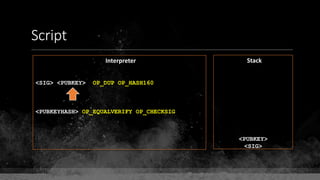
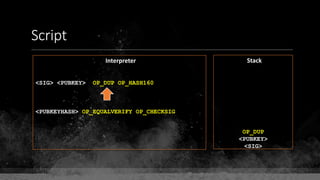
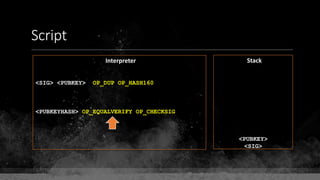
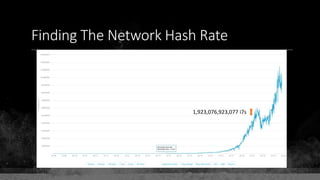
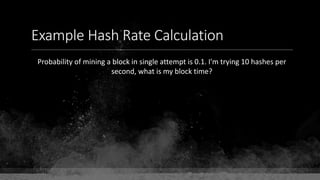
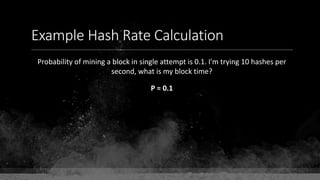
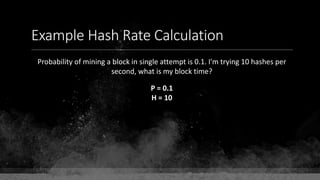
The document provides a comprehensive overview of Bitcoin fundamentals, focusing on the structure and functionality of its blockchain. It defines key components like blocks, transactions, and addresses while emphasizing Bitcoin's status as the first and most secure blockchain. The document also touches on the relationship between private keys, public keys, and Bitcoin addresses.





















































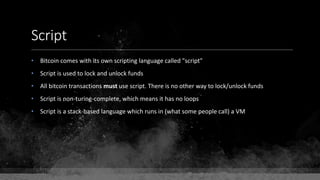
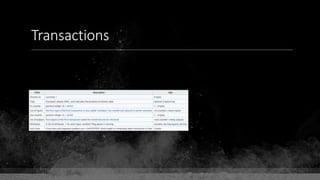
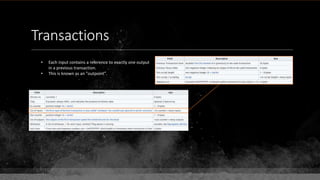
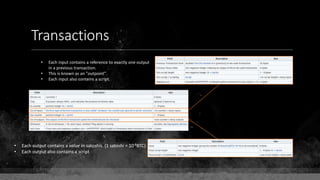
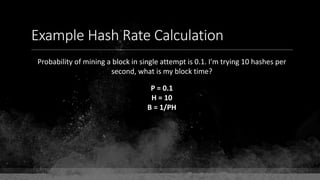
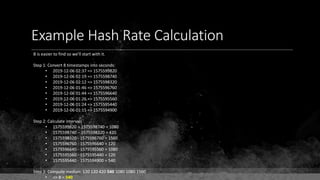
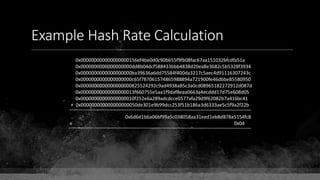
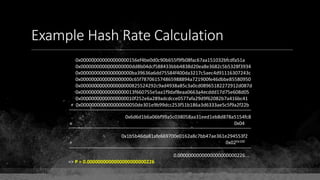
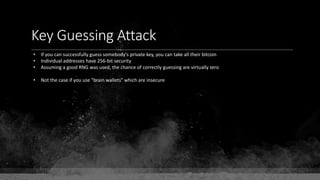
![Keys & Addresses
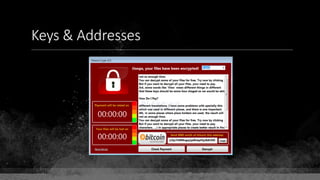
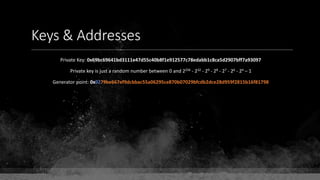
Private Key: 0x69bc69641bd3111e47d55c40b8f1e912577c78edabb1c8ca5d2907bff7a93097
Private key is just a random number between 0 and 2256 - 232 - 29 - 28 - 27 - 26 - 24 – 1
Generator point: 0x0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
To get the unique public key for this private key, we add the generator point to itself private key times.
