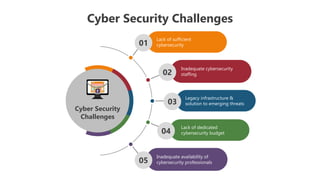
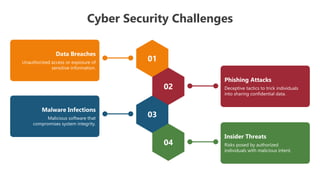
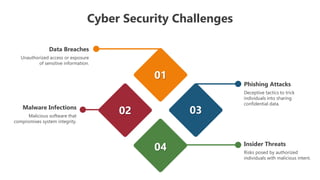
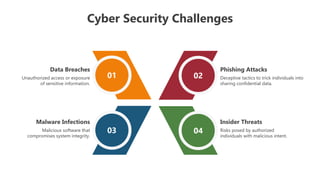
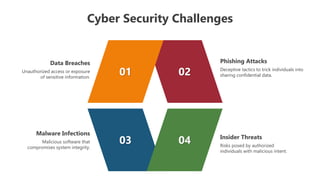
The document outlines various cybersecurity challenges including ransomware attacks, insider threats, data breaches, malware infections, and phishing attacks, which are compounded by inadequate staffing and budgetary constraints. It also provides instructions for editing presentation elements and details the terms of use for both free and premium subscribers of Slideegg. The emphasis is on maintaining security while managing and using cybersecurity resources effectively.