Assignment 4
•Download as DOCX, PDF•
1 like•57 views
Hackers illegally break into computer systems for personal gain or damage, often to steal financial information. They have in-depth technical knowledge that allows them to create hacking tools. Crackers also illegally access computer systems, but lack the technical skills of hackers. Crackers rely more on pre-existing hacking tools and cause damage through actions like replacing websites. Both hackers and crackers commit cybercrimes, but hackers do so using their own technical abilities while crackers rely on existing tools.
Report
Share
Report
Share
Recommended
Hacking 

The document discusses different types of hackers, including white-hat and black-hat hackers. White-hat hackers enjoy learning computer systems, while black-hat hackers, also called crackers, engage in illegal activities like stealing credit cards or passwords. The document also outlines common hacking methods like port scanning and denial of service attacks. It recommends steps for client-side security including anti-virus software, personal firewalls, and encryption to protect against hacking threats.
Hacking

This document discusses hacking and provides definitions and examples. It defines hacking as unauthorized computer access and distinguishes between hackers and crackers. Various types of hacking are described such as password, email, and credit card hacking. The document also gives a brief history of hacking and reasons why hackers engage in hacking. Examples are provided for how to hack passwords on websites like Yahoo, Facebook, and Gmail.
Hacking ppt

This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email rashed_ec2012@rediffmail.com
Hacking and its types

The document is a seminar report on hacking and its types submitted by Rishab Gupta to the Computer Science Department. It includes an abstract discussing how hacking exploits computer systems to access unauthorized information and the importance of ethical hacking to increase security. The report contains acknowledgments, a table of contents, and 5 chapters discussing the scope and importance of hacking, different types of ethical hacking, hacking methodology, and the advantages and disadvantages of hacking. It aims to provide information to secure systems from hackers and protect information.
Hacking,History Of Hacking,Types of Hacking,Types Of Hackers,Cyber Laws for ...

Hacking
History Of Hacking
Types of Hacking
The Most World’s famous Hackers
Types Of Hackers
Scope Of Ethical Hackers
Cyber Laws for Hacking and their Punishments in Pakistan
How to Prevent Hacking
Hacking

The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.
Ethical hacking

This document discusses the concept of ethical hacking. It defines ethical hacking as testing systems for security purposes, while distinguishing it from criminal hacking. It describes different types of hackers like white hat and black hat hackers. The document then covers various hacking techniques like email hacking through phishing and keyloggers, hacking Windows systems by exploiting the SAM database, and use of trojans for remote access or data theft. Prevention methods are also highlighted for some attacks.
Hacking Kishor

Hacking involves exploring systems and programming skills, while cracking uses those skills illegally. Hackers have various motivations including fun, profit, challenges, and exposing weaknesses. There are different types of hackers such as white hats who are professional security experts and black hats who are criminal hackers. Without hackers, many programming languages and operating systems would not exist. Crackers create security issues but also jobs to improve security. Common attacks include social engineering, denial of service attacks, and SQL injection. Once inside a system, a hacker can modify files and logs, install backdoors, and attack other systems. Hacking overall has benefited the computer industry by advancing programming and security.
Recommended
Hacking 

The document discusses different types of hackers, including white-hat and black-hat hackers. White-hat hackers enjoy learning computer systems, while black-hat hackers, also called crackers, engage in illegal activities like stealing credit cards or passwords. The document also outlines common hacking methods like port scanning and denial of service attacks. It recommends steps for client-side security including anti-virus software, personal firewalls, and encryption to protect against hacking threats.
Hacking

This document discusses hacking and provides definitions and examples. It defines hacking as unauthorized computer access and distinguishes between hackers and crackers. Various types of hacking are described such as password, email, and credit card hacking. The document also gives a brief history of hacking and reasons why hackers engage in hacking. Examples are provided for how to hack passwords on websites like Yahoo, Facebook, and Gmail.
Hacking ppt

This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email rashed_ec2012@rediffmail.com
Hacking and its types

The document is a seminar report on hacking and its types submitted by Rishab Gupta to the Computer Science Department. It includes an abstract discussing how hacking exploits computer systems to access unauthorized information and the importance of ethical hacking to increase security. The report contains acknowledgments, a table of contents, and 5 chapters discussing the scope and importance of hacking, different types of ethical hacking, hacking methodology, and the advantages and disadvantages of hacking. It aims to provide information to secure systems from hackers and protect information.
Hacking,History Of Hacking,Types of Hacking,Types Of Hackers,Cyber Laws for ...

