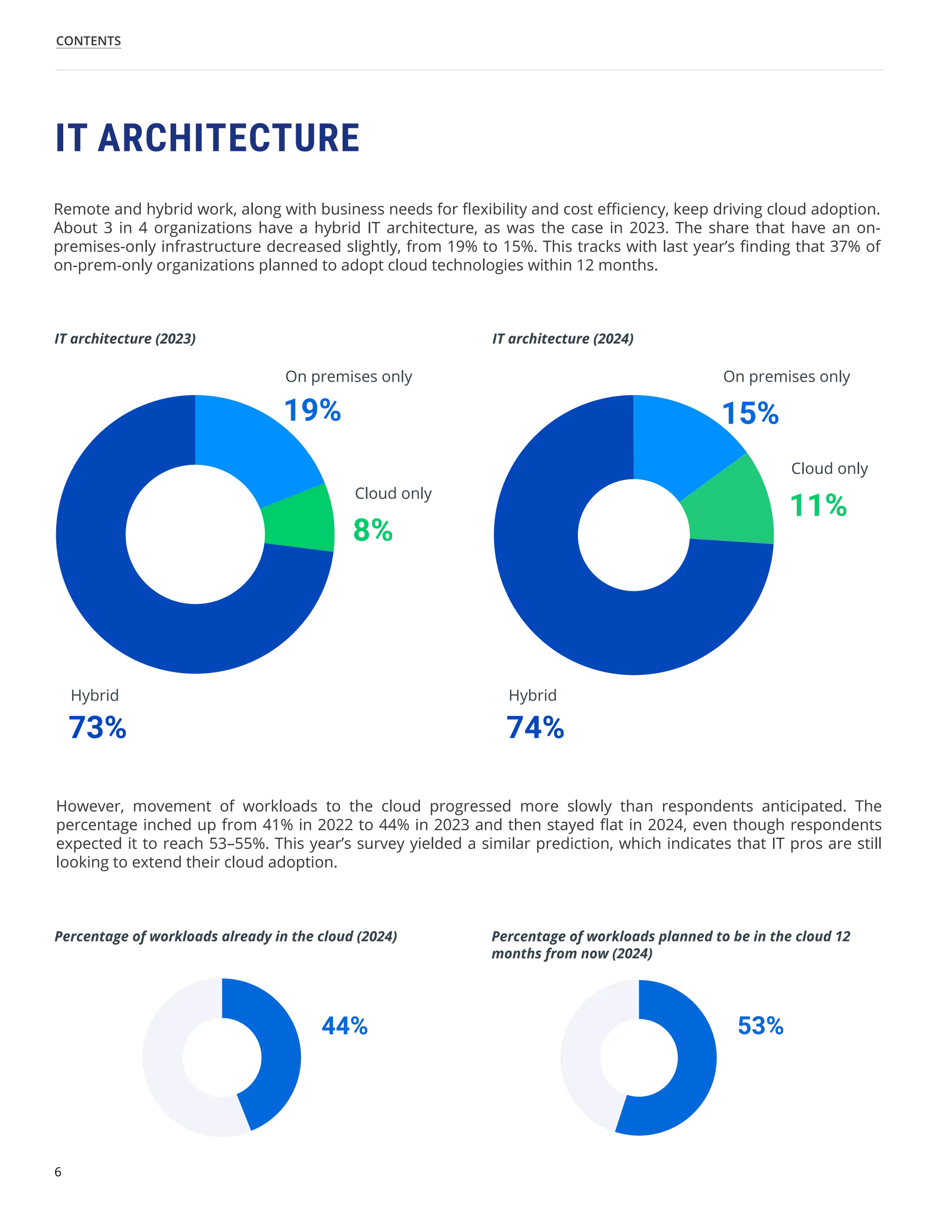
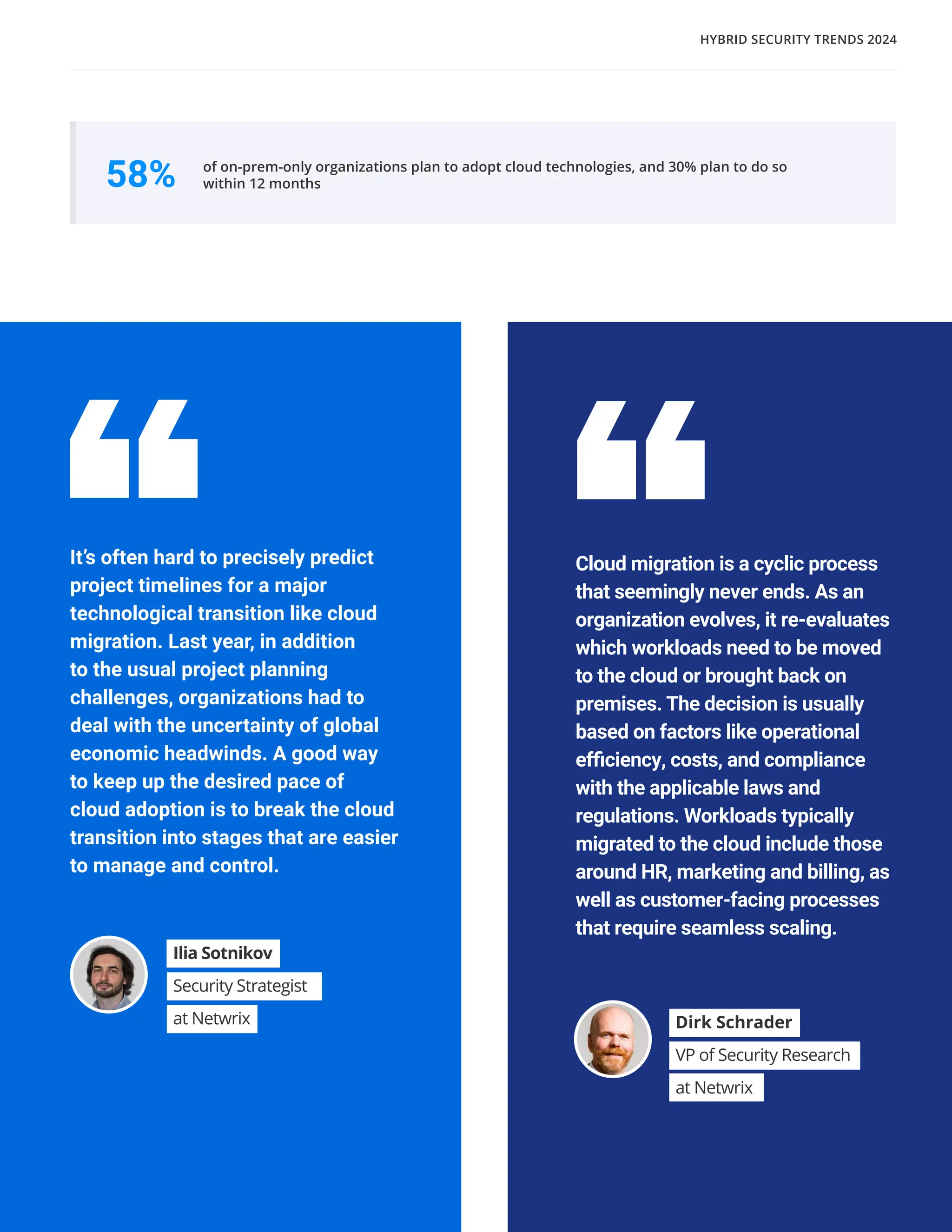
