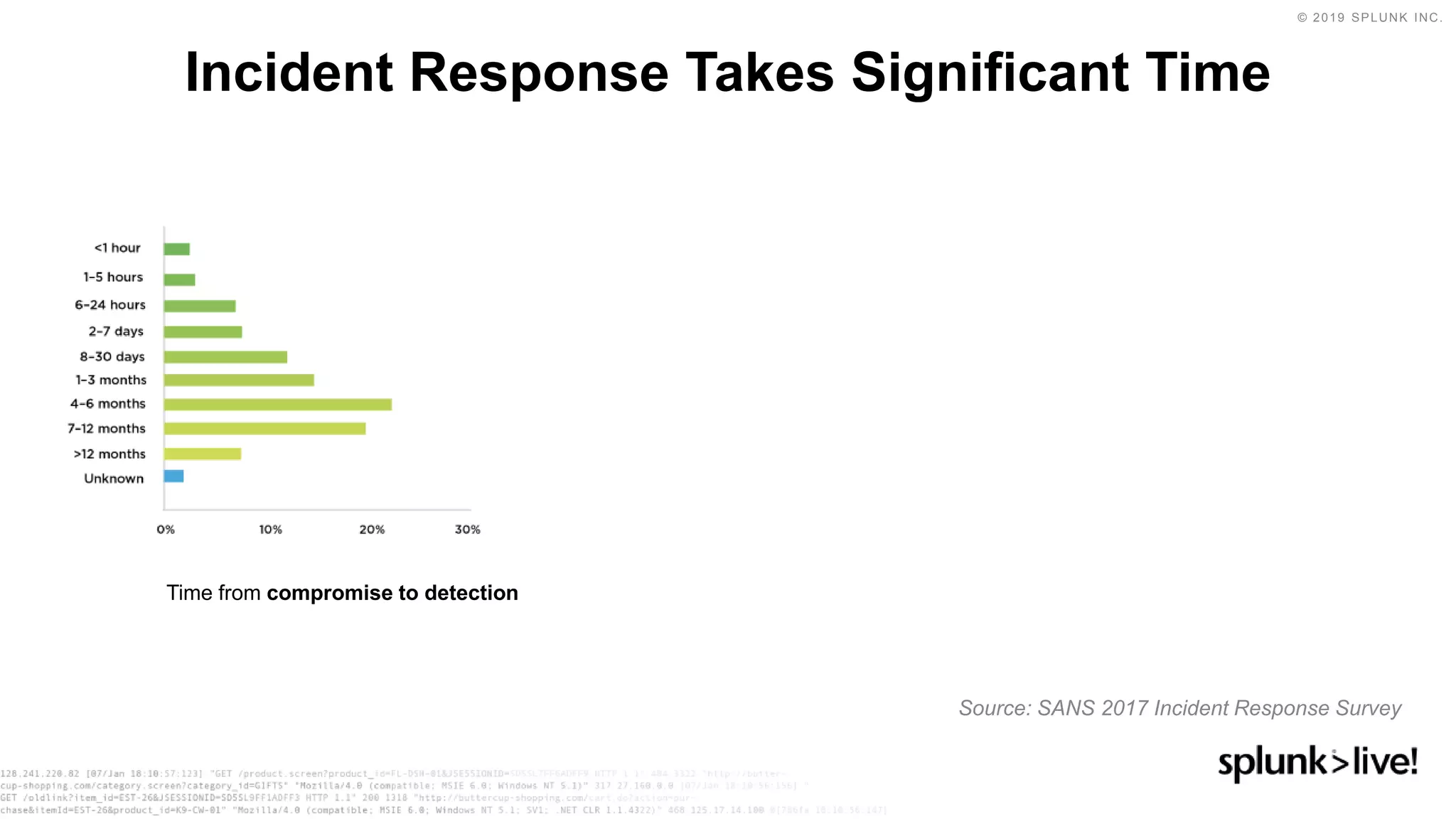
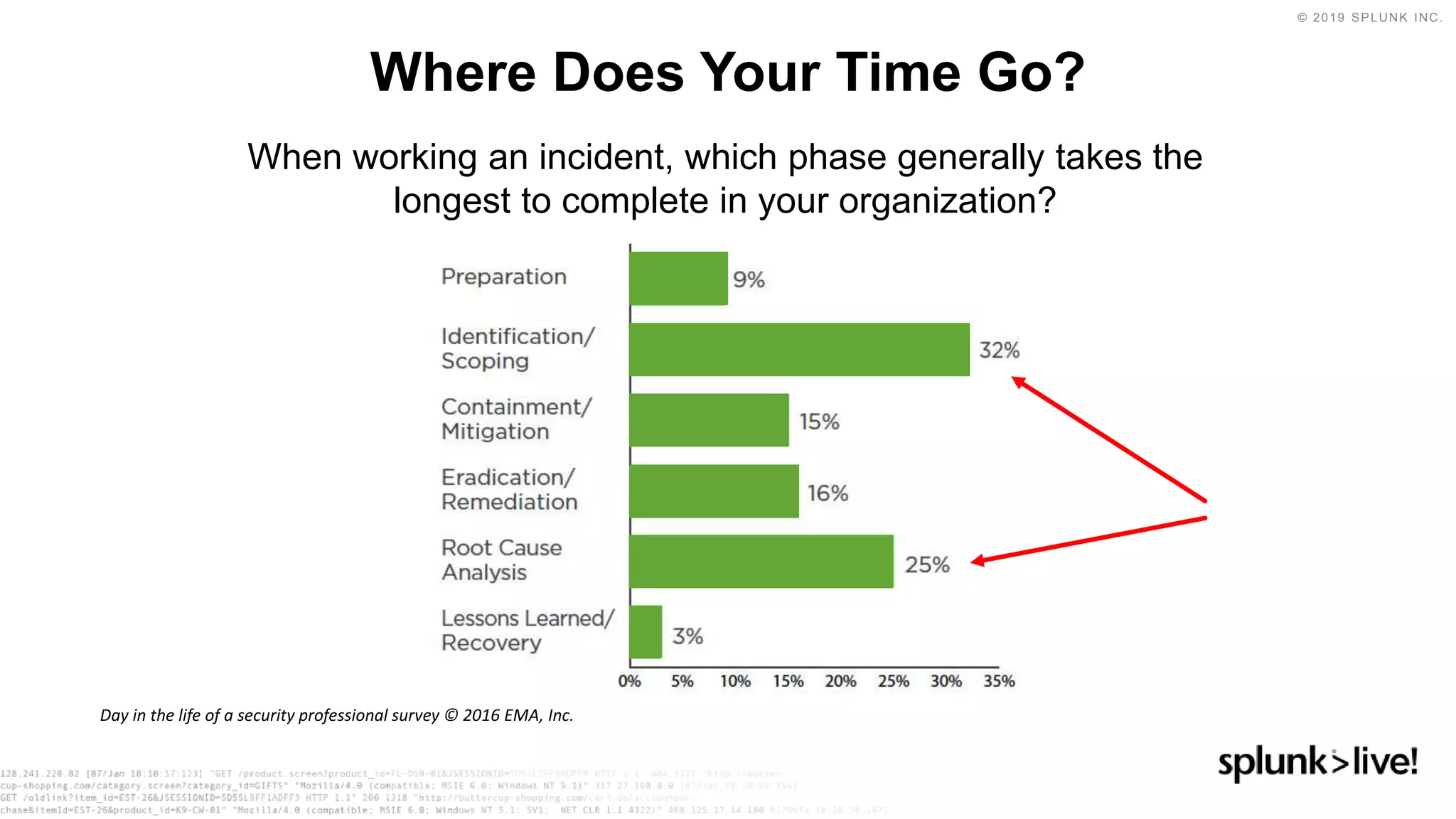
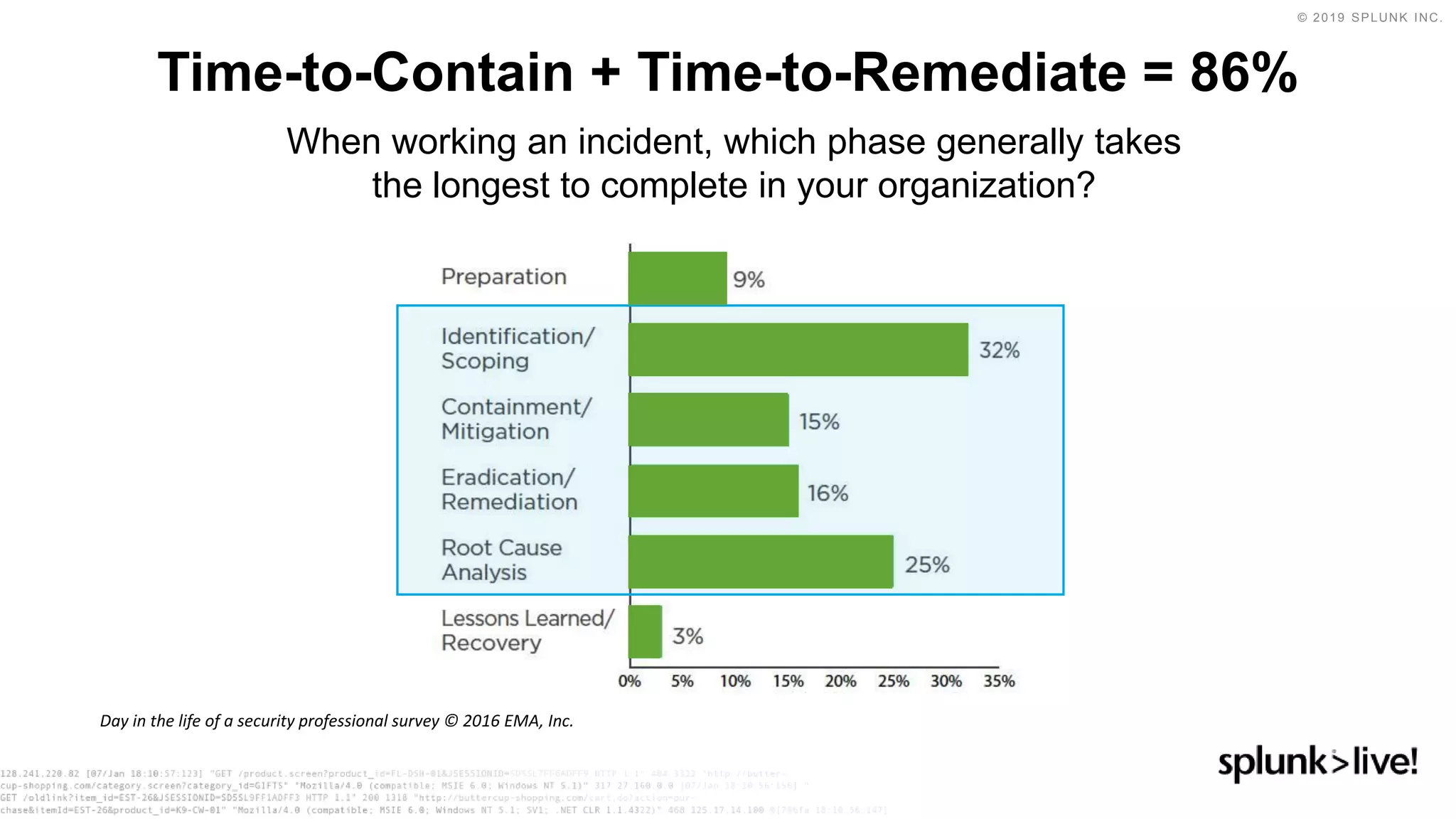
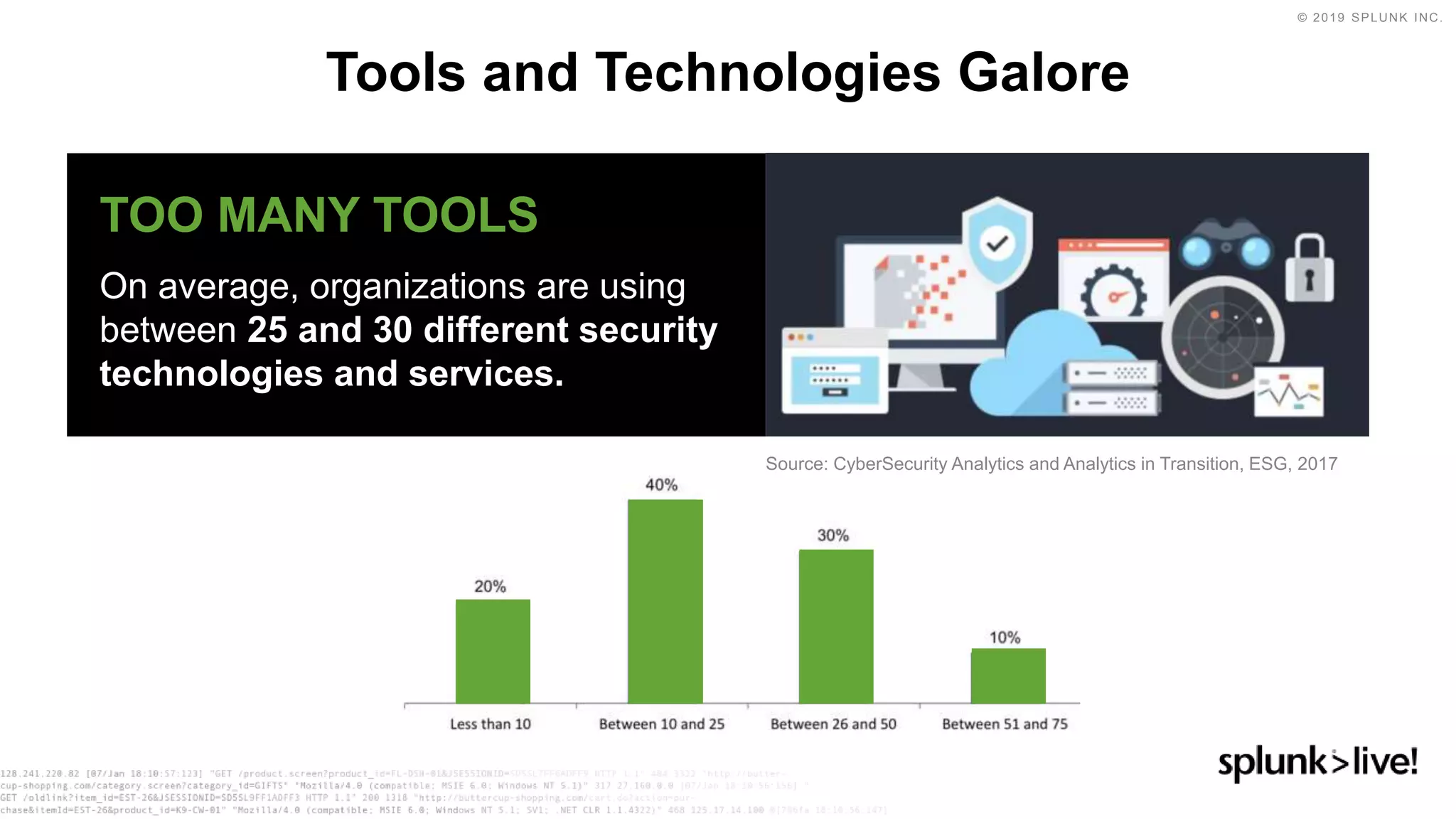