Hacking
History Of Hacking
Types of Hacking
The Most World’s famous Hackers
Types Of Hackers
Scope Of Ethical Hackers
Cyber Laws for Hacking and their Punishments in Pakistan
How to Prevent Hacking
Hacking

The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.
Ethical hacking

This document discusses the concept of ethical hacking. It defines ethical hacking as testing systems for security purposes, while distinguishing it from criminal hacking. It describes different types of hackers like white hat and black hat hackers. The document then covers various hacking techniques like email hacking through phishing and keyloggers, hacking Windows systems by exploiting the SAM database, and use of trojans for remote access or data theft. Prevention methods are also highlighted for some attacks.
Hacking Kishor

Hacking involves exploring systems and programming skills, while cracking uses those skills illegally. Hackers have various motivations including fun, profit, challenges, and exposing weaknesses. There are different types of hackers such as white hats who are professional security experts and black hats who are criminal hackers. Without hackers, many programming languages and operating systems would not exist. Crackers create security issues but also jobs to improve security. Common attacks include social engineering, denial of service attacks, and SQL injection. Once inside a system, a hacker can modify files and logs, install backdoors, and attack other systems. Hacking overall has benefited the computer industry by advancing programming and security.
Ethical hacking

The document discusses ethical hacking and provides information on:
1) What ethical hacking is and who ethical hackers are. It notes they help find security vulnerabilities without malicious intent.
2) A brief history of hacking from the 1960s to 2000s, including some notable hacking incidents.
3) The different types of hackers - white hat who help security, black hat who hack maliciously, and grey hat whose intentions are unclear.
Hacking and its types

The document discusses the history and types of hacking. It begins with definitions of hacking and hackers, then discusses the history of hacking emerging in the 1960s at MIT. It outlines famous hackers from history and reasons people hack, such as for fun or to show off skills. The document categorizes different types of hacking like website, network, and password hacking. It provides tips on securing data and accounts, as well as advantages and disadvantages of hacking. In conclusion, it emphasizes the importance of secure passwords and being aware of website security indicators.
Introduction To Ethical Hacking

This document introduces the concept of ethical hacking. It begins by defining hacking as finding solutions to real-life problems, and clarifies that the original meaning of "hack" was not related to computers. It then discusses how the term entered computer culture at MIT in the 1960s, where hackers were students who solved problems in innovative ways, unlike "tools" who just attended class. The document outlines some traits of good hacks and provides examples. It emphasizes that media misconstrues hackers as criminals, and explains that real hackers have strong ethics and help catch cyber criminals, unlike crackers who hack systems illegally. The rest of the document provides an overview of skills, subjects, and basic concepts needed for ethical hacking.
Introduction to Hacking

White hat hackers, also known as ethical hackers, check for vulnerabilities in systems with permission to make security improvements. Black hat hackers get unauthorized access to steal data and cause damage for profit. Hacking involves finding flaws and weaknesses, not using automatic software. Common hacking methods include phishing (fake login pages), keylogging (capturing keystrokes), and remote administration tools (giving attackers access). The document provides an introduction to different types of hackers and basic hacking techniques like phishing, keylogging, and remote access tools rather than automatic software.
Computer and Internet hacking

This document discusses computer and internet hacking. It defines hacking as modifying hardware and software outside of a creator's intended purpose. Hackers have an in-depth understanding of computers and how the internet works. The document outlines different types of hackers including white hats who hack for ethical purposes, grey hats who may commit minor crimes but not for personal gain, and black hats who hack illegally for personal benefit. It also mentions common hacker attacks like exploiting vulnerabilities in internet-connected systems and networks.
Ethical hacking

ethical hacking.............by arohan sharma for making presentation for companies and other purposes........contact 8803231644
Ethical Hacking

This document discusses hacking and ethical hacking. It provides an overview of different types of hackers (white hat, black hat, grey hat) and defines ethical hacking as hacking performed to help identify security vulnerabilities. It then presents a case study about a data breach at AAPT where a hacker group accessed customer data. An investigation found that AAPT failed to take reasonable security measures to protect the data, such as using an outdated version of software with known vulnerabilities. As a result, the commissioner recommended steps for AAPT to improve its security practices and audit processes.
National information security education & awareness program

This document provides an introduction to ethical hacking and discusses the differences between hackers and crackers. It defines hackers as developers who find solutions to real-life problems, while crackers illegally break into systems. The document discusses career options for students interested in information security and recommends studying computer science, IT, or electronics in Indian universities. It also includes a case study about a woman whose privacy was invaded by a remote attacker and urges developing strong ethics as a hacker to help catch cyber criminals.
Computer hacking

You all can infer what would be in the PPT from the title itself. In this PPT it is not told directly how to hack. Just a brief info of hacking and cyber security is given. How can one save himself/herself from becoming a victim of cybercrime? How to hack is given in my next PPT?
Hacking & Hackers

