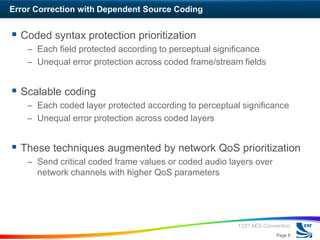
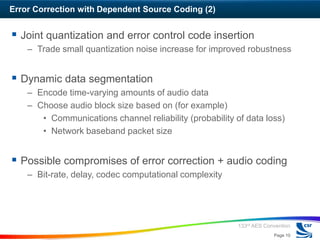
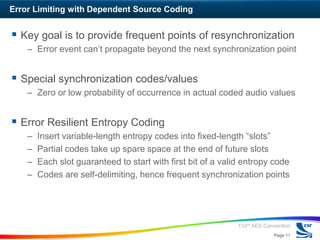
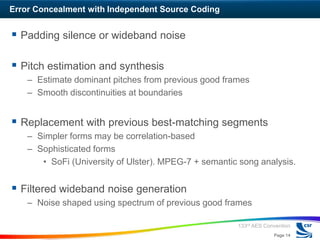
The workshop discussed approaches to error-tolerant audio coding for networked audio. The panelists presented on classification of audio error control strategies including error correction, error limiting, and error concealment. Error correction can be done with independent or dependent source coding. Dependent source coding prioritizes error protection based on perceptual significance. Error limiting aims to limit error propagation through frequent resynchronization points. Error concealment techniques try to reduce the perceptual impact of errors.