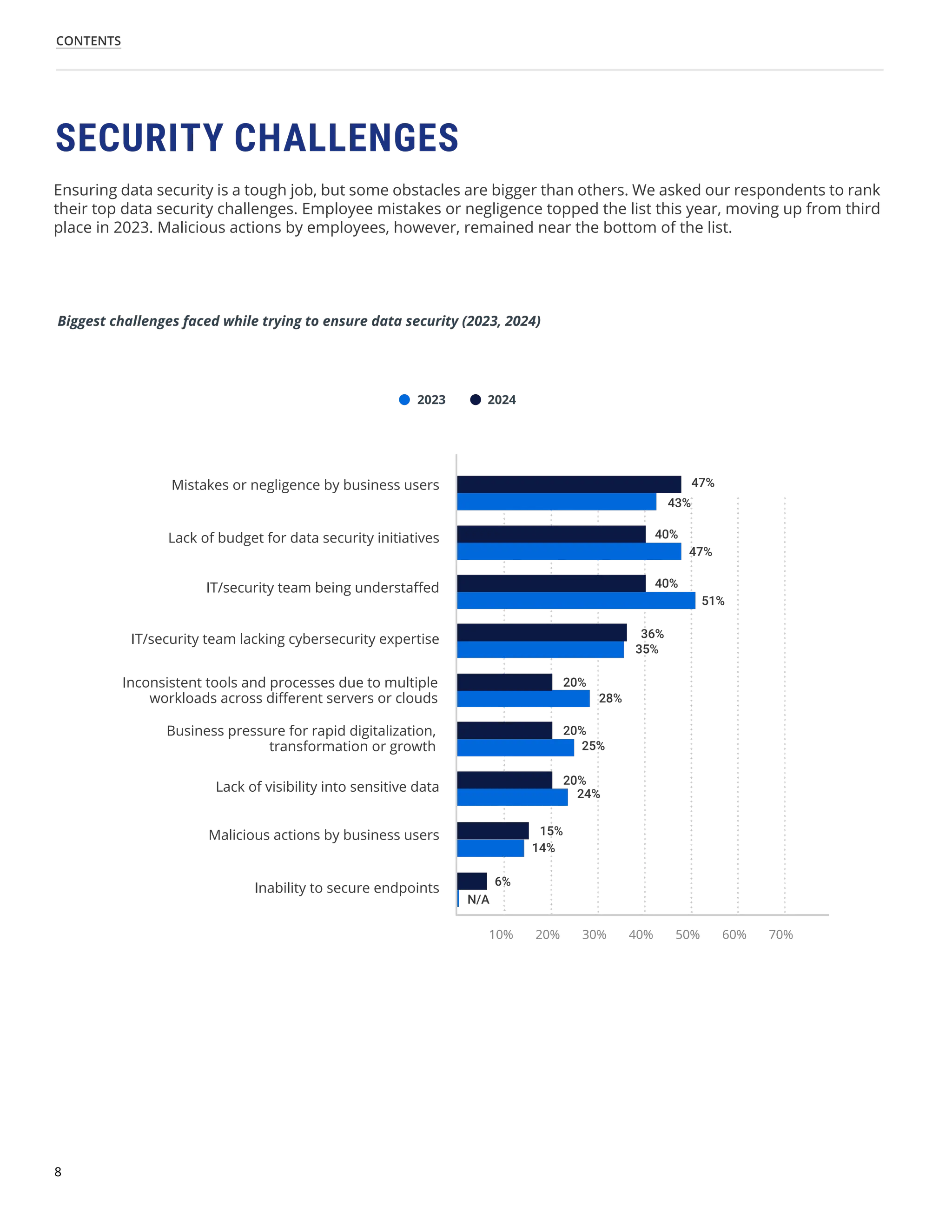
