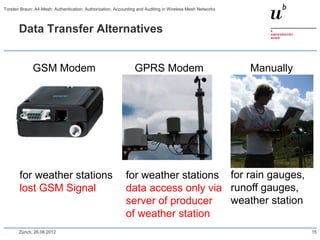
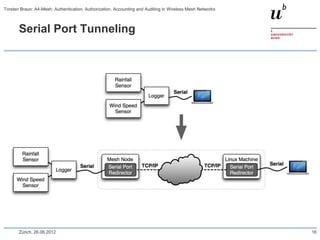
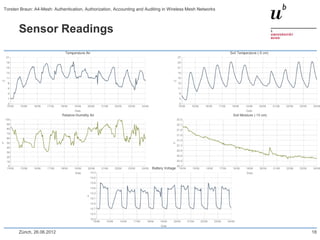
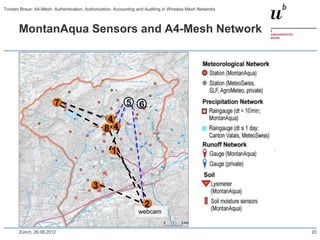
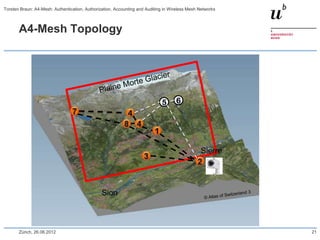
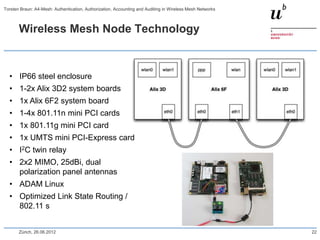
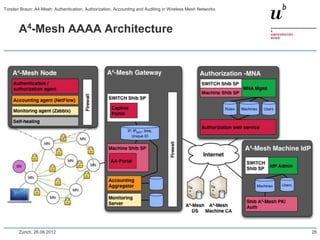
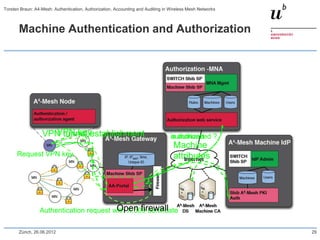
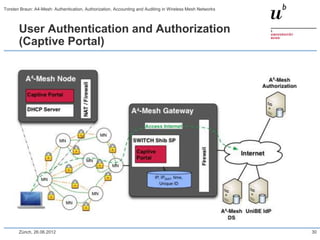
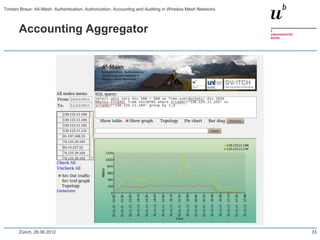
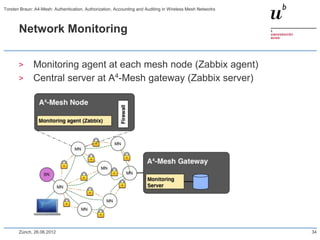
The document discusses the A4-Mesh project which aims to provide broadband network access to researchers in remote locations using a wireless mesh network. The project implements authentication, authorization, accounting, and auditing (AAAA) to secure access for wireless mesh nodes and users. A pilot network is deployed in the MontanAqua environmental monitoring application to provide scientists real-time sensor data access. The network uses SWITCHaai for user authentication and develops mechanisms for wireless mesh node authentication and integration. Traffic and network monitoring are implemented for accounting and auditing of mesh nodes and users.