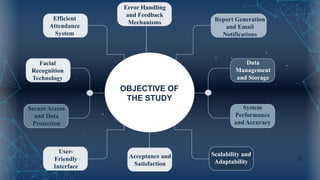
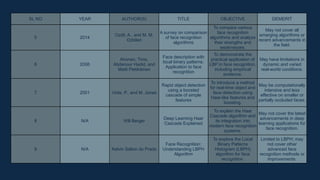
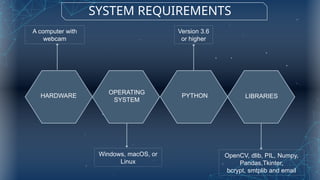
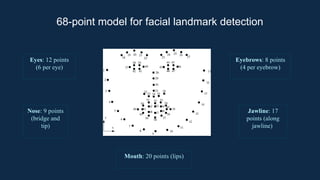
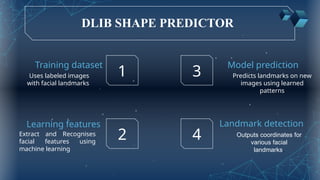
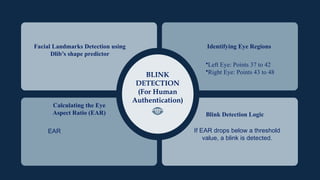
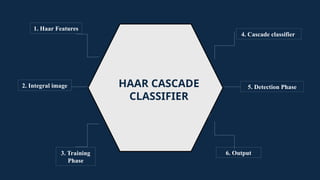
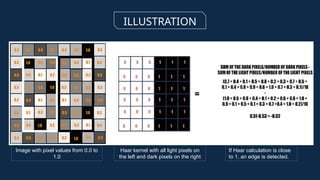
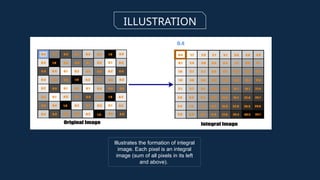
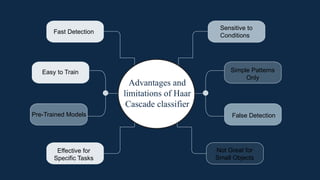
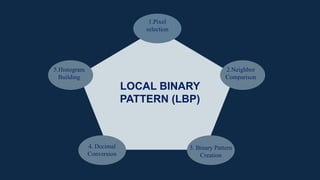
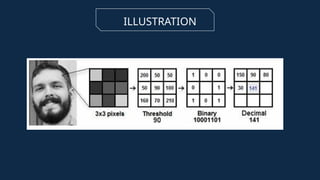
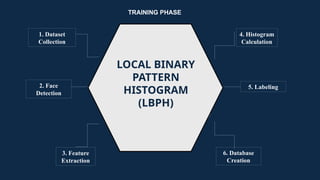
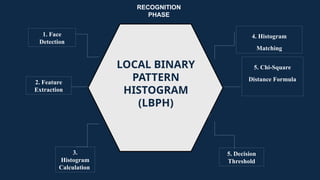
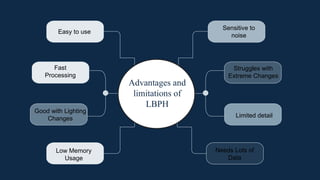
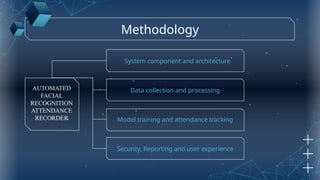
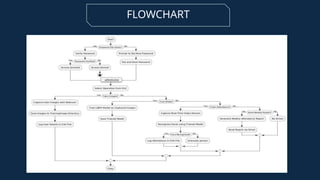
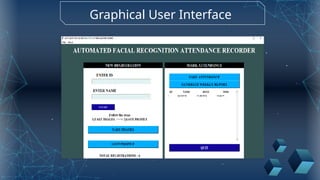
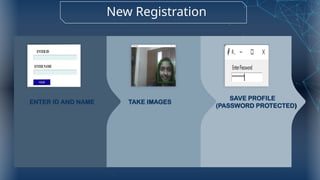
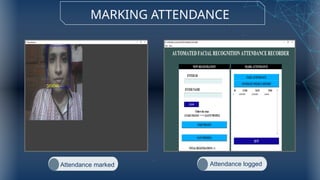
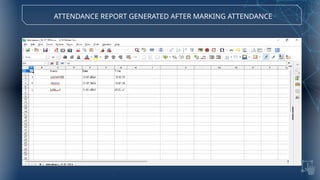
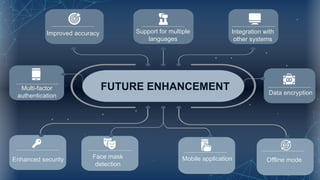
The document discusses the implementation of an automated facial recognition attendance recorder, which enhances attendance management through improved accuracy, efficiency, and security. Key components include blink detection for live face verification, haar cascade classifiers for face detection, and local binary pattern histograms for recognition, all secured with password protection and automated reporting. Future enhancements may involve integrating advanced algorithms, multi-factor authentication, and additional functionality for scalability.