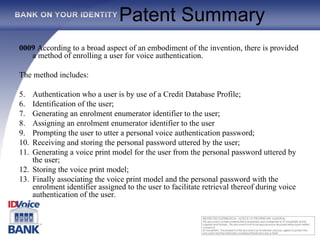
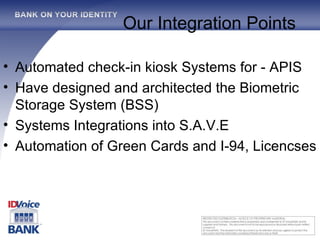
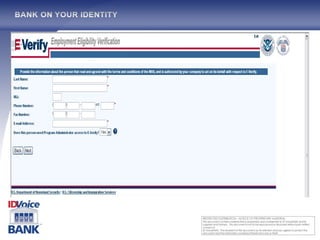
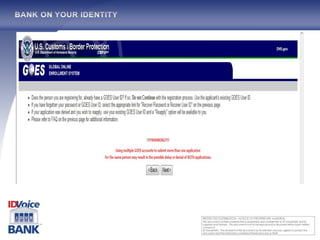
The document outlines the One Voice TM technology, which encompasses a patented real-time biometric voice identity management system capable of automating authentication processes through voice recognition. Founded in 2002 and backed by major credit companies, this service aims to facilitate secure and efficient transactions while reducing fraud and identity theft. It highlights the system's ease of use and language independence, targeting diverse markets with its extensive voice identity database and integration capabilities.
















![Zeliha Artan Business Development and Marketing [email_address] 416.995.0074](https://image.slidesharecdn.com/IDVBUSGOVintergrations2-122937203744-phpapp01/85/US-Security-for-Cyber-Security-31-320.jpg)
