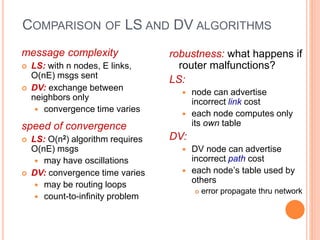
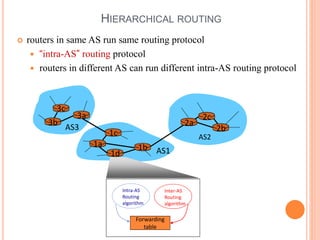
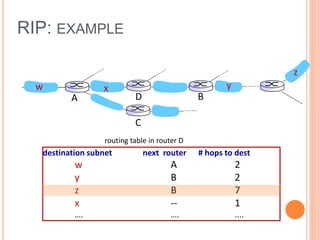
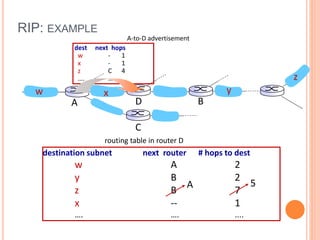
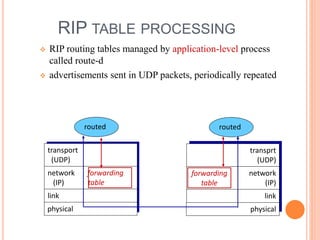
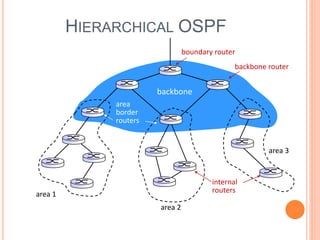
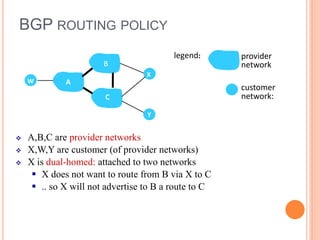
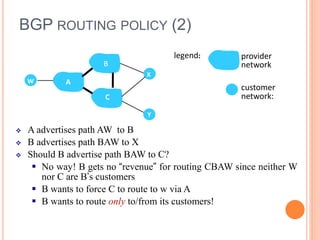
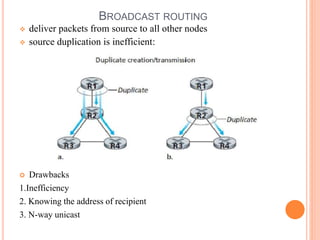
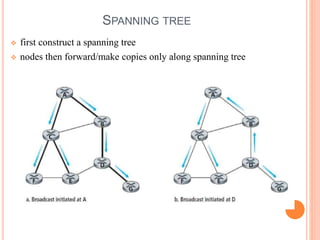
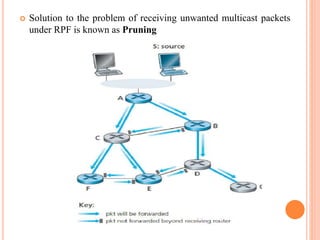
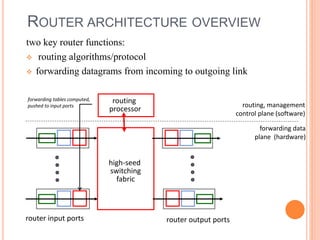
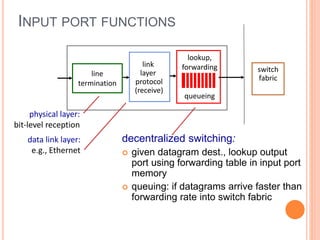
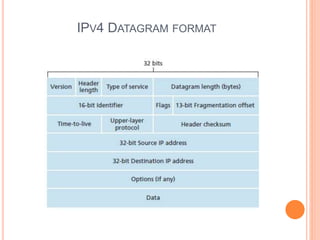
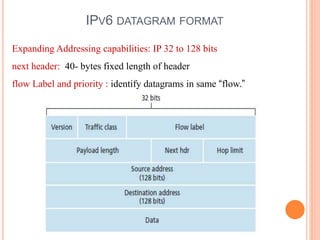
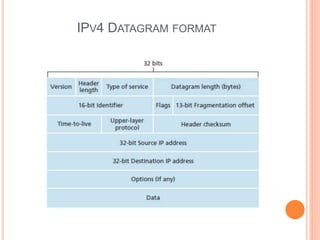
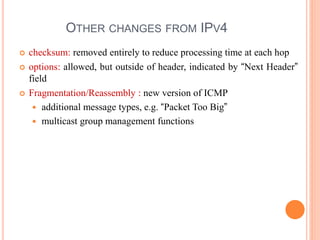
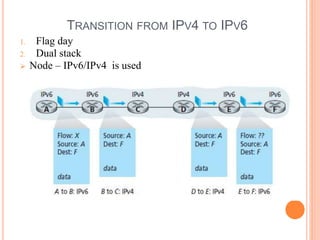
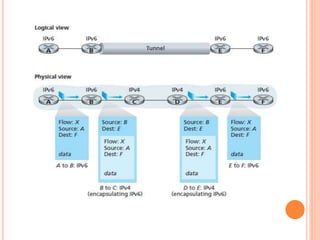
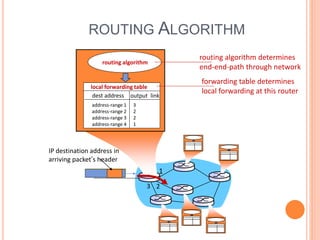
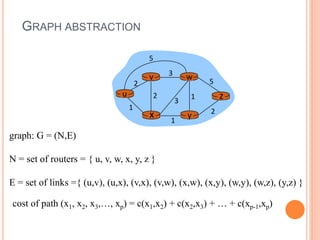
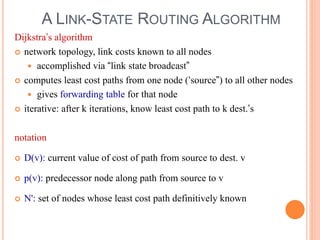
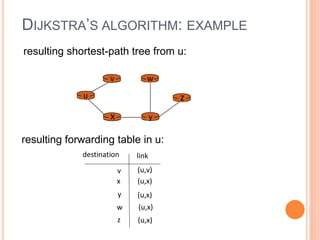