Hacking is the process of attempting to gain unauthorized access to computer resources. A hacker is someone who seeks or exploits weaknesses in a computer system. There are different types of hackers including white hats who fix weaknesses, black hats who hack for personal gain, and gray hats who identify weaknesses to share. Common types of hacking include website, network, email, password, online banking, and computer hacking. While ethical hacking can help identify security issues, most hacking has disadvantages like enabling criminals, harming privacy, being illegal, and causing financial losses.
Attack chaining for web exploitation #c0c0n2015

This is the deck which is used to present at c0c0n 2015. Due to some privacy reasons, I'm unable to share few screenshots. If interested please reach out to me.
If you have some feedback please drop an email to abhijeth0423@gmail.com.
Video will be published soon which will give more idea about the talk.
Also credits to: @mat www.wesecureapp.com
my new HACKING

This document provides an outline for a presentation on hacking. It begins with definitions of hacking and different types of hackers. The history and evolution of hacking is discussed. Various types of hacking techniques like denial of service attacks, password cracking, and social engineering are described. Common hacking tools such as Nmap, Cain and Abel, and keyloggers are listed. The document outlines how hacking attacks work and their potential effects. It discusses certifications in ethical hacking and concludes that while hacking can be a crime, proper security measures and computer ethics can help prevent and detect hacking activities.
Is hacking good or bad

The document discusses different types of hackers and their activities. It defines hacking as gaining unauthorized access to computer systems and networks. White hat hackers use their skills ethically to test security and help organizations, like Linus Torvalds who created Linux. Black hat hackers violate security for malicious reasons, such as Jonathan James who stole software from NASA. The document concludes that hacking can be good when used to create innovative technologies, but should not be used for illegal activities.
Preventions of Email Hacking

How to prevent from email hacking.
email, email prevention, email prevention techniques, how hack email, how to make email secure, strategy of email prevention
Web defacement

This document provides definitions and information related to hacking and web defacement. It defines hacking as unauthorized use of computer and network resources. A hacker is described as an expert programmer who breaks security, while a cracker breaks in with malicious intent. Web defacement is when a hacker compromises a web server and changes the visual appearance or data on a page. Types of hacking discussed include password, email, site, banking and network hacking. The effects of hacking and methods to prevent hacking like software updates, firewalls, and antivirus software are also summarized.
Kinds of hackers

There are three main types of hackers: black hats, white hats, and gray hats. Black hat hackers illegally compromise security systems for personal gain or malicious purposes. White hat hackers ethically test security systems to help organizations by reporting vulnerabilities. Gray hat hackers fall between black and white hats, sometimes illegally accessing systems without permission but not for malicious ends.
Cybercrime (Computer Hacking)

This presentation deals with the past, present and future implications of cybercrime with respect to computer hacking.
Cyber hacking dev days by aes team

Hacking is an act of penetrating computer systems to gain knowledge about the system and how it works. This is considered illegal since it is like breaking into someone’s house.
Ethical hacking tausif h4 ck3r

The document discusses ethical hacking, which refers to authorized security testing of systems to identify vulnerabilities. It notes that ethical hackers have the same skills as black hat hackers but perform attacks in a non-destructive manner with permission. It describes different types of ethical hackers like white hat and grey hat hackers and their purposes. The document also outlines the steps of an ethical hacking process including preparation, footprinting, and vulnerability identification.
Hacking

This document discusses hacking and provides definitions and examples. It defines hacking as unauthorized computer access and distinguishes between hackers and crackers. Various types of hacking are described such as password, email, and credit card hacking. The document also gives a brief history of hacking and reasons why hackers engage in hacking. Examples are provided for how to hack passwords on websites like Yahoo, Facebook, and Gmail.
More Related Content
What's hot
Ethical hacking

The document discusses ethical hacking and provides information on:
1) What ethical hacking is and who ethical hackers are. It notes they help find security vulnerabilities without malicious intent.
2) A brief history of hacking from the 1960s to 2000s, including some notable hacking incidents.
3) The different types of hackers - white hat who help security, black hat who hack maliciously, and grey hat whose intentions are unclear.
Hacking and its types

The document discusses the history and types of hacking. It begins with definitions of hacking and hackers, then discusses the history of hacking emerging in the 1960s at MIT. It outlines famous hackers from history and reasons people hack, such as for fun or to show off skills. The document categorizes different types of hacking like website, network, and password hacking. It provides tips on securing data and accounts, as well as advantages and disadvantages of hacking. In conclusion, it emphasizes the importance of secure passwords and being aware of website security indicators.
Introduction To Ethical Hacking

This document introduces the concept of ethical hacking. It begins by defining hacking as finding solutions to real-life problems, and clarifies that the original meaning of "hack" was not related to computers. It then discusses how the term entered computer culture at MIT in the 1960s, where hackers were students who solved problems in innovative ways, unlike "tools" who just attended class. The document outlines some traits of good hacks and provides examples. It emphasizes that media misconstrues hackers as criminals, and explains that real hackers have strong ethics and help catch cyber criminals, unlike crackers who hack systems illegally. The rest of the document provides an overview of skills, subjects, and basic concepts needed for ethical hacking.
Introduction to Hacking