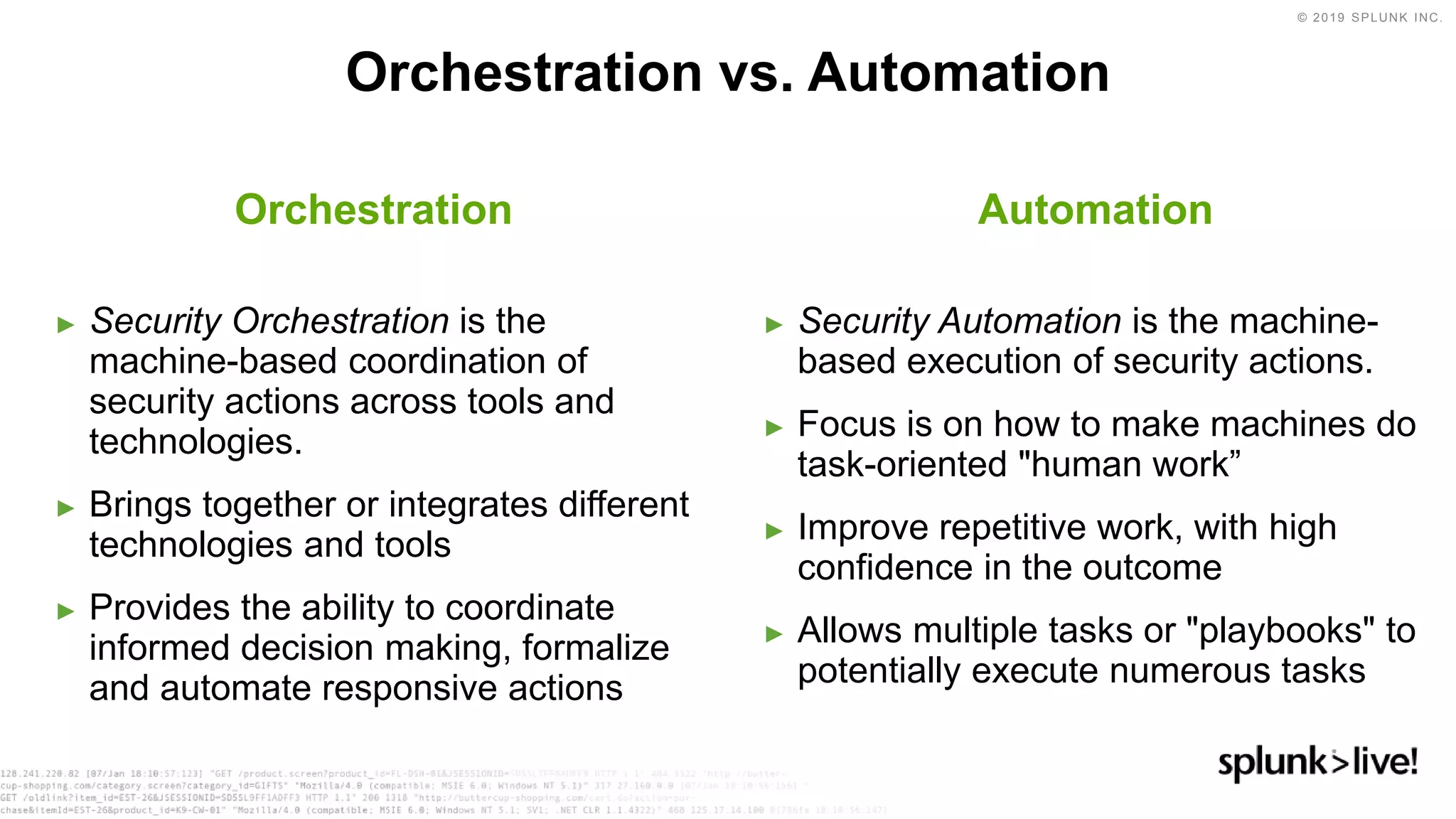
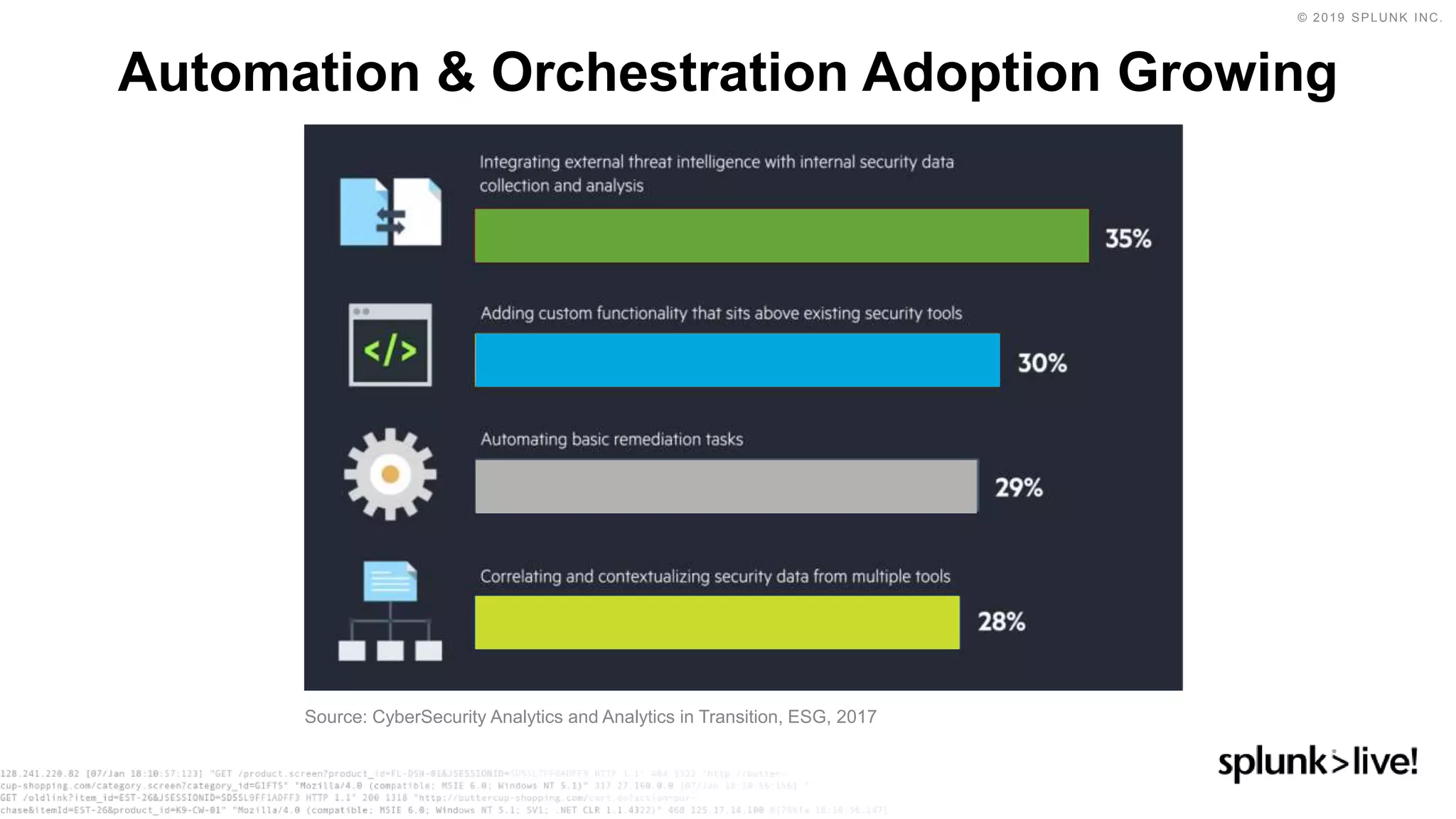
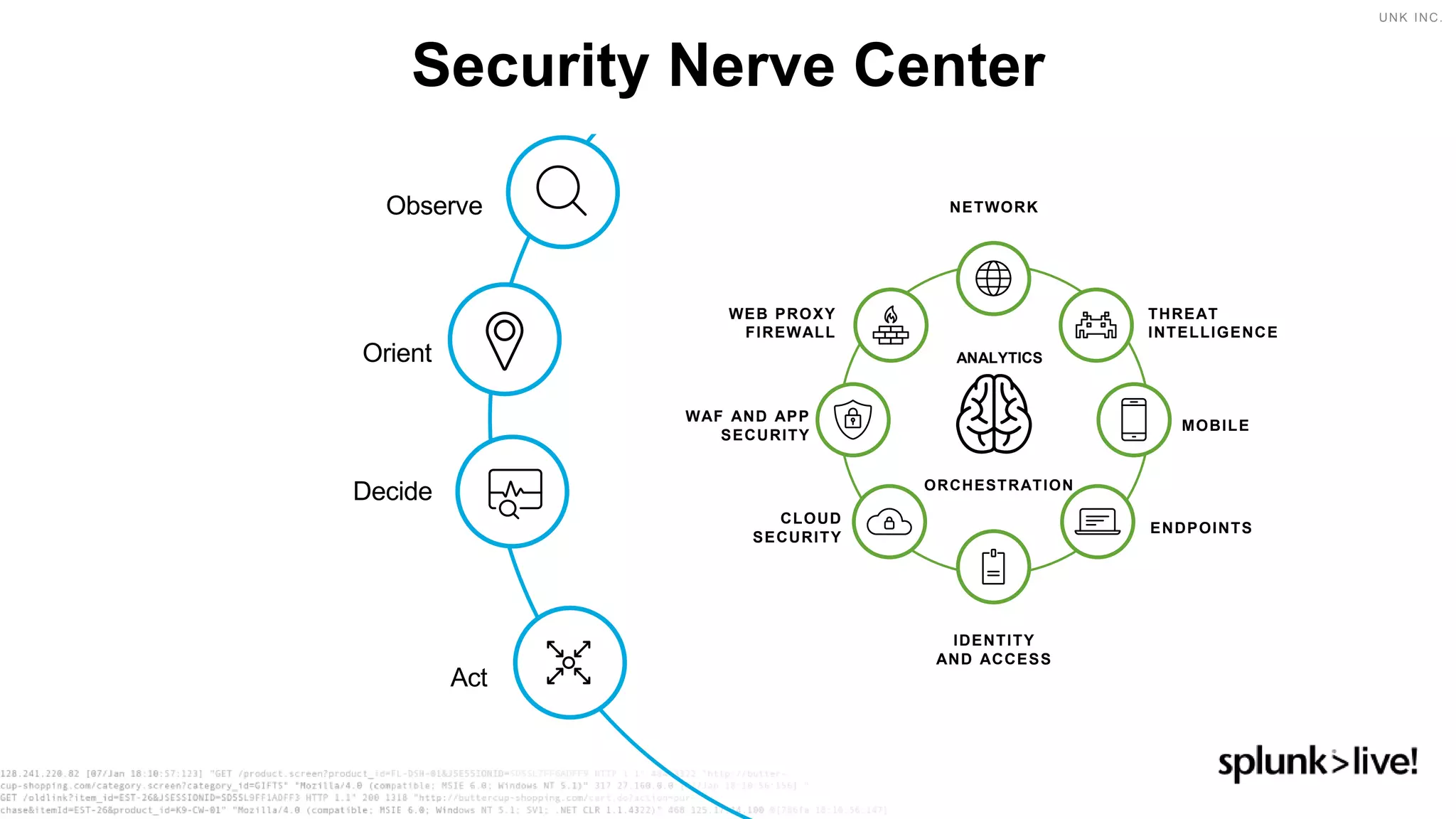
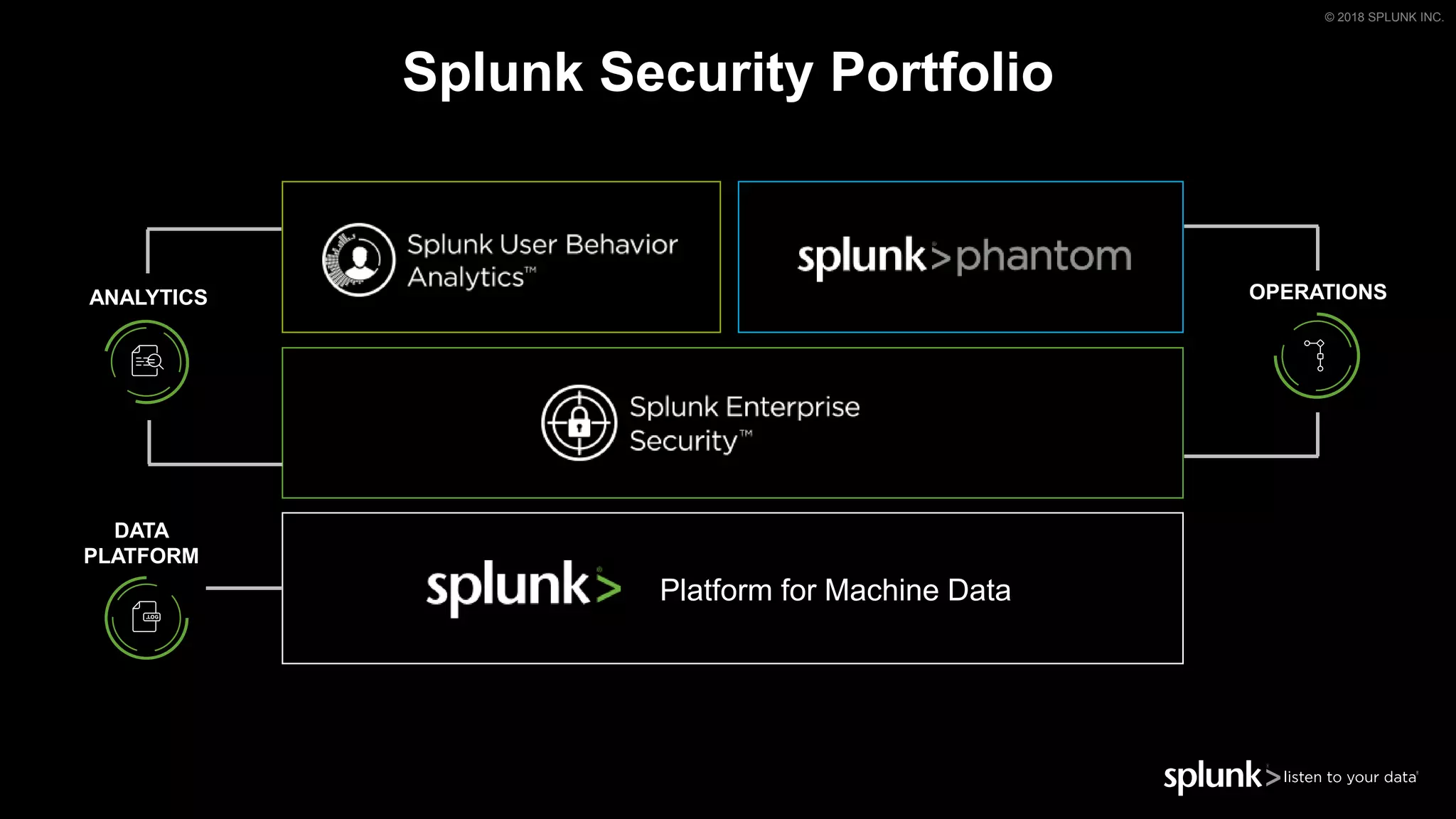
