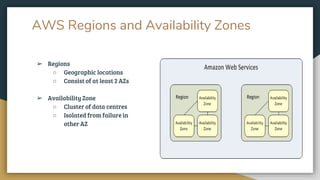
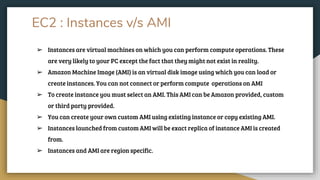
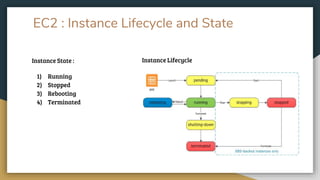
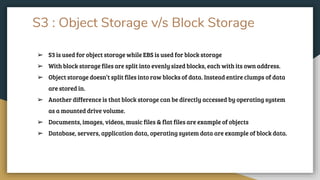
This document provides an overview of Amazon Web Services (AWS) and some of its core services. It defines AWS as a cloud platform offering over 165 services globally. Key AWS concepts discussed include Identity and Access Management (IAM) for user authentication, the AWS Console for accessing services, AWS regions and availability zones for geographic distribution of resources, and Elastic Compute Cloud (EC2) for launching virtual servers. Specific EC2 features explained are instances, AMIs, security groups, EBS volumes, and networking. The document also introduces Amazon Simple Storage Service (S3) for object storage and different storage classes.






![IAM Policies : IAM Policies are JSON
documents which you can attach
with IAM user, group or roles.
Entity permissions are controlled
using these policy documents.
For eg. this IAM policy document
limits all S3 bucket operations on
bucket “my-test-bucket” but
explicitly denying every AWS
service except S3.
AWS Identity Access Management
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::my-test-bucket",
"arn:aws:s3:::my-test-bucket/*"
]
},
{
"Effect": "Deny",
"NotAction": "s3:*",
"NotResource": [
"arn:aws:s3:::my-test-bucket",
"arn:aws:s3:::my-test-bucket/*"
]
}
]
}](https://image.slidesharecdn.com/awsbasicssession-190710151115/85/AWS-basics-session-8-320.jpg)