3 d game work flow
•Download as DOCX, PDF•
0 likes•131 views
3 d game work flow
Report
Share
Report
Share
Recommended
CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddel

CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddelmohamed khalaf alla mohamedain
More Related Content
Viewers also liked
CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddel

CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddelmohamed khalaf alla mohamedain
Viewers also liked (11)
MuleSoft ESB Payload Encrypt Decrypt using anypoint enterprise security

MuleSoft ESB Payload Encrypt Decrypt using anypoint enterprise security
CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddel

CHAPTER 6 REQUIREMENTS MODELING: SCENARIO based Model , Class based moddel
More from PhillipWynne12281991
More from PhillipWynne12281991 (20)
Y1 games ig2 learner assessment submission declaration

Y1 games ig2 learner assessment submission declaration
Recently uploaded
Recently uploaded (20)
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
3 d game work flow
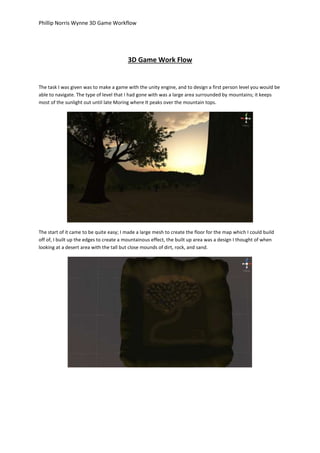
- 1. Phillip Norris Wynne 3D Game Workflow 3D Game Work Flow The task I was given was to make a game with the unity engine, and to design a first person level you would be able to navigate. The type of level that I had gone with was a large area surrounded by mountains; it keeps most of the sunlight out until late Moring where It peaks over the mountain tops. The start of it came to be quite easy; I made a large mesh to create the floor for the map which I could build off of, I built up the edges to create a mountainous effect, the built up area was a design I thought of when looking at a desert area with the tall but close mounds of dirt, rock, and sand.
- 2. Phillip Norris Wynne 3D Game Workflow The next image is showing the textures I have put into my game, with not having a lot of time to complete this level only a few textures were used, this is the grassy texture that I used for the game. To make the pathways I used a different texture mixed and blended with the one from earlier, it gives the pathways a more distinctive look, like they have been walked upon more than the grass This image is of the path way going through the small suburban town; it gives you a way to get around the map so you’re not wandering around. This is also the main part of the map the small town, you have to navigate this to get to the large woods.
- 3. Phillip Norris Wynne 3D Game Workflow This image shows the large forest, I found out when you got to the middle it was almost impossible to get out, as the terrian was very steap and hard to manovour, add to the almost impossible sense that you had no idea where you were. The images below are showing details in the surburb. The details are mailny surban villages and a lot of tree. These objects are also all have collision mask meaning you cannot walk through them.