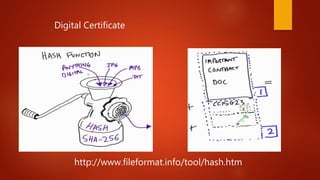
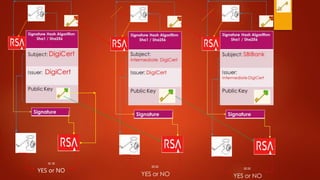
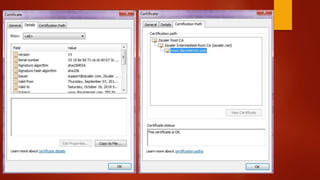
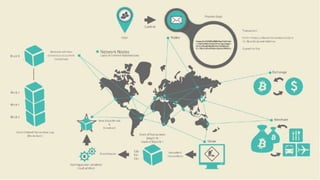
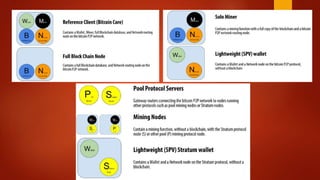
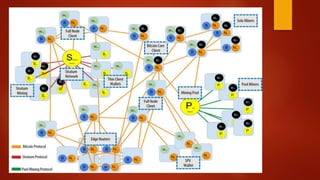
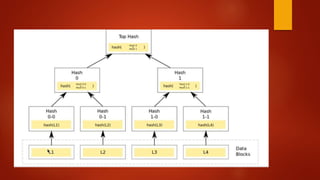
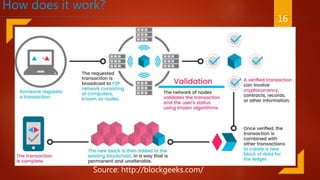
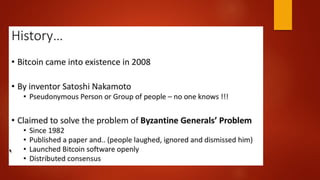
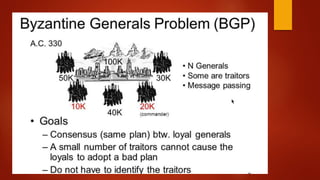
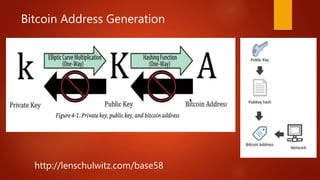
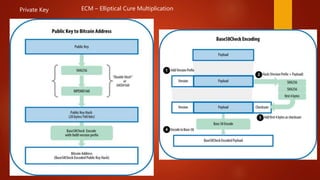
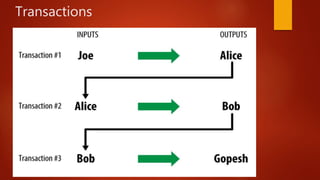
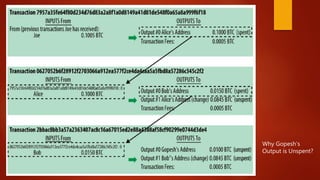
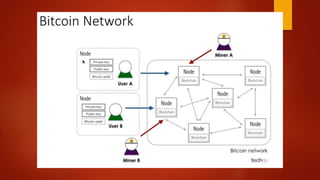
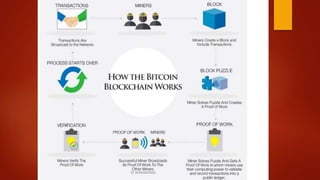
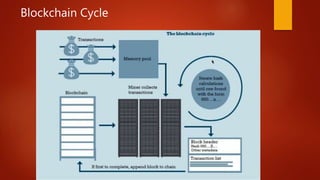
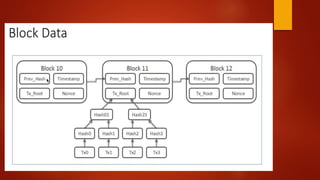
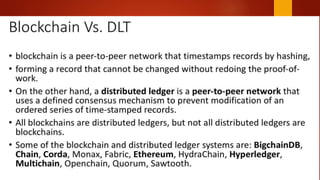
Blockchain is a decentralized ledger or list of all transactions across a peer-to-peer network. It underlies technologies like Bitcoin and has potential to disrupt many business processes. No single user controls the blockchain, transactions are broadcast to the network and validated through consensus. The author of the blockchain concept is unknown, thought to use the pseudonym Satoshi Nakamoto. Blockchains use techniques like proof-of-work to serialize changes and achieve distributed consensus to maintain integrity without centralized authority.





























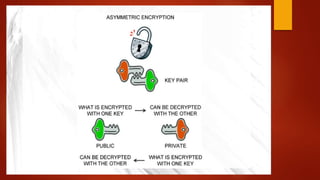

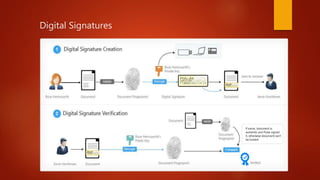



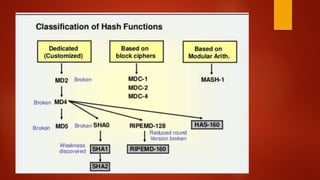

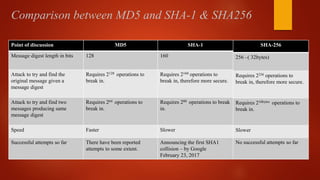
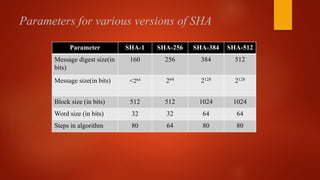
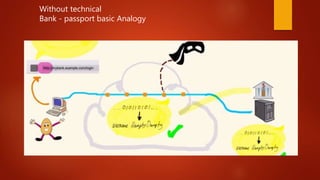

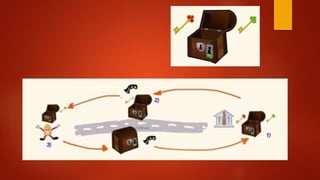
![Whole Process
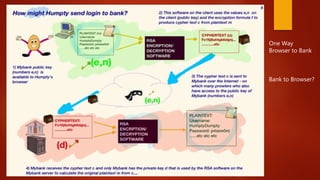
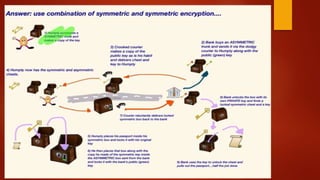
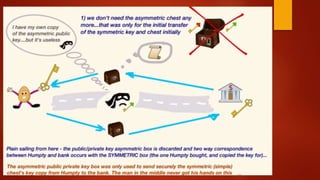
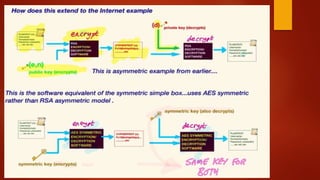
Client send req to the server
Server sends res to the Client [public key and certificate] Has Private key
installed
Client send one of the symmetric key to the server
Encrypted with server public key
Secure End – to – End Communication with symetic](https://image.slidesharecdn.com/blockchain-180127102043/85/Blockchain-Corporate-Style-72-320.jpg)