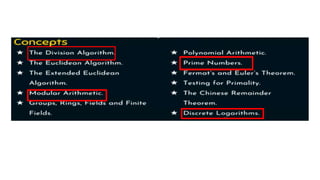
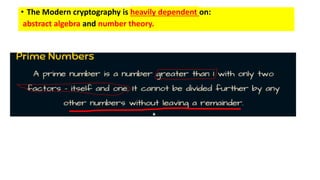
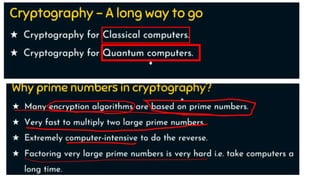
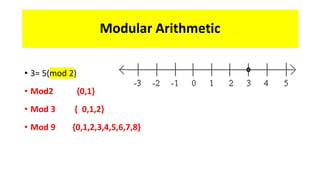
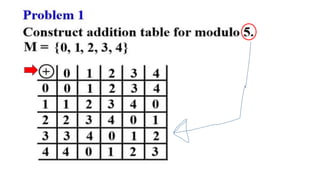
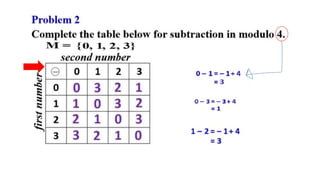
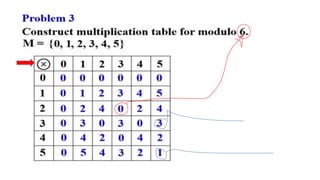
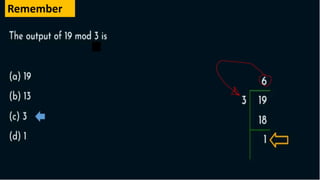
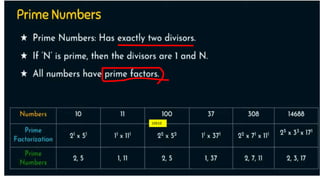
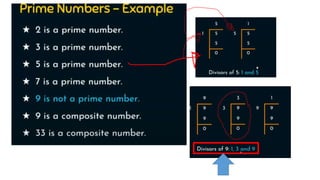
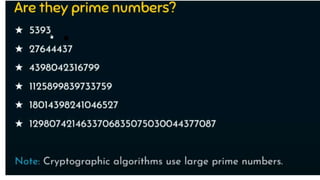
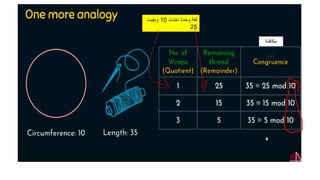
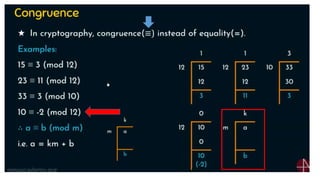
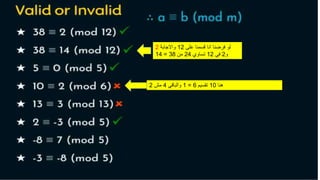
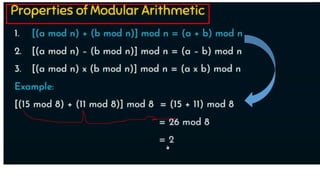
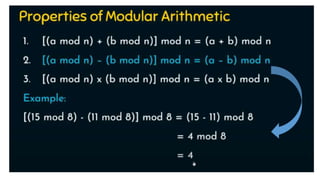
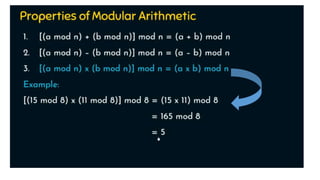
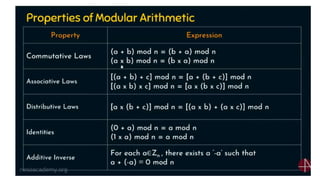
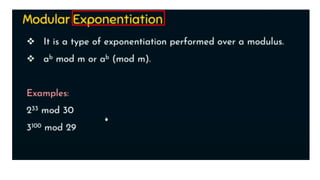
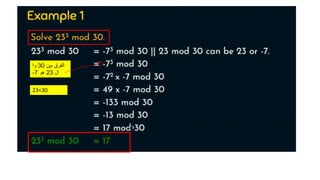
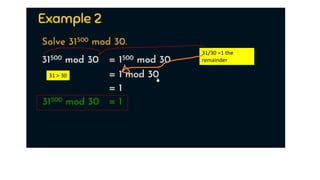
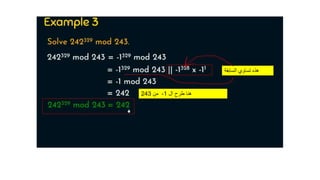
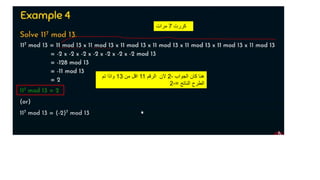
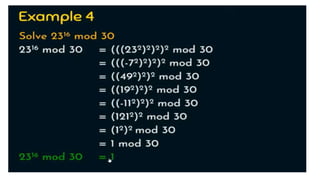
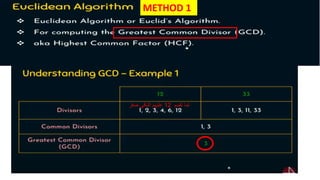
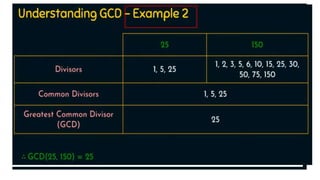
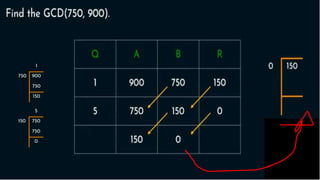
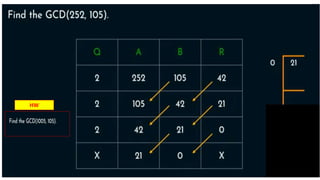
