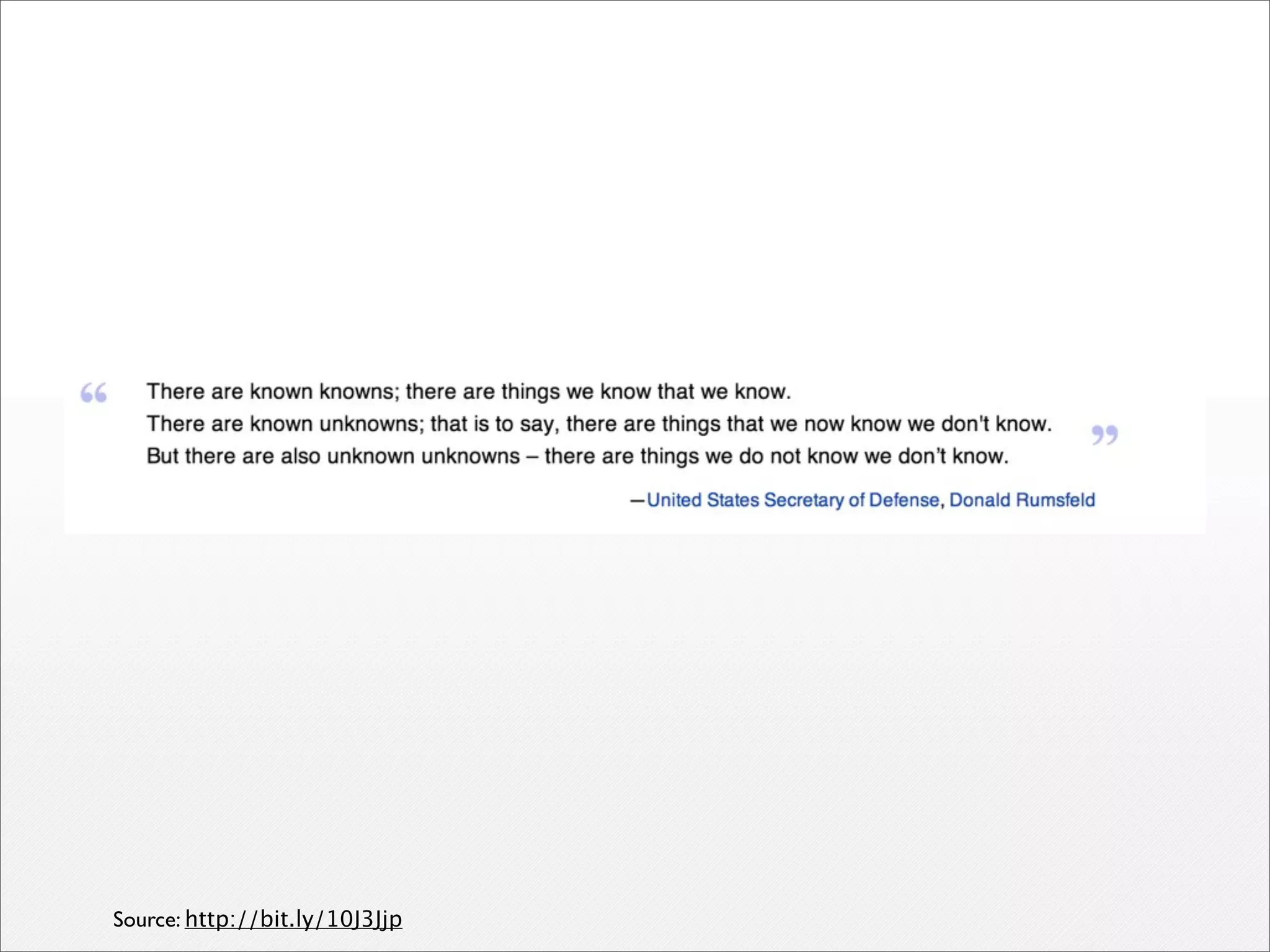
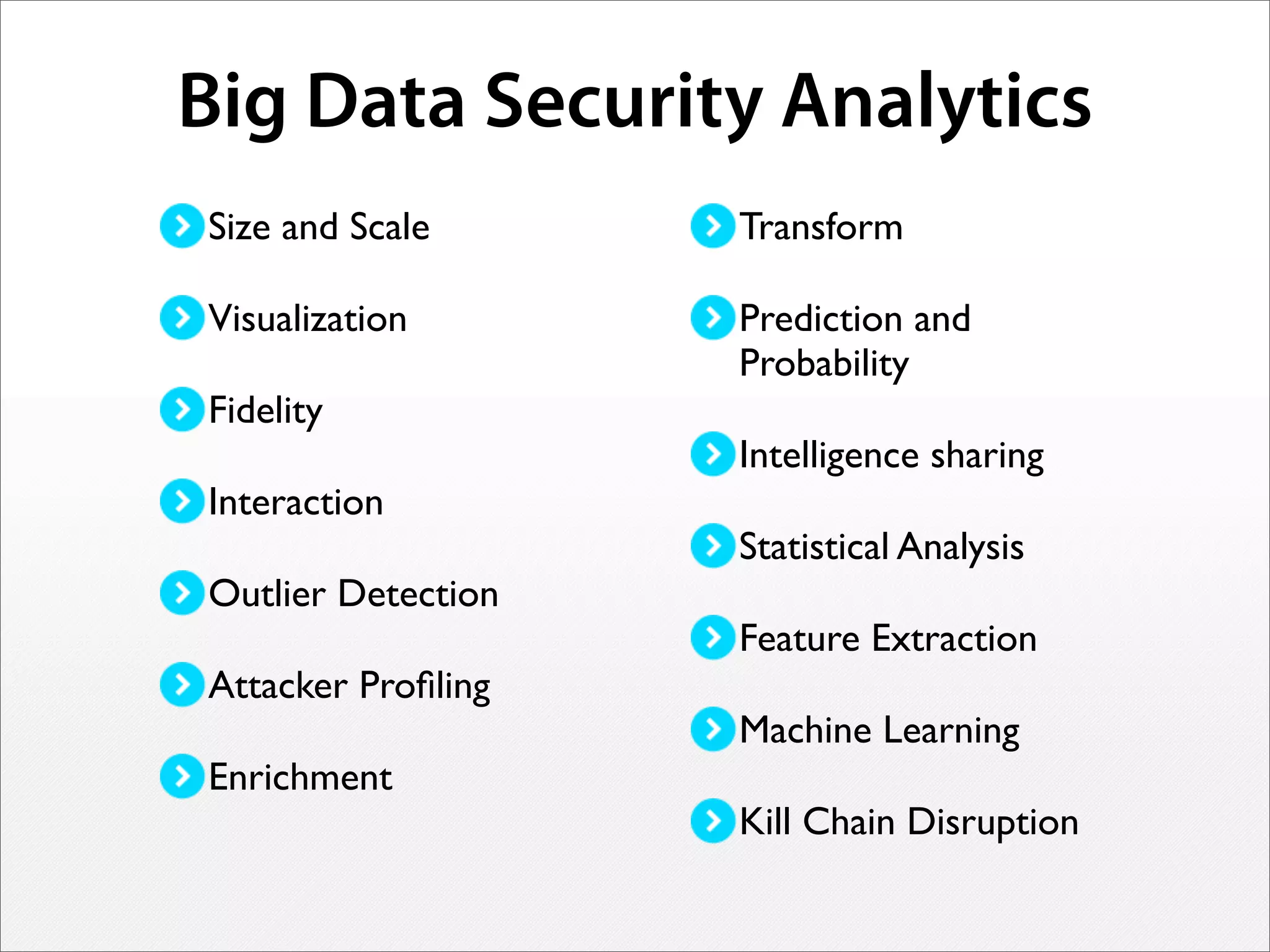
Michael Baker discusses big data security analytics