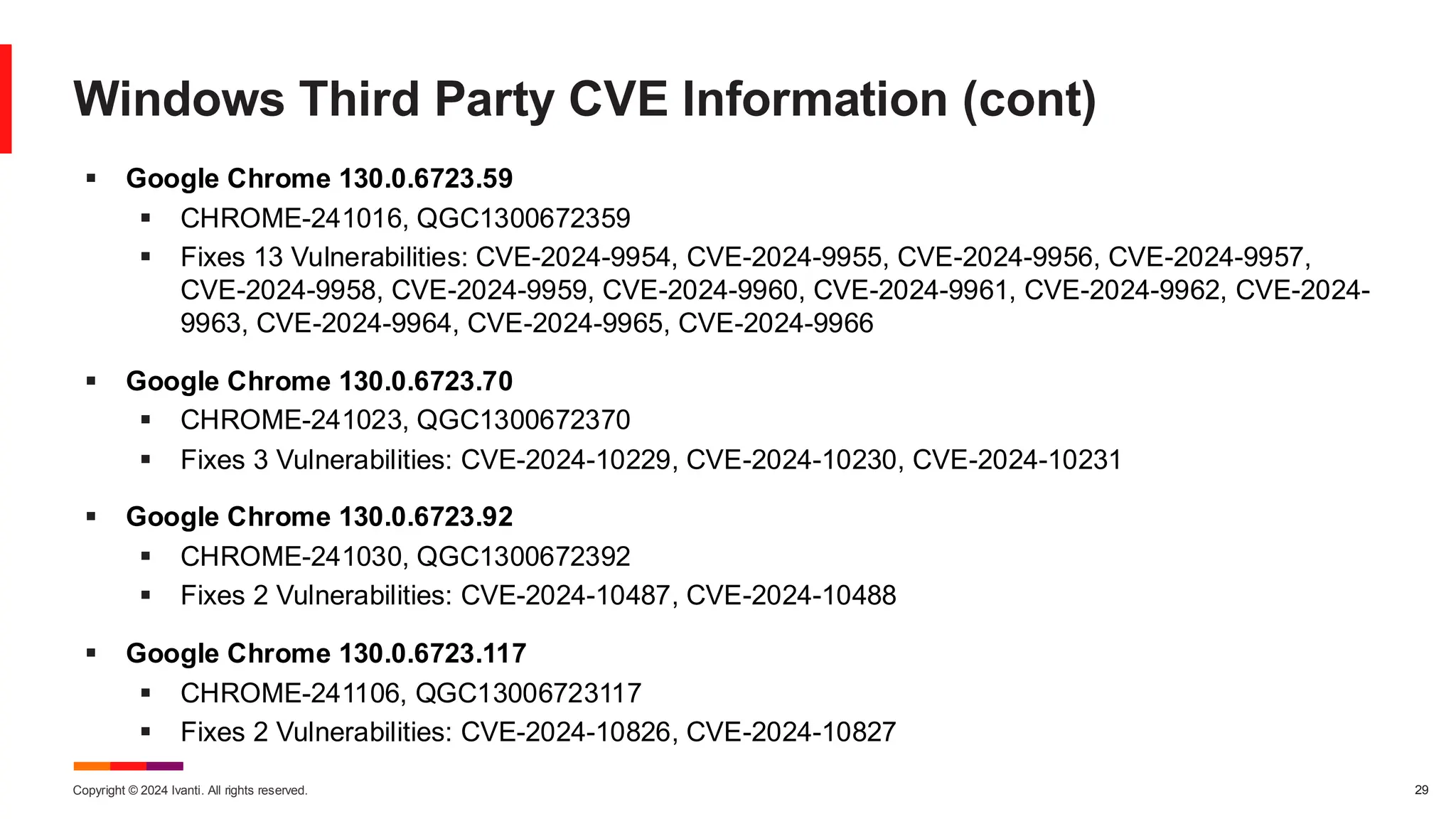
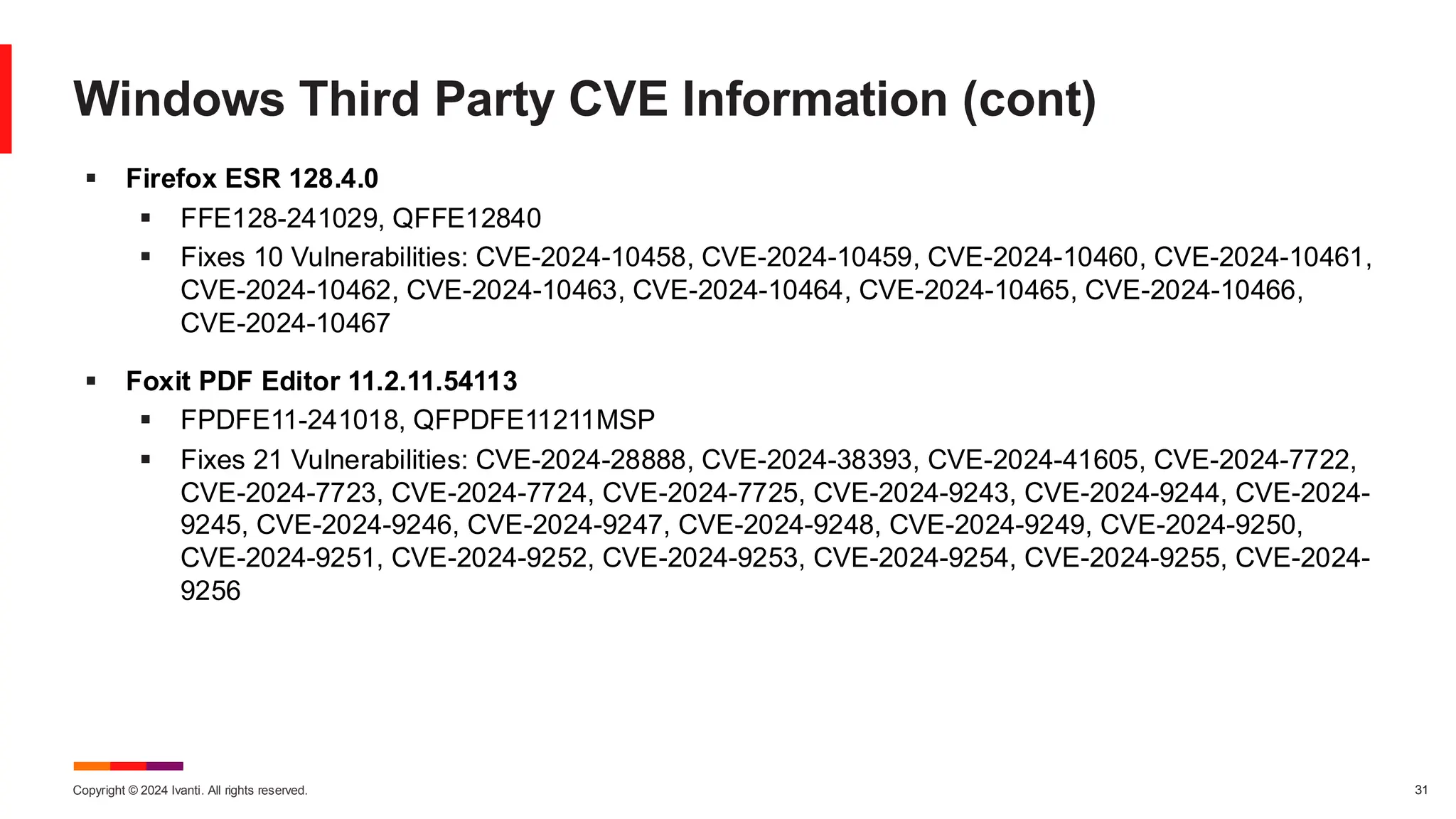
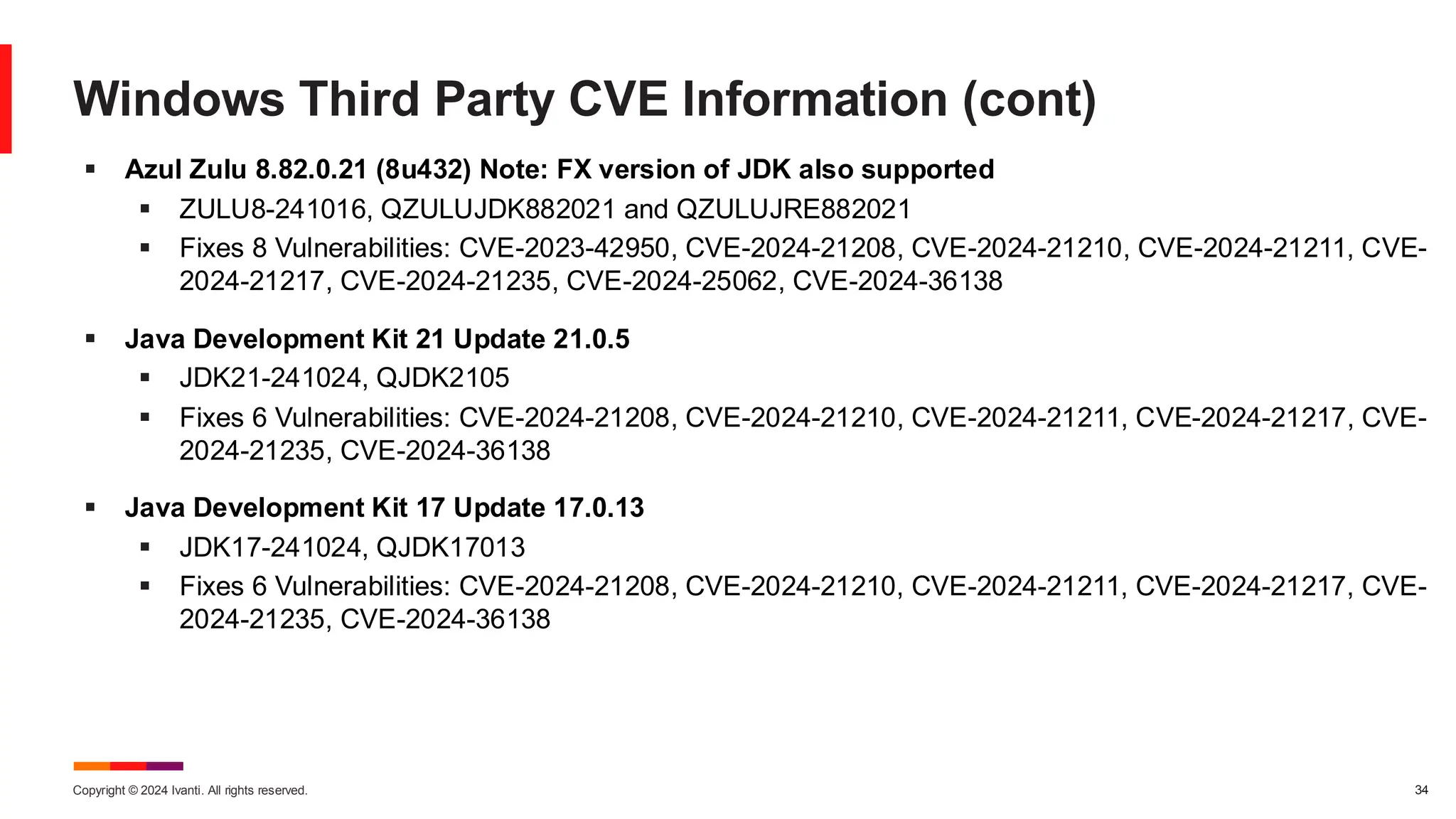
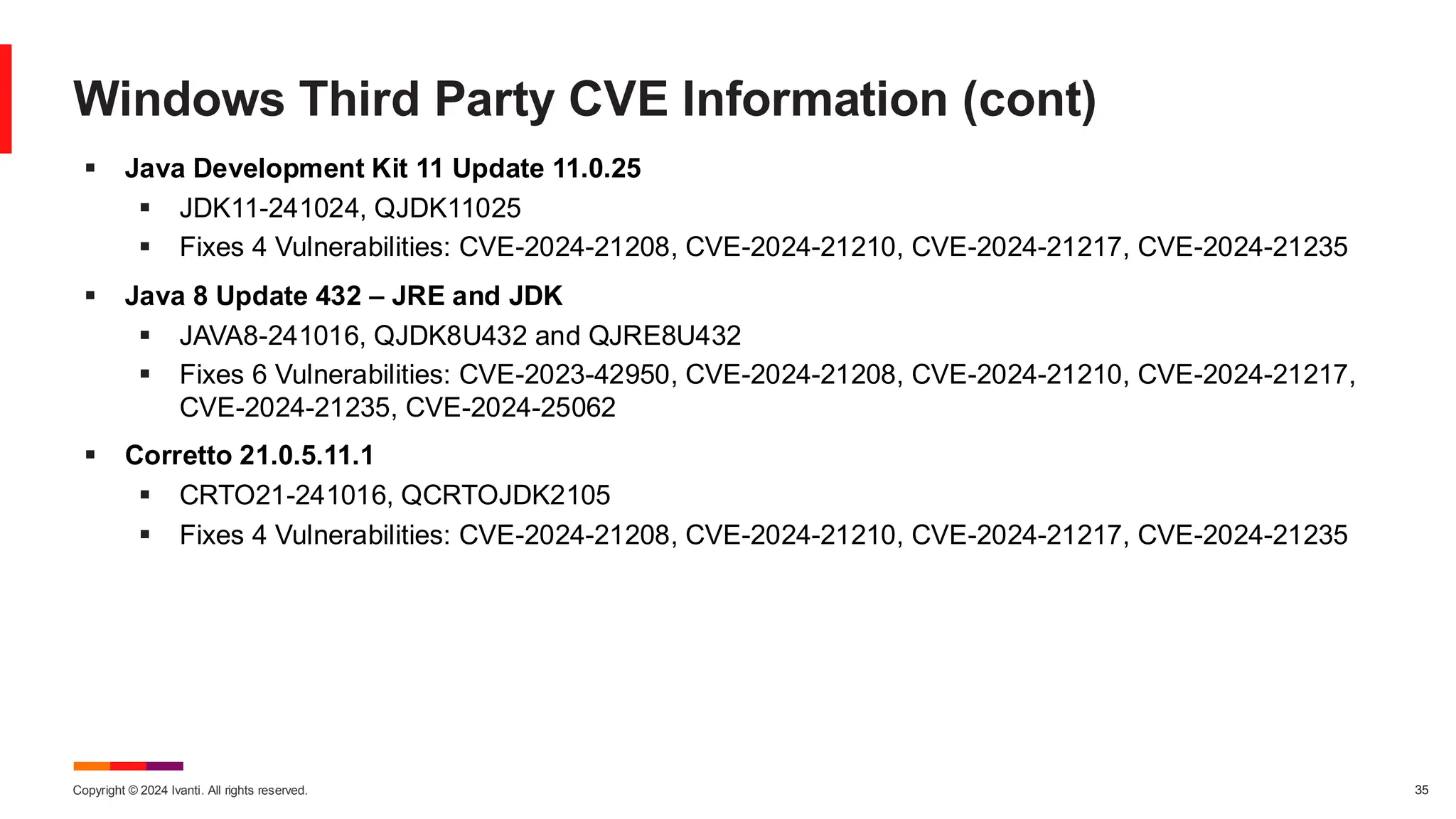
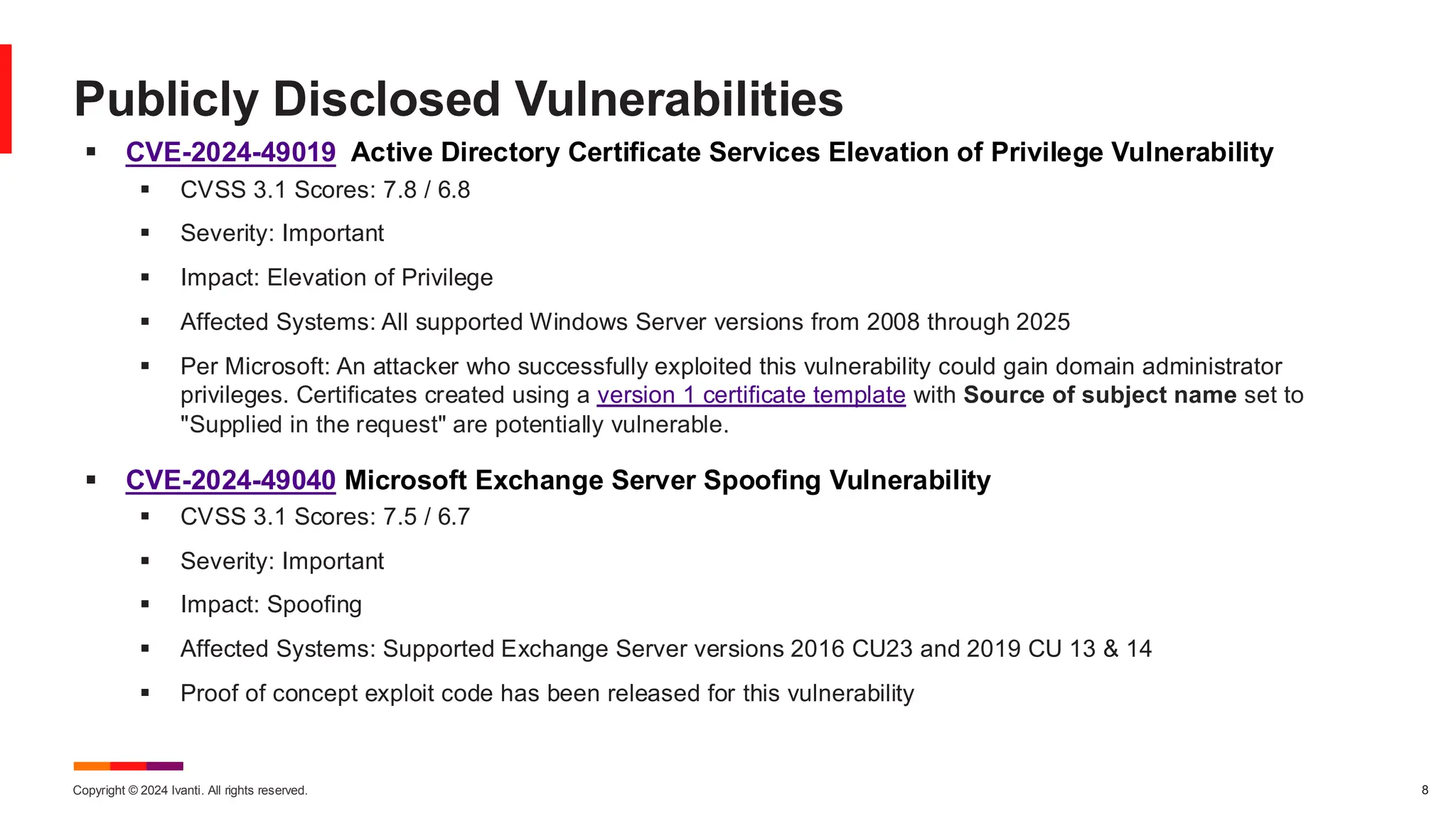