Public key: 0x0380864b7759a43923d2d0c99b142843fc306199a94995e55cb204d9a91fa09feb
PubkeyHash = SHA256(RipeMD160(Public Key)) = 0xd8e5899f2589b7fa9df2513bf2366d2031f2d478
VersionByte (0x00) | PubkeyHash = 0x00d8e5899f2589b7fa9df2513bf2366d2031f2d478
SHA2562(VersionByte | PubkeyHash)[:4] (Checksum) = 0x08c131a4](https://image.slidesharecdn.com/bitcoin-fundamentals-200707114103/85/Bitcoin-fundamentals-61-320.jpg)
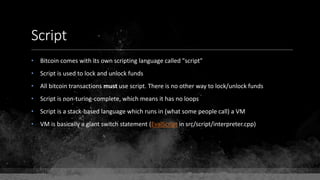
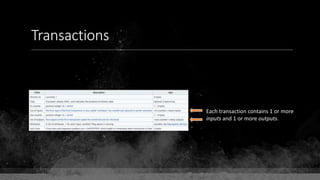
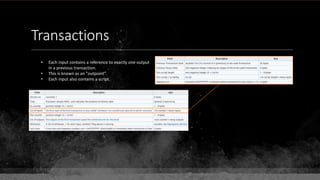
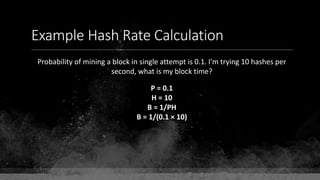
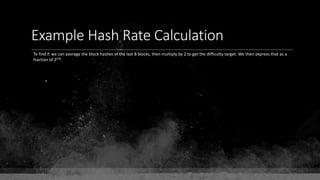
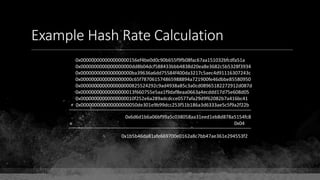
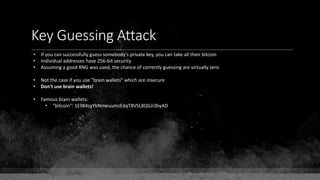
![Keys & Addresses
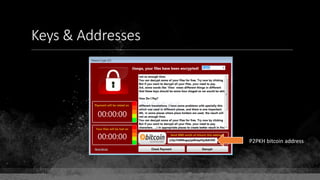
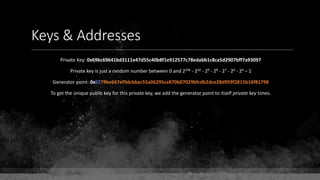
Private Key: 0x69bc69641bd3111e47d55c40b8f1e912577c78edabb1c8ca5d2907bff7a93097
Private key is just a random number between 0 and 2256 - 232 - 29 - 28 - 27 - 26 - 24 – 1
Generator point: 0x0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
To get the unique public key for this private key, we add the generator point to itself private key times.