White hat hackers, also known as ethical hackers, check for vulnerabilities in systems with permission to make security improvements. Black hat hackers get unauthorized access to steal data and cause damage for profit. Hacking involves finding flaws and weaknesses, not using automatic software. Common hacking methods include phishing (fake login pages), keylogging (capturing keystrokes), and remote administration tools (giving attackers access). The document provides an introduction to different types of hackers and basic hacking techniques like phishing, keylogging, and remote access tools rather than automatic software.
Computer and Internet hacking

This document discusses computer and internet hacking. It defines hacking as modifying hardware and software outside of a creator's intended purpose. Hackers have an in-depth understanding of computers and how the internet works. The document outlines different types of hackers including white hats who hack for ethical purposes, grey hats who may commit minor crimes but not for personal gain, and black hats who hack illegally for personal benefit. It also mentions common hacker attacks like exploiting vulnerabilities in internet-connected systems and networks.
Ethical hacking

ethical hacking.............by arohan sharma for making presentation for companies and other purposes........contact 8803231644
Ethical Hacking

This document discusses hacking and ethical hacking. It provides an overview of different types of hackers (white hat, black hat, grey hat) and defines ethical hacking as hacking performed to help identify security vulnerabilities. It then presents a case study about a data breach at AAPT where a hacker group accessed customer data. An investigation found that AAPT failed to take reasonable security measures to protect the data, such as using an outdated version of software with known vulnerabilities. As a result, the commissioner recommended steps for AAPT to improve its security practices and audit processes.
National information security education & awareness program

This document provides an introduction to ethical hacking and discusses the differences between hackers and crackers. It defines hackers as developers who find solutions to real-life problems, while crackers illegally break into systems. The document discusses career options for students interested in information security and recommends studying computer science, IT, or electronics in Indian universities. It also includes a case study about a woman whose privacy was invaded by a remote attacker and urges developing strong ethics as a hacker to help catch cyber criminals.
Computer hacking

You all can infer what would be in the PPT from the title itself. In this PPT it is not told directly how to hack. Just a brief info of hacking and cyber security is given. How can one save himself/herself from becoming a victim of cybercrime? How to hack is given in my next PPT?
Hacking & Hackers

Hacking is the process of attempting to gain unauthorized access to computer resources. A hacker is someone who seeks or exploits weaknesses in a computer system. There are different types of hackers including white hats who fix weaknesses, black hats who hack for personal gain, and gray hats who identify weaknesses to share. Common types of hacking include website, network, email, password, online banking, and computer hacking. While ethical hacking can help identify security issues, most hacking has disadvantages like enabling criminals, harming privacy, being illegal, and causing financial losses.
Attack chaining for web exploitation #c0c0n2015

This is the deck which is used to present at c0c0n 2015. Due to some privacy reasons, I'm unable to share few screenshots. If interested please reach out to me.
If you have some feedback please drop an email to abhijeth0423@gmail.com.
Video will be published soon which will give more idea about the talk.
Also credits to: @mat www.wesecureapp.com
my new HACKING

This document provides an outline for a presentation on hacking. It begins with definitions of hacking and different types of hackers. The history and evolution of hacking is discussed. Various types of hacking techniques like denial of service attacks, password cracking, and social engineering are described. Common hacking tools such as Nmap, Cain and Abel, and keyloggers are listed. The document outlines how hacking attacks work and their potential effects. It discusses certifications in ethical hacking and concludes that while hacking can be a crime, proper security measures and computer ethics can help prevent and detect hacking activities.
Is hacking good or bad

The document discusses different types of hackers and their activities. It defines hacking as gaining unauthorized access to computer systems and networks. White hat hackers use their skills ethically to test security and help organizations, like Linus Torvalds who created Linux. Black hat hackers violate security for malicious reasons, such as Jonathan James who stole software from NASA. The document concludes that hacking can be good when used to create innovative technologies, but should not be used for illegal activities.
Preventions of Email Hacking

How to prevent from email hacking.
email, email prevention, email prevention techniques, how hack email, how to make email secure, strategy of email prevention
Web defacement

This document provides definitions and information related to hacking and web defacement. It defines hacking as unauthorized use of computer and network resources. A hacker is described as an expert programmer who breaks security, while a cracker breaks in with malicious intent. Web defacement is when a hacker compromises a web server and changes the visual appearance or data on a page. Types of hacking discussed include password, email, site, banking and network hacking. The effects of hacking and methods to prevent hacking like software updates, firewalls, and antivirus software are also summarized.
Kinds of hackers

