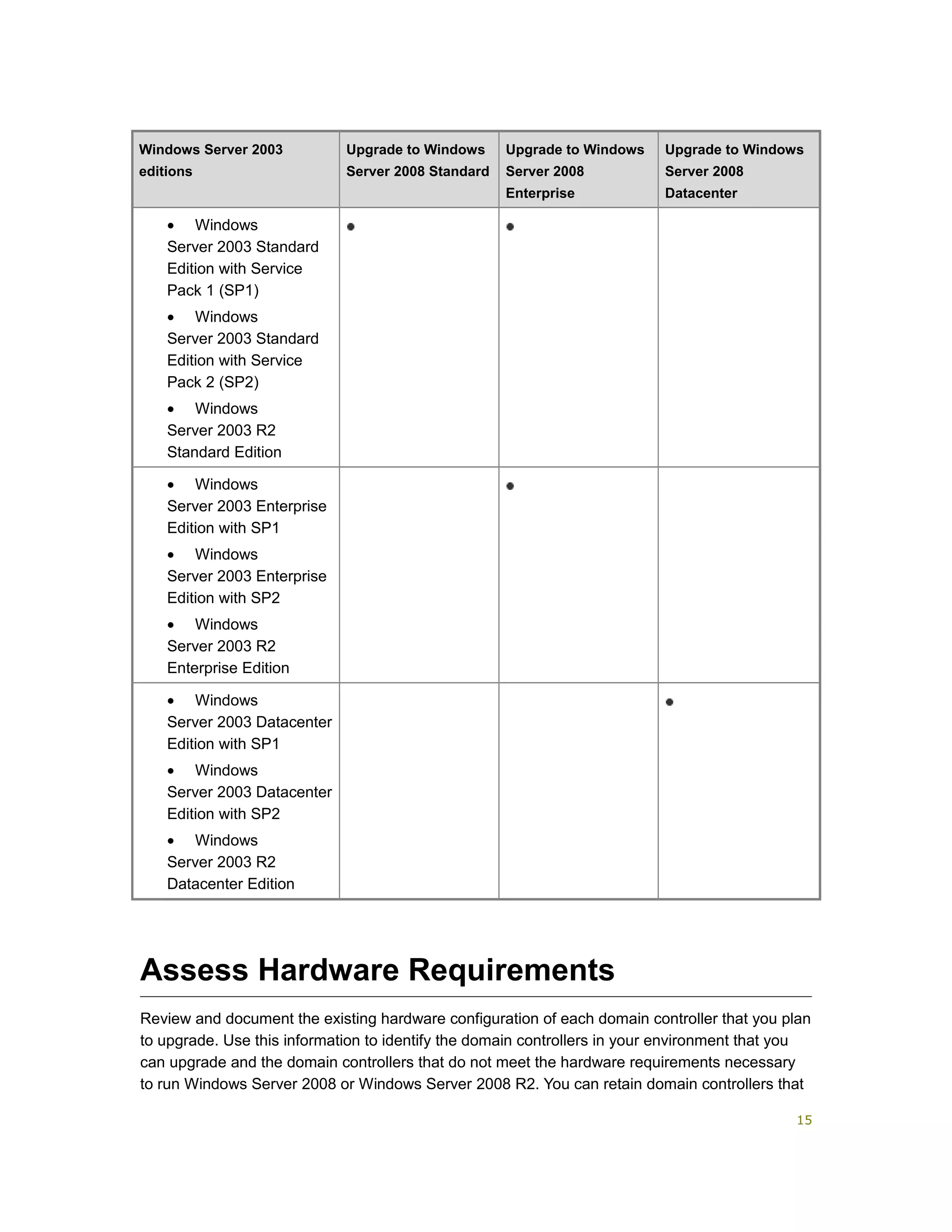
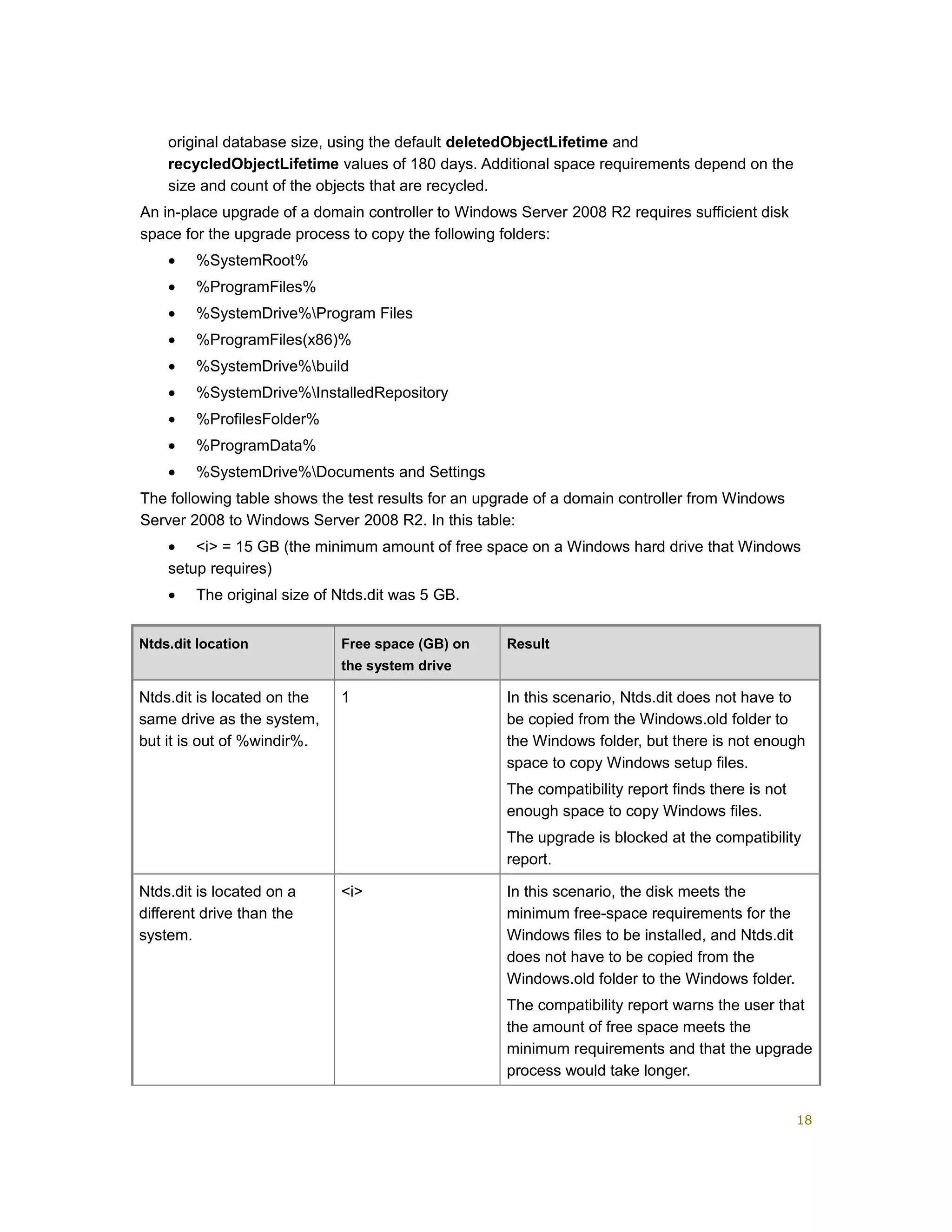
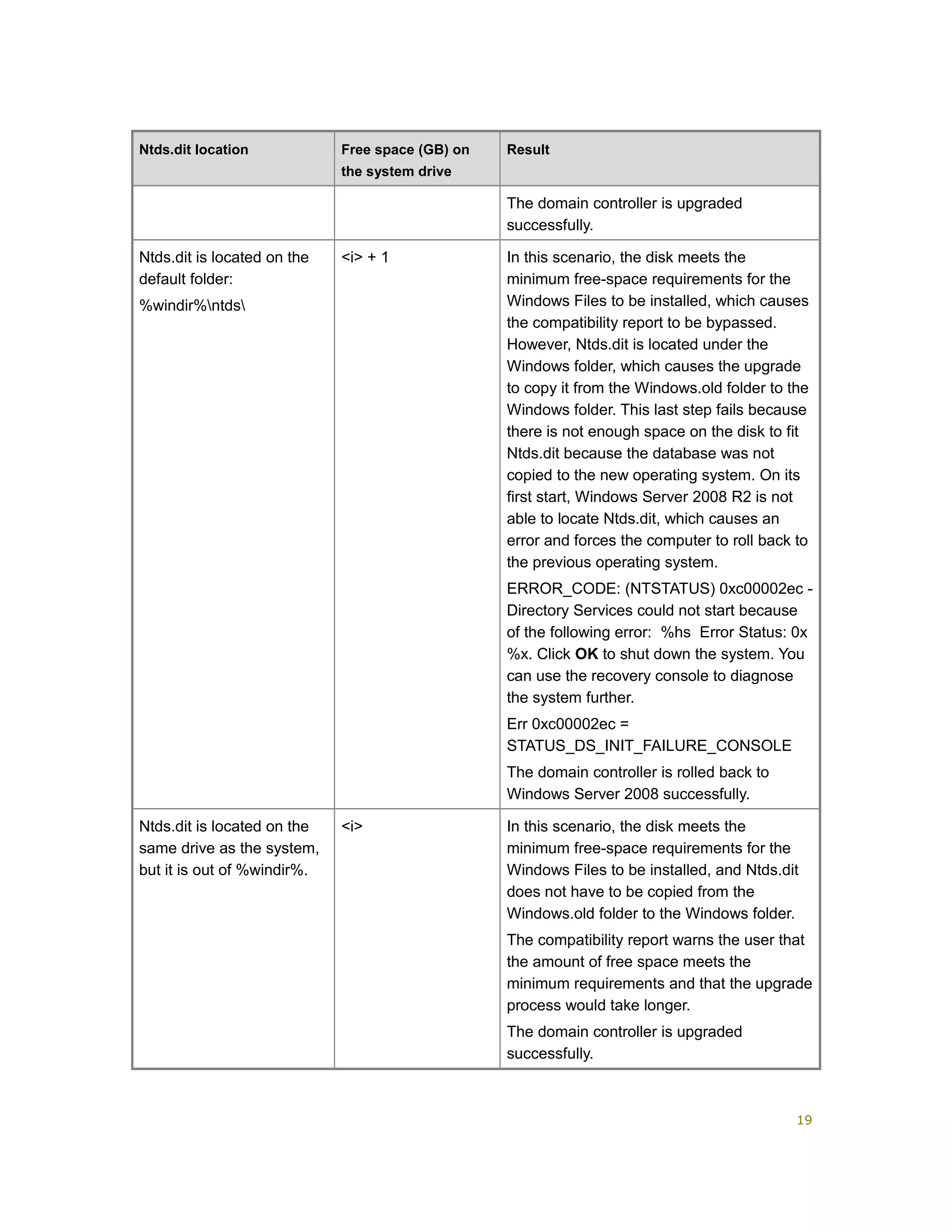
The document provides guidance for upgrading Active Directory domains to Windows Server 2008 or Windows Server 2008 R2. It outlines key planning tasks such as assigning credentials, introducing a test server, determining supported upgrades, assessing hardware requirements, and developing a test plan. Detailed instructions are given for performing tasks like installing AD DS on a test server, upgrading domain controllers, and completing post-upgrade configuration. Background information and references are also included to aid in the planning and execution of the domain upgrade process.





![Upgrading Active Directory Domains to
Windows Server 2008 and Windows Server
2008 R2 AD DS Domains
Upgrading your network operating system requires minimal network configuration and typically
