More Related Content
Similar to Year of the AppSec Breach_Forrester
Similar to Year of the AppSec Breach_Forrester (20)
Year of the AppSec Breach_Forrester
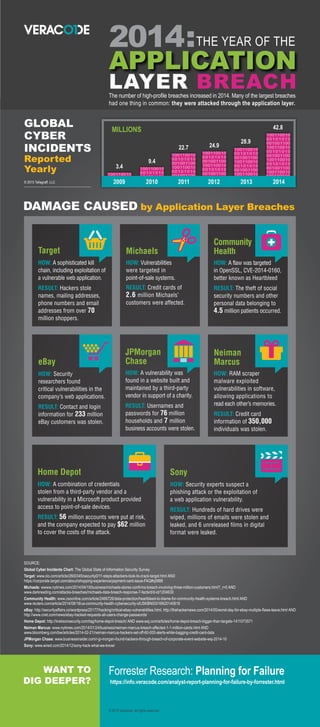
- 1. DAMAGE CAUSED by Application Layer Breaches
2014:THE YEAR OF THE
LAYER BREACHThe number of high-profile breaches increased in 2014. Many of the largest breaches
had one thing in common: they were attacked through the application layer.
GLOBAL
CYBER
INCIDENTS
Reported
Yearly
© 2015 Tellagraff, LLC
SOURCE:
Global Cyber Incidents Chart: The Global State of Information Security Survey
Target: www.cio.com/article/2600345/security0/11-steps-attackers-took-to-crack-target.html AND
https://corporate.target.com/about/shopping-experience/payment-card-issue-FAQ#q5888
Michaels: wwww.nytimes.com/2014/04/19/business/michaels-stores-confirms-breach-involving-three-million-customers.html?_r=0 AND
www.darkreading.com/attacks-breaches/michaels-data-breach-response-7-facts/d/d-id/1204630
Community Health: www.csoonline.com/article/2466726/data-protection/heartbleed-to-blame-for-community-health-systems-breach.html AND
www.reuters.com/article/2014/08/18/us-community-health-cybersecurity-idUSKBN0GI16N20140818
eBay: http://securityaffairs.co/wordpress/25177/hacking/critical-ebay-vulnerabilities.html, http://thehackernews.com/2014/05/worst-day-for-ebay-multiple-flaws-leave.html AND
http://www.cnet.com/news/ebay-hacked-requests-all-users-change-passwords/
Home Depot: http://krebsonsecurity.com/tag/home-depot-breach/ AND www.wsj.com/articles/home-depot-breach-bigger-than-targets-1411073571
Neiman Marcus: www.nytimes.com/2014/01/24/business/neiman-marcus-breach-affected-1-1-million-cards.html AND
www.bloomberg.com/bw/articles/2014-02-21/neiman-marcus-hackers-set-off-60-000-alerts-while-bagging-credit-card-data
JPMorgan Chase: www.businessinsider.com/r-jp-morgan-found-hackers-through-breach-of-corporate-event-website-wsj-2014-10
Sony: www.wired.com/2014/12/sony-hack-what-we-know/
Target
HOW: A sophisticated kill
chain, including exploitation of
a vulnerable web application.
RESULT: Hackers stole
names, mailing addresses,
phone numbers and email
addresses from over 70
million shoppers.
Michaels
HOW: Vulnerabilities
were targeted in
point-of-sale systems.
RESULT: Credit cards of
2.6 million Michaels’
customers were affected.
Community
Health
HOW: A flaw was targeted
in OpenSSL, CVE-2014-0160,
better known as Heartbleed
RESULT: The theft of social
security numbers and other
personal data belonging to
4.5 million patients occurred.
eBay
HOW: Security
researchers found
critical vulnerabilities in the
company’s web applications.
RESULT: Contact and login
information for 233 million
eBay customers was stolen.
Neiman
Marcus
HOW: RAM scraper
malware exploited
vulnerabilities in software,
allowing applications to
read each other’s memories.
RESULT: Credit card
information of 350,000
individuals was stolen.
Sony
HOW: Security experts suspect a
phishing attack or the exploitation of
a web application vulnerability.
RESULT: Hundreds of hard drives were
wiped, millions of emails were stolen and
leaked, and 6 unreleased films in digital
format were leaked.
Home Depot
HOW: A combination of credentials
stolen from a third-party vendor and a
vulnerability in a Microsoft product provided
access to point-of-sale devices.
RESULT: 56 million accounts were put at risk,
and the company expected to pay $62 million
to cover the costs of the attack.
JPMorgan
Chase
HOW: A vulnerability was
found in a website built and
maintained by a third-party
vendor in support of a charity.
RESULT: Usernames and
passwords for 76 million
households and 7 million
business accounts were stolen.
Forrester Research: Planning for Failure
https://info.veracode.com/analyst-report-planning-for-failure-by-forrester.html
© 2015 Veracode. All rights reserved.
WANT TO
DIG DEEPER?
3.4
9.4
22.7 24.9
28.9
42.8
2009 2010 2011 2012 2013 2014
MILLIONS