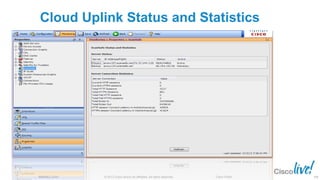
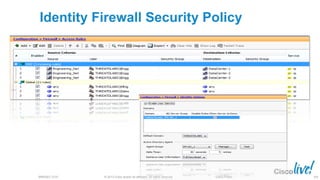
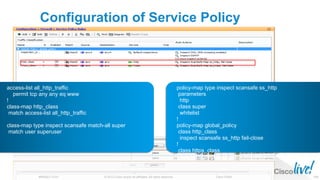
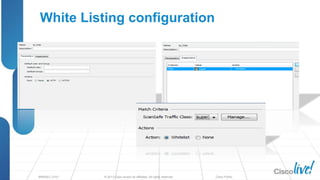
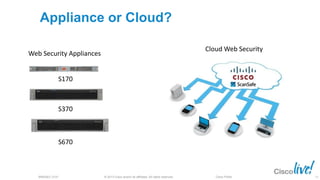
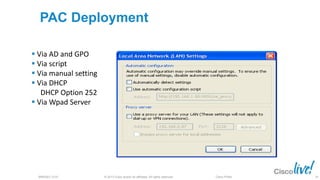
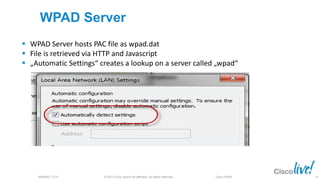
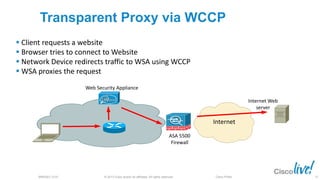
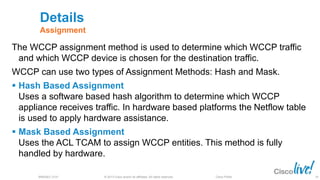
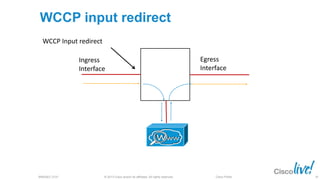
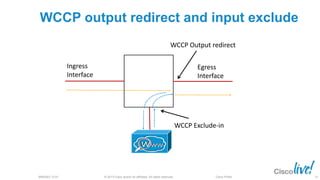
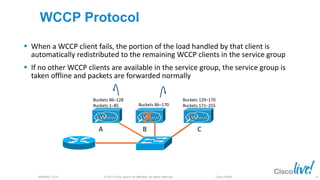
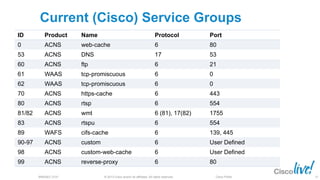
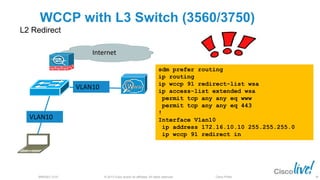
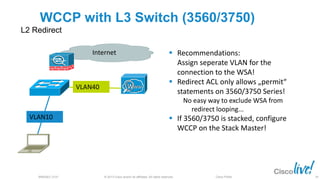
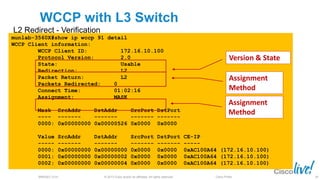
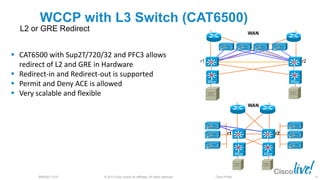
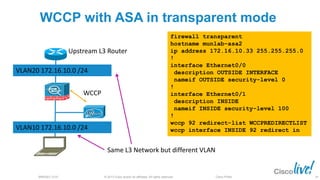
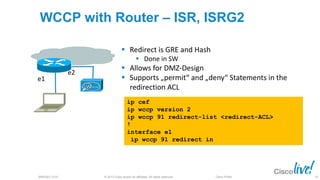
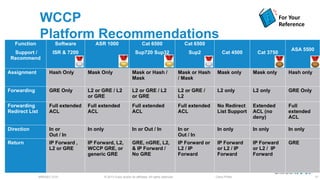
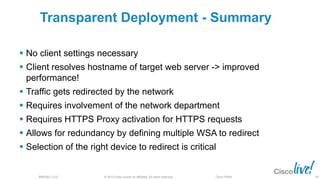
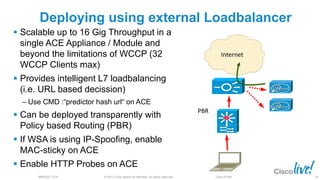
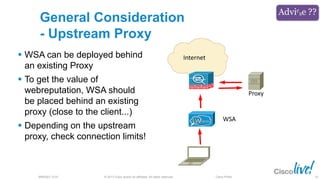
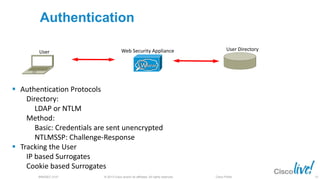
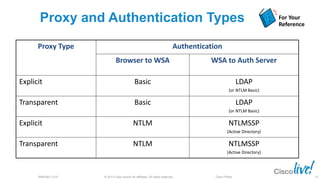
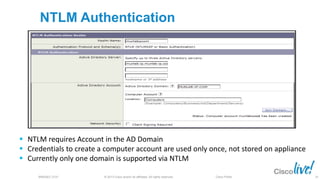