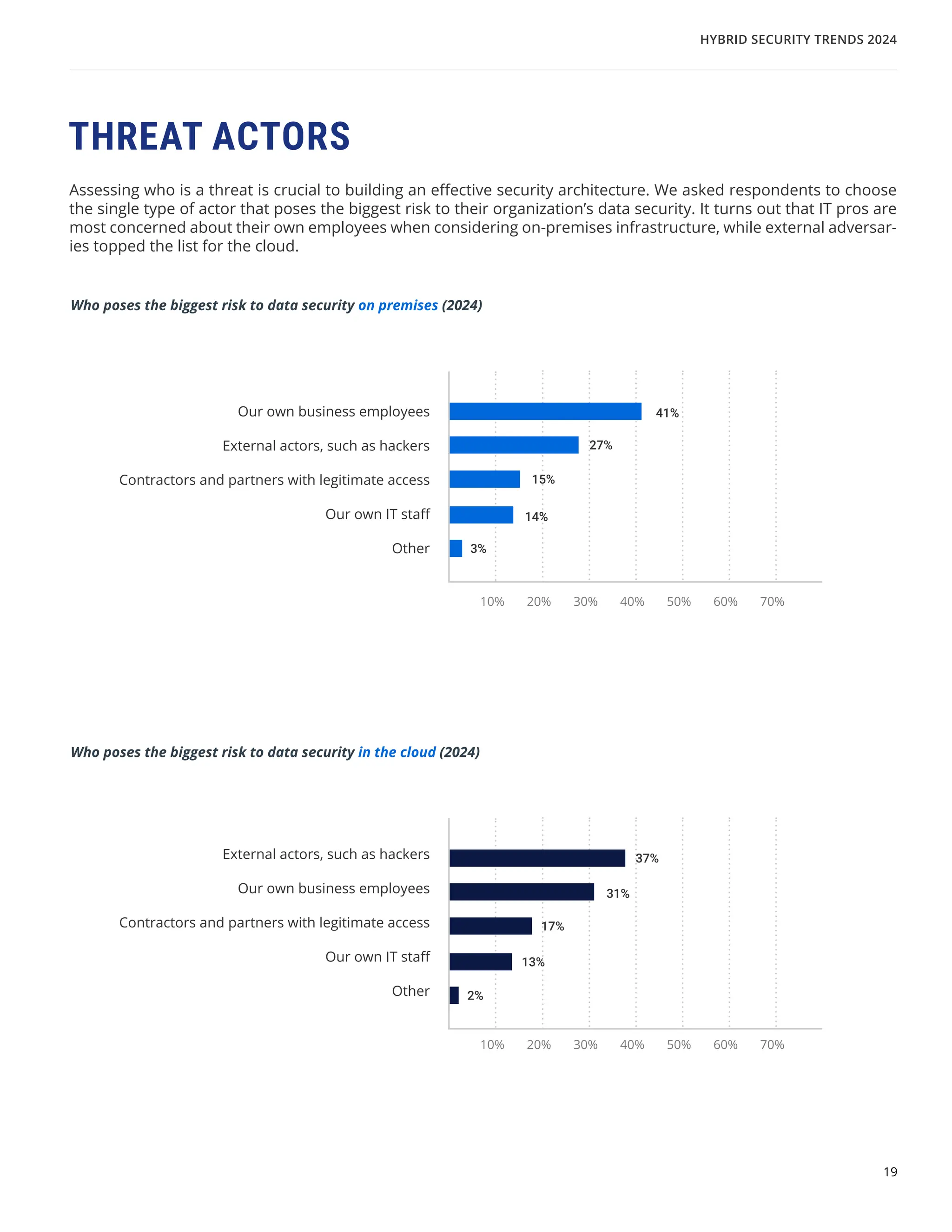
