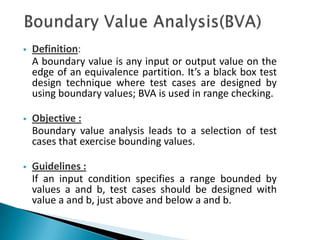
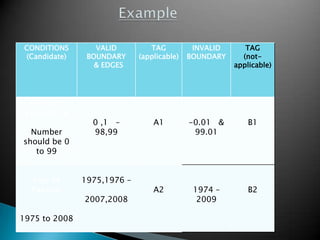
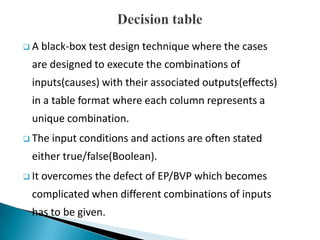
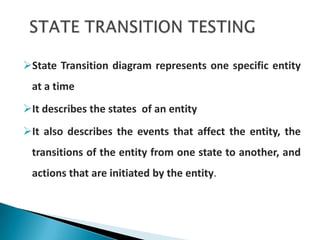
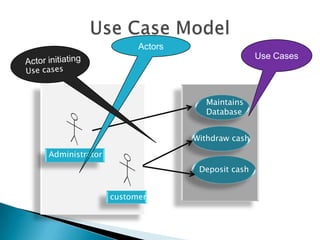
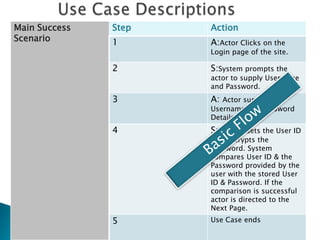
The document discusses the equivalence partitioning (EP) technique for black-box testing. It states that EP divides test conditions into groups called partitions that can be considered the same. Only one test case per partition needs to be tested. An example given partitions a bank account balance into valid and invalid ranges, with boundaries like $0.00. Guidelines for boundary value analysis are provided, such as testing values just above and below boundaries. Other techniques discussed include boundary value analysis, decision table testing, and state transition testing.