Public key: 0x0380864b7759a43923d2d0c99b142843fc306199a94995e55cb204d9a91fa09feb
PubkeyHash = SHA256(RipeMD160(Public Key)) = 0xd8e5899f2589b7fa9df2513bf2366d2031f2d478
VersionByte (0x00) | PubkeyHash = 0x00d8e5899f2589b7fa9df2513bf2366d2031f2d478
SHA2562(VersionByte | PubkeyHash)[:4] (Checksum) = 0x08c131a4
VersionByte | PubkeyHash | Checksum = 0x00d8e5899f2589b7fa9df2513bf2366d2031f2d47808c131a4](https://image.slidesharecdn.com/bitcoin-fundamentals-200707114103/85/Bitcoin-fundamentals-62-320.jpg)
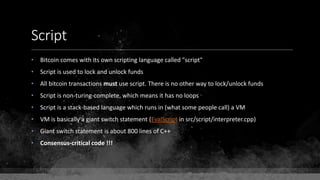
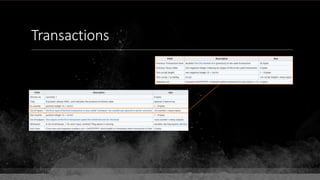
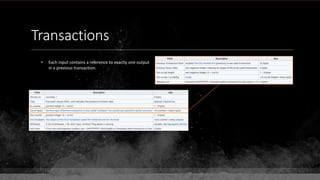
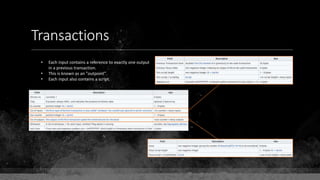
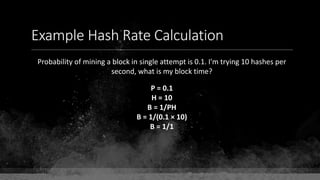
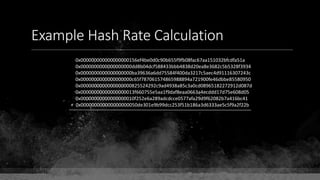
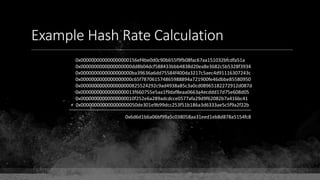
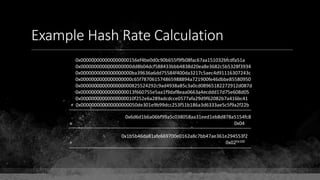
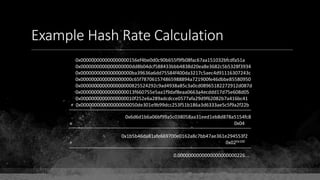
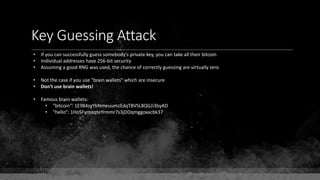
![Keys & Addresses
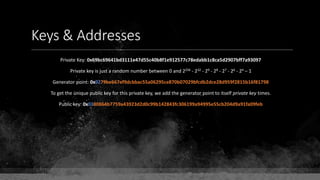
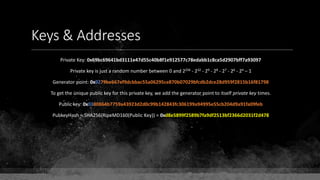
Private Key: 0x69bc69641bd3111e47d55c40b8f1e912577c78edabb1c8ca5d2907bff7a93097
Private key is just a random number between 0 and 2256 - 232 - 29 - 28 - 27 - 26 - 24 – 1
Generator point: 0x0279be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
To get the unique public key for this private key, we add the generator point to itself private key times.
Public key: 0x0380864b7759a43923d2d0c99b142843fc306199a94995e55cb204d9a91fa09feb
PubkeyHash = SHA256(RipeMD160(Public Key)) = 0xd8e5899f2589b7fa9df2513bf2366d2031f2d478
VersionByte (0x00) | PubkeyHash = 0x00d8e5899f2589b7fa9df2513bf2366d2031f2d478
SHA2562(VersionByte | PubkeyHash)[:4] (Checksum) = 0x08c131a4
VersionByte | PubkeyHash | Checksum = 0x00d8e5899f2589b7fa9df2513bf2366d2031f2d47808c131a4
Base58CheckEncode(0x00d8e5899f2589b7fa9df2513bf2366d2031f2d47808c131a4)
= 1LmqvzD5KgNs1a8tcibuiNNM1MfZxLr5pw](https://image.slidesharecdn.com/bitcoin-fundamentals-200707114103/85/Bitcoin-fundamentals-63-320.jpg)