[Infographic] 5 Security Threats in Healthcare Industry
•
0 likes•180 views
Learn about the most pertinent risks that plague the healthcare industry.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
5 Types of Insider Threats and How to Detect them in Your ERP System

5 Types of Insider Threats and How to Detect them in Your ERP System
Cyber Vulnerabilities & How companies can test them

Cyber Vulnerabilities & How companies can test them
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
"Towards Value-Centric Big Data" e-SIDES Workshop - “You’re monitoring my wh...

"Towards Value-Centric Big Data" e-SIDES Workshop - “You’re monitoring my wh...
New Developments in Cybersecurity and Technology for RDOs: Howland

New Developments in Cybersecurity and Technology for RDOs: Howland
How Federal Agencies Can Build a Layered Defense for Privileged Accounts

How Federal Agencies Can Build a Layered Defense for Privileged Accounts
Ransomware in Healthcare: 5 Attacks on Hospitals & Lessons Learned

Ransomware in Healthcare: 5 Attacks on Hospitals & Lessons Learned
Prevent Insider Threats with User Activity Monitoring

Prevent Insider Threats with User Activity Monitoring
Similar to [Infographic] 5 Security Threats in Healthcare Industry
Similar to [Infographic] 5 Security Threats in Healthcare Industry (20)
Systems Thinking on a National Level, Part 2Drew David.docx

Systems Thinking on a National Level, Part 2Drew David.docx
How to secure information systemsSolutionAnswerInformation.pdf

How to secure information systemsSolutionAnswerInformation.pdf
Adjusting Your Security Controls: It’s the New Normal

Adjusting Your Security Controls: It’s the New Normal
Before the Breach: Using threat intelligence to stop attackers in their tracks

Before the Breach: Using threat intelligence to stop attackers in their tracks
Cybersecurity Risks of 3rd Party Cloud-Apps in 2022 Whitepaper by Protected H...

Cybersecurity Risks of 3rd Party Cloud-Apps in 2022 Whitepaper by Protected H...
Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS

Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS
Top 10 Cyber Security Threats and How to Prevent Them

Top 10 Cyber Security Threats and How to Prevent Them
More from Seqrite
More from Seqrite (10)
Cybersecurity Myths for Small and Medium-Sized Businesses

Cybersecurity Myths for Small and Medium-Sized Businesses
UTM & Next-Gen Firewall Solution: What's the difference?

UTM & Next-Gen Firewall Solution: What's the difference?
Unified Threat Management Vs Next-Gen Firewall: What's the difference?

Unified Threat Management Vs Next-Gen Firewall: What's the difference?
[Infographic] How ransomware gets into your system![[Infographic] How ransomware gets into your system](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] How ransomware gets into your system](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] How ransomware gets into your system
[Infographic] 7 Cyber attacks that shook the world![[Infographic] 7 Cyber attacks that shook the world](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 7 Cyber attacks that shook the world](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 7 Cyber attacks that shook the world
Recently uploaded
indian Call Girl Panchkula ❤️🍑 9907093804 Low Rate Call Girls Ludhiana Tulsi

indian Call Girl Panchkula ❤️🍑 9907093804 Low Rate Call Girls Ludhiana TulsiHigh Profile Call Girls Chandigarh Aarushi
No Advance 9053900678 Chandigarh Call Girls , Indian Call Girls For Full Ni...

No Advance 9053900678 Chandigarh Call Girls , Indian Call Girls For Full Ni...Vip call girls In Chandigarh
VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow

VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service LucknowCall Girls Lucknow Aaradhya Independent Escort Service Lucknow
Call Girl Guwahati Aashi 👉 7001305949 👈 🔝 Independent Escort Service Guwahati

Call Girl Guwahati Aashi 👉 7001305949 👈 🔝 Independent Escort Service GuwahatiCall Girls Lucknow Aaradhya Independent Escort Service Lucknow
Jalandhar Female Call Girls Contact Number 9053900678 💚Jalandhar Female Call...

Jalandhar Female Call Girls Contact Number 9053900678 💚Jalandhar Female Call...Call Girls Service Chandigarh Ayushi
Call Girl Dehradun Aashi 🔝 7001305949 🔝 💃 Independent Escort Service Dehradun

Call Girl Dehradun Aashi 🔝 7001305949 🔝 💃 Independent Escort Service DehradunCall Girls Lucknow Aaradhya Independent Escort Service Lucknow
Call Girls Service Chandigarh Grishma ❤️🍑 9907093804 👄🫦 Independent Escort Se...