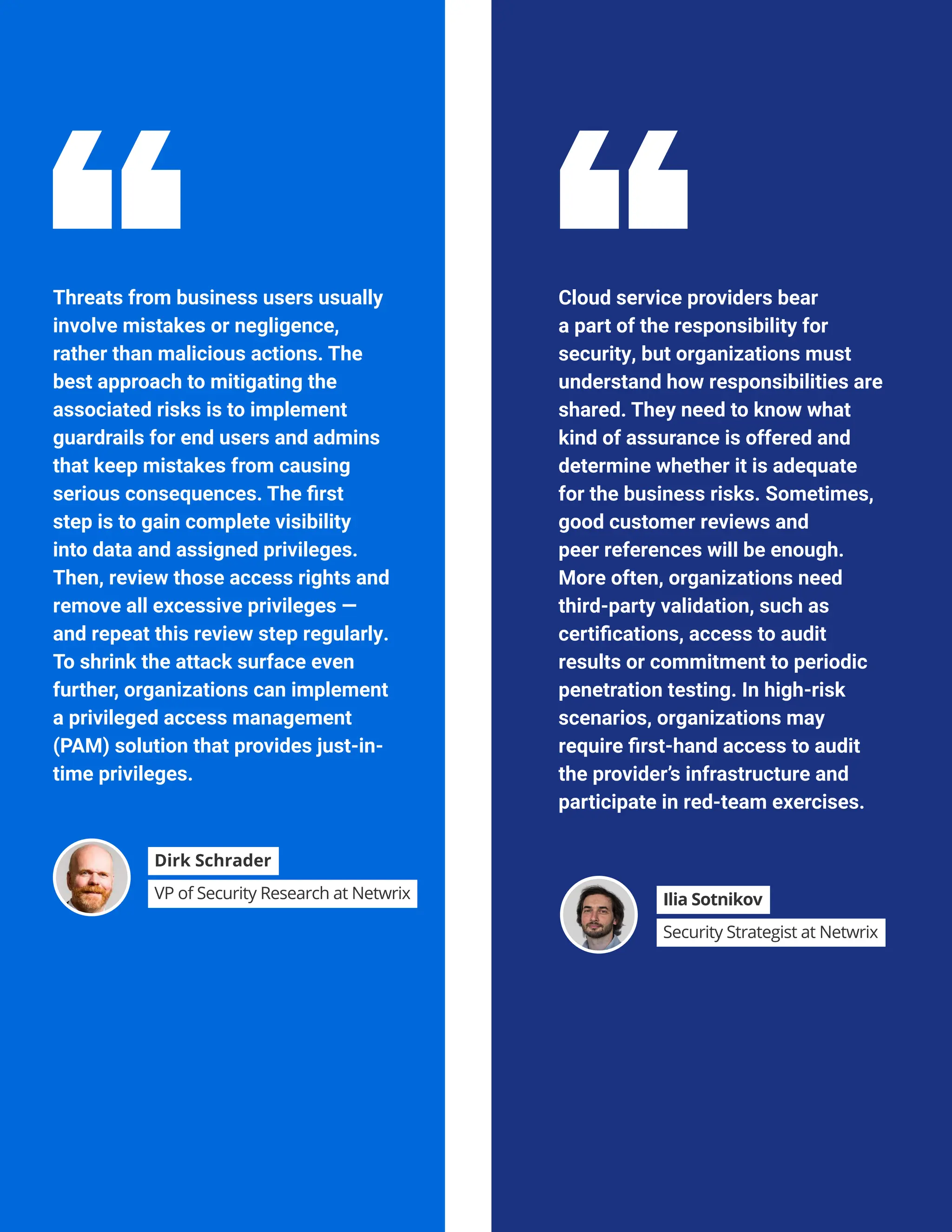
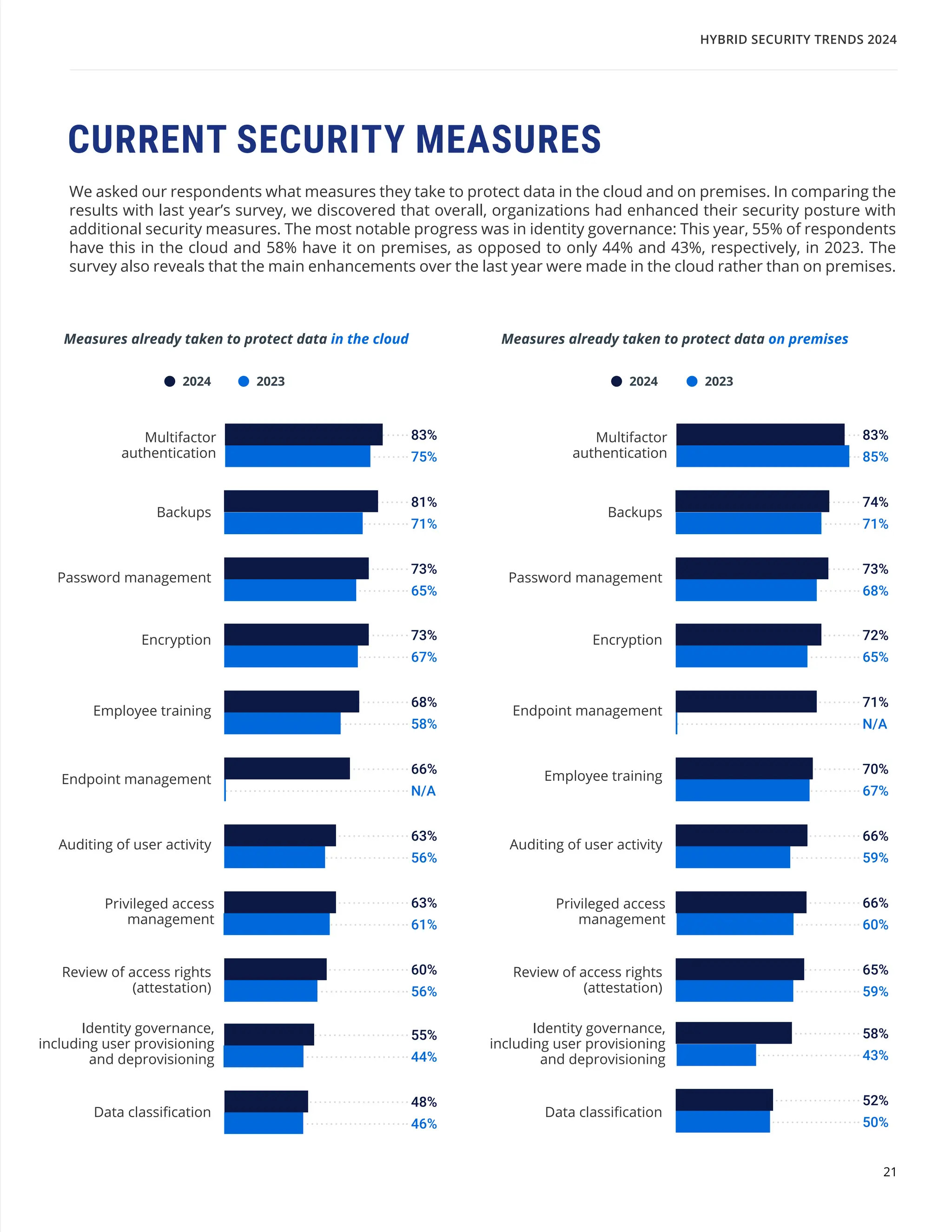
