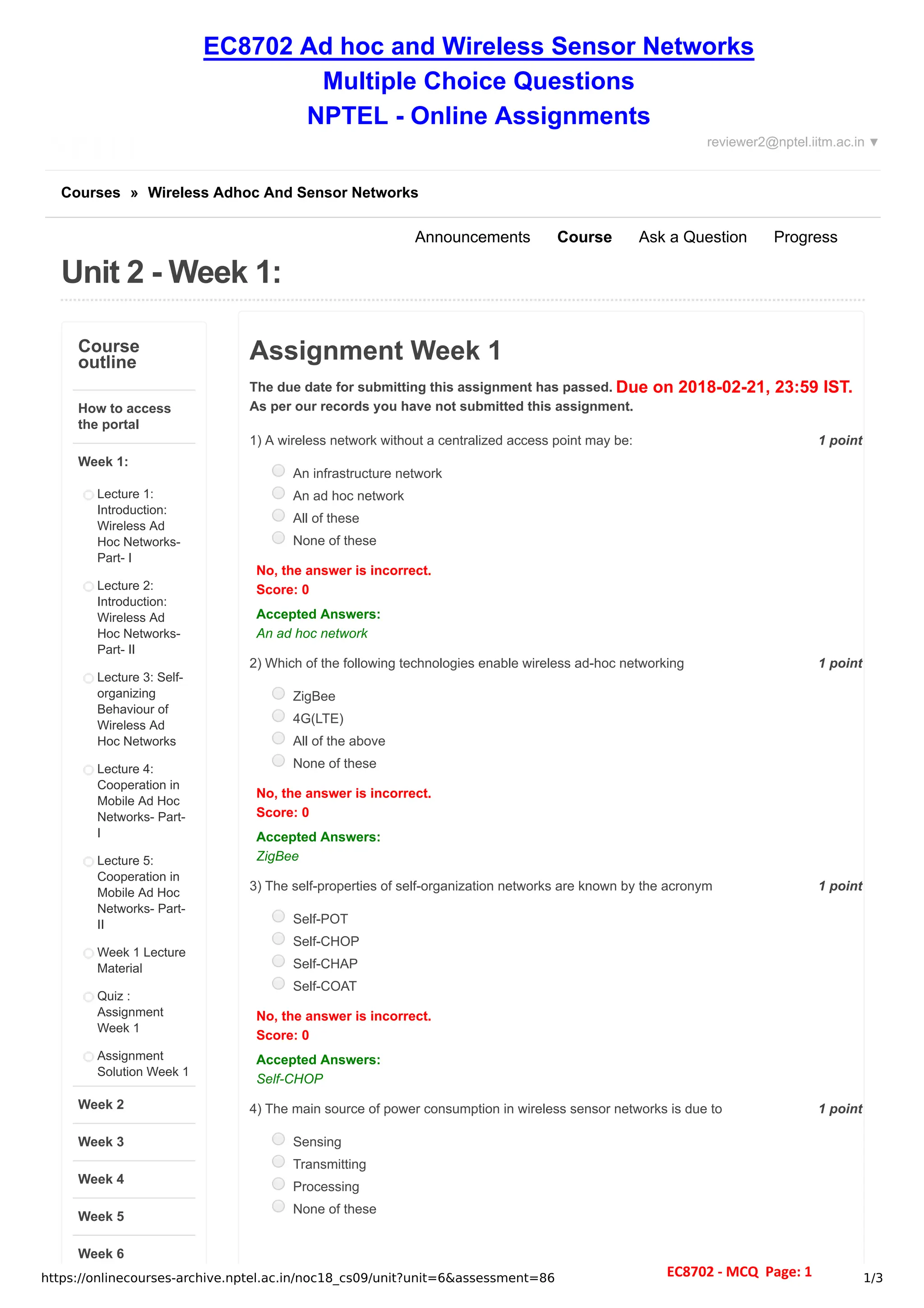
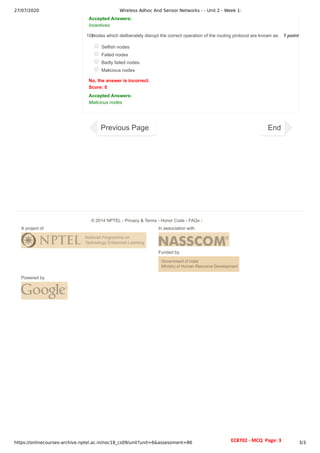
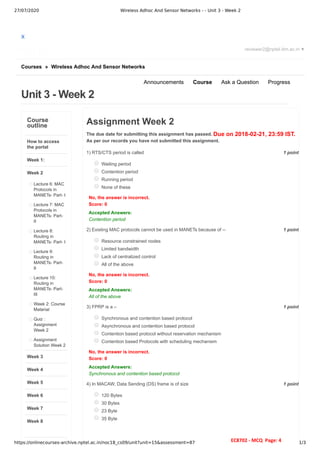
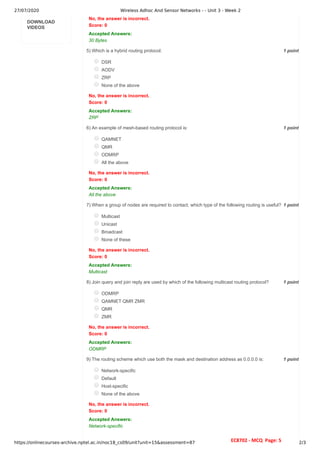
The document details the course structure and assessments for a wireless ad hoc and sensor networks course, highlighting lectures and assignments across several weeks. It includes quizzes and multiple choice questions covering topics like self-organizing behavior, MAC protocols, and routing in MANETs. The document also contains student assessment records, indicating unsubmitted assignments and incorrect answers.