has a low impact on user operations. The upgrade process is straightforward, efficient, and allows
your organization to take advantage of the improved security that is offered by the
Windows Server® 2008 and Windows Server 2008 R2 operating systems.
About this guide
This guide is intended for use by system administrators and system engineers. It provides
detailed guidance for upgrading Windows 2000 or Windows Server 2003 Active Directory
domains to Active Directory Domain Services (AD DS) domains that have domain controllers
running Windows Server 2008 or Windows Server 2008 R2. For a seamless deployment
experience, use the checklists that are provided in this guide and complete the tasks in the order
in which they are presented.
In this guide
• Overview of Upgrading Active Directory Domains
• Planning to Upgrade Active Directory Domains
• Performing the Upgrade of Active Directory Domains
• Completing the Upgrade of Active Directory Domains
• Finding Additional Information About Upgrading Active Directory Domains
• Appendix A: Background Information for Upgrading Active Directory Domains
• Microsoft Support Quick Start for Adding Windows Server 2008 or Windows Server 2008
R2 Domain Controllers to Existing Domains
Related information
• For more information about the AD DS logical structure and the Domain Name System
(DNS) infrastructure that is necessary to support AD DS, see Designing the Logical
Structure for Windows Server 2008 AD DS [LH].
• For more information about AD DS functional levels, see Enabling Advanced Features
for AD DS.
• For more information about installing and configuring a DNS server, see Deploying
Domain Name System (DNS) (http://go.microsoft.com/fwlink/?LinkId=93656).