Call Girls Service Chandigarh Grishma ❤️🍑 9907093804 👄🫦 Independent Escort Se...High Profile Call Girls Chandigarh Aarushi
Recently uploaded (20)
Call Girl Raipur 9873940964 Book Hot And Sexy Girls

Call Girl Raipur 9873940964 Book Hot And Sexy Girls
indian Call Girl Panchkula ❤️🍑 9907093804 Low Rate Call Girls Ludhiana Tulsi

indian Call Girl Panchkula ❤️🍑 9907093804 Low Rate Call Girls Ludhiana Tulsi
pOOJA sexy Call Girls In Sector 49,9999965857 Young Female Escorts Service In...

pOOJA sexy Call Girls In Sector 49,9999965857 Young Female Escorts Service In...
No Advance 9053900678 Chandigarh Call Girls , Indian Call Girls For Full Ni...

No Advance 9053900678 Chandigarh Call Girls , Indian Call Girls For Full Ni...
Call Girls Service Chandigarh Gori WhatsApp ❤9115573837 VIP Call Girls Chandi...

Call Girls Service Chandigarh Gori WhatsApp ❤9115573837 VIP Call Girls Chandi...
Russian Call Girls in Hyderabad Ishita 9907093804 Independent Escort Service ...

Russian Call Girls in Hyderabad Ishita 9907093804 Independent Escort Service ...
VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow

VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow
hyderabad call girl.pdfRussian Call Girls in Hyderabad Amrita 9907093804 Inde...

hyderabad call girl.pdfRussian Call Girls in Hyderabad Amrita 9907093804 Inde...
Call Girl Guwahati Aashi 👉 7001305949 👈 🔝 Independent Escort Service Guwahati

Call Girl Guwahati Aashi 👉 7001305949 👈 🔝 Independent Escort Service Guwahati
Dehradun Call Girls Service ❤️🍑 9675010100 👄🫦Independent Escort Service Dehradun

Dehradun Call Girls Service ❤️🍑 9675010100 👄🫦Independent Escort Service Dehradun
Call Girls LB Nagar 7001305949 all area service COD available Any Time

Call Girls LB Nagar 7001305949 all area service COD available Any Time
Jalandhar Female Call Girls Contact Number 9053900678 💚Jalandhar Female Call...

Jalandhar Female Call Girls Contact Number 9053900678 💚Jalandhar Female Call...
Call Girls Secunderabad 7001305949 all area service COD available Any Time

Call Girls Secunderabad 7001305949 all area service COD available Any Time
Call Girl Dehradun Aashi 🔝 7001305949 🔝 💃 Independent Escort Service Dehradun

Call Girl Dehradun Aashi 🔝 7001305949 🔝 💃 Independent Escort Service Dehradun
Call Girls Service Chandigarh Grishma ❤️🍑 9907093804 👄🫦 Independent Escort Se...

Call Girls Service Chandigarh Grishma ❤️🍑 9907093804 👄🫦 Independent Escort Se...
Gurgaon iffco chowk 🔝 Call Girls Service 🔝 ( 8264348440 ) unlimited hard sex ...

Gurgaon iffco chowk 🔝 Call Girls Service 🔝 ( 8264348440 ) unlimited hard sex ...
Vip Kolkata Call Girls Cossipore 👉 8250192130 ❣️💯 Available With Room 24×7

Vip Kolkata Call Girls Cossipore 👉 8250192130 ❣️💯 Available With Room 24×7
Russian Escorts Aishbagh Road * 9548273370 Naughty Call Girls Service in Lucknow

Russian Escorts Aishbagh Road * 9548273370 Naughty Call Girls Service in Lucknow
Russian Call Girls in Raipur 9873940964 Book Hot And Sexy Girls