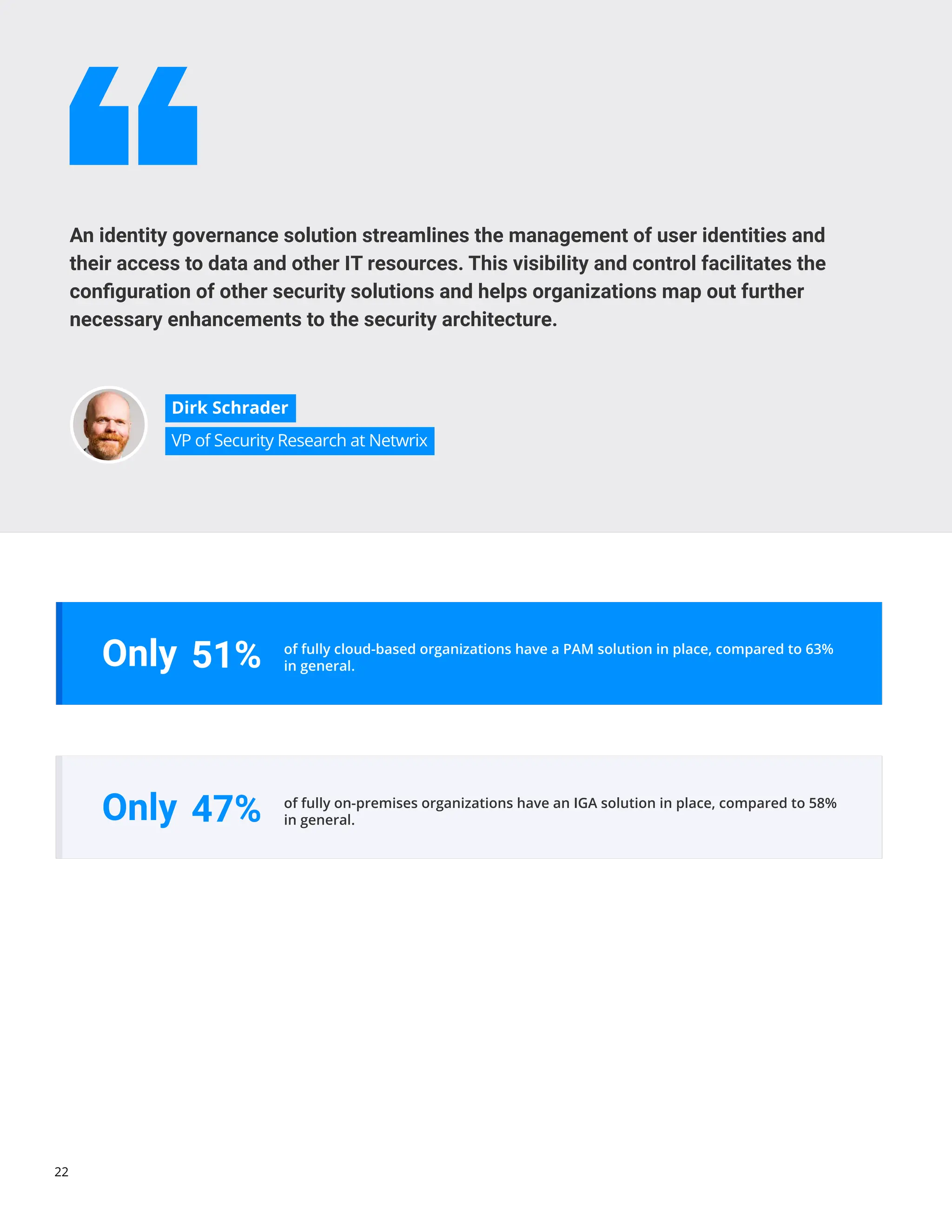
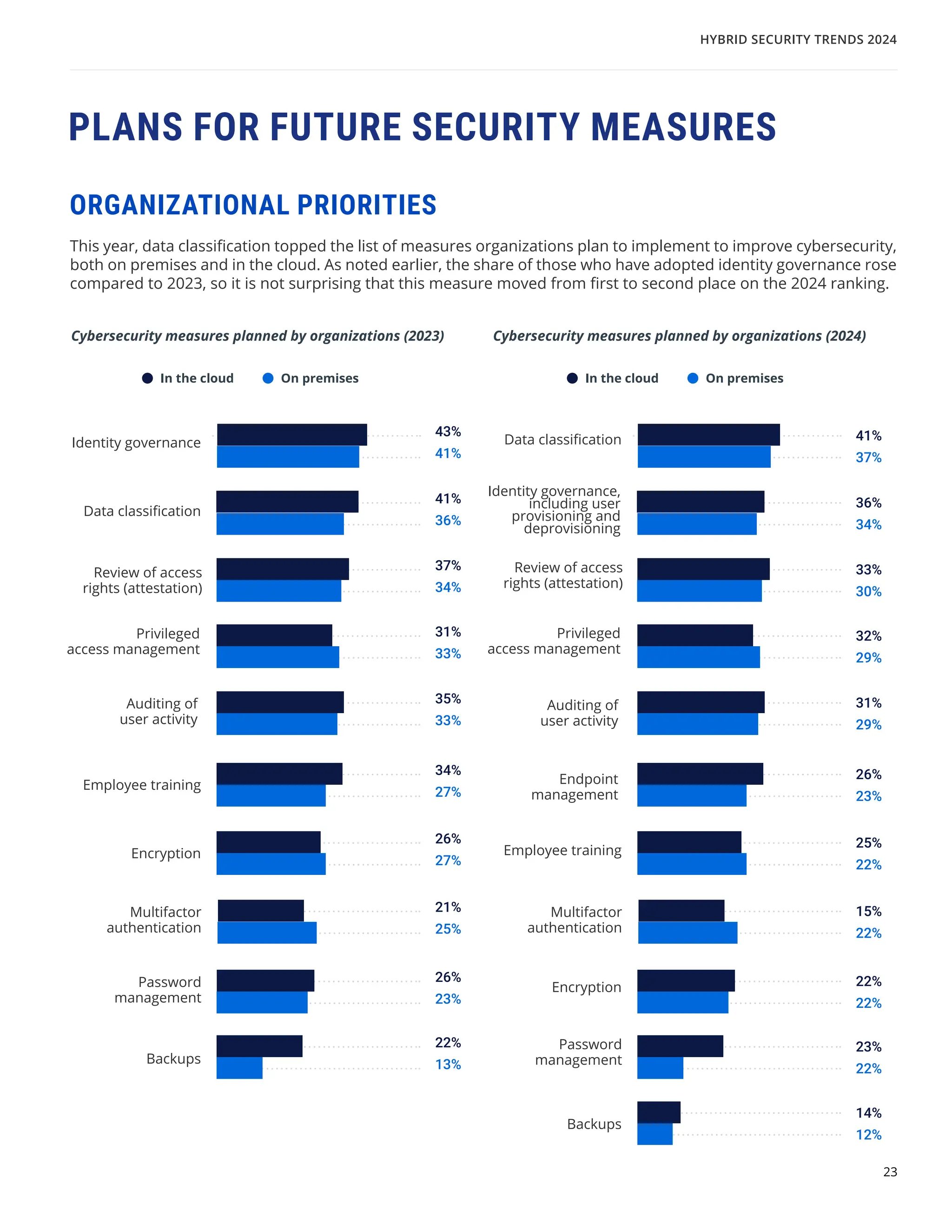