and how analyzing full network data at scale and in real-time can help detect threats. Three key points:
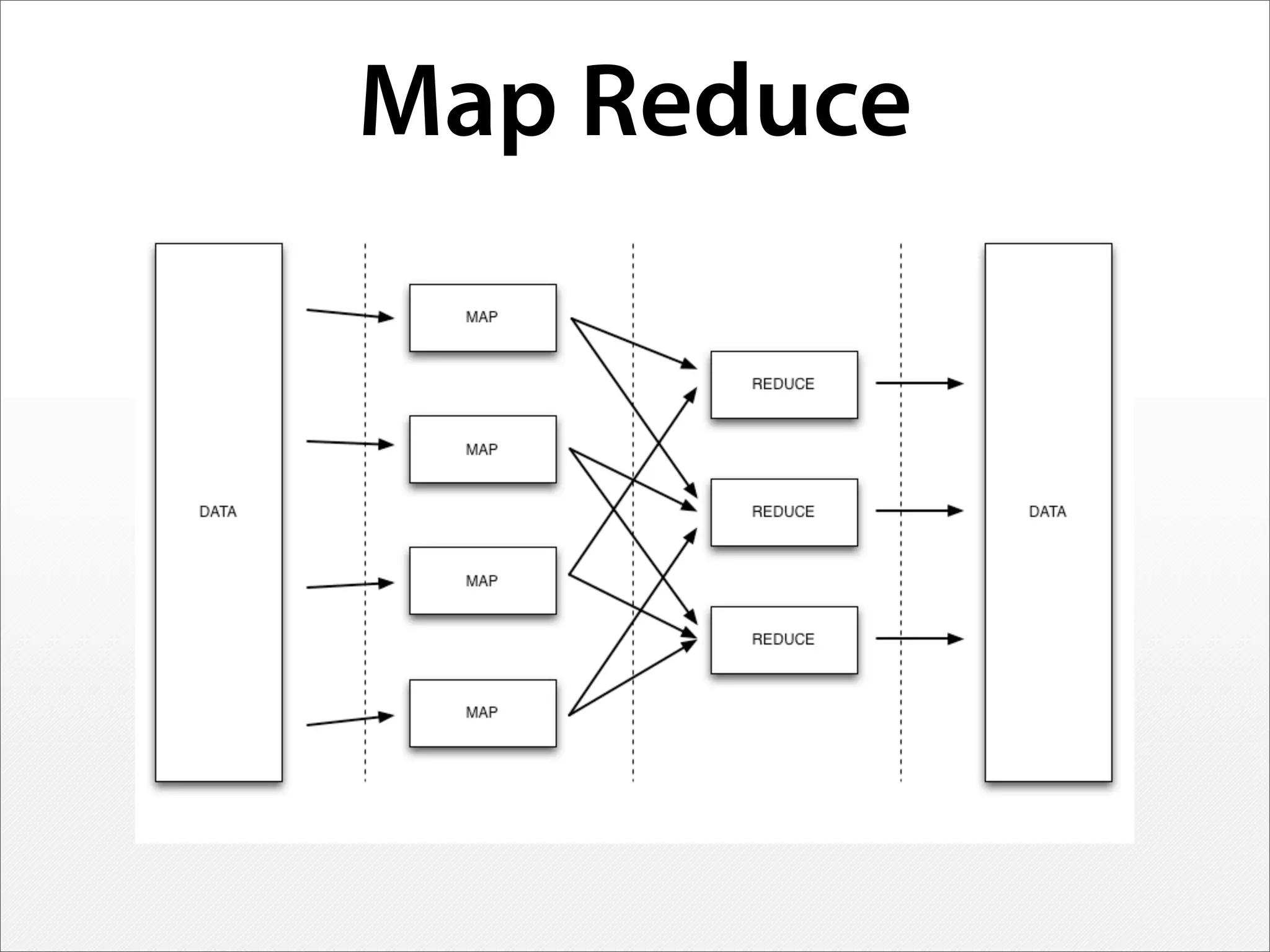