There are three main types of hackers: black hats, white hats, and gray hats. Black hat hackers illegally compromise security systems for personal gain or malicious purposes. White hat hackers ethically test security systems to help organizations by reporting vulnerabilities. Gray hat hackers fall between black and white hats, sometimes illegally accessing systems without permission but not for malicious ends.
Cybercrime (Computer Hacking)

This presentation deals with the past, present and future implications of cybercrime with respect to computer hacking.
Cyber hacking dev days by aes team

Hacking is an act of penetrating computer systems to gain knowledge about the system and how it works. This is considered illegal since it is like breaking into someone’s house.
What's hot (20)
National information security education & awareness program

National information security education & awareness program
Similar to Assignment 4
Ethical hacking tausif h4 ck3r

The document discusses ethical hacking, which refers to authorized security testing of systems to identify vulnerabilities. It notes that ethical hackers have the same skills as black hat hackers but perform attacks in a non-destructive manner with permission. It describes different types of ethical hackers like white hat and grey hat hackers and their purposes. The document also outlines the steps of an ethical hacking process including preparation, footprinting, and vulnerability identification.
Hacking

This document discusses hacking and provides definitions and examples. It defines hacking as unauthorized computer access and distinguishes between hackers and crackers. Various types of hacking are described such as password, email, and credit card hacking. The document also gives a brief history of hacking and reasons why hackers engage in hacking. Examples are provided for how to hack passwords on websites like Yahoo, Facebook, and Gmail.
Hacking_ The Ultimate Hacking for Beginners_ How to Hack_ Hacking Intelligenc...

This document provides an overview of hacking, including definitions of key terms like hacker, cracking, and cracker. It discusses different types of hackers like white hat, black hat, and grey hat hackers. It also covers computer security, computer crimes, cyber terrorism, and the top 10 intelligence agencies in the world. The document is an introductory guide to hacking that defines common terms and concepts.
Β. Hucking 

Hackers are people who try to gain unauthorized access to computer systems. Originally, the term "hacker" referred positively to computer enthusiasts who enjoyed programming, but it now generally refers to those who break into systems or use their skills maliciously. Common types of hacking include breaking into networks, bypassing passwords, defacing websites, and denial of service attacks. Hackers can steal valuable information like credit cards or install backdoors and programs to spy on users. Motives for hacking range from challenges, attention-seeking, education, and criminal plans to steal data and money. Famous hackers include Jonathan James, Kevin Mitnick, Albert Gonzalez, Kevin Poulsen, and Gary McKinnon.
Why Ethical Hacking Course in 2022.pdf

Vinsys is best Institute in Dubai for Ethical Hacking and Cybersecurity courses which offers complete aid regarding the matter of ethical hacking without any preparation.
Hacker cracker cybercrime-computer security

This document discusses computer security, ethics, hackers, crackers, and cybercrime. It defines computer security as protecting hardware, software, and stored information from threats. The importance of computer security is to protect users from different threats by installing security software like firewalls, antivirus, and anti-spyware. Cybercrime is any illegal act committed using computers or the internet, such as fraud, hacking, or spreading viruses. Hackers have in-depth network knowledge and create tools to break into systems, while crackers break in without permission using hacking tools for personal gain or damage. The document provides examples of hacking and cracking and assignment questions related to these topics.
Ethical-Hacking.pdf

Ethical Hacking is the process of legal activities of accessing the system security and identifying the data breaks and the network threats, and solves the issues by not letting the data easily available to everyone. At Vinsys, we provide ethical hacking courses and other cybersecurity related courses. You can attend our online training in UAE, Saudi Arabia, Kuwait and get trained from our subject matter experts.
Hacking vs cracking

This document discusses the differences between hacking and cracking. Hacking refers to gaining unauthorized access to a computer system out of curiosity or challenge, and without intent to cause harm. Cracking, on the other hand, is the illegal act of gaining unauthorized access with the intent to damage systems or data. The objectives of hackers are exploration and learning, while crackers aim to steal data and break security measures for personal gain or malicious purposes. Key differences are that hacking itself is legal while cracking is illegal, and hackers create code while crackers break code.
module 3 Cyber Risks and Incident Management.pptx

This document provides an overview of cyber risks and incident management. It discusses types of hackers like black hat, white hat, and grey hat hackers. It covers cyberattacks, vulnerabilities, critical security components, and the dark web and deep web. It also addresses incident management, governance and compliance, cybersecurity design, maintaining resilience, security operation centers, digital forensics, cyber risks, cyber insurance, network security, cloud security, and application security.
Hacking ppt