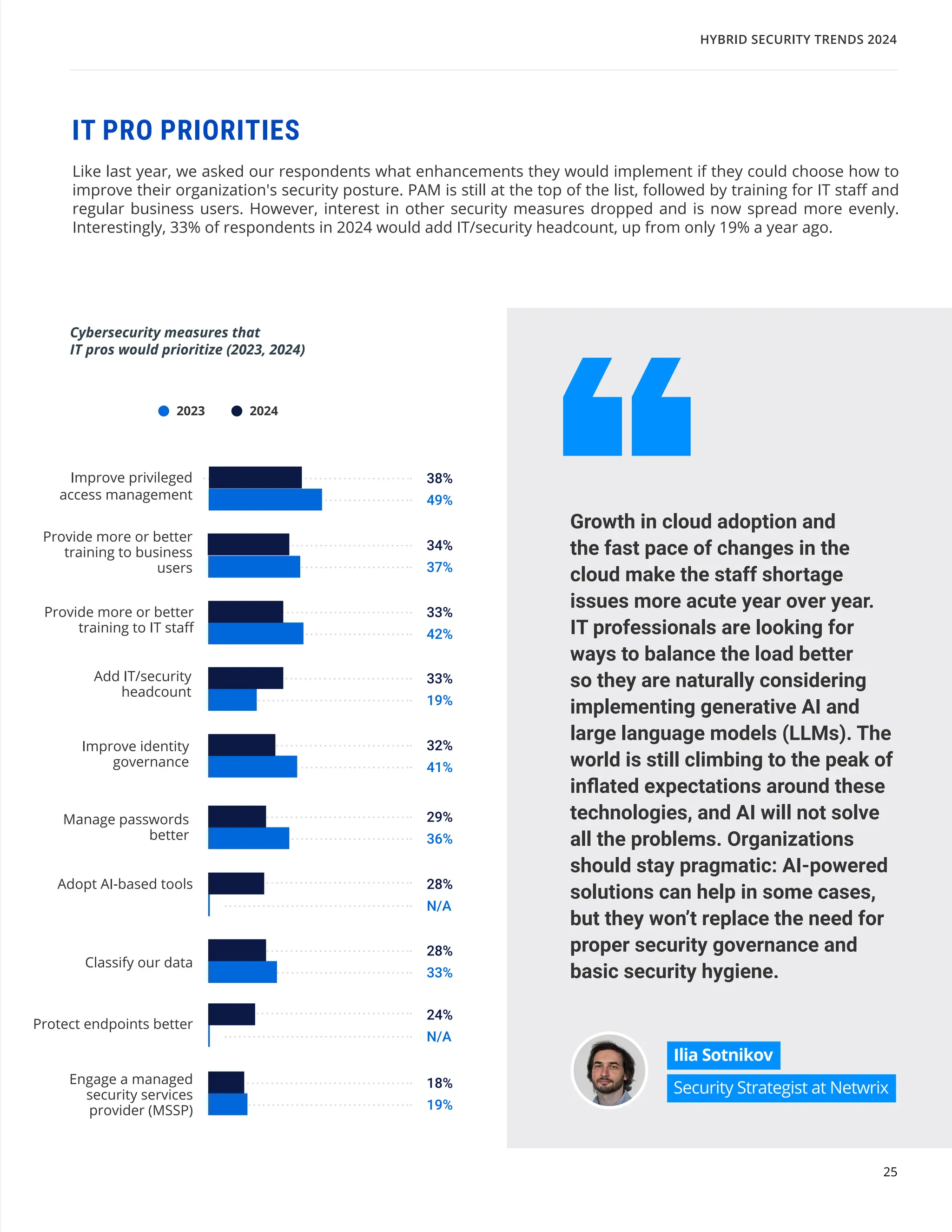