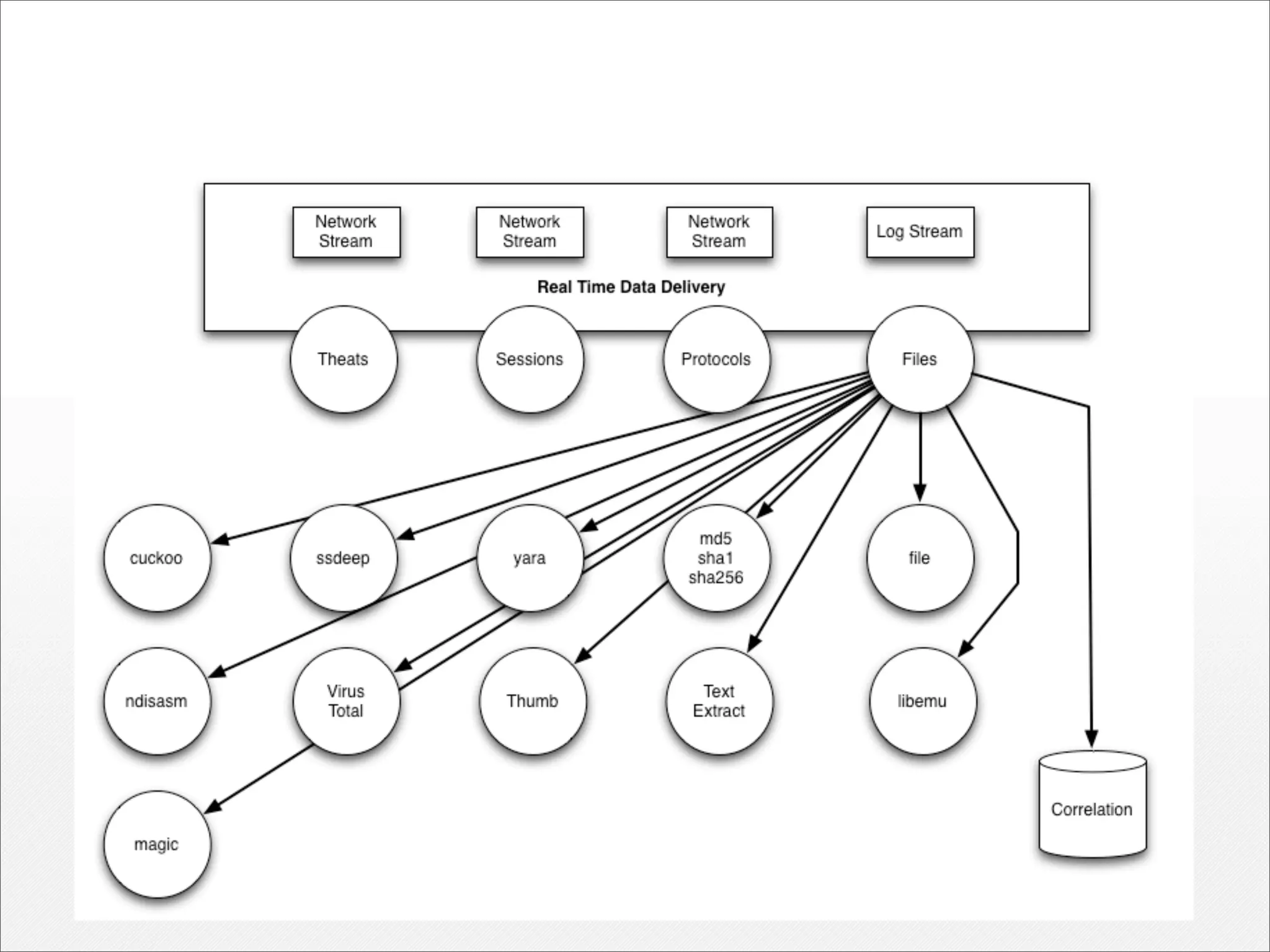
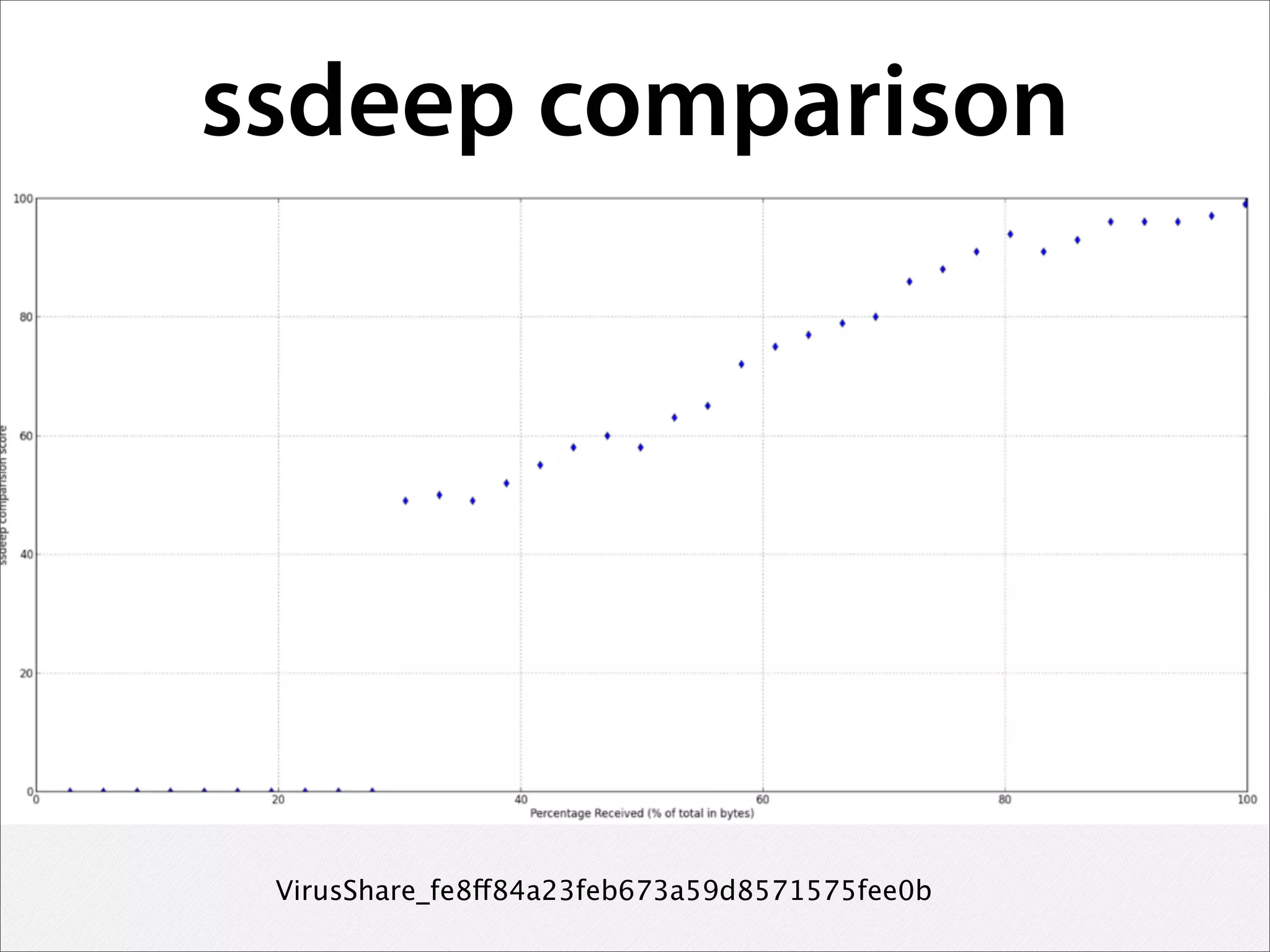
1) Analyzing complete network streams without aggregation allows understanding subtle attacks and exploring data through visualization and machine learning.
2) Enriching data with additional context like user and system profiles improves detection of attackers and security investigations.
