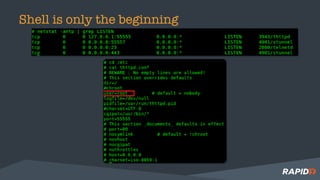
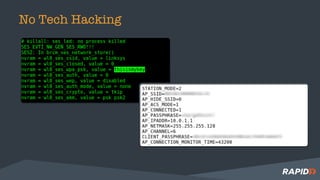
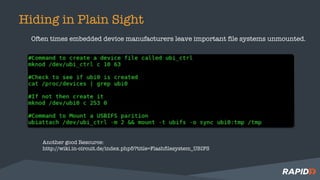
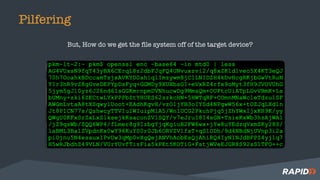
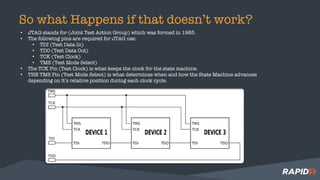
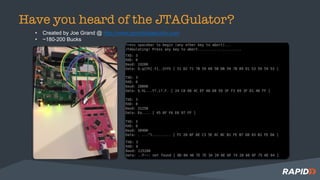
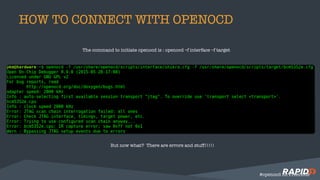
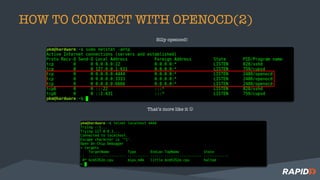
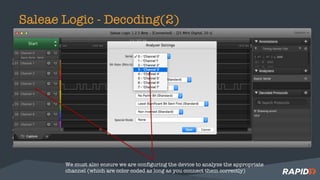
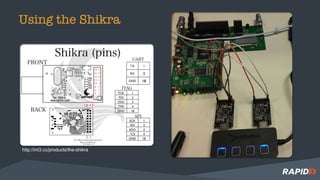
The document discusses hardware security assessments of Internet of Things (IoT) devices. It provides tips for obtaining cheap IoT devices, identifying device components, interfacing with devices using logic analyzers and hardware debugging tools, extracting file systems, and performing reverse engineering. Methods covered include identifying interfaces like UART and JTAG, using tools like Saleae Logic, Bus Pirate, Shikra, and OpenOCD, and reversing binaries with tools like Binary Ninja, IDA Pro, and Radare2.
















![Connecting to UART
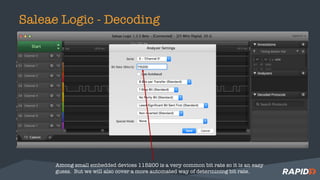
The command used to connect to a UART serial adapter will vary by
device and OS but will generally be similar to the command below.
sudo screen /dev/[device id] baud rate
Or the the case of the Device ID below for the Shikra:
sudo screen /dev/ttyUSB0 115200](https://image.slidesharecdn.com/bsides-puertorico-2017-180202205751/85/Bsides-Puerto-Rico-2017-23-320.jpg)