7](https://image.slidesharecdn.com/addsdomainupgrade-140701101517-phpapp02/75/Adds-domain-upgrade-6-2048.jpg)









![click Administrative Tools, and then click DNS to open the DNS Manager.
2. Right-click the DNS zone that uses the fully qualified domain name (FQDN) of the
Active Directory domain, and then click Properties.
3. Click the Change button next to Replication: All DNS servers in this domain.
4. Click To all DNS servers in this domain:<domain_name>, and then click OK.
Membership in Domain Admins or Enterprise Admins, or equivalent, is the minimum required
to complete this procedure. Review details about using the appropriate accounts and group
memberships at http://go.microsoft.com/fwlink/?LinkId=83477.
1. On a domain controller that hosts a DNS server in the forest root domain, click Start,
click Administrative Tools, and then click DNS to open DNS Manager.
2. Right-click the _msdcs.<forest_root_domain> DNS zone, and then click Properties.
3. Click the Change button next to Replication: All DNS servers in this forest.
4. Click To all DNS servers in this forest:<forest_name>, and then click OK.
For more information, see Deploying Domain Name System (DNS)
(http://go.microsoft.com/fwlink/?LinkId=93656).
Redirect Users and Computers
The procedures in this topic are required only if you are upgrading Windows 2000
Active Directory domains. A Windows Server 2003 Active Directory domain organizational
unit (OU) structure will remain the same after the upgrade is complete.
The default CN=Users and CN=Computers containers that are created when AD DS is installed
are not OUs. Objects in the default containers are more difficult to manage because Group Policy
cannot be applied directly to them. New user accounts, computer accounts, and security groups
that are created by using earlier versions of user interface (UI) and command-line management
tools do not allow administrators to specify a target OU. For this reason, administrators are not
allowed to create these objects in either the CN=Computers container or the CN=User container,
by default. Examples of these earlier versions include the net user and net computer
commands, the net group command, or the netdom add command where the /ou parameter is
either not specified or not supported.
We recommend that administrators who upgrade Windows 2000–based domain controllers
redirect the well-known path for the CN=Users and CN=Computers containers to an OU that is
specified by the administrator so that Group Policy can be applied to containers hosting newly
created objects. For more information about creating an OU design, see Designing the Logical
Structure for Windows Server 2008 AD DS [LH].
To change the replication scope of the _msdcs.forest_root_domain DNS zone by using
a DNS application directory partition
Note
43](https://image.slidesharecdn.com/addsdomainupgrade-140701101517-phpapp02/75/Adds-domain-upgrade-42-2048.jpg)


![• For a worksheet to assist you in documenting your domain controller information, see Job
Aids for Windows Server 2003 Deployment Kit (http://go.microsoft.com/fwlink/?
LinkID=102558). Download
Job_Aids_Planning_Testing_and_Piloting_Deployment_Projects.zip and open
DSSUPWN_2.doc.
• For more information about deploying Distributed File System (DFS), see Designing and
Deploying File Servers (http://go.microsoft.com/fwlink/?LinkID=27928).
• For more information about configuring optional registry parameters for the Boot
Information Negotiation Layer (BINL) service, see article 235979 in the Microsoft Knowledge
Base (http://go.microsoft.com/fwlink/?LinkID=106488).
• For more information about Windows 2000 administration tools and upgrade issues, see
article 304718 in the Microsoft Knowledge Base (http://go.microsoft.com/fwlink/?
LinkId=106490).
• For more information about read-only domain controllers (RODCs), see Read-Only
Domain Controller Planning and Deployment Guide (http://go.microsoft.com/fwlink/?
LinkId=135993).
• For more information about Windows Services for UNIX 2.0 application compatibility
issues and the hotfix installation file, see article 293783 in the Microsoft Knowledge Base
(http://go.microsoft.com/fwlink/?LinkID=106317).
• For information about installing AD DS by using a command line or an answer file, see
Installing a New Forest (http://go.microsoft.com/fwlink/?LinkId=101704).
• For more information, see Effects of netlogon cryptographic support changes in Windows
Server 2008 (http://go.microsoft.com/fwlink/?LinkId=164558).
• For more information, see Compact the directory database file (offline defragmentation)
(http://go.microsoft.com/fwlink/?LinkID=106343).
• For more information about backing up AD DS, see the AD DS Backup and Recovery
Step-by-Step Guide (http://go.microsoft.com/fwlink/?LinkID=93077).
