey.This book conducts an online survey by distributing questionnaires among more than 390 respondents who come from over 30 industries, to collect extensive attitudes and perceptions towards social business from professionals of various functional departments,and provides suggestions for the organizations which are (or will be) undergoing social business changes.
Digital Jungle Credentials - Cross Cultural Digital Marketing Agency

Digital Jungle is a cross cultural digital marketing Agency that works with Western organizations to market to a Chinese audience; living in China or abroad. This presentation outlines the Agency Credentials. A presentation that provides an overview of our Chinese focused digital marketing services including the digital channels used such as social, search, online media and email to amplify and echo key communication messages. Further, this presentation outlines the services, products and case studies.
Digital in 2017: Eastern Asia

All the stats, data, and trends you need to understand the state of the internet, social media, and mobile in Eastern Asia in 2017. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read all the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
Digital in 2017: Southern Europe

All the stats, data, and trends you need to understand the state of the internet, social media, and mobile in Southern Europe in 2017. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read all the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
2016 Digital Yearbook

This companion report to We Are Social's comprehensive new Digital in 2016 report presents headline internet, social and mobile data for 232 countries around the world. Each country snapshot is presented as its own infographic, ready to be copy-pasted direct into your own presentations or web content. For a more insightful analysis of the numbers in this report, please visit http://bit.ly/DSM2016ES.
2017 Digital Yearbook

A snapshot of internet, social media, and mobile use in every country in the world. This report is part of a suite of reports brought to you by We Are Social and Hootsuite - read the other reports for free at http://www.slideshare.net/wearesocialsg/presentations
Digital in 2017 Global Overview

A teaser of what's to come in We Are Social and Hootsuite's full Digital in 2017 report, which we'll be publishing very soon.
Digital in 2016

We Are Social's comprehensive new Digital in 2016 report presents internet, social media, and mobile usage statistics and trends from all over the world. It contains more than 500 infographics, including global data snapshots, regional overviews, and in-depth profiles of the digital landscapes in 30 of the world's key economies. For a more insightful analysis of the numbers contained in this report, please visit http://bit.ly/DSM2016ES.
8 Tips for Scaling Mobile Users in China by Edith Yeung

8 tips for scaling mobile users in china and what can we learn from Uber growth in China. Presented at Launch Festival 2016.
Mobile Is Eating the World (2016)

In this update of his past presentations on Mobile Eating the World -- delivered most recently at The Guardian's Changing Media Summit -- a16z’s Benedict Evans takes us through how technology is universal through mobile. How mobile is not a subset of the internet anymore. And how mobile (and accompanying trends of cloud and AI) is also driving new productivity tools.
In fact, mobile -- which encompasses everything from drones to cars -- is everything.
Viewers also liked (15)
Deve se substituir um solenóide sempre que o código de falhas acusar defeito ...

Deve se substituir um solenóide sempre que o código de falhas acusar defeito ...
2014 from social business to big data white paper insights from cic's 2013-20...

2014 from social business to big data white paper insights from cic's 2013-20...
China Internet Influencers - Nov 2011 [Edith Yeung]![China Internet Influencers - Nov 2011 [Edith Yeung]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![China Internet Influencers - Nov 2011 [Edith Yeung]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
China Internet Influencers - Nov 2011 [Edith Yeung]
Digital Jungle Credentials - Cross Cultural Digital Marketing Agency

Digital Jungle Credentials - Cross Cultural Digital Marketing Agency
8 Tips for Scaling Mobile Users in China by Edith Yeung

8 Tips for Scaling Mobile Users in China by Edith Yeung
More from Kantar Media CIC
2014 从社会化商业迈向大数据白皮书 来自2013-2014中国企业社会化商业调研的洞察

Kantar Media CIC继11年始,连续三年推出《社会化商业白皮书》,帮助企业从无到有建立起对中国社会化媒体和社会化商业的理解。而现在,为了帮助更多企业具象化地了解如何实施社会化商业,Kantar Media CIC正式发布《从社会化商业迈向大数据》白皮书---来自2013-2014中国企业社会化商业调研的洞察,通过对390多个覆盖超过30个行业的受访者进行在线调研,将企业各职能部门人士对社会化商业的态度和理解做出深入分析,也给正在或者即将处于社会化商业变革下的组织提供商业化进阶的建议。
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released “2013 White Paper on Travellers - The Rise of Social Travel ” today. This white paper collects and analyzes the information related to social media, maps out five types of travellers active on social media - business travellers, self-drive travellers, package tourists, luxury shopping travellers and backpackers, and has identified their unique attitudes to travel and different consumption behaviours, aiming to help brand marketers develop more effective and targeted marketing strategies.
CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》

CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》。该白皮书通过收集和深入分析社交媒体讨论以及相关信息,将中国旅行者分为五大类型:商旅人群、跟团客、自驾族、奢侈购物游人群和背包客(按在线讨论热烈程度由低到高排列),并对他们对旅行的不同的态度和差异化的消费行为特征进行了分析,旨在帮助品牌更加精准地制定市场战略。
CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》

CIC与群邑智库联合发布2013旅游行业白皮书《社会化旅游的崛起》。该白皮书通过收集和深入分析社交媒体讨论以及相关信息,将中国旅行者分为五大类型:商旅人群、跟团客、自驾族、奢侈购物游人群和背包客(按在线讨论热烈程度由低到高排列),并对他们对旅行的不同的态度和差异化的消费行为特征进行了分析,旨在帮助品牌更加精准地制定市场战略。
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released “2013 White Paper on Travellers - The Rise of Social Travel ” today. This white paper collects and analyzes the information related to social media, maps out five types of travellers active on social media - business travellers, self-drive travellers, package tourists, luxury shopping travellers and backpackers, and has identified their unique attitudes to travel and different consumption behaviours, aiming to help brand marketers develop more effective and targeted marketing strategies.
Viral Video Cinema vol.20:Stop Motion Animation Collection

In a digital age, there’s something quite satisfying about seeing traditional techniques put into practice.
In this collection, we’ve listed the top 6 stop-motion animation ads for your viewing pleasure.
CIC中国社会化媒体格局概览图2013

CIC2013年中国社会化媒体格局图正式发布。基于各社会化媒体平台的业态成熟度以及平台之间的功能依附关系,将中国的社会化媒体平台划分为“核心网络”、“增值衍生网络”、“基础功能网络”和“新兴/细分网络”四大类。
CIC China Social Media Landscape 2013

CIC China Social Media Landscape 2013 Published. It's been an explosive 5 years since CIC articulated the 1st ChinaSocial Media Landscape in 2008 and today. We're honored to release the most up to date version of this iconic industry infographic, the CIC China Social Media Landscape 2013.
More from Kantar Media CIC (20)
Viral video cinema vol.23:content is king in video marketing

Viral video cinema vol.23:content is king in video marketing
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...
CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...

CIC and GroupM China released 2013 White Paper on Travellers - The Rise of So...
Viral Video Cinema vol.20:Stop Motion Animation Collection

Viral Video Cinema vol.20:Stop Motion Animation Collection
IWOM watch 2012 compilation_weibo development (Part 5)

IWOM watch 2012 compilation_weibo development (Part 5)
IWOM watch 2012 compilation_wechat development (Part 4)

IWOM watch 2012 compilation_wechat development (Part 4)
IWOM watch 2012 compilation_social marketing (Part 9)

IWOM watch 2012 compilation_social marketing (Part 9)
From Social Media to Social Business white paper series topic 3 :China‘s Soci...

From Social Media to Social Business white paper series topic 3 :China‘s Soci...
Recently uploaded
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
GridMate - End to end testing is a critical piece to ensure quality and avoid...

End to end testing is a critical piece to ensure quality and avoid regressions. In this session, we share our journey building an E2E testing pipeline for GridMate components (LWC and Aura) using Cypress, JSForce, FakerJS…
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
Essentials of Automations: The Art of Triggers and Actions in FME

In this second installment of our Essentials of Automations webinar series, we’ll explore the landscape of triggers and actions, guiding you through the nuances of authoring and adapting workspaces for seamless automations. Gain an understanding of the full spectrum of triggers and actions available in FME, empowering you to enhance your workspaces for efficient automation.
We’ll kick things off by showcasing the most commonly used event-based triggers, introducing you to various automation workflows like manual triggers, schedules, directory watchers, and more. Plus, see how these elements play out in real scenarios.
Whether you’re tweaking your current setup or building from the ground up, this session will arm you with the tools and insights needed to transform your FME usage into a powerhouse of productivity. Join us to discover effective strategies that simplify complex processes, enhancing your productivity and transforming your data management practices with FME. Let’s turn complexity into clarity and make your workspaces work wonders!
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Recently uploaded (20)
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
GridMate - End to end testing is a critical piece to ensure quality and avoid...

GridMate - End to end testing is a critical piece to ensure quality and avoid...
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
Essentials of Automations: The Art of Triggers and Actions in FME

Essentials of Automations: The Art of Triggers and Actions in FME
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