Russian Call Girls in Raipur 9873940964 Book Hot And Sexy Girls
[Infographic] 5 Security Threats in Healthcare Industry
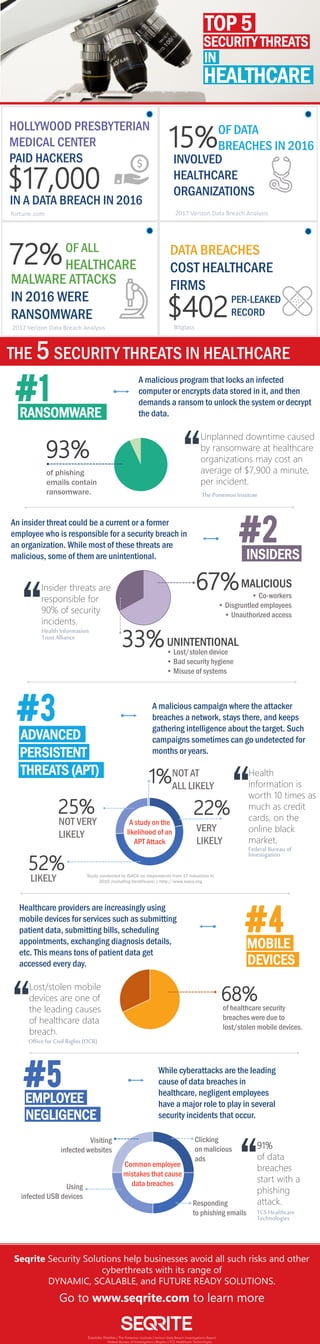
- 1. TOP 5 IN SECURITY THREATS HEALTHCARE IN A DATA BREACH IN 2016 $17,000 OF DATA BREACHES IN 2016 OF ALL HEALTHCARE72% MALWARE ATTACKS IN 2016 WERE RANSOMWARE DATA BREACHES COST HEALTHCARE FIRMS $402PER-LEAKED RECORD #1 RANSOMWARE A malicious program that locks an infected computer or encrypts data stored in it, and then demands a ransom to unlock the system or decrypt the data. THE 5 SECURITY THREATS IN HEALTHCARE 93% of phishing emails contain ransomware. Unplanned downtime caused by ransomware at healthcare organizations may cost an average of $7,900 a minute, per incident. “ ThePonemon Institute #2 INSIDERS An insider threat could be a current or a former employee who is responsible for a security breach in an organization. While most of these threats are malicious, some of them are unintentional. 67% 33% MALICIOUS • Co-workers • Disgruntled employees • Unauthorized access UNINTENTIONAL • Lost/stolen device • Bad security hygiene • Misuse of systems Insider threats are responsible for 90% of security incidents.“ #3 ADVANCED PERSISTENT THREATS (APT) A malicious campaign where the attacker breaches a network, stays there, and keeps gathering intelligence about the target. Such campaigns sometimes can go undetected for months or years. 22% 52% 25% 1% VERY LIKELY LIKELY NOT AT ALL LIKELY NOT VERY LIKELY A study on the likelihood of an APT Attack Health information is worth 10 times as much as credit cards, on the online black market. “ Federal Bureau of #4 MOBILE DEVICES Healthcare providers are increasingly using mobile devices for services such as submitting patient data, submitting bills, scheduling appointments, exchanging diagnosis details, etc. This means tons of patient data get accessed every day. 68%of healthcare security breaches were due to lost/stolen mobile devices. Lost/stolen mobile devices are one of the leading causes of healthcare data breach. “ Investigation Office for Civil Rights (OCR) #5 EMPLOYEE NEGLIGENCE While cyberattacks are the leading cause of data breaches in healthcare, negligent employees have a major role to play in several security incidents that occur. Clicking on malicious ads Responding to phishing emails Using infected USB devices Visiting infected websites 91% of data breaches start with a phishing attack. “ TCS Healthcare Common employee mistakes that cause data breaches Seqrite Security Solutions help businesses avoid all such risks and other cyberthreats with its range of DYNAMIC, SCALABLE, and FUTURE READY SOLUTIONS. Go to www.seqrite.com to learn more Sources: Technologies Health Information Trust Alliance PhishMe | The Ponemon Institute | Verizon Data Breach Investigations Report Federal Bureau of Investigation | Bitglass | TCS Healthcare Technologies Study conducted by ISACA on respondents from 17 industries in 2015 (including Healthcare) | http://www.isaca.org 2017 Verizon Data Breach Analysis Bitglass HOLLYWOOD PRESBYTERIAN MEDICAL CENTER PAID HACKERS 15% 2017 Verizon Data Breach Analysisfortune.com INVOLVED HEALTHCARE ORGANIZATIONS
