5 Types of Insider Threats and How to Detect them in Your ERP System
•
0 likes•20 views
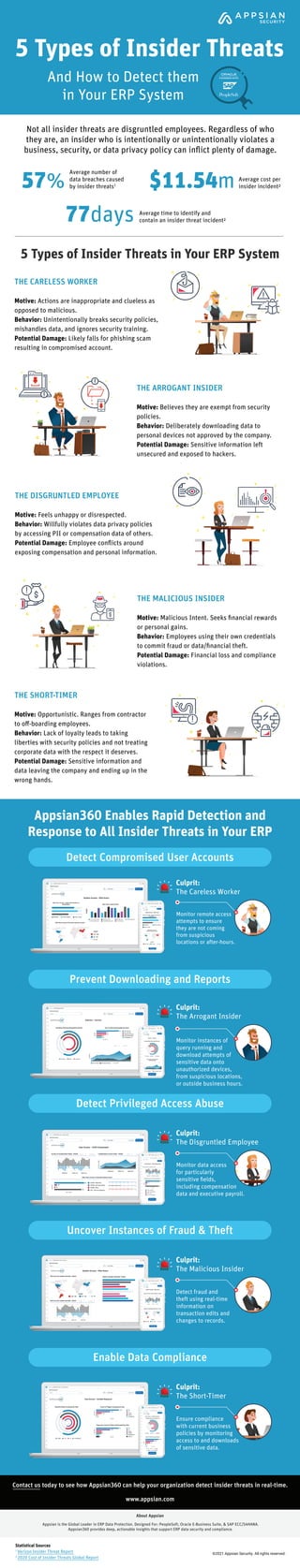
Not all insider threats are disgruntled employees. Regardless of who they are, an insider who is intentionally or unintentionally violating a business, security, or data privacy policy can inflict plenty of damage. Learn more about who they are and how you can stop them.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
How to Build an Insider Threat Program in 30 Minutes 

How to Build an Insider Threat Program in 30 Minutes
Phish, Spoof, Scam: Insider Threats, the GDPR & Other Regulations

Phish, Spoof, Scam: Insider Threats, the GDPR & Other Regulations
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Prevent Insider Threats with User Activity Monitoring

Prevent Insider Threats with User Activity Monitoring
Similar to 5 Types of Insider Threats and How to Detect them in Your ERP System
From ITC Agent Conference 2015...
Have you ever really thought about all the confidential data you store in your agency? Do you realize how easily your data could be stolen? Are you protecting yourself and your agency from theft of information? Attend this session to hear the tips, tricks and suggestions that will protect your agency and your clients' information.Security Features and Securing Your Data in TurboRater and InsurancePro - Kel...

Security Features and Securing Your Data in TurboRater and InsurancePro - Kel...Insurance Technologies Corporation (ITC)
Cyber criminals are always on the lookout to find ways for gaining profits by misusing the data leaks of an organisation. In this blog, Explain How to Prevent Data Leakage. Techno Edge Systems LLC provide Endpoint Security Solutions in Dubai, UAE for Businesses. Call at 054-4653108 Visit us: www.itamcsupport.ae.Is It Possible to Prevent Data Leaks in an Effective Manner.pdf

Is It Possible to Prevent Data Leaks in an Effective Manner.pdfIT AMC Support Dubai - Techno Edge Systems LLC
Similar to 5 Types of Insider Threats and How to Detect them in Your ERP System (20)
Identity intelligence: Threat-aware Identity and Access Management

Identity intelligence: Threat-aware Identity and Access Management
Part 1: Identifying Insider Threats with Fidelis EDR Technology 

Part 1: Identifying Insider Threats with Fidelis EDR Technology
Cyber Threat Landscape- Security Posture - ver 1.0

Cyber Threat Landscape- Security Posture - ver 1.0
Security Features and Securing Your Data in TurboRater and InsurancePro - Kel...

Security Features and Securing Your Data in TurboRater and InsurancePro - Kel...
Security Scare - Cybersecurity & What to Do About It!

Security Scare - Cybersecurity & What to Do About It!
How to Protect Your Business from Cyber Threats | The Entrepreneur Review

How to Protect Your Business from Cyber Threats | The Entrepreneur Review
Is It Possible to Prevent Data Leaks in an Effective Manner.pdf

Is It Possible to Prevent Data Leaks in an Effective Manner.pdf
Compete To Win: Don’t Just Be Compliant – Be Secure!

Compete To Win: Don’t Just Be Compliant – Be Secure!
Understanding Website Data Security And Its Importance.pdf

Understanding Website Data Security And Its Importance.pdf
Recently uploaded
Recently uploaded (20)
WSO2CON 2024 - How CSI Piemonte Is Apifying the Public Administration

WSO2CON 2024 - How CSI Piemonte Is Apifying the Public Administration
WSO2CON 2024 - Building a Digital Government in Uganda

WSO2CON 2024 - Building a Digital Government in Uganda
Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...

Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...
Large-scale Logging Made Easy: Meetup at Deutsche Bank 2024

Large-scale Logging Made Easy: Meetup at Deutsche Bank 2024
WSO2Con2024 - From Blueprint to Brilliance: WSO2's Guide to API-First Enginee...

WSO2Con2024 - From Blueprint to Brilliance: WSO2's Guide to API-First Enginee...
WSO2CON 2024 - IoT Needs CIAM: The Importance of Centralized IAM in a Growing...

WSO2CON 2024 - IoT Needs CIAM: The Importance of Centralized IAM in a Growing...
WSO2CON 2024 - API Management Usage at La Poste and Its Impact on Business an...

WSO2CON 2024 - API Management Usage at La Poste and Its Impact on Business an...
WSO2CON 2024 - Navigating API Complexity: REST, GraphQL, gRPC, Websocket, Web...

WSO2CON 2024 - Navigating API Complexity: REST, GraphQL, gRPC, Websocket, Web...
WSO2CON 2024 - WSO2's Digital Transformation Journey with Choreo: A Platforml...

WSO2CON 2024 - WSO2's Digital Transformation Journey with Choreo: A Platforml...
WSO2CON 2024 - Unlocking the Identity: Embracing CIAM 2.0 for a Competitive A...

WSO2CON 2024 - Unlocking the Identity: Embracing CIAM 2.0 for a Competitive A...
WSO2Con2024 - Facilitating Broadband Switching Services for UK Telecoms Provi...

WSO2Con2024 - Facilitating Broadband Switching Services for UK Telecoms Provi...
WSO2CON 2024 - Freedom First—Unleashing Developer Potential with Open Source

WSO2CON 2024 - Freedom First—Unleashing Developer Potential with Open Source
WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation

WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation
WSO2CON 2024 - Building the API First Enterprise – Running an API Program, fr...

WSO2CON 2024 - Building the API First Enterprise – Running an API Program, fr...
5 Types of Insider Threats and How to Detect them in Your ERP System
- 1. 5 Types of Insider Threats in Your ERP System 5 Types of Insider Threats ©2021 Appsian Security. All rights reserved. Average time to identify and contain an insider threat incident² 77days Average number of data breaches caused by insider threats1 Average cost per insider incident² 57% $11.54m Not all insider threats are disgruntled employees. Regardless of who they are, an insider who is intentionally or unintentionally violates a business, security, or data privacy policy can inflict plenty of damage. Appsian360 Enables Rapid Detection and Response to All Insider Threats in Your ERP Contact us today to see how Appsian360 can help your organization detect insider threats in real-time. Appsian is the Global Leader in ERP Data Protection. Designed For: PeopleSoft, Oracle E-Business Suite, & SAP ECC/S4HANA. Appsian360 provides deep, actionable insights that support ERP data security and compliance. THE CARELESS WORKER Motive: Actions are inappropriate and clueless as opposed to malicious. Behavior: Unintentionally breaks security policies, mishandles data, and ignores security training. Potential Damage: Likely falls for phishing scam resulting in compromised account. THE SHORT-TIMER Motive: Opportunistic. Ranges from contractor to off-boarding employees. Behavior: Lack of loyalty leads to taking liberties with security policies and not treating corporate data with the respect it deserves. Potential Damage: Sensitive information and data leaving the company and ending up in the wrong hands. THE MALICIOUS INSIDER Motive: Malicious Intent. Seeks financial rewards or personal gains. Behavior: Employees using their own credentials to commit fraud or data/financial theft. Potential Damage: Financial loss and compliance violations. THE DISGRUNTLED EMPLOYEE Motive: Feels unhappy or disrespected. Behavior: Willfully violates data privacy policies by accessing PII or compensation data of others. Potential Damage: Employee conflicts around exposing compensation and personal information. THE ARROGANT INSIDER Motive: Believes they are exempt from security policies. Behavior: Deliberately downloading data to personal devices not approved by the company. Potential Damage: Sensitive information left unsecured and exposed to hackers. Statistical Sources 1 Verizon Insider Threat Report 2 2020 Cost of Insider Threats Global Report Culprit: The Careless Worker Monitor remote access attempts to ensure they are not coming from suspicious locations or after-hours. Culprit: The Arrogant Insider Monitor instances of query running and download attempts of sensitive data onto unauthorized devices, from suspicious locations, or outside business hours. Monitor data access for particularly sensitive fields, including compensation data and executive payroll. Detect Compromised User Accounts Detect Privileged Access Abuse Prevent Downloading and Reports Culprit: The Disgruntled Employee Detect fraud and theft using real-time information on transaction edits and changes to records. Uncover Instances of Fraud & Theft Culprit: The Malicious Insider Ensure compliance with current business policies by monitoring access to and downloads of sensitive data. Enable Data Compliance Culprit: The Short-Timer www.appsian.com About Appsian And How to Detect them in Your ERP System