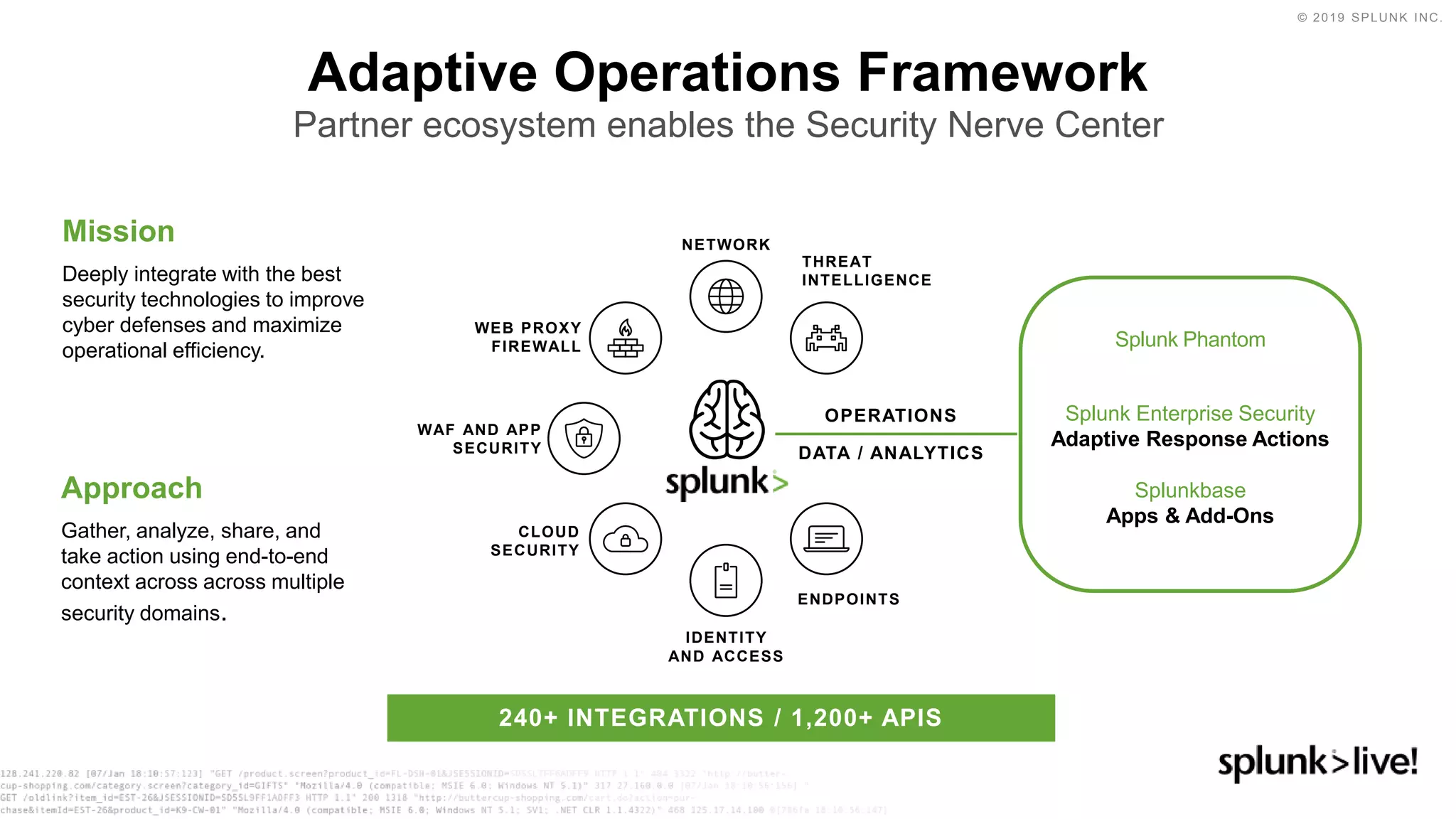
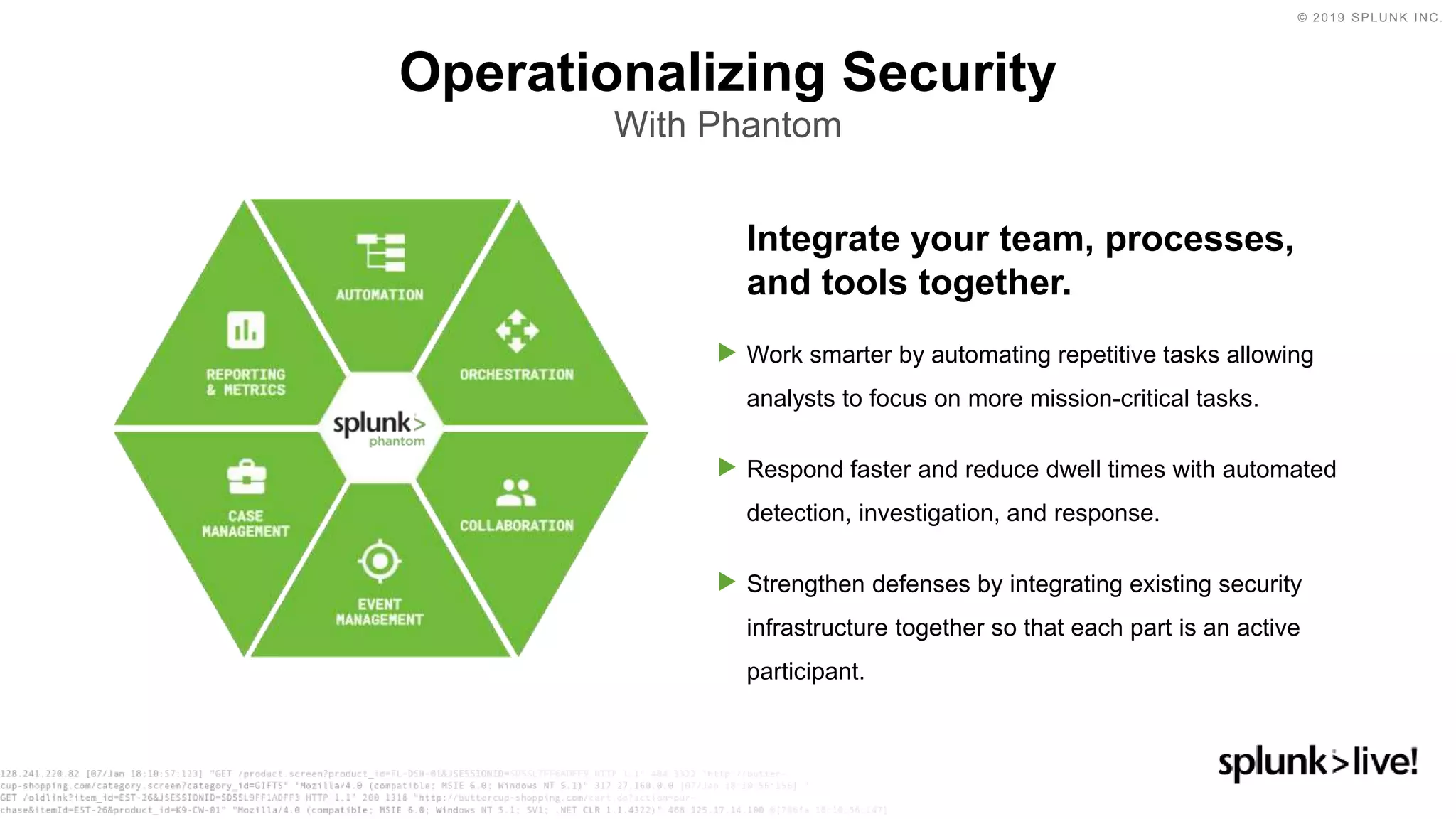
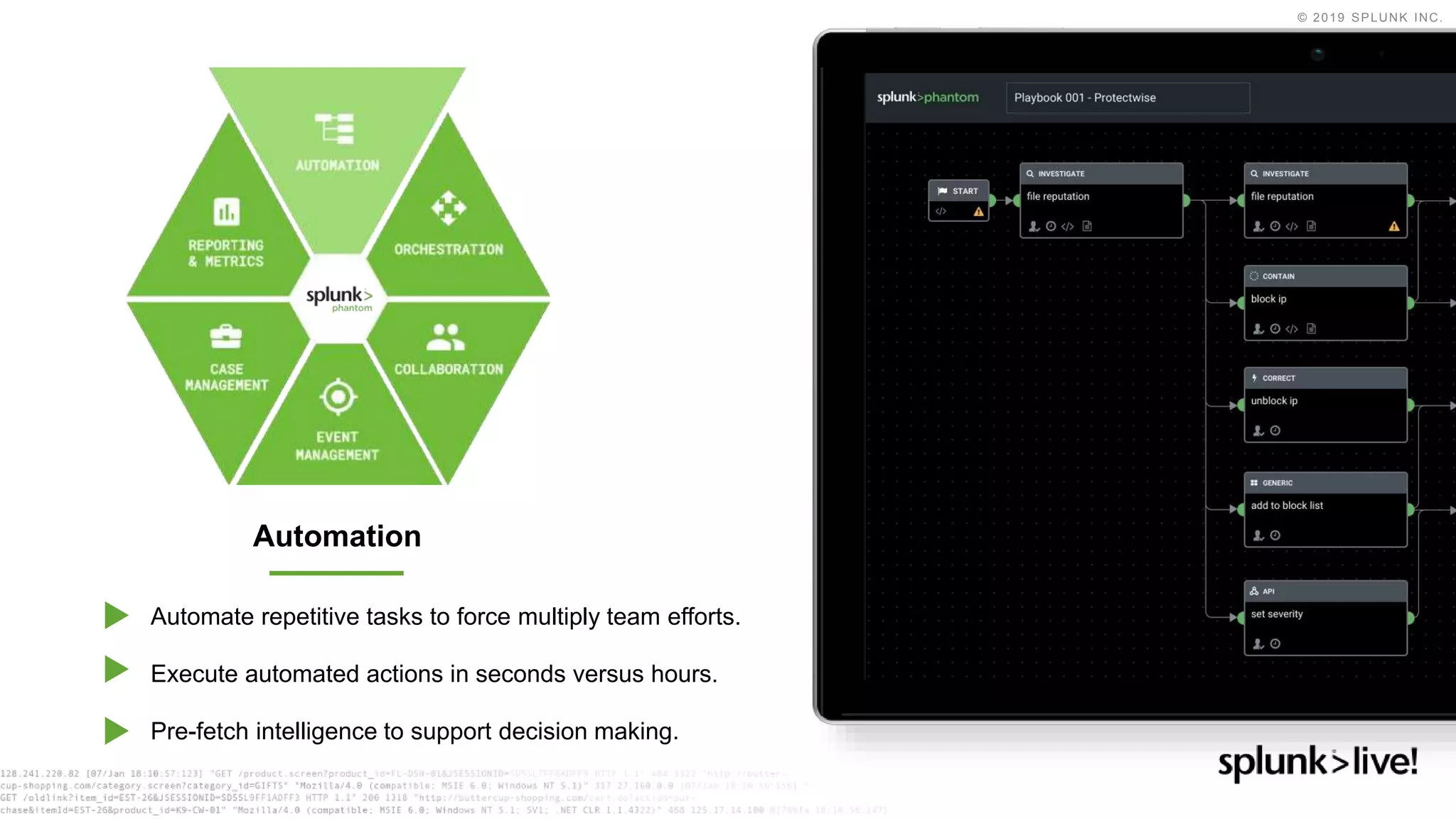
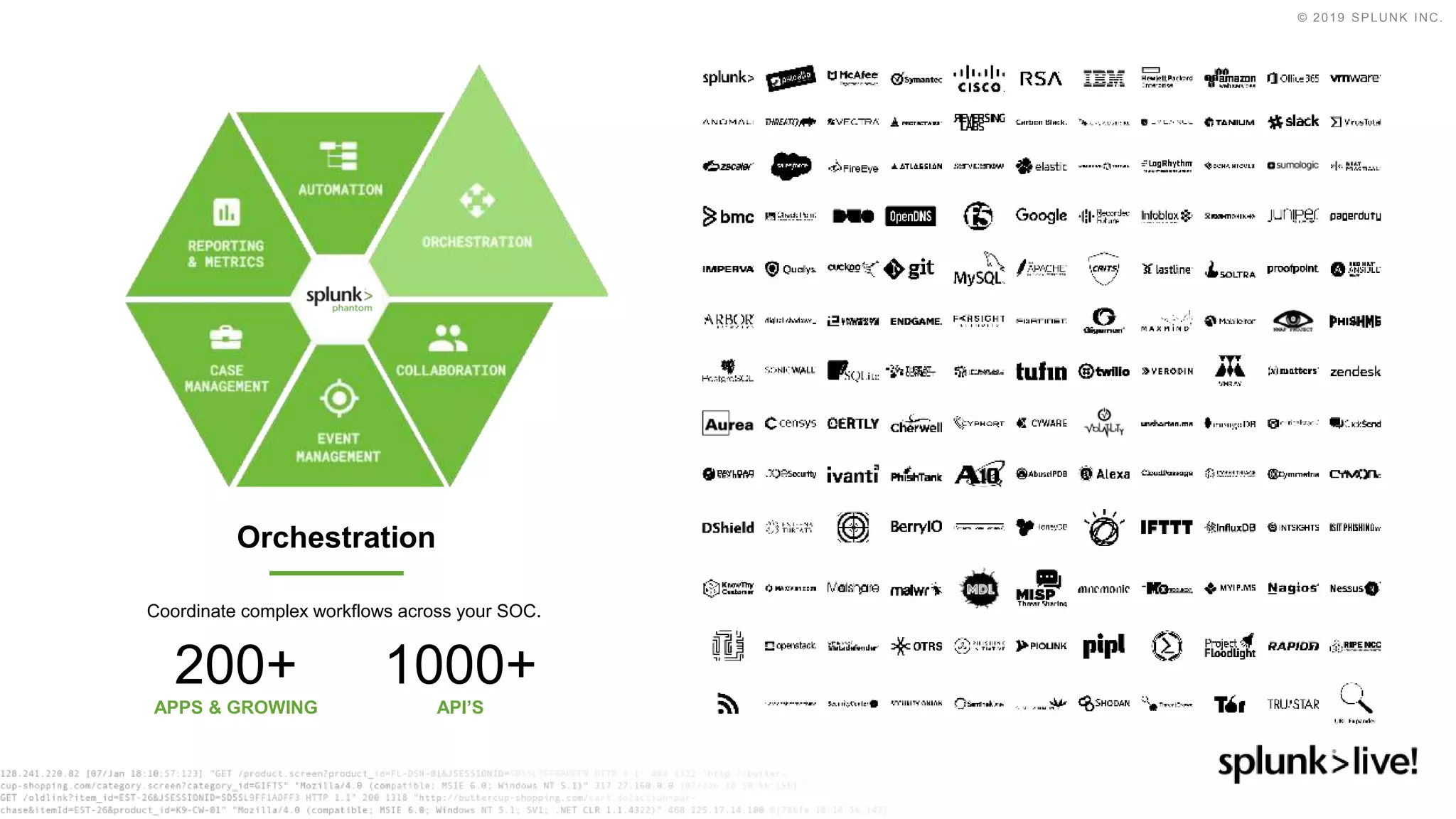
