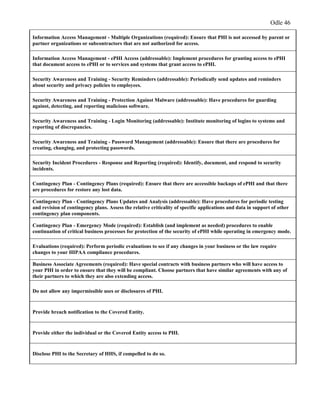
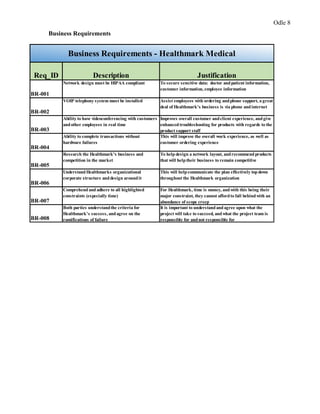
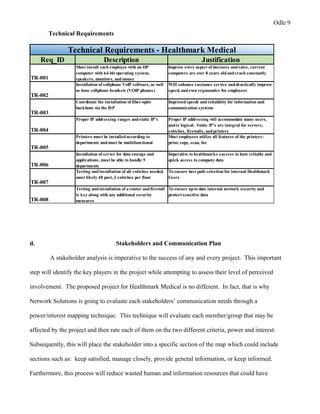
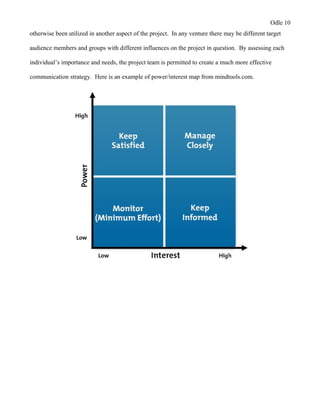
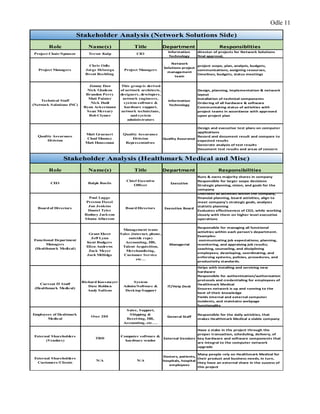
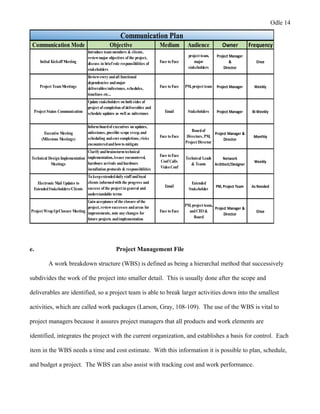
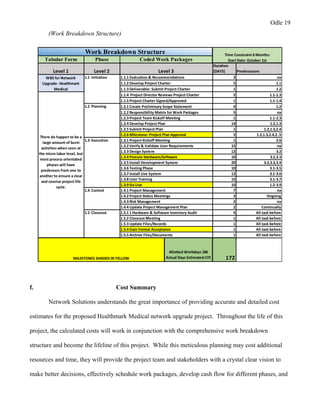
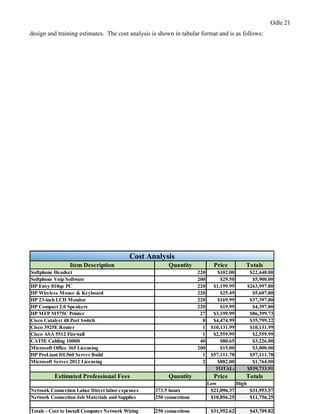
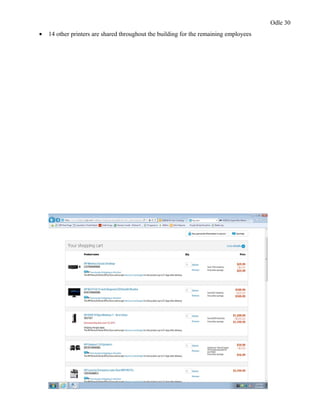
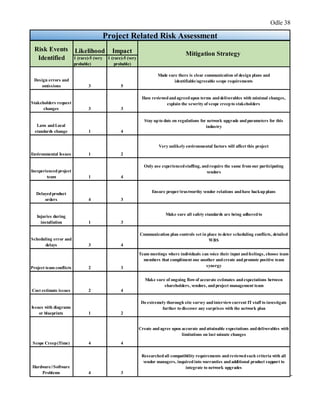
This document provides a proposal for upgrading the computer network at Healthmark Medical. It describes the current issues with their outdated network architecture and hardware, which is negatively impacting business operations. The proposed project would replace all employee computers, install a new VOIP phone system, fiber internet connection, servers, switches, and other network components. Requirements for the project are outlined, including the need for HIPAA compliance, improved network speeds, and addressing constraints like timelines. Key stakeholders are identified and a communication plan is proposed to keep everyone informed during the project. The goal is to implement the new network within six months to improve Healthmark Medical's technology and business performance.






























![Odle 42
• Office 365 Message Encryption allows you to send encrypted email to anyone.
• Data loss prevention prevents sensitive data from leaking either inside or outside the
organization.
• Data loss prevention can be combined with Rights Management and Office 365 Message
Encryption to give greater controls to your admins to apply appropriate policies to protect
sensitive data.
(products.office.com)
Additional Hardware Security (Firewall/Router)
• SecurityEmbedded hardware-accelerated VPN encryption for secure collaboration
• Integrated threat control using Cisco IOS Firewall, Zone-Based Firewall, IPS, and Content
Filtering
• Identity management using authentication, authorization, and accounting (AAA) and public key
infrastructure
• Exceptional next-generation firewall services provide the visibility and detailed control that
your enterprise needs to safely take advantage of new applications and devices.[1]
• Cisco AVC controls specific behaviors within allowed microapplications.
• Cisco Web Security Essentials (WSE) restricts web and web application use based on the
reputation of a site.
• Broad and deep network security through an array of integrated cloud- and software-based next-
generation firewall services is backed by Cisco Security Intelligence Operations (SIO).
• A highly effective intrusion prevention system (IPS) is provided with Cisco Global Correlation.
• A high-performance VPN and always-on remote access are included.](https://image.slidesharecdn.com/e7e7da13-8645-4562-8c4c-69963bff406c-151021210311-lva1-app6892/85/Capstone-Final-Project-42-320.jpg)