Hacking involves gaining unauthorized access to computer systems or networks. There are three main types of hackers: white hats who hack for security testing, black hats who hack maliciously, and grey hats who may hack to expose vulnerabilities but also for profit. Common hacking targets include passwords, emails, websites, and credit card numbers. While hacking can be used to recover lost passwords or test security, it is illegal and poses disadvantages like enabling criminals to steal data, violating privacy, and allowing competitors to destroy work.
Hackingppt 160730081605

Hacking involves gaining unauthorized access to computer systems or networks. There are three main types of hackers: white hats who hack for security testing, black hats who hack maliciously, and grey hats who may hack to expose vulnerabilities but also for profit. Common hacking targets include passwords, emails, websites, and credit card numbers. While hacking can be used to recover lost passwords or test security, it is illegal and poses disadvantages like enabling criminals, harming privacy, and allowing destruction of work.
Hacking

This document discusses hacking, including definitions of hacking and different types of hackers. It defines hacking as gaining unauthorized access to a computer or network. Hackers are expert programmers who break into systems. There are three main types of hackers - white hats who help security, black hats who hack maliciously, and grey hats who notify admins of vulnerabilities. The document also outlines the history of hacking and different types of hacking like password, email, and website hacking. It provides examples of how to hack passwords, email, websites, and credit cards. Finally, it lists ways to prevent hacking like installing firewalls and antivirus software, changing passwords regularly, and not giving out personal information.
Hackers ethics presentation

This document discusses hackers and ethical hacking. It defines hackers as computer enthusiasts who use their skills for both legal and illegal purposes. Ethical hackers are employed by companies to test security vulnerabilities, while black-hat and grey-hat hackers engage in unauthorized hacking activities. The document outlines different types of hackers and their roles, as well as tools used in ethical hacking like Sam Spade to gather host information. The conclusion emphasizes the importance of understanding hacking techniques to strengthen security and prevent unauthorized access.
Ethical hacking

Ethical hacking also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal. Ethical hacking is performed with the target’s permission. The intent of ethical hacking is to discover vulnerabilities from a hacker’s viewpoint so systems can be better secured. Its part of an overall information risk management program that allows for ongoing security improvements. Ethical hacking can also ensure that vendors’ claims about the security of their products are legitimate.
What is a Hacker (part 2): How data is stolen

The simple answer is that hackers break into computers by exploiting vulnerabilities. The vulnerability might not even be computer-related; it can be a new employee unfamiliar with the companies security routines.
Introduction to Ethical Hacking (Basics)

Basic information about Ethical Hacking. :)
Includes What is hacking, Hacking types, Different levels in hackers.
Computer hacking

The document provides an overview of computer hacking including its history, types of hackers and their motivations, common hacking tools, and ways to prevent hacking. It discusses how hacking involves illegally accessing private information from computer systems and networks with malicious intent. Hacking is considered a serious crime under federal and international law. The document also explores debates around the definition of "hacker" and whether all forms of hacking should be considered unethical.
Ethical Hacking And Hacking Attacks

I published a paper on "Ethical Hacking And Hacking Attacks". The purpose of the paper is to tell that what is hacking, who are hackers, their types and some hacking attacks performed by them. In the paper I also discussed that how these attacks are performed.
Armand Hacking

This document summarizes the history and types of hacking, the effects of hacking, and ways to avoid being hacked. It discusses how hacking started as a study of computers and how some well-known hackers gained notoriety. It describes academic, hobby, and security hackers. It also outlines the malicious intents of some hackers, such as stealing personal or business information, and how they can infect systems with viruses or trojans. Finally, it recommends using a firewall and up-to-date antivirus software to help prevent hacking.
Computer ethics

The document discusses various topics related to computer ethics. It begins by defining computer ethics as enforcing ethical implementation and use of computing resources through avoiding copyright infringement and unauthorized distribution of digital content. It then lists 10 commandments of computer ethics established by the Computer Ethics Institute in 1992. Some concepts that can lead to unethical computer use discussed include data stealing, cybercrime, hacking, and embezzlement. Cybercrime refers to criminal acts involving computers or networks. Common types of cybercrime are hacking, stealing software/data, and identity theft. Data theft is also common using devices like USB drives to copy large amounts of data. Hacking involves exploiting security weaknesses for unauthorized access, while social engineering and malware attacks are other risks.
Similar to Assignment 4 (20)
Hacking_ The Ultimate Hacking for Beginners_ How to Hack_ Hacking Intelligenc...

Hacking_ The Ultimate Hacking for Beginners_ How to Hack_ Hacking Intelligenc...
Recently uploaded
Should Repositories Participate in the Fediverse?

