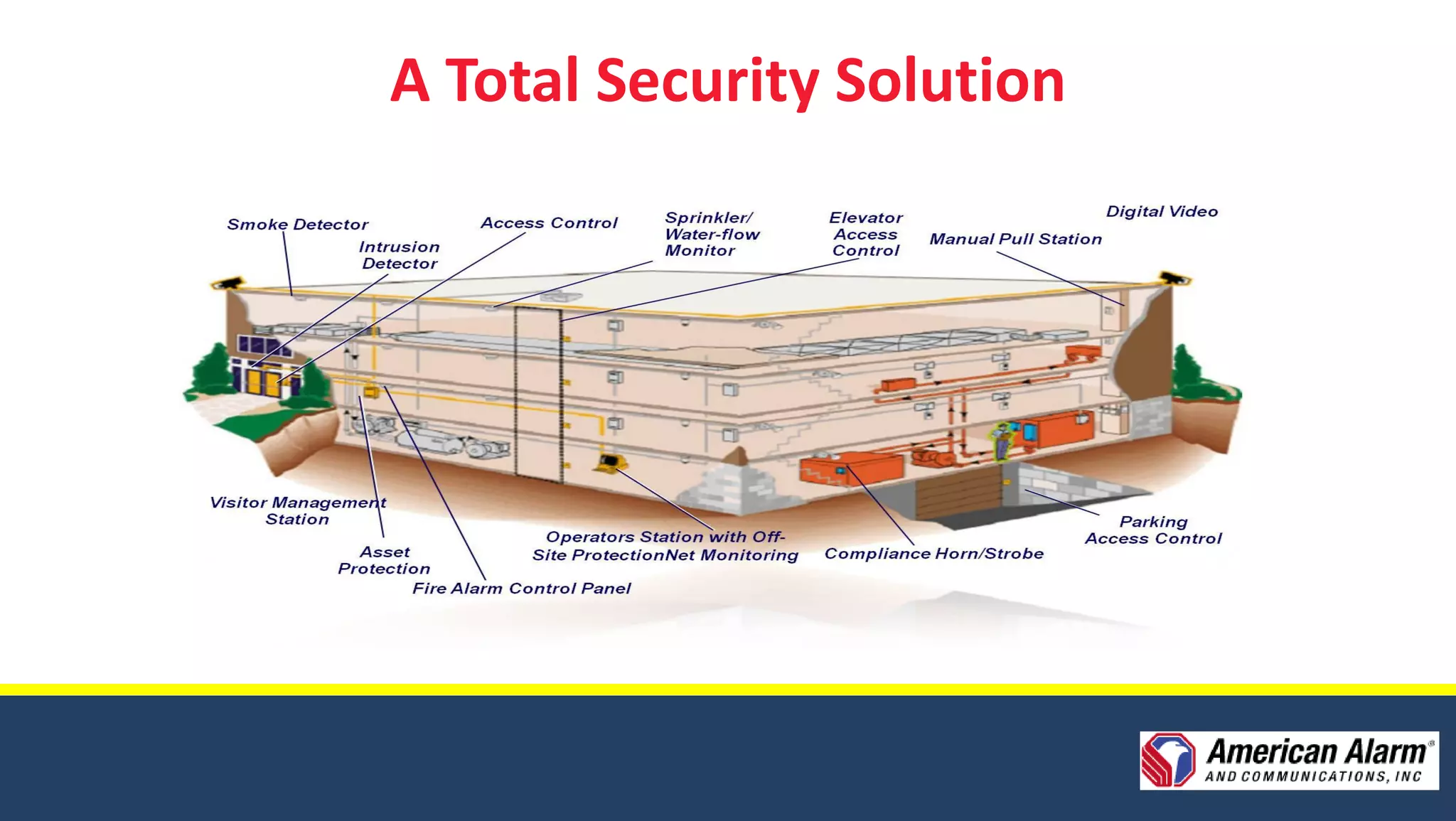
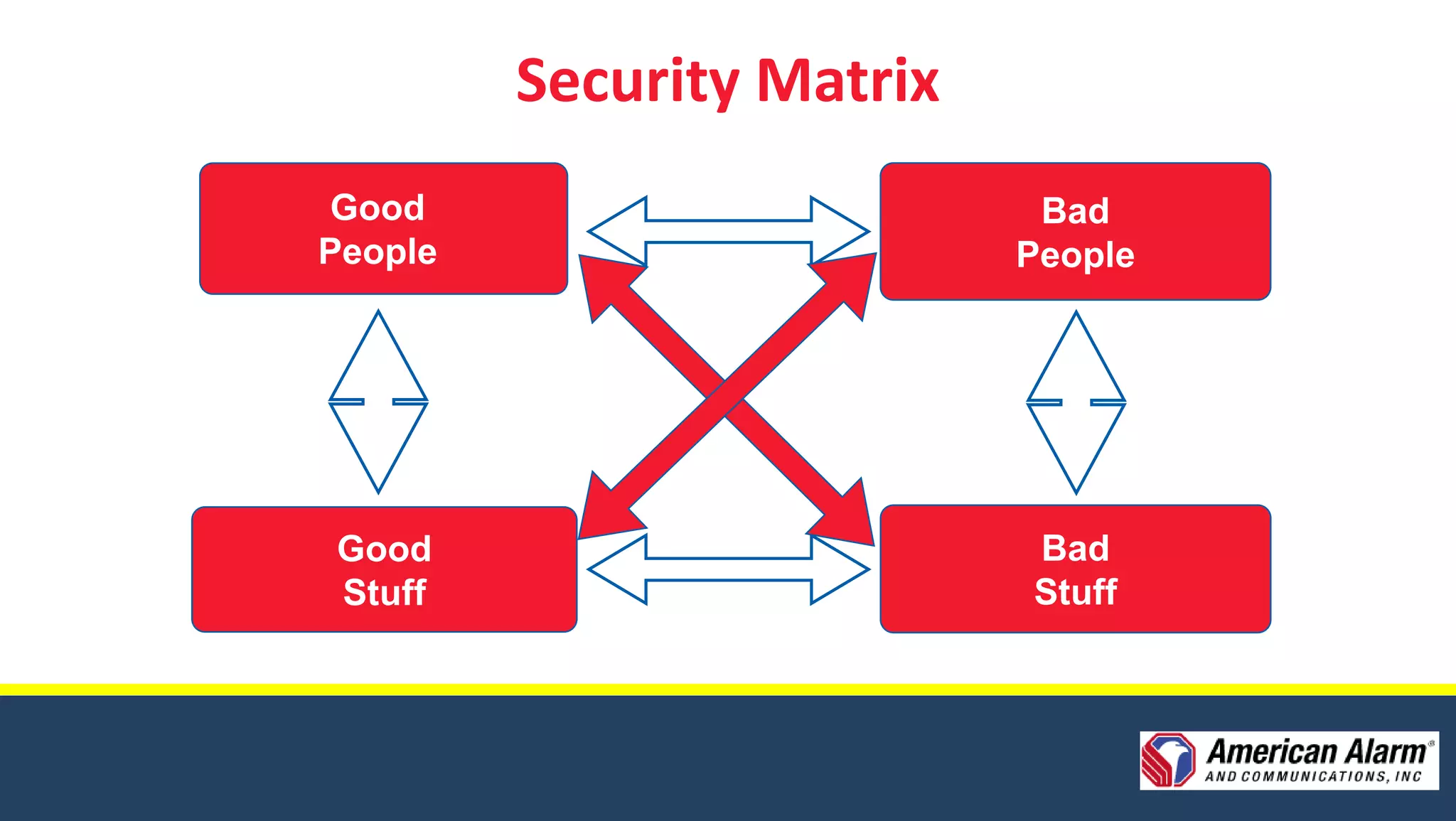
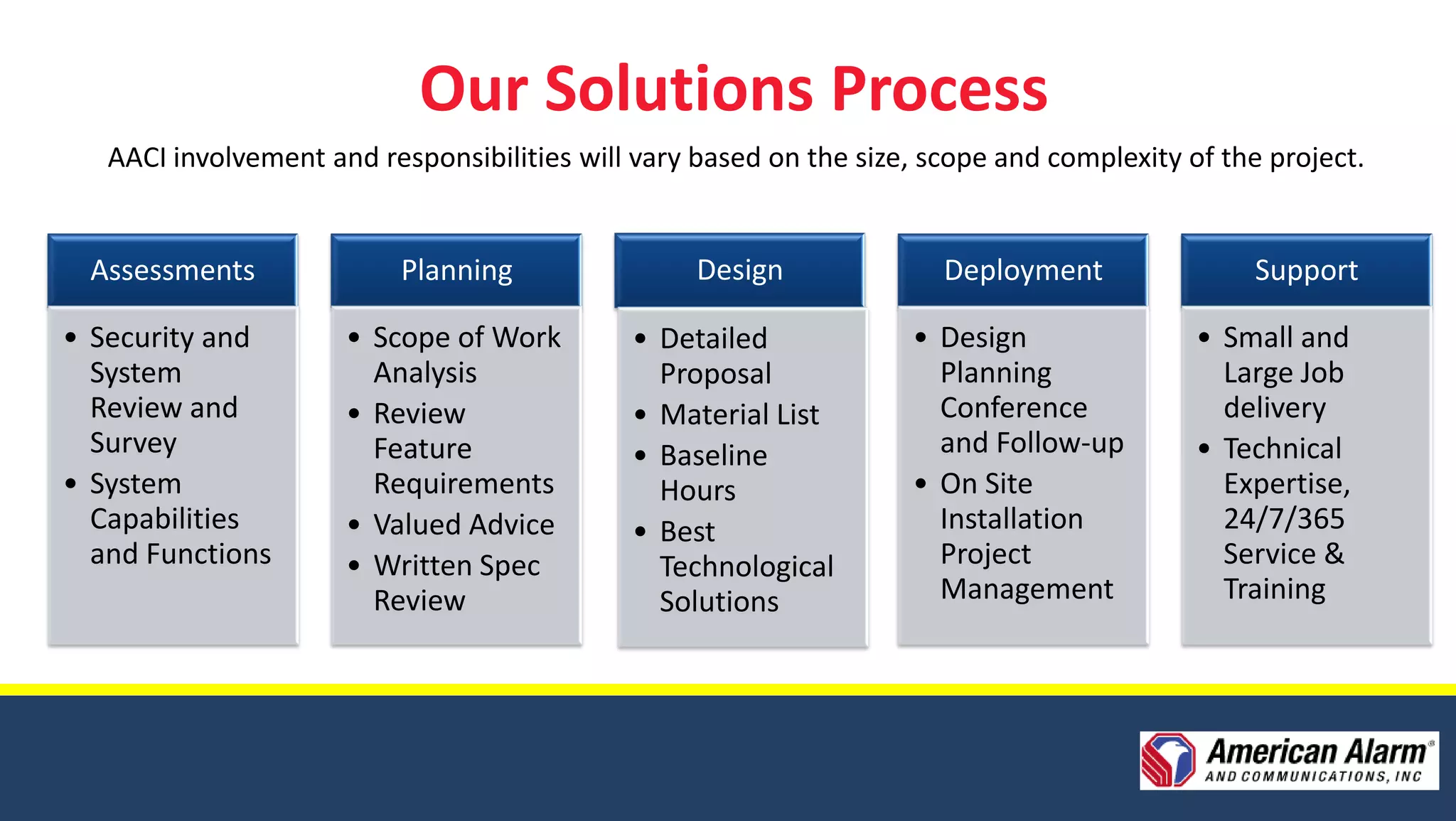
