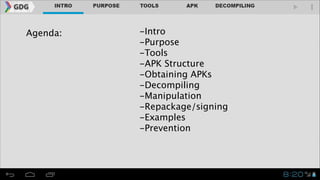
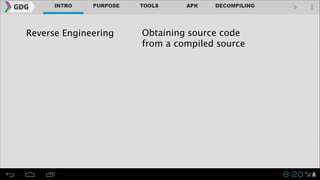
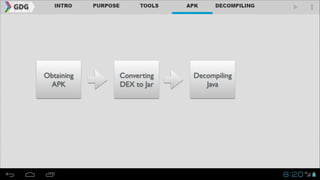
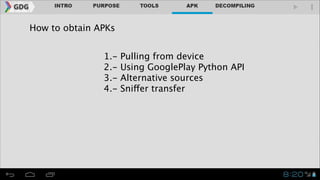
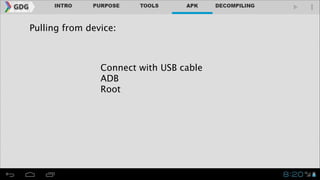
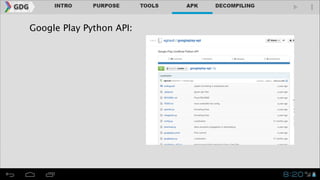
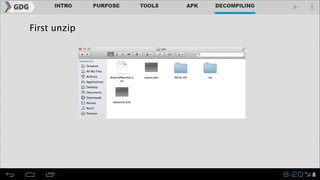
- The document outlines an agenda for covering topics related to reverse engineering Android applications (APKs), including obtaining APKs, decompiling them, manipulating the code, and repackaging/signing the APK.
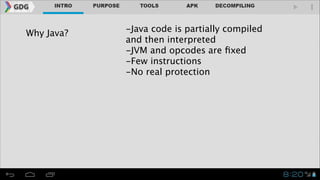
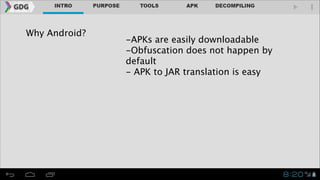
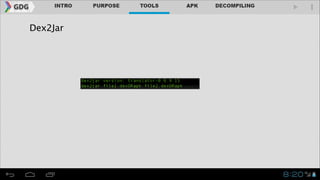
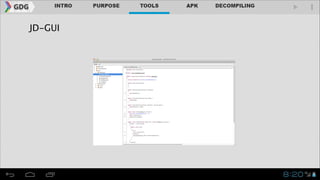
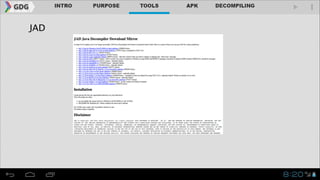
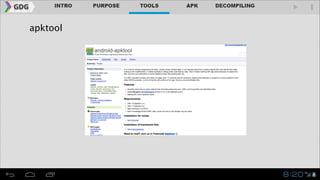
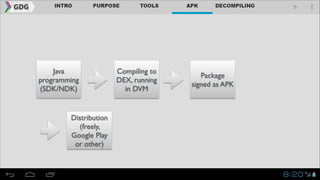
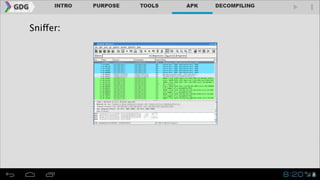
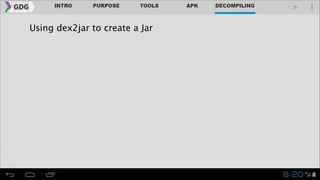
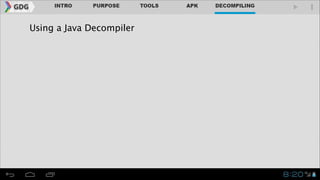
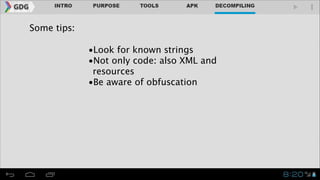
- It introduces tools like Dex2jar, JD-GUI, JAD, and apktool that can be used to decompile APKs into a readable format and manipulate the code.
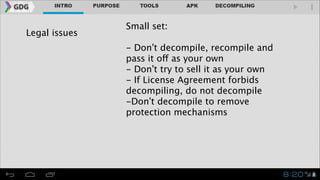
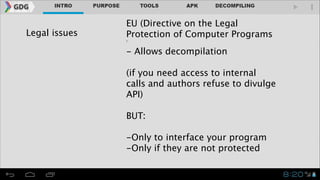
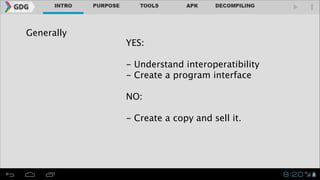
- Legal and ethical considerations around reverse engineering are discussed, noting what is generally allowed like understanding interoperability but not creating copies to sell.
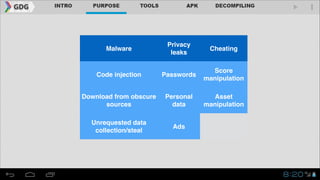
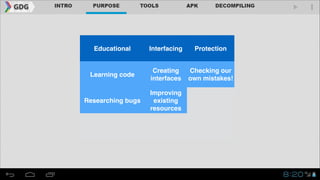
- Examples of educational, protective, and malicious uses of reverse engineering are provided.



![Protecting your source
[We want] to protect [the] code by making
reverse engineering so technically difficult
that it becomes impossible or at the very
least economically inviable.
!
-Christian Collberg,](https://image.slidesharecdn.com/andevconkeynote-131117191739-phpapp02/85/AnDevCon-Android-Reverse-Engineering-32-320.jpg)