8 Convincing Statistics About Insider Threats
•
0 likes•175 views
The insider threat is at large. Take these statistics into consideration when you are developing your information security action plan. Visit https://itsecuritycentral.teramind.co/ for more information on the subject.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (19)
Its 2019 - Should Pharma Still Be Scared of Digital?

Its 2019 - Should Pharma Still Be Scared of Digital?
Best of Both Worlds: Correlating Static and Dynamic Analysis Results

Best of Both Worlds: Correlating Static and Dynamic Analysis Results
Steria Etude sur le Big Data en europe infographic / Septembre 2013

Steria Etude sur le Big Data en europe infographic / Septembre 2013
Where Flow Charts Don’t Go -- Website Security Statistics Report (2015)

Where Flow Charts Don’t Go -- Website Security Statistics Report (2015)
No More Snake Oil: Why InfoSec Needs Security Guarantees

No More Snake Oil: Why InfoSec Needs Security Guarantees
WhiteHat Security 8th Website Security Statistics Report

WhiteHat Security 8th Website Security Statistics Report
Similar to 8 Convincing Statistics About Insider Threats
Internal or insider threats are far more dangerous than the external - bala g...

Internal or insider threats are far more dangerous than the external - bala g...Bala Guntipalli ♦ MBA
Similar to 8 Convincing Statistics About Insider Threats (20)
5 Types of Insider Threats and How to Detect them in Your ERP System

5 Types of Insider Threats and How to Detect them in Your ERP System
5 Traits of Companies Successfully Preventing Fraud and How to Apply Them in ...

5 Traits of Companies Successfully Preventing Fraud and How to Apply Them in ...
Internal or insider threats are far more dangerous than the external - bala g...

Internal or insider threats are far more dangerous than the external - bala g...
We are living in a world where cyber security is a top priority for .pdf

We are living in a world where cyber security is a top priority for .pdf
Secure Wall - how should companies protect themselves from cyber crime?

Secure Wall - how should companies protect themselves from cyber crime?
Verizon 2014 data breach investigation report and the target breach

Verizon 2014 data breach investigation report and the target breach
5 Technology Trends Construction Contractors Can't Afford To Ignore

5 Technology Trends Construction Contractors Can't Afford To Ignore
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Recently uploaded
Recently uploaded (20)
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
8 Convincing Statistics About Insider Threats
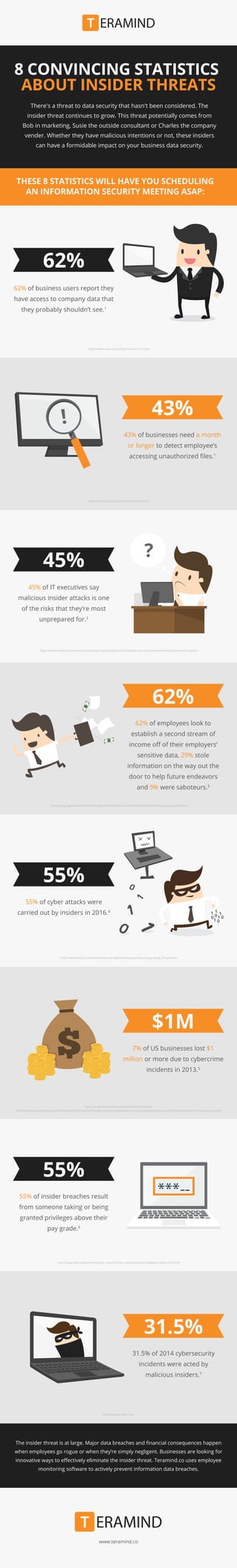
- 1. 8 CONVINCING STATISTICS ABOUT INSIDER THREATS The insider threat is at large. Major data breaches and financial consequences happen when employees go rogue or when they’re simply negligent. Businesses are looking for innovative ways to effectively eliminate the insider threat. Teramind.co uses employee monitoring software to actively prevent information data breaches. www.teramind.co There's a threat to data security that hasn't been considered. The insider threat continues to grow. This threat potentially comes from Bob in marketing, Susie the outside consultant or Charles the company vender. Whether they have malicious intentions or not, these insiders can have a formidable impact on your business data security. THESE 8 STATISTICS WILL HAVE YOU SCHEDULING AN INFORMATION SECURITY MEETING ASAP: 1 https://www.varonis.com/learn/ponemon-2016/ 62% of business users report they have access to company data that they probably shouldn’t see.1 62% 62% of employees look to establish a second stream of income off of their employers’ sensitive data, 29% stole information on the way out the door to help future endeavors and 9% were saboteurs.3 62% 3 http://blogs.gartner.com/anton-chuvakin/2016/05/09/our-understanding-insider-threats-paper-publishes/ 55% of insider breaches result from someone taking or being granted privileges above their pay grade.6 55% https://iapp.org/media/pdf/resource_center/Verizon_data-breach-investigation-report-2015.pdf 7% of US businesses lost $1 million or more due to cybercrime incidents in 2013.5 $1M https://ec.europa.eu/home-affairs/sites/homeaffairs/ files/what-we-do/policies/organized-crime-and-human-trafficking/corruption/experience-sharing-programme/docs/o.iskit-global-economic-crime-survey_en.pdf 45% of IT executives say malicious insider attacks is one of the risks that they’re most unprepared for.2 45% 2 https://www.mimecast.com/resources/analyst-reports/Dates/2016/2/email-security-uncovered-mimecast-research-report/ 55% of cyber attacks were carried out by insiders in 2016.4 55% 4 http://www-05.ibm.com/services/europe/digital-whitepaper/security/growing_threats.html 43% of businesses need a month or longer to detect employee’s accessing unauthorized files.1 43% 1 https://www.varonis.com/learn/ponemon-2016/ 31.5% of 2014 cybersecurity incidents were acted by malicious insiders.7 31.5% http://www-01.ibm.com
