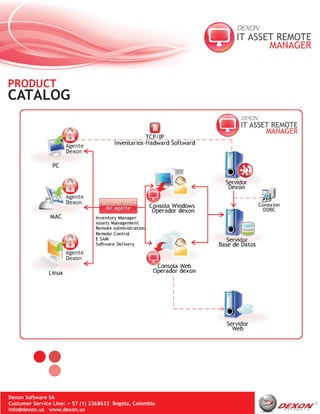
Dexon Software's DEXON ASSET REMOTE MANAGER product is designed to remotely manage, audit, and monitor an organization's entire IT infrastructure and assets. It includes modules for inventory management, asset management across the lifecycle, software license management, remote administration, remote control, and software delivery. The product aims to help organizations better align their IT with business objectives through centralized management and cost reduction.