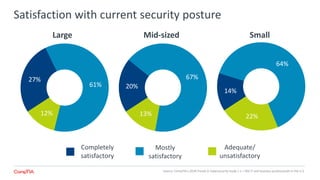
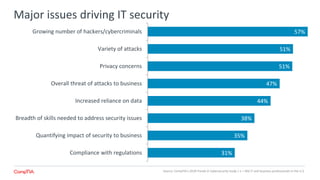
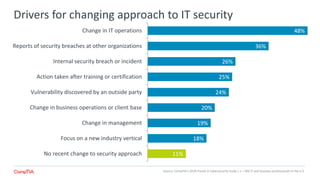
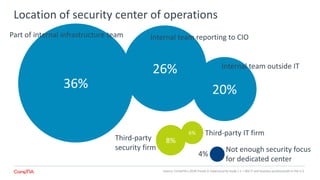
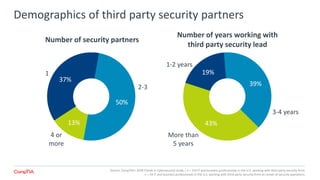
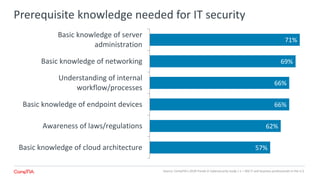
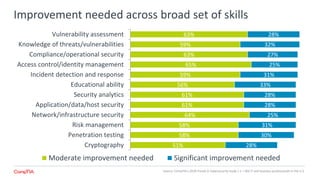
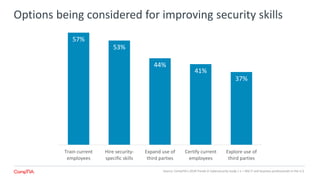
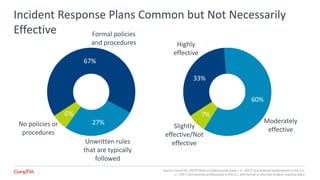
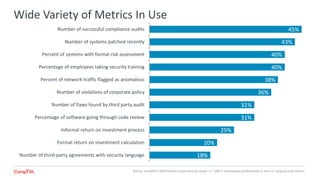
The 2018 Trends in Cybersecurity report highlights that a significant portion of IT and business professionals in the U.S. feel only partially satisfied with their organizations' security postures. Key issues driving a reevaluation of security measures include compliance, the threat of cyberattacks, and the need for diverse skills. Organizations are considering strategies such as training current employees, hiring specialists, and enhancing third-party collaborations to improve security capabilities.