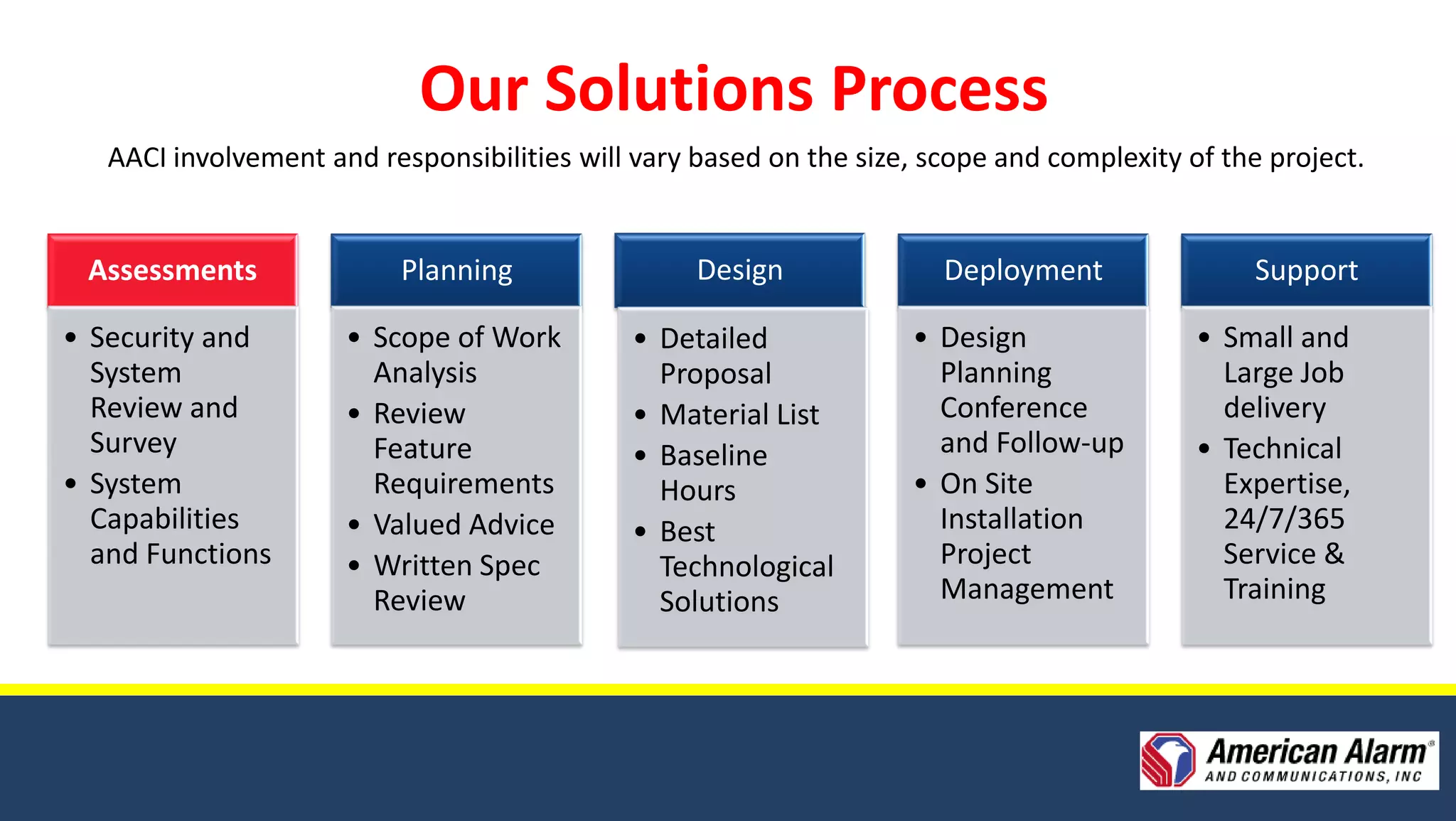
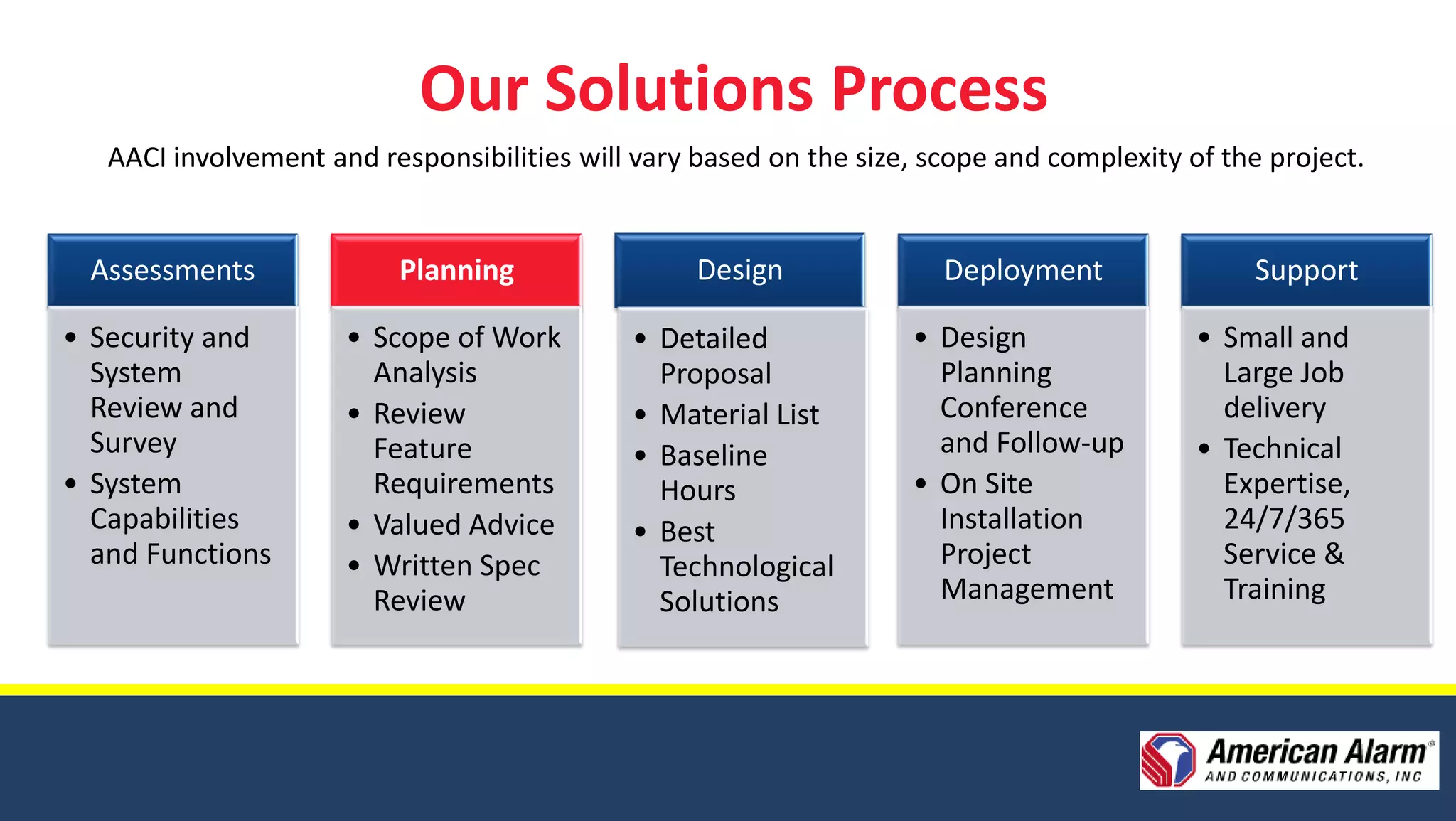
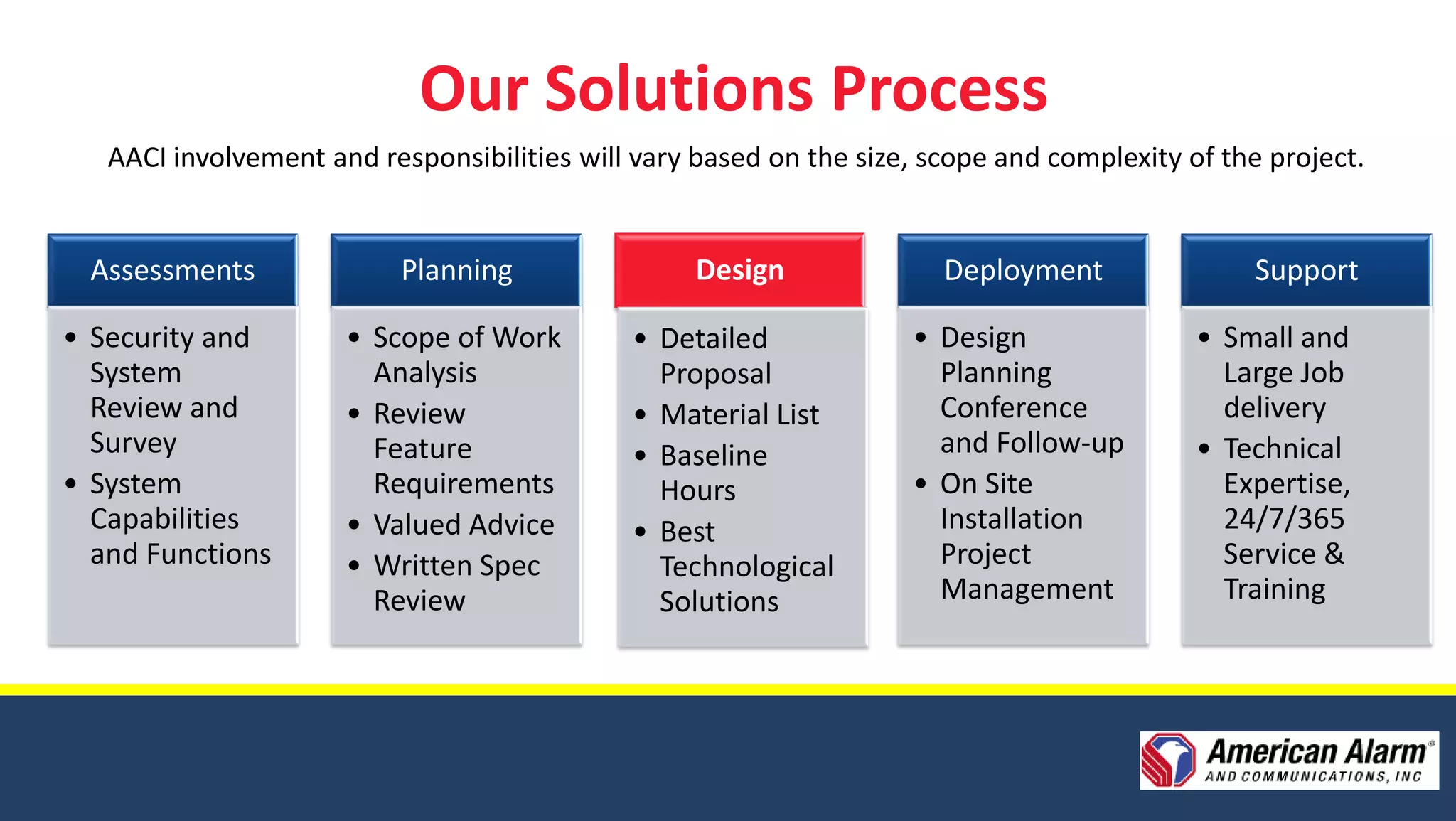
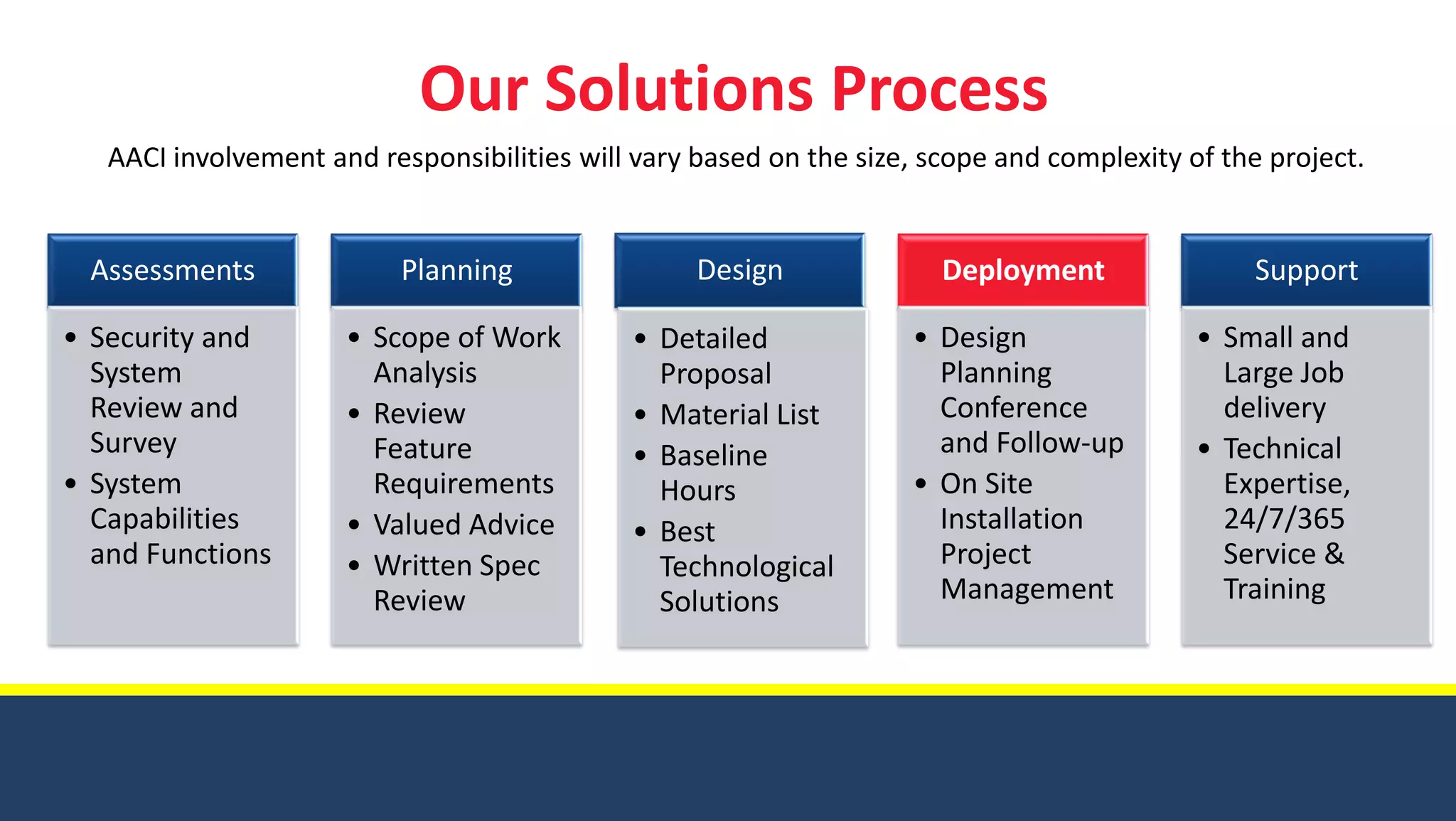