• For more information about DNS, see Deploying Domain Name System (DNS)
(http://go.microsoft.com/fwlink/?LinkId=93656).
• For more information about creating an organizational unit (OU) design, see Designing
the Logical Structure for Windows Server 2008 AD DS [LH].
Appendix A: Background Information for
Upgrading Active Directory Domains
Before you begin the process of upgrading your Windows 2000 or Windows Server 2003
Active Directory environment to Active Directory Domain Services (AD DS), become familiar with
some important issues that affect the upgrade process.
46](https://image.slidesharecdn.com/addsdomainupgrade-140701101517-phpapp02/75/Adds-domain-upgrade-45-2048.jpg)











![Server 2008 SP2
If you use devolution to
resolve DNS names
(instead of suffix search
list), apply the DNS
devolution hotfix.
957579 (http://go.microsoft.com/fwlink/?
LinkId=178224)
Windows
Server 2008 SP2
Group Policy Preferences
rerelease
943729 (http://go.microsoft.com/fwlink/?
LinkId=164591)
974266 (http://go.microsoft.com/fwlink/?
LinkID=165035)
Windows
Server 2008 SP2
Synchronize the Directory
Services Restore Mode
(DSRM) Administrator
password with a domain
user account
961320 (http://go.microsoft.com/fwlink/?
LinkId=177814)
The following table lists hotfixes for Windows Server 2008 R2.
Description Microsoft Knowledge Base article Comment
Windows
Server 2008 R2
Dynamic DNS updates
to BIND servers log
NETLOGON event 5774
with error status 9502
2002490 (http://go.microsoft.com/fwlink/?
LinkId=178225)
[The article will
include a hotfix.]
Event ID 1202 logged
with status 0x534 if
security policy modified
2000705 (http://go.microsoft.com/fwlink/?
LinkId=165961)
Hotfix is in
progress. Also
scheduled for
Windows
Server 2008 R2
SP1.
TimeZoneKeyName
registry entry name is
corrupt on 64-bit
upgrades
2001086 (http://go.microsoft.com/fwlink/?
LinkId=178226)
Occurs only on x64-
based server
upgrades in
Dynamic DST time
zones. To see if
your servers are
affected, click the
taskbar clock. If the
clock fly-out
indicates a time
64](https://image.slidesharecdn.com/addsdomainupgrade-140701101517-phpapp02/75/Adds-domain-upgrade-63-2048.jpg)



![For Windows Server 2008 R2:
If the infrastructure master is 64-bit, use the following syntax:
D:supportadprepadprep /domainprep /gpprep
If the infrastructure master is 32-bit, use the following syntax:
D:supportadprepadprep32 /domainprep /gpprep
If you encounter errors, see “Domainprep errors” later in this topic
Upgrade domain controllers
This section includes the following topics:
• Background information about the in-place upgrade process
• Upgrading and promoting new domain controllers into an existing domain
• Post-installation tasks
• Fixes to install after AD DS installation
Background information about the in-place upgrade process
When you upgrade existing domain controllers or promote new domain controllers into existing
domains, consider the following:
Computers running Windows 2000 Server cannot be upgraded in place to Windows Server 2008
or Windows Server 2008 R2.
In-place upgrades from Windows Server 2003 or Windows Server 2003 R2 to Windows
Server 2008 or Windows Server 2008 R2 are supported, with the following exception: x86-
based operating systems cannot be upgraded in place to x64-based versions of Windows
Server 2008 or Windows Server 2008 R2 (which supports only the x64-based architecture).
A writeable domain controller cannot be upgraded to be an RODC. The reverse is also true.
A server that runs the full installation of Windows Server 2008 R2 cannot be upgraded to be a
server that runs a Server Core installation of Windows Server 2008 R2. The reverse is also
true.
For more information about supported and unsupported upgrades, see Windows Server 2008 R2
Upgrade Paths (http://go.microsoft.com/fwlink/?LinkID=154894).
Windows Server 2008 and Windows Server 2008 R2 both auto-install Internet Protocol version 6
(IPv6). Do not arbitrarily disable or remove IPv6.
To promote RODCs:
• The adprep[32] /rodcprep command must have completed successfully.
• The forest functional level must be Windows Server 2003 or higher.
• A writable (or “full”) domain controller that runs Windows Server 2008 or Windows
Server 2008 R2 must exist in the target domain.
68](https://image.slidesharecdn.com/addsdomainupgrade-140701101517-phpapp02/75/Adds-domain-upgrade-67-2048.jpg)