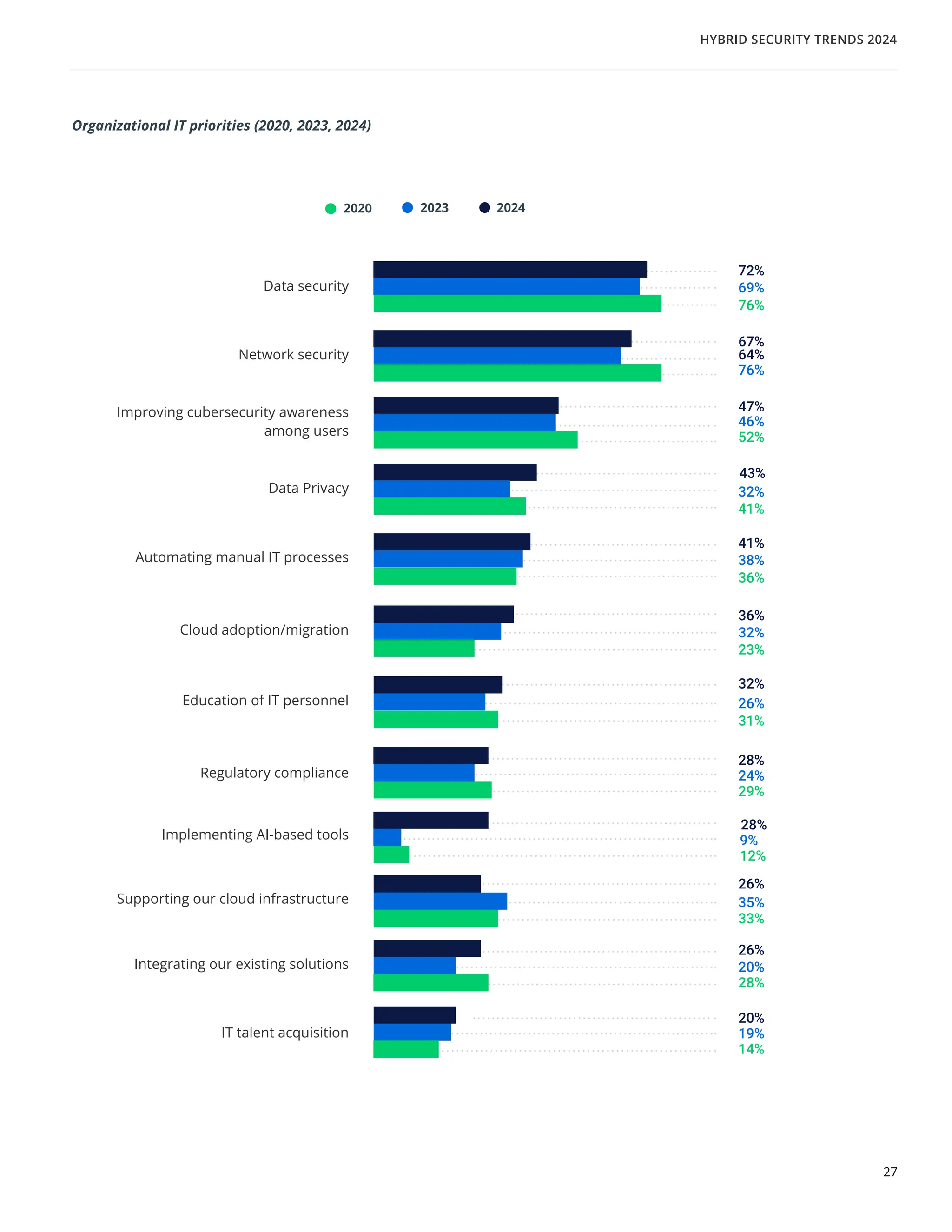