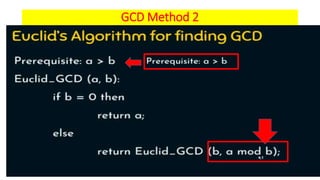
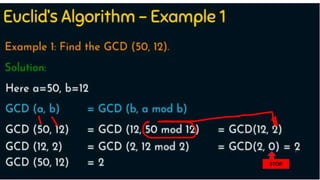
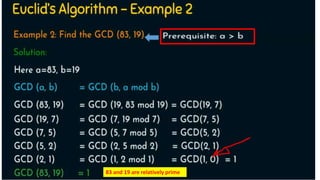
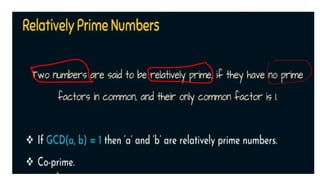
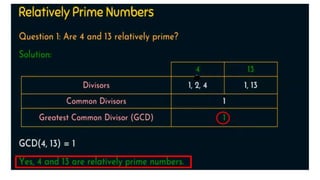
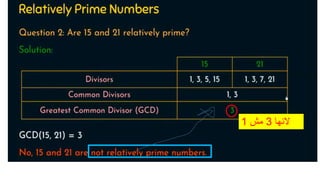
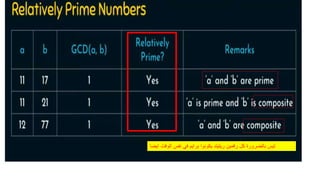
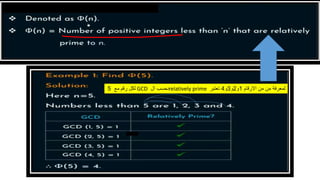
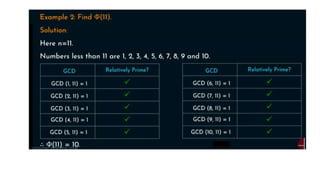
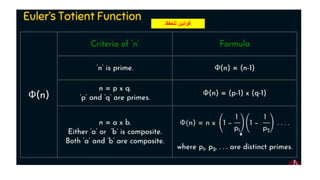
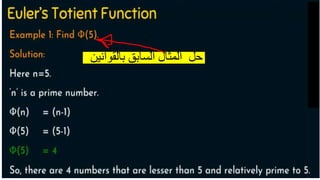
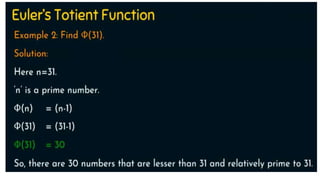
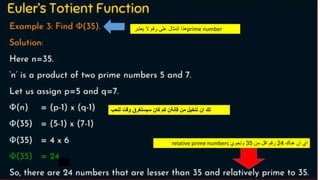
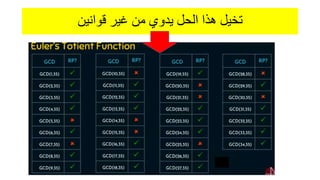
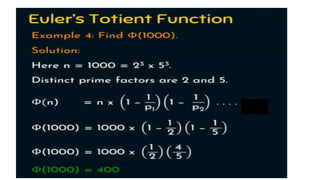
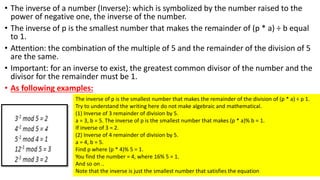
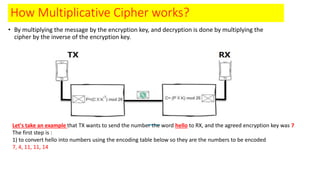
Modern cryptography relies heavily on abstract algebra and number theory. Modular arithmetic involves dividing numbers and taking the remainder. The multiplicative cipher encrypts messages by multiplying them by an encryption key, and decrypts them by multiplying the cipher by the inverse of the key. The affine cipher combines the additive and multiplicative ciphers, applying one then the other, to further strengthen security.