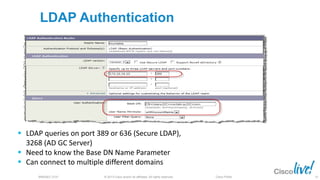
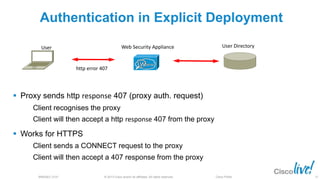
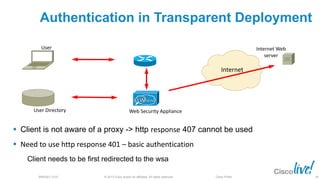
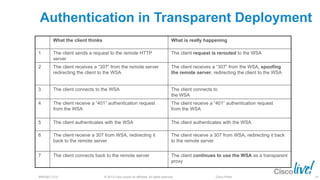
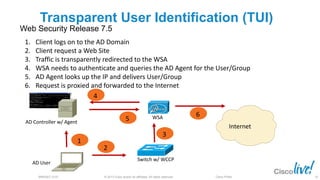
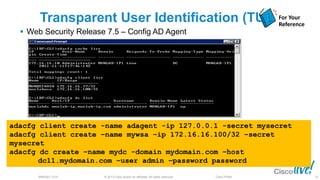
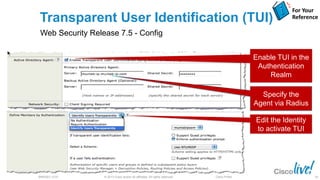
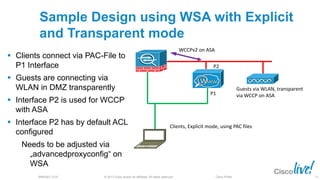
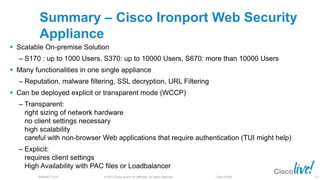
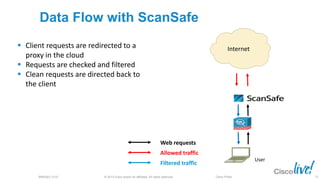
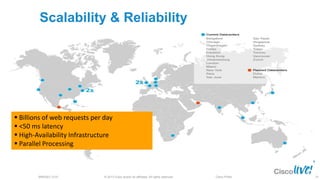
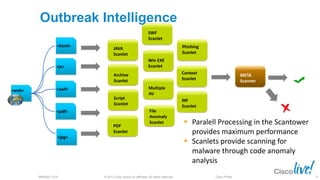
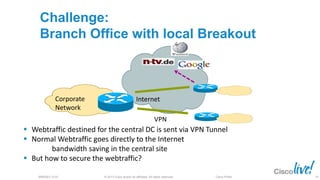
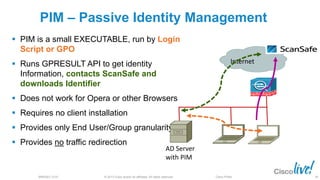
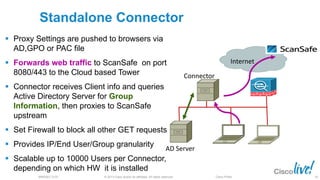
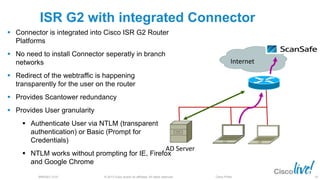
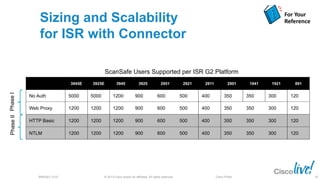
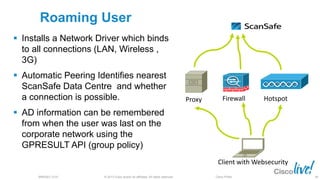
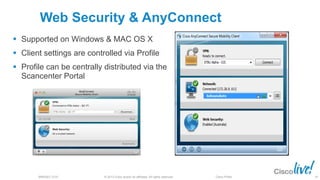
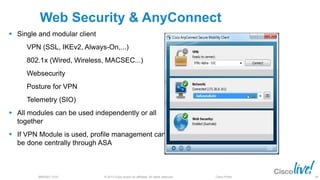
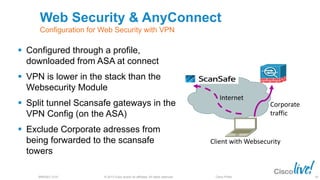
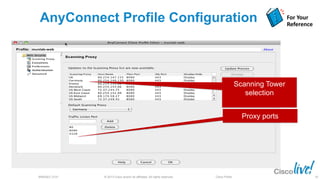
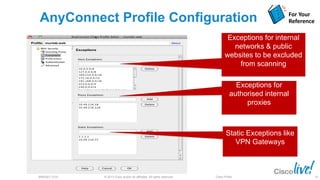
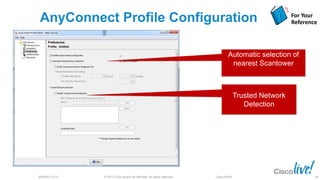
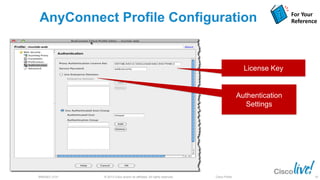
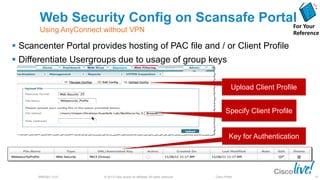
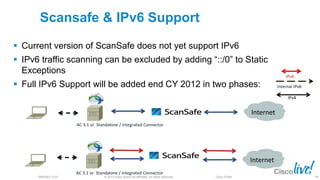