Presentation for OR2024 making the case that repositories could play a part in the "fediverse" of distributed social applications
一比一原版(USYD毕业证)悉尼大学毕业证如何办理

USYD硕士毕业证成绩单【微信95270640】《如何办理悉尼大学毕业证认证》【办证Q微信95270640】《悉尼大学文凭毕业证制作》《USYD学历学位证书哪里买》办理悉尼大学学位证书扫描件、办理悉尼大学雅思证书!
国际留学归国服务中心《如何办悉尼大学毕业证认证》《USYD学位证书扫描件哪里买》实体公司,注册经营,行业标杆,精益求精!
如果您是以下情况,我们都能竭诚为您解决实际问题:【公司采用定金+余款的付款流程,以最大化保障您的利益,让您放心无忧】
1、在校期间,因各种原因未能顺利毕业,拿不到官方毕业证+微信95270640
2、面对父母的压力,希望尽快拿到悉尼大学悉尼大学毕业证offer;
3、不清楚流程以及材料该如何准备悉尼大学悉尼大学毕业证offer;
4、回国时间很长,忘记办理;
5、回国马上就要找工作,办给用人单位看;
6、企事业单位必须要求办理的;
面向美国乔治城大学毕业留学生提供以下服务:
【★悉尼大学悉尼大学毕业证offer毕业证、成绩单等全套材料,从防伪到印刷,从水印到钢印烫金,与学校100%相同】
【★真实使馆认证(留学人员回国证明),使馆存档可通过大使馆查询确认】
【★真实教育部认证,教育部存档,教育部留服网站可查】
【★真实留信认证,留信网入库存档,可查悉尼大学悉尼大学毕业证offer】
我们从事工作十余年的有着丰富经验的业务顾问,熟悉海外各国大学的学制及教育体系,并且以挂科生解决毕业材料不全问题为基础,为客户量身定制1对1方案,未能毕业的回国留学生成功搭建回国顺利发展所需的桥梁。我们一直努力以高品质的教育为起点,以诚信、专业、高效、创新作为一切的行动宗旨,始终把“诚信为主、质量为本、客户第一”作为我们全部工作的出发点和归宿点。同时为海内外留学生提供大学毕业证购买、补办成绩单及各类分数修改等服务;归国认证方面,提供《留信网入库》申请、《国外学历学位认证》申请以及真实学籍办理等服务,帮助众多莘莘学子实现了一个又一个梦想。
专业服务,请勿犹豫联系我
如果您真实毕业回国,对于学历认证无从下手,请联系我,我们免费帮您递交
诚招代理:本公司诚聘当地代理人员,如果你有业余时间,或者你有同学朋友需要,有兴趣就请联系我
你赢我赢,共创双赢
你做代理,可以帮助悉尼大学同学朋友
你做代理,可以拯救悉尼大学失足青年
你做代理,可以挽救悉尼大学一个个人才
你做代理,你将是别人人生悉尼大学的转折点
你做代理,可以改变自己,改变他人,给他人和自己一个机会过暑假的小学生快乐的日子总是过得飞快山娃尚未完全认清那几位小朋友时他们却一个接一个地回家了山娃这时才恍然发现二个月的暑假已转到了尽头他的城市生活也将划上一个不很圆满的句号了值得庆幸的是山娃早记下了他们的学校和联系方式说也奇怪在山娃离城的头一天父亲居然请假陪山娃耍了一天那一天父亲陪着山娃辗转长隆水上乐园疯了一整天水上漂流高空冲浪看大马戏大凡里面有的父亲都带着他去疯一把山娃算了算这一次足足花了老爸元很
快速办理(Vic毕业证书)惠灵顿维多利亚大学毕业证完成信一模一样

学校原件一模一样【微信:741003700 】《(Vic毕业证书)惠灵顿维多利亚大学毕业证》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
HijackLoader Evolution: Interactive Process Hollowing

CrowdStrike researchers have identified a HijackLoader (aka IDAT Loader) sample that employs sophisticated evasion techniques to enhance the complexity of the threat. HijackLoader, an increasingly popular tool among adversaries for deploying additional payloads and tooling, continues to evolve as its developers experiment and enhance its capabilities.
In their analysis of a recent HijackLoader sample, CrowdStrike researchers discovered new techniques designed to increase the defense evasion capabilities of the loader. The malware developer used a standard process hollowing technique coupled with an additional trigger that was activated by the parent process writing to a pipe. This new approach, called "Interactive Process Hollowing", has the potential to make defense evasion stealthier.
怎么办理(umiami毕业证书)美国迈阿密大学毕业证文凭证书实拍图原版一模一样

原版定制【微信:bwp0011】《(umiami毕业证书)美国迈阿密大学毕业证文凭证书》【微信:bwp0011】成绩单 、雅思、外壳、留信学历认证永久存档查询,采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信bwp0011】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信bwp0011】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...