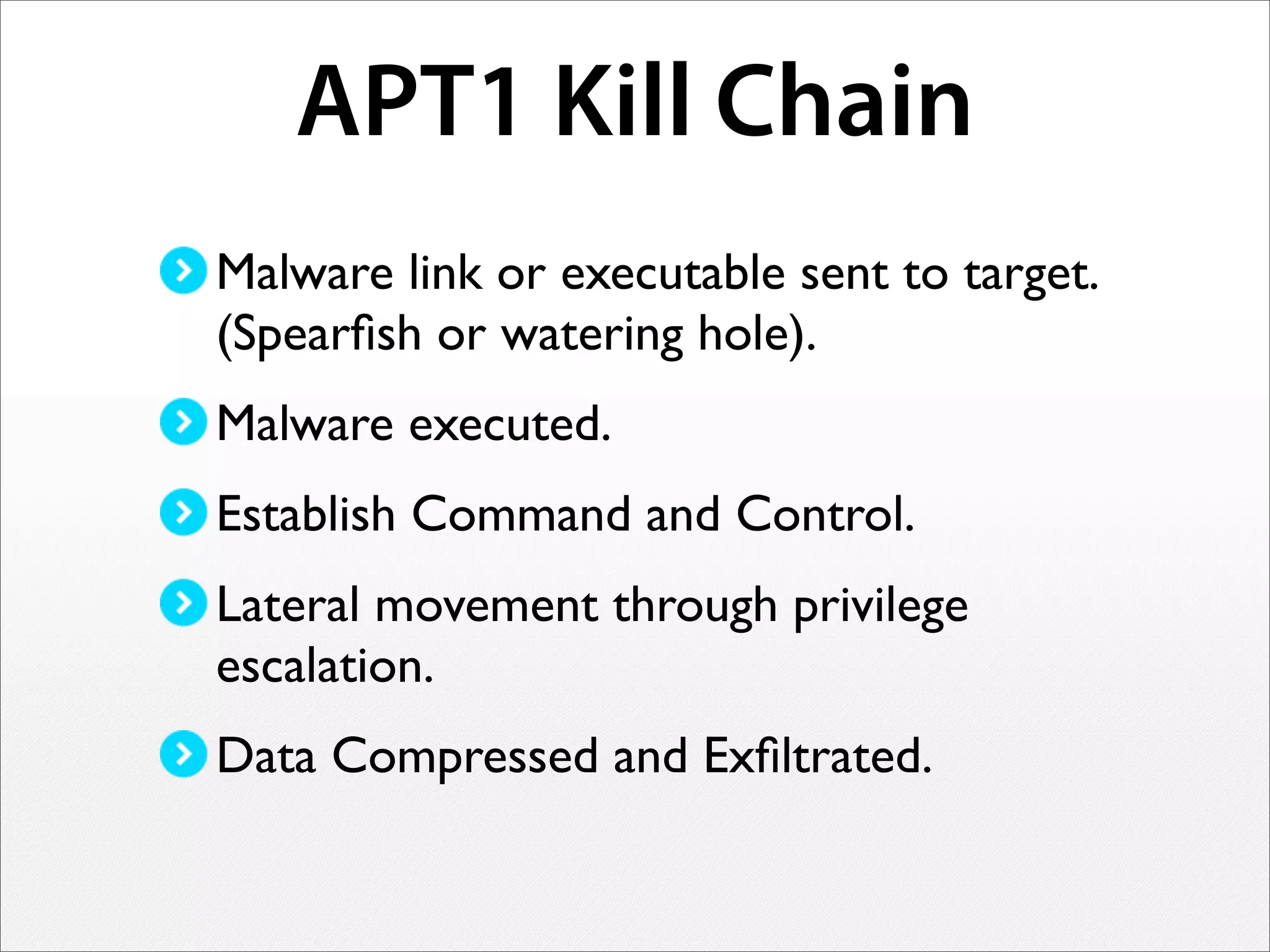
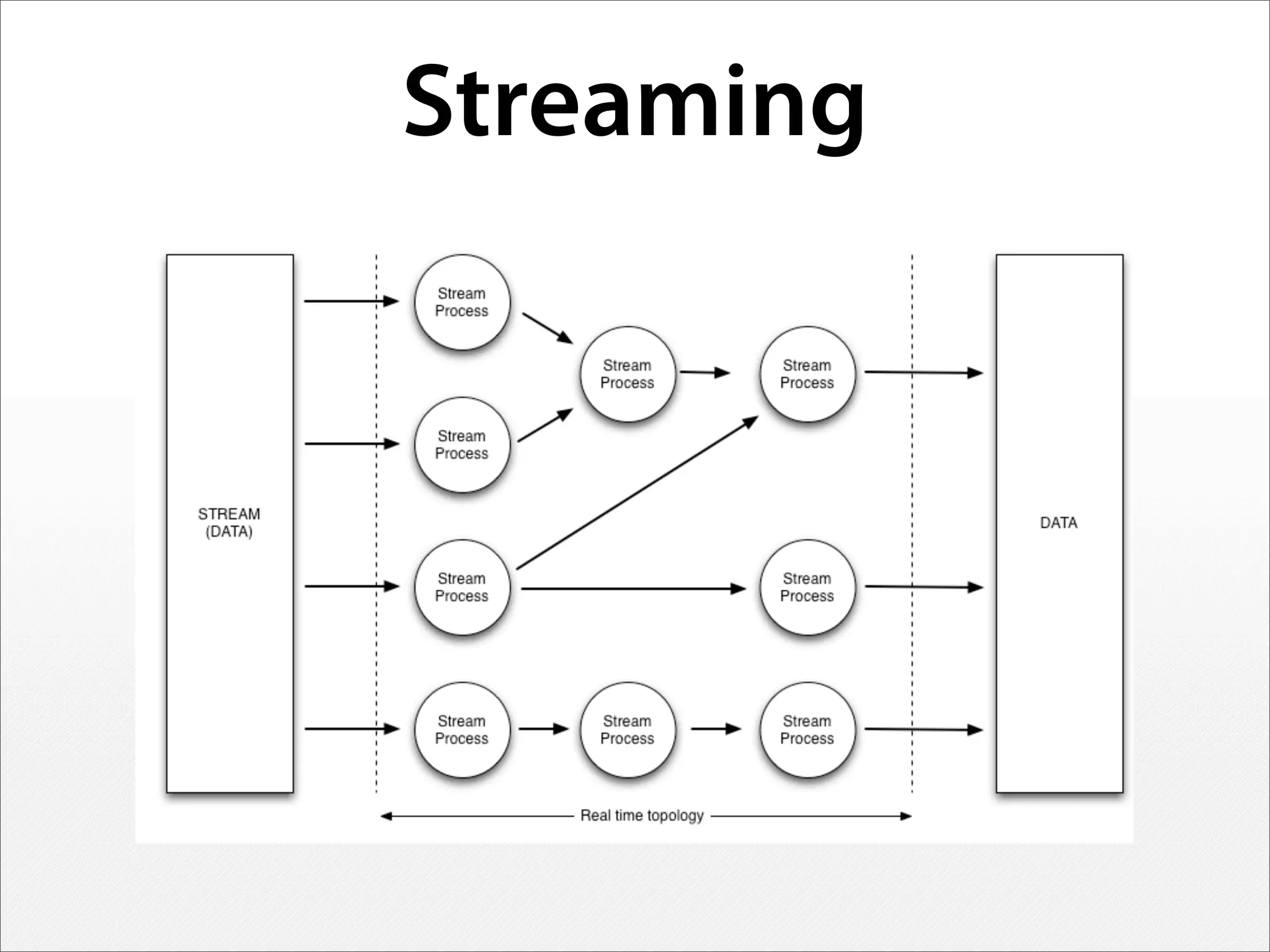
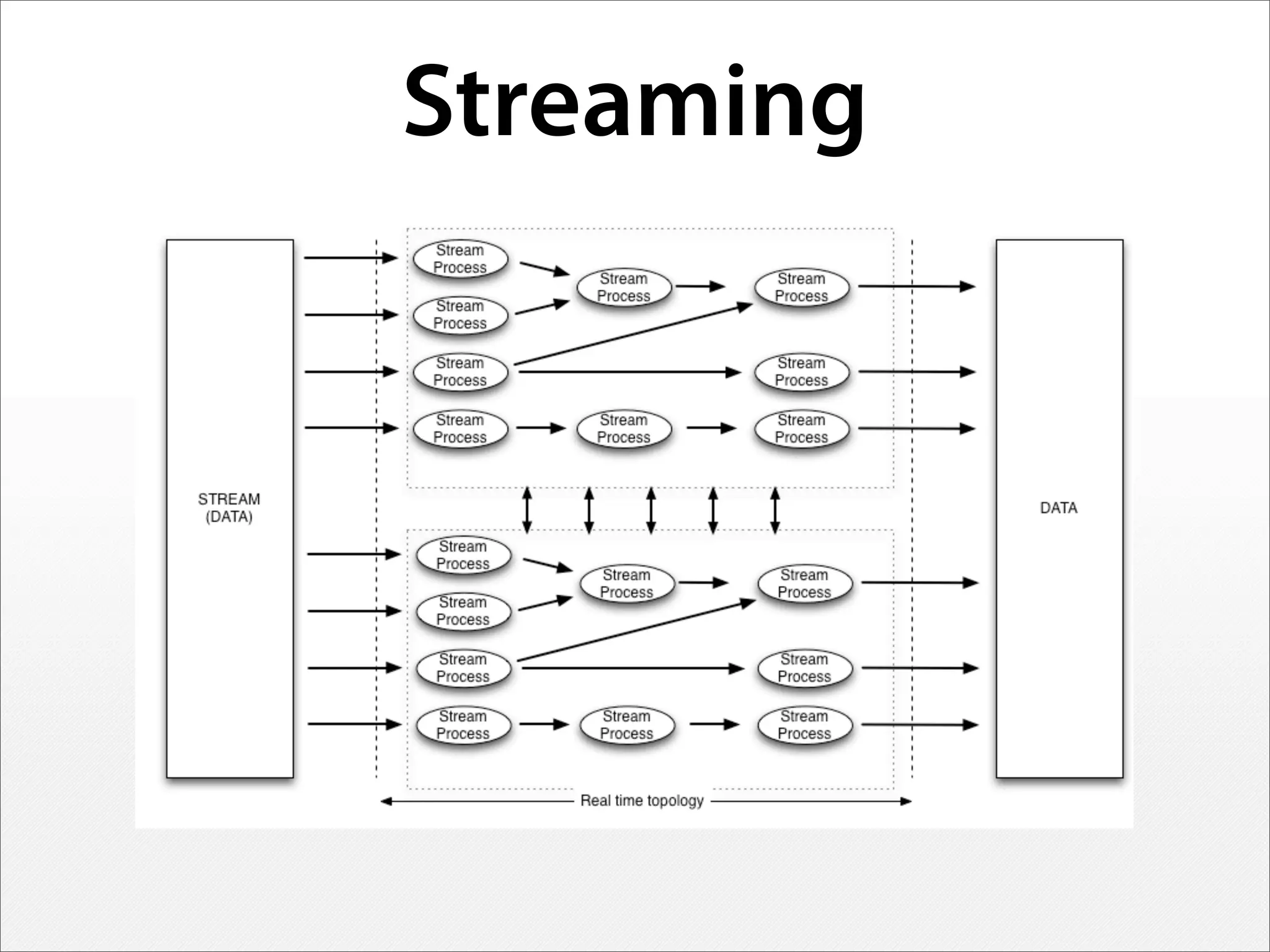
3) Real-time streaming analytics and the ability to "rewind" and explore historical network data is critical for detecting unknown threats, profiling attackers, and disrupting cyber kill chains. This level of analysis goes beyond traditional SIEM tools.




![Exhibit A
CVE-2011-3192 - “Apache Killer”
auxiliary/dos/http/apache_range_dos 2011-08-19
normal Apache Range header DoS (Apache Killer)
Snort 1:19825
/Ranges*x3As*bytes=([dx2D]+x2C){50}/Hsmi
/Ranges*x3As*bytes=([dx2D]+[x2Cs]*){50}/
Hsmi](https://image.slidesharecdn.com/auscert-findingneedlesinhaystacks-130523003806-phpapp01/75/Auscert-Finding-needles-in-haystacks-the-size-of-countries-6-2048.jpg)