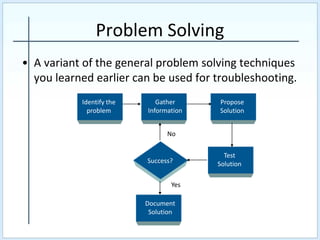
Troubleshooting a computer problem involves remaining calm, documenting all steps taken, and testing solutions without making the problem worse. The process includes identifying the problem symptoms, gathering information about recent changes and the current configuration, and using online and diagnostic resources. Potential solutions are proposed and tested through a process of elimination, with only one variable changed at a time. If a solution is not successful, more information is gathered to propose and test another option.