Adli Wahid, Senior Internet Security Specialist at APNIC, delivered a presentation titled 'Honeypots Unveiled: Proactive Defense Tactics for Cyber Security' at the Phoenix Summit held in Dhaka, Bangladesh from 23 to 24 May 2024.
Bengaluru Dreamin' 24 - Personal Branding

Session on Personal Branding presented at Bengaluru Dreamin
Discover the benefits of outsourcing SEO to India

"Discover the benefits of outsourcing SEO to India! From cost-effective services and expert professionals to round-the-clock work advantages, learn how your business can achieve digital success with Indian SEO solutions.
快速办理(新加坡SMU毕业证书)新加坡管理大学毕业证文凭证书一模一样

学校原件一模一样【微信:741003700 】《(新加坡SMU毕业证书)新加坡管理大学毕业证文凭证书》【微信:741003700 】学位证,留信认证(真实可查,永久存档)原件一模一样纸张工艺/offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原。
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
【主营项目】
一.毕业证【q微741003700】成绩单、使馆认证、教育部认证、雅思托福成绩单、学生卡等!
二.真实使馆公证(即留学回国人员证明,不成功不收费)
三.真实教育部学历学位认证(教育部存档!教育部留服网站永久可查)
四.办理各国各大学文凭(一对一专业服务,可全程监控跟踪进度)
如果您处于以下几种情况:
◇在校期间,因各种原因未能顺利毕业……拿不到官方毕业证【q/微741003700】
◇面对父母的压力,希望尽快拿到;
◇不清楚认证流程以及材料该如何准备;
◇回国时间很长,忘记办理;
◇回国马上就要找工作,办给用人单位看;
◇企事业单位必须要求办理的
◇需要报考公务员、购买免税车、落转户口
◇申请留学生创业基金
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
一比一原版新西兰林肯大学毕业证(Lincoln毕业证书)学历如何办理

原版办【微信号:95270640】【新西兰林肯大学毕业证(Lincoln毕业证书)】【微信号:95270640】《成绩单、外壳、雅思、offer、真实留信官方学历认证(永久存档/真实可查)》采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路)我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信号95270640】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信号95270640】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
Securing BGP: Operational Strategies and Best Practices for Network Defenders...

Md. Zobair Khan,
Network Analyst and Technical Trainer at APNIC, presented 'Securing BGP: Operational Strategies and Best Practices for Network Defenders' at the Phoenix Summit held in Dhaka, Bangladesh from 23 to 24 May 2024.
办理新西兰奥克兰大学毕业证学位证书范本原版一模一样

原版一模一样【微信:741003700 】【新西兰奥克兰大学毕业证学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Recently uploaded (12)
HijackLoader Evolution: Interactive Process Hollowing

HijackLoader Evolution: Interactive Process Hollowing
Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...

Honeypots Unveiled: Proactive Defense Tactics for Cyber Security, Phoenix Sum...
Securing BGP: Operational Strategies and Best Practices for Network Defenders...

Securing BGP: Operational Strategies and Best Practices for Network Defenders...
Assignment 4
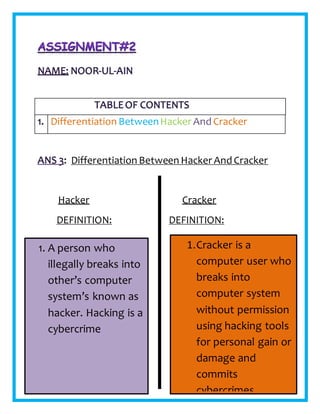
- 1. Differentiation Between Hacker And Cracker Hacker Cracker DEFINITION: DEFINITION: Differentiation BetweenHacker And Cracker 1. A person who illegally breaks into other’s computer system’s known as hacker. Hacking is a cybercrime 1.Cracker is a computer user who breaks into computer system without permission using hacking tools for personal gain or damage and commits cybercrimes.
- 2. 2. Hackers are computer experts who try to gain unauthorized access to computer system for stealing and corrupting information. 3. Most of the hackers break into computers for financial benefits. They try to get credit card details or bank account information so that they can steal money. 4. Hackers have in- depth knowledge on network programming and can create tools and malicious software for others to break into 2. Most of the crackers does not have professional computer skill to hack computer system but they have knowledge about using hacking tools 3. Crackers break into computers and cause serious damage. They also break into Web server and replace the home page of a website with a page of their own design. 4. Cracker doesnot have indepth knowledge on network programming.
- 3. Example: A hacker can develop software in which all the dictionary file is loaded that contains all the dictionary words. When the software is run it tries all the dictionary wordsone by one as password to hack a computer. This methodworks if the user is having a simple password that exists a dictionary. Example: A cracker can install a key logger on another user’s computer through internet. A key-logger is a software that records every letter typed on keyboard. When the user uses Facebook and enters the Facebook account details, it will be recorded in the cracker’s computer. Now, he can easily hack the Facebook account.