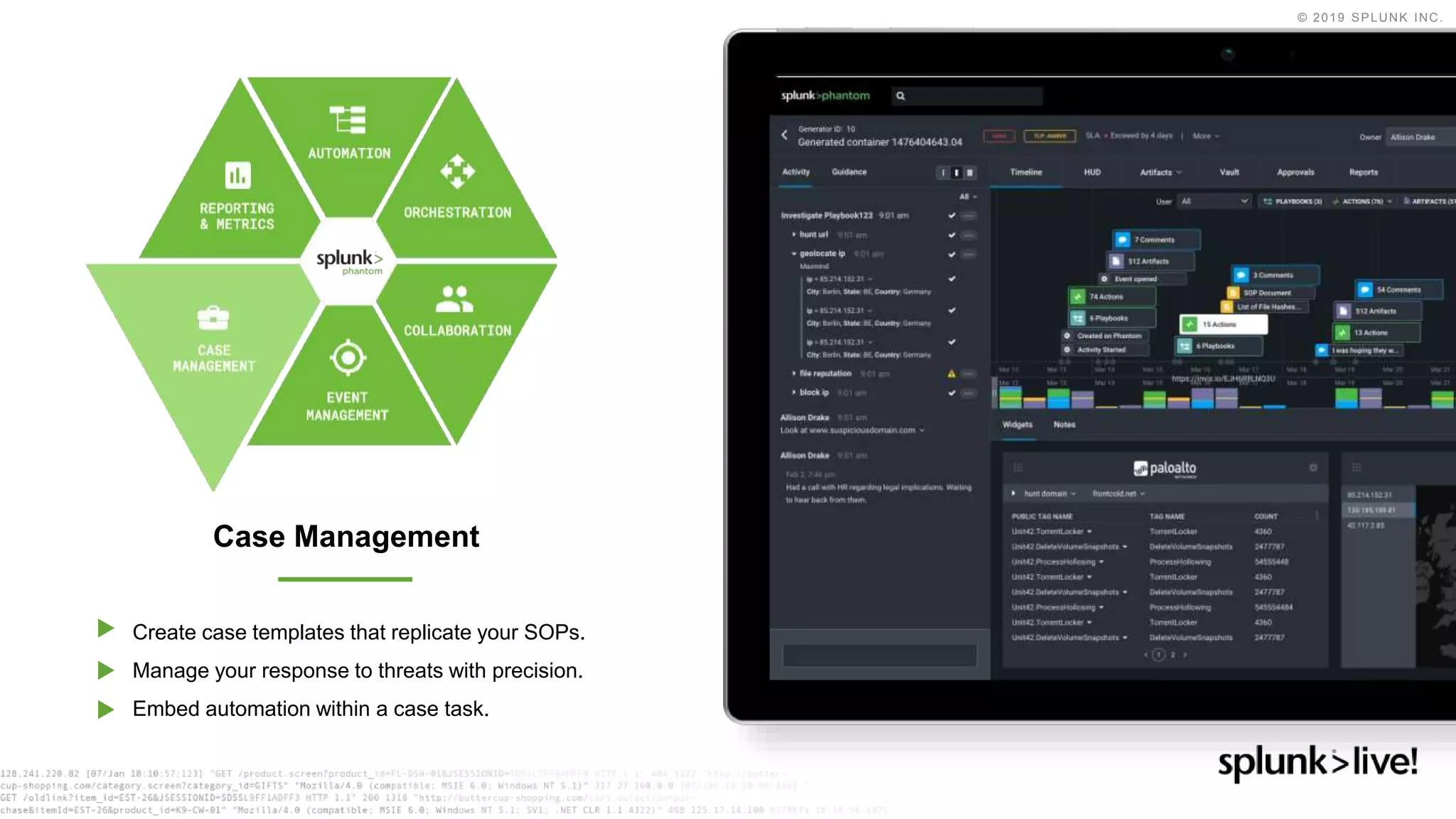
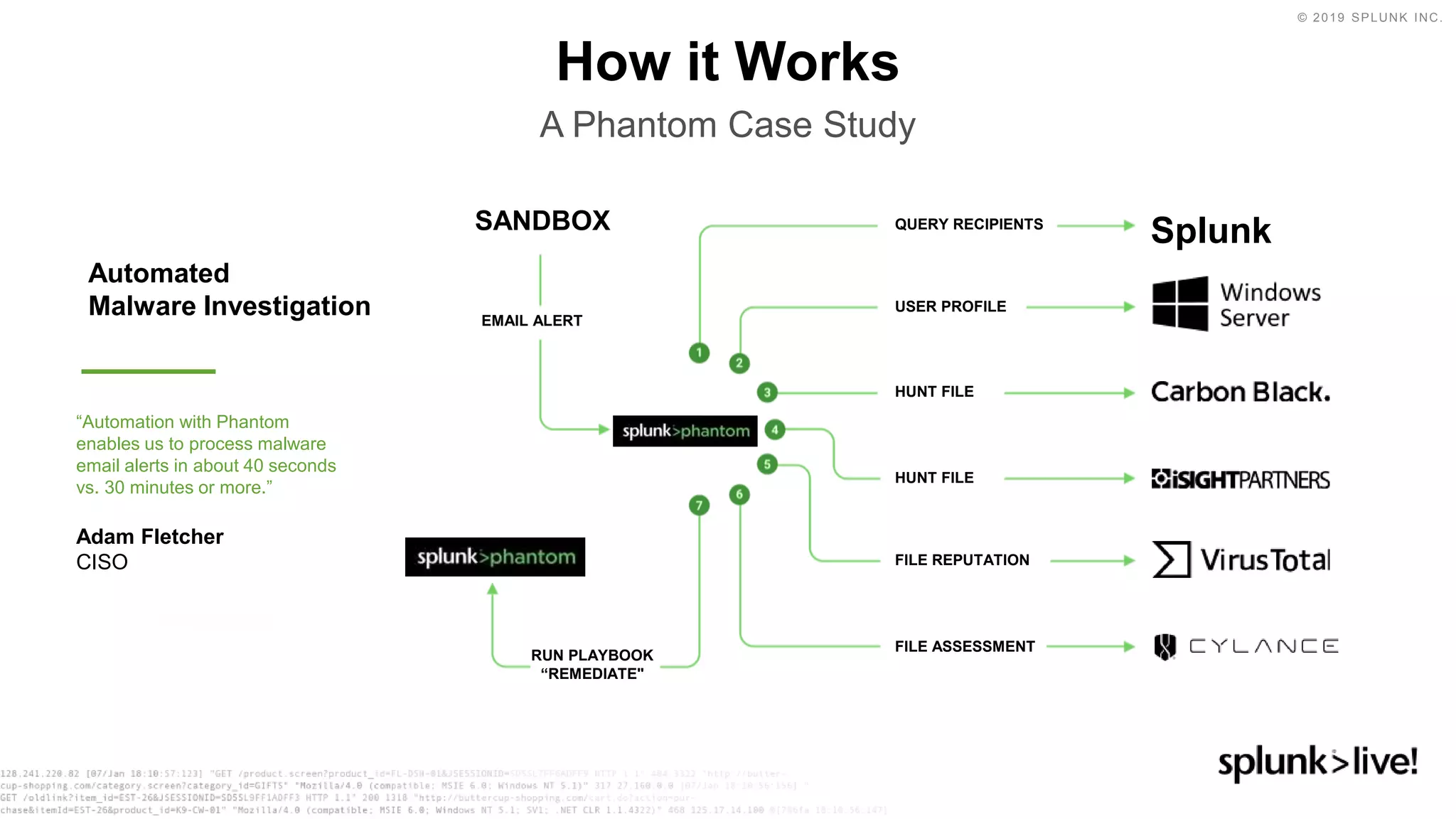
This document discusses how orchestration and automation can accelerate incident response. It notes that incident response currently takes a significant amount of time, with the majority of time spent on containment and remediation. It also states that security operations are challenged by too many alerts, a lack of integration between tools, and difficulties attracting, training and retaining skills at scale. The document argues that orchestration and automation can help address these challenges by coordinating security actions across tools and technologies, and executing repetitive security tasks. It provides an overview of Splunk's security portfolio for operationalizing security, including the Splunk Phantom platform for security orchestration and automation.