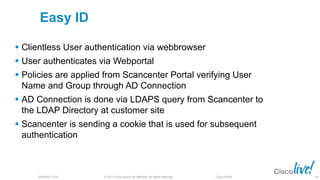
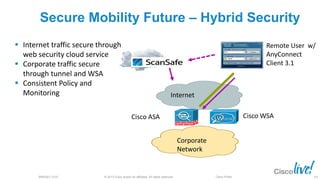
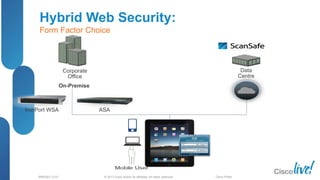
The document discusses deploying web security through Cisco's web security appliances and cloud web security. It provides an overview of web security and describes Cisco's appliance and cloud-based options. It also covers how to configure the Cisco web security appliance for explicit and transparent proxy deployment using protocols like WCCP (Web Cache Communication Protocol) for traffic redirection.








































![© 2013 Cisco and/or its affiliates. All rights reserved.BRKSEC-2101 Cisco Public 106
Configuration Parameters
Cisco Cloud Web Security General Options
[no] server {primary | backup} {ip <ip-address> | fqdn <fqdn>} [port <port-no>]
[no] retry-count <2 - 100>
[no] license <16 byte Hex key>
Configured in system context when the
ASA is running in multiple
context mode](https://image.slidesharecdn.com/brksec-2101deployingwebsecurity-150513145818-lva1-app6891/85/Brksec-2101-deploying-web-security-106-320.jpg)