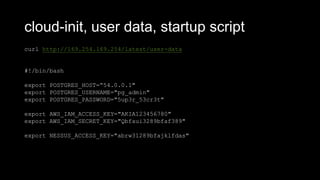
- The document summarizes common architecture flaws in AWS environments, including lack of account segmentation, improper logging configuration, insufficient alerts and monitoring, insecure secrets management, and overpermissive IAM policies. It provides examples and recommendations for addressing each issue, such as using separate AWS accounts for different environments, configuring CloudTrail, GuardDuty, and a SIEM, using HashiCorp Vault for secrets, and restricting IAM policies to specific resources. The presenter has extensive experience deploying and securing applications on AWS.















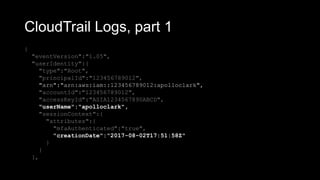
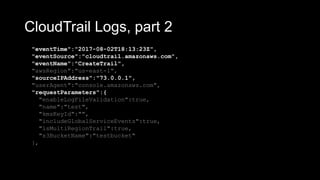
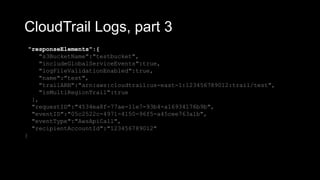
![CloudWatch Log, syslog
Jul 11 04:37:01 ip-172-31-9-199 CRON[9575]: (root) CMD
(/var/awslogs/bin/awslogs-nanny.sh > /dev/null 2>&1)
• You can create a “Log Stream”, to save logs into
an S3 bucket, for easier retrieval.](https://image.slidesharecdn.com/awsarchitectureflaws2019-05-0513-30-190506164624/85/AWS-Architecture-Flaws-18-320.jpg)



















![IAM Policy, S3 bucket, resource name
{
"Version": "2012-10-17",
"Statement": [
{
“Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:GetObjectVersion”
],
"Resource": "arn:aws:s3:*:*:CompanyA/Marketing/*"
}
]
}](https://image.slidesharecdn.com/awsarchitectureflaws2019-05-0513-30-190506164624/85/AWS-Architecture-Flaws-42-320.jpg)
![IAM Policy, EBS, resource tag
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:AttachVolume",
"ec2:DetachVolume"
],
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"StringEquals": {"ec2:ResourceTag/Department": “Marketing"}
}
}
]
}](https://image.slidesharecdn.com/awsarchitectureflaws2019-05-0513-30-190506164624/85/AWS-Architecture-Flaws-43-320.jpg)
![IAM Policy, RDS
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "rds:DescribeDBInstances",
"Resource": "*"
}
]
}](https://image.slidesharecdn.com/awsarchitectureflaws2019-05-0513-30-190506164624/85/AWS-Architecture-Flaws-44-320.jpg)