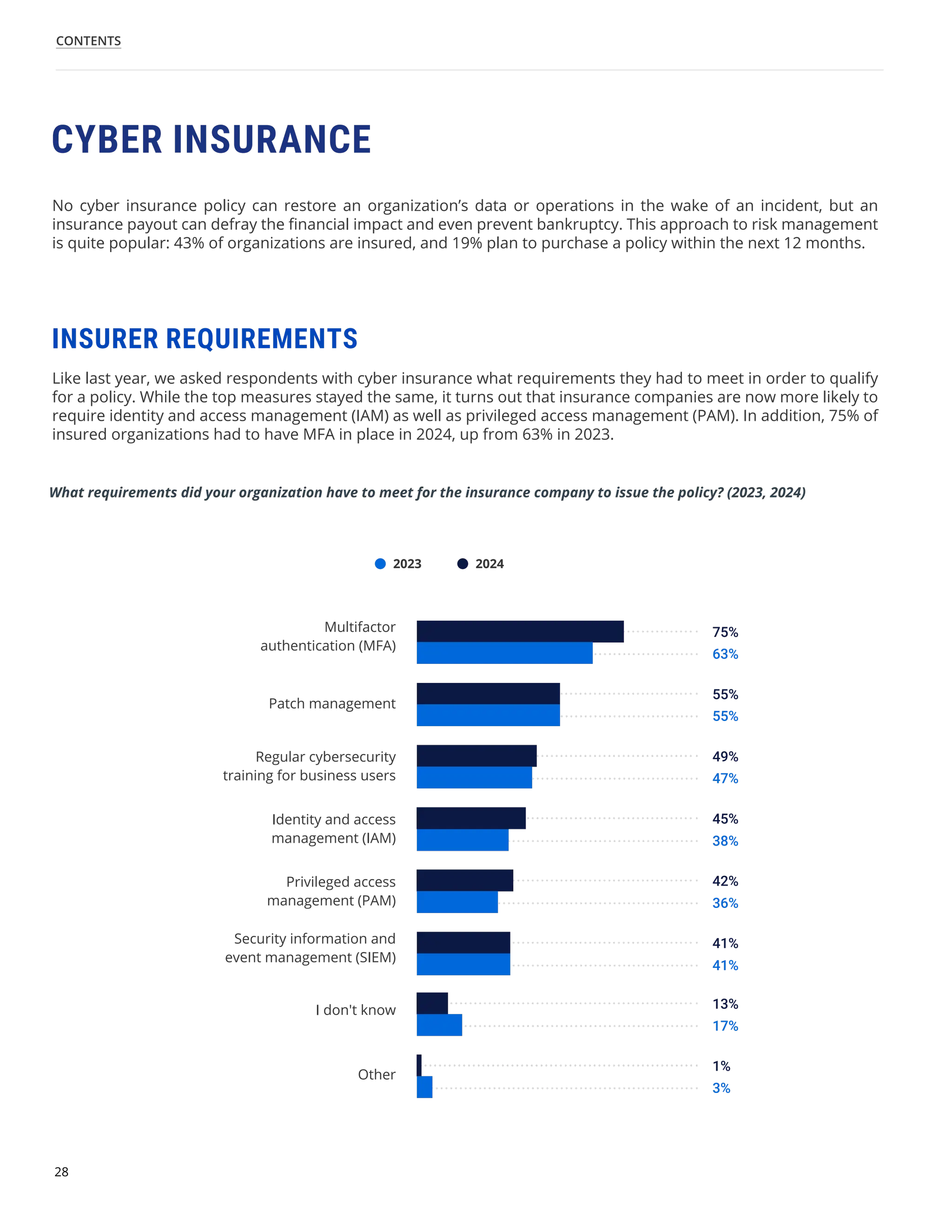
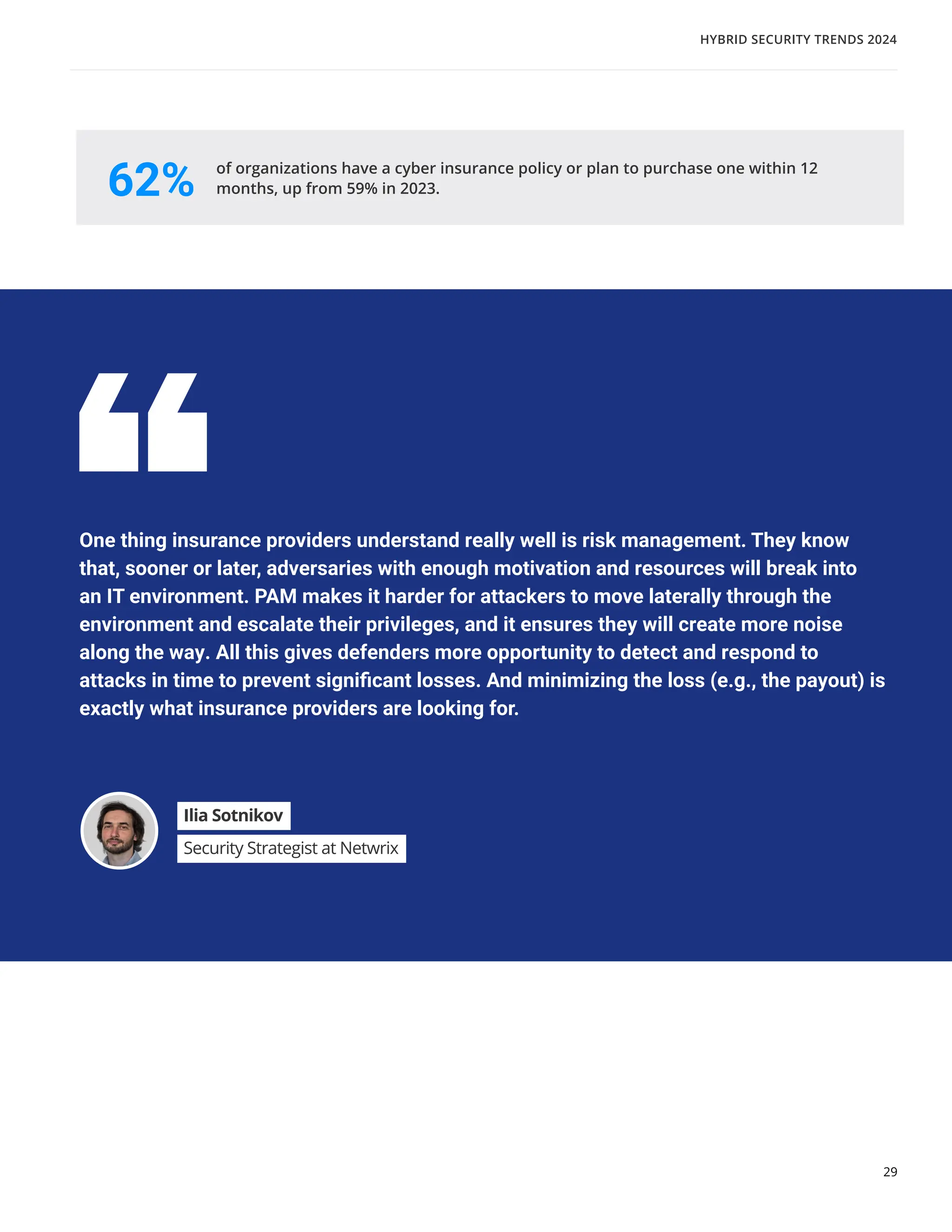