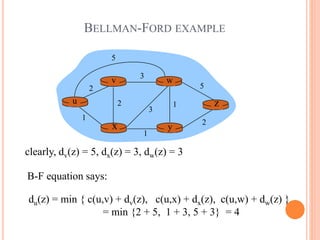
This document provides an overview of key concepts in the network layer, including the architecture of routers, IPv6, routing algorithms like link state and distance vector, and routing protocols like RIP, OSPF, and BGP. It discusses router functions such as routing algorithms/protocols and packet forwarding. It also covers topics like switching fabrics, queuing, and hierarchical routing between autonomous systems.






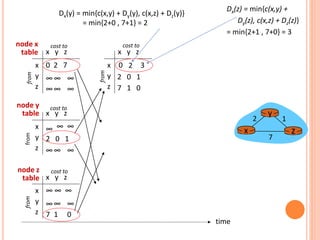
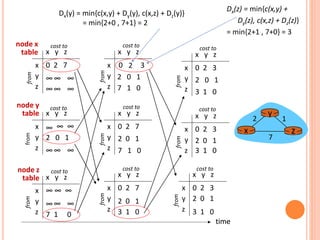
![DISTANCE VECTOR ALGORITHM
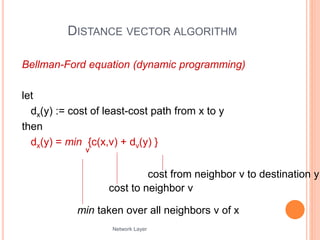
Dx(y) = estimate of least cost from x to y
x maintains distance vector Dx = [Dx(y): y in N ]
node x:
knows cost to each neighbor v: c(x,v)
maintains its neighbors’ distance vectors. For each
neighbor v, x maintains
Dv = [Dv(y): y in N ]](https://image.slidesharecdn.com/module3-transportlayer-240416133403-a767ab46/85/Module-3-transport_layer-pptx-26-320.jpg)