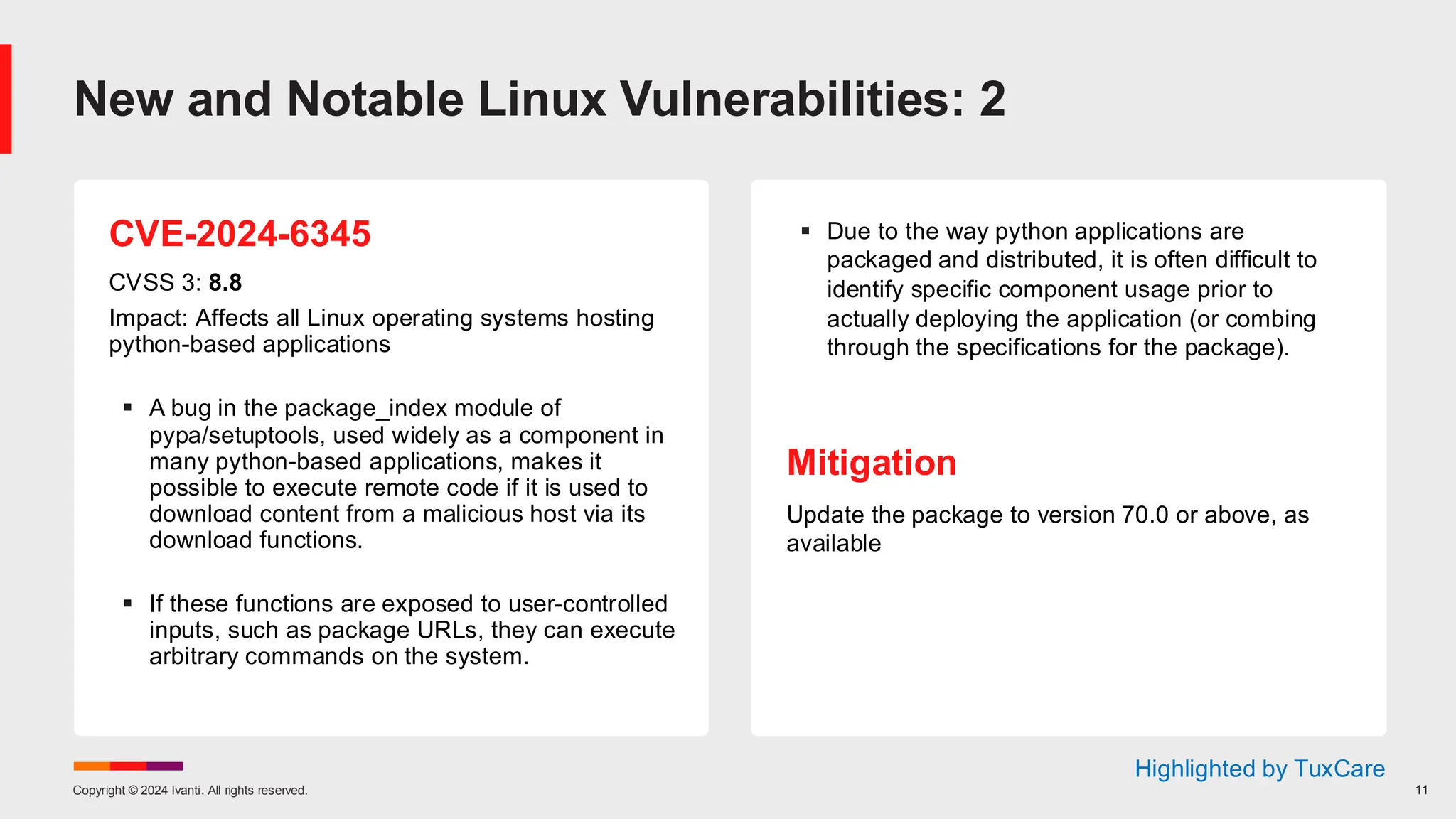
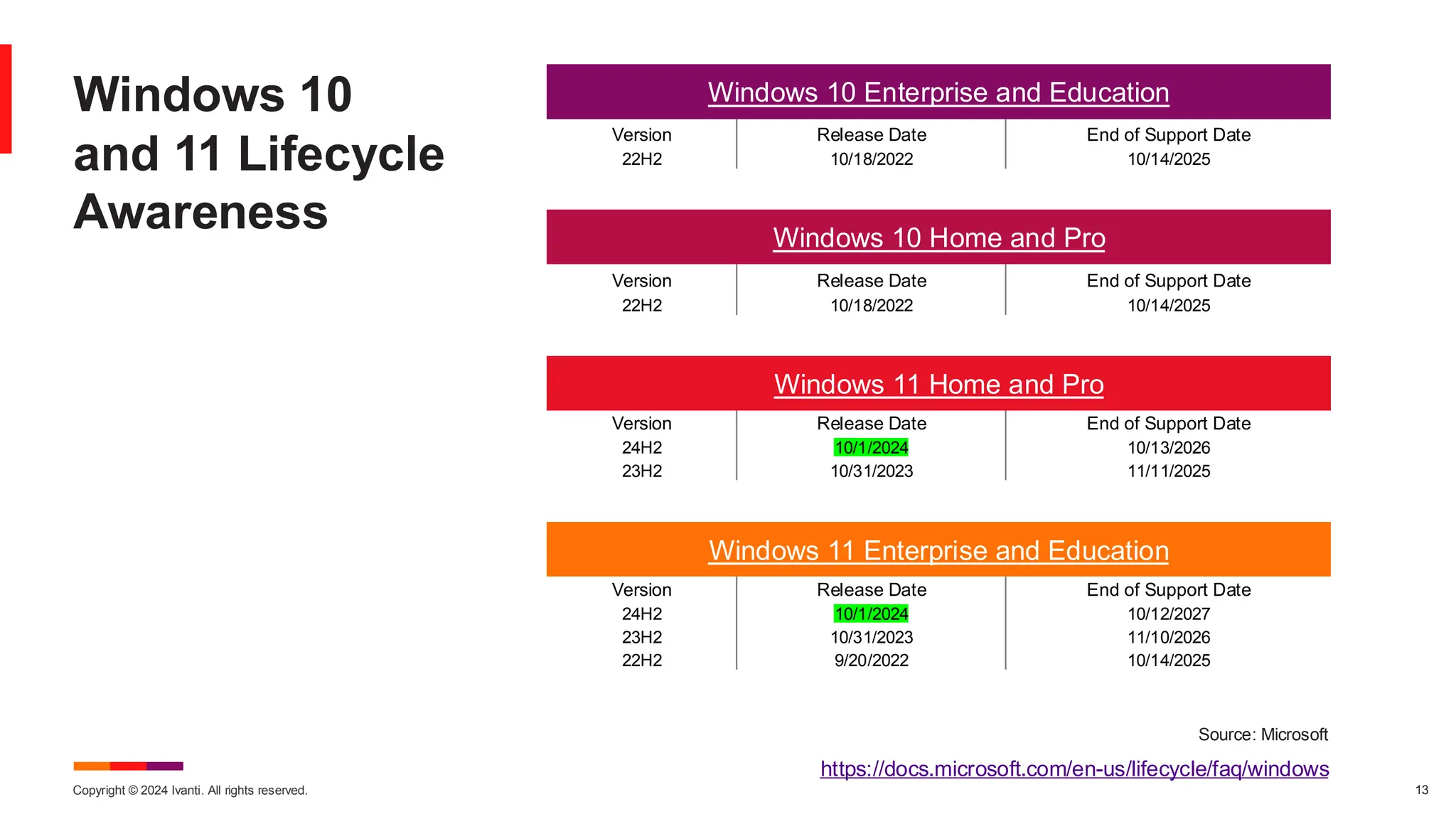
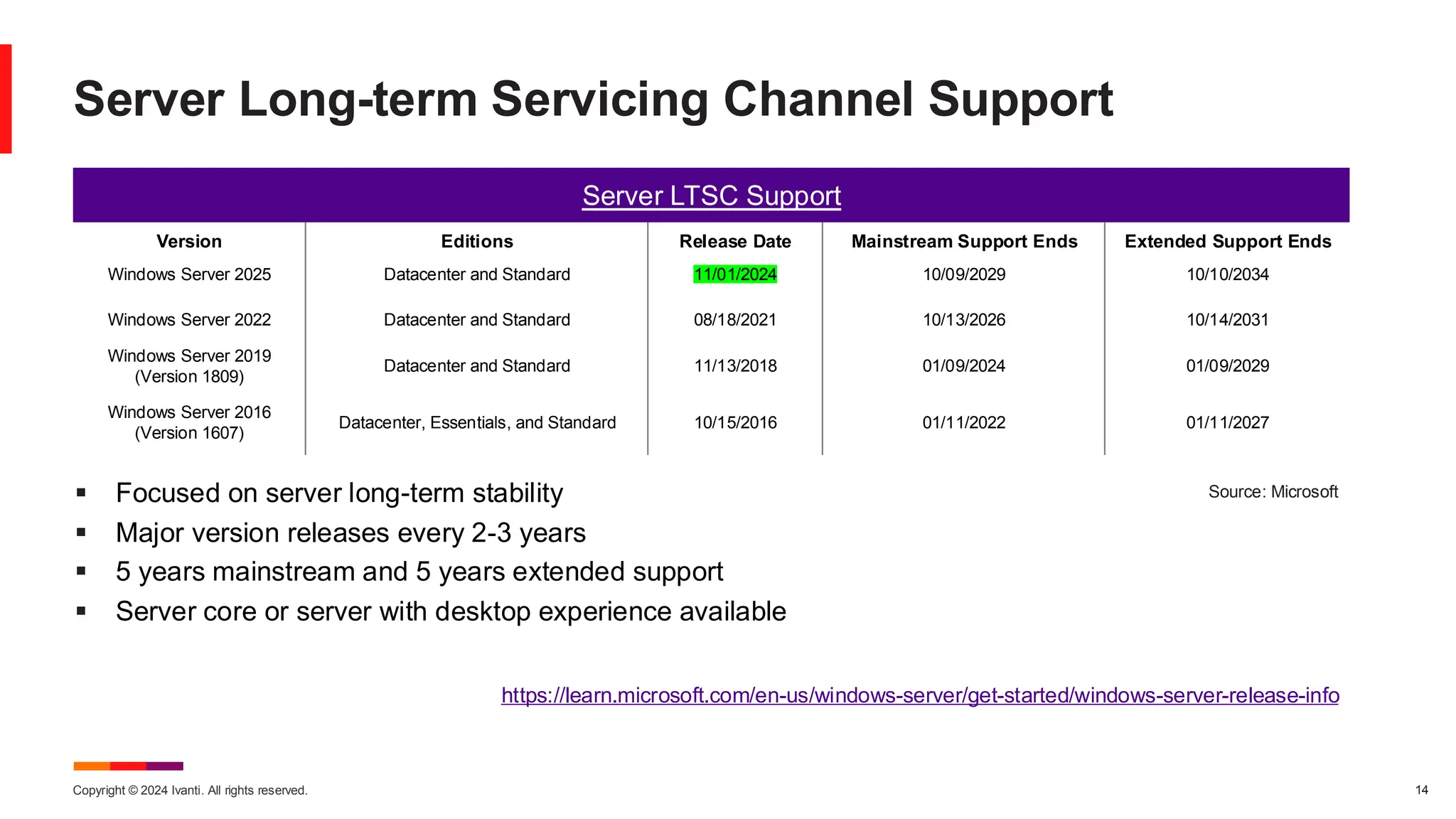
The November 2024 Patch Tuesday prioritizes critical updates for Windows OS addressing two exploited vulnerabilities (CVE-2024-49039 and CVE-2024-43451) and an important update for Microsoft Exchange Server due to a published vulnerability (CVE-2024-49040). The document outlines additional vulnerabilities, security updates for various Microsoft products, and emphasizes the need for timely updates to safeguard systems. Also discussed are lifecycle timelines for Windows 10 and 11, and long-term support for Windows Server versions.









![Copyright © 2024 Ivanti. All rights reserved. 18
November Known Issues for Windows 11
▪ KB 5046633 – Windows 11 version 22H2, Windows 11 version 23H2, all editions
▪ [OpenSSH] Following the installation of the October 2024 security update, some customers
report that the OpenSSH (Open Secure Shell) service fails to start, preventing SSH
connections.
▪ Workaround: Customers can temporarily resolve the issue by updating permissions (ACLs)
on the affected directories. See KB for details
▪ KB 5046617 – Windows 11 version 24H2, all editions
▪ [Roblox] We’re aware of an issue where players on Arm devices are unable to download
and play Roblox via the Microsoft Store on Windows.
▪ Workaround: Download Roblox directly from vendor.](https://image.slidesharecdn.com/nov2024patchtuesday-241113173723-eb1a9ed7/75/November-Patch-Tuesday-18-2048.jpg)