The December 2023 Patch Tuesday webinar presented a relatively light lineup of updates, highlighting Microsoft and Apple’s releases, including fixes for 34 new CVEs with a focus on OS and browser vulnerabilities. Critical vulnerabilities, particularly affecting log4j and Samba, as well as ongoing concerns in Linux systems, were also discussed, stressing the need for immediate updates. Known issues in Windows 11 and Windows 10 updates were noted, along with important security updates for Microsoft Office and third-party applications.














![Copyright © 2023 Ivanti. All rights reserved.
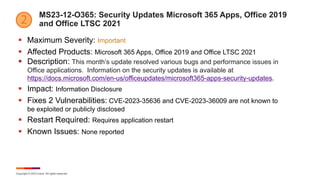
December Known Issues for Windows 11
§ KB 5033369 – Windows 11 21H2
§ [Encrypt Drive Reporting Error] Using the FixedDrivesEncryptionType or
SystemDrivesEncryptionType policy settings in the BitLocker configuration service
provider (CSP) node in mobile device management (MDM) apps might incorrectly
show a 65000 error in the "Require Device Encryption" setting for some devices in
your environment. Affected environments are those with the “Enforce drive
encryption type on operating system drives” or "Enforce drive encryption on fixed
drives" policies set to enabled and selecting either "full encryption" or "used space
only". Microsoft Intune is affected by this issue but third-party MDMs might also be
affected.
§ Important: This issue is a reporting issue only and does not affect drive encryption
or the reporting of other issues on the device, including other BitLocker issues.
§ Microsoft is working on a resolution](https://image.slidesharecdn.com/itdecember2023patchtuesday-231214161620-64a50dc2/85/2023-Patch-Tuesday-Italia-Dicembre-17-320.jpg)
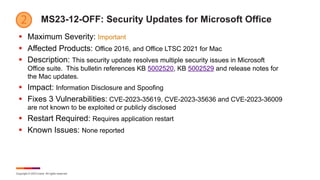
![Copyright © 2023 Ivanti. All rights reserved.
December Known Issues for Windows 11 (cont)
§ KB 5033375 – Windows 11 22H2/23H2
§ [Encrypt Drive Reporting Error]
§ [Icon Display] Windows devices using more than one (1) monitor might experience
issues with desktop icons moving unexpectedly between monitors or other icon
alignment issues when attempting to use Copilot in Windows (in preview).
§ [Emoji Display] The color font format for COLRv1 does not render properly. This
format enables Windows to display emoji with a 3D-like appearance.
§ [Narrator] When using physical media or disc images (ISO) to install Windows 11,
version 23H2 (also referred to as the Windows 11 2023 Update) on a device,
Microsoft Narrator might not start. Narrator is commonly initialized using keyboard
commands, such as Ctrl + Windows key + Enter. Although Narrator is present in
Windows when the installation process begins, it might open in an unresponsive
state when initialized using any method.
§ Microsoft is working on a resolution for all four issues.](https://image.slidesharecdn.com/itdecember2023patchtuesday-231214161620-64a50dc2/85/2023-Patch-Tuesday-Italia-Dicembre-18-320.jpg)

![Copyright © 2023 Ivanti. All rights reserved.
December Known Issues for Windows 10
§ KB 5033372 – Windows 10 Enterprise and Education, version 21H2;
Windows 10 IoT Enterprise, version 21H2; Windows 10 Enterprise
Multi-Session, version 21H2; and Windows 10, version 22H2, all
editions
§ [Encrypt Drive Reporting Error]
§ KB 5033371 – Win 10 Ent LTSC 2019, Win 10 IoT Ent LTSC 2019,
Windows 10 IoT Core 2019 LTSC, Windows Server 2019
§ [Encrypt Drive Reporting Error]](https://image.slidesharecdn.com/itdecember2023patchtuesday-231214161620-64a50dc2/85/2023-Patch-Tuesday-Italia-Dicembre-20-320.jpg)