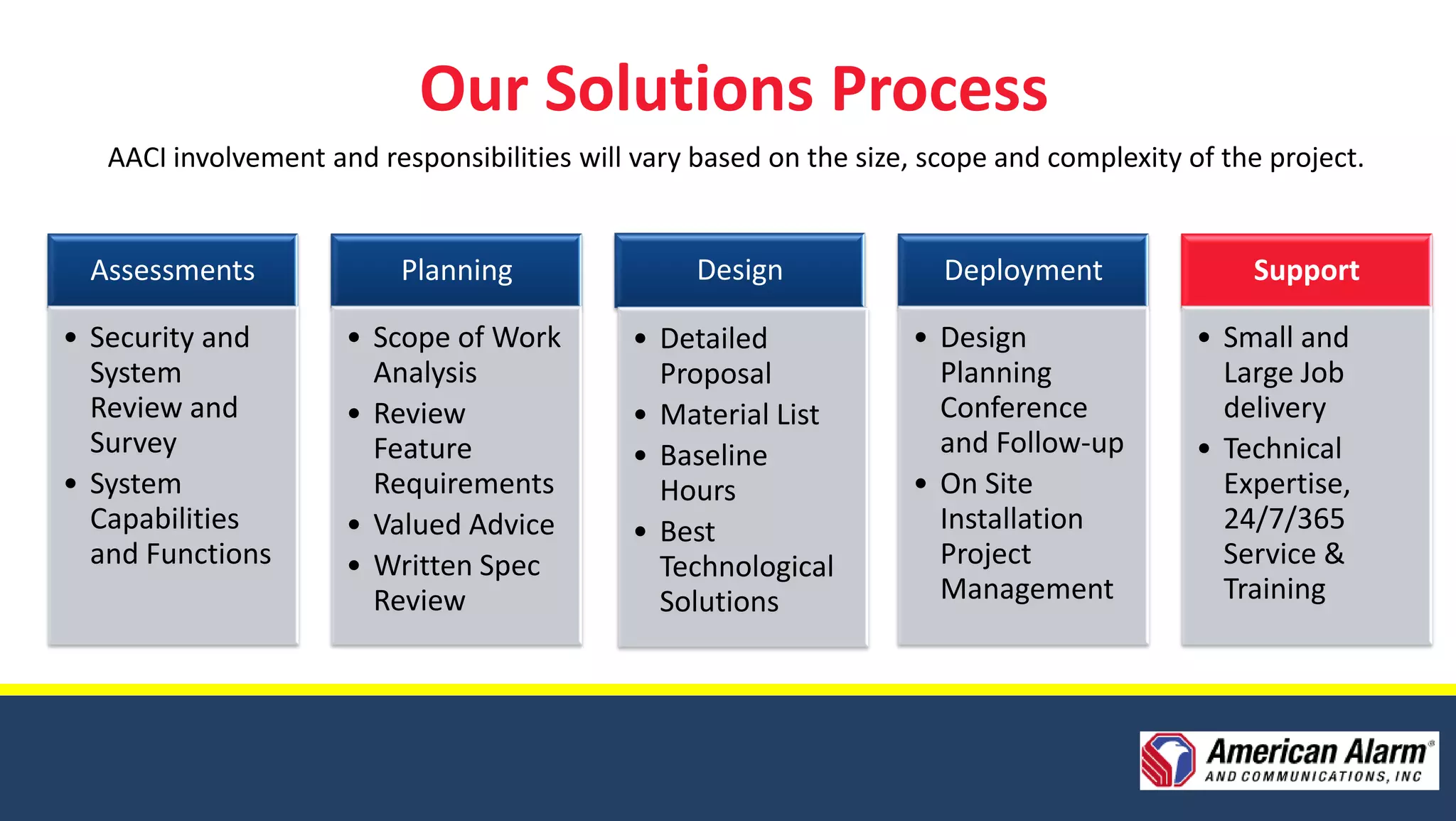
American Alarm & Communications provides security technology solutions and services. It was founded in 1971 by three MIT engineers with a focus on innovation, excellence, and customer service. Today it works to provide the best security solutions for customers through assessment, planning, design, deployment, monitoring, support and training. It has over 40 years of experience in security and was ranked the top security firm in Boston and 40th nationally in 2010. It offers comprehensive security solutions including access control, video surveillance, intrusion detection, and emergency communications. The company uses a process including assessments, planning, design, deployment and long-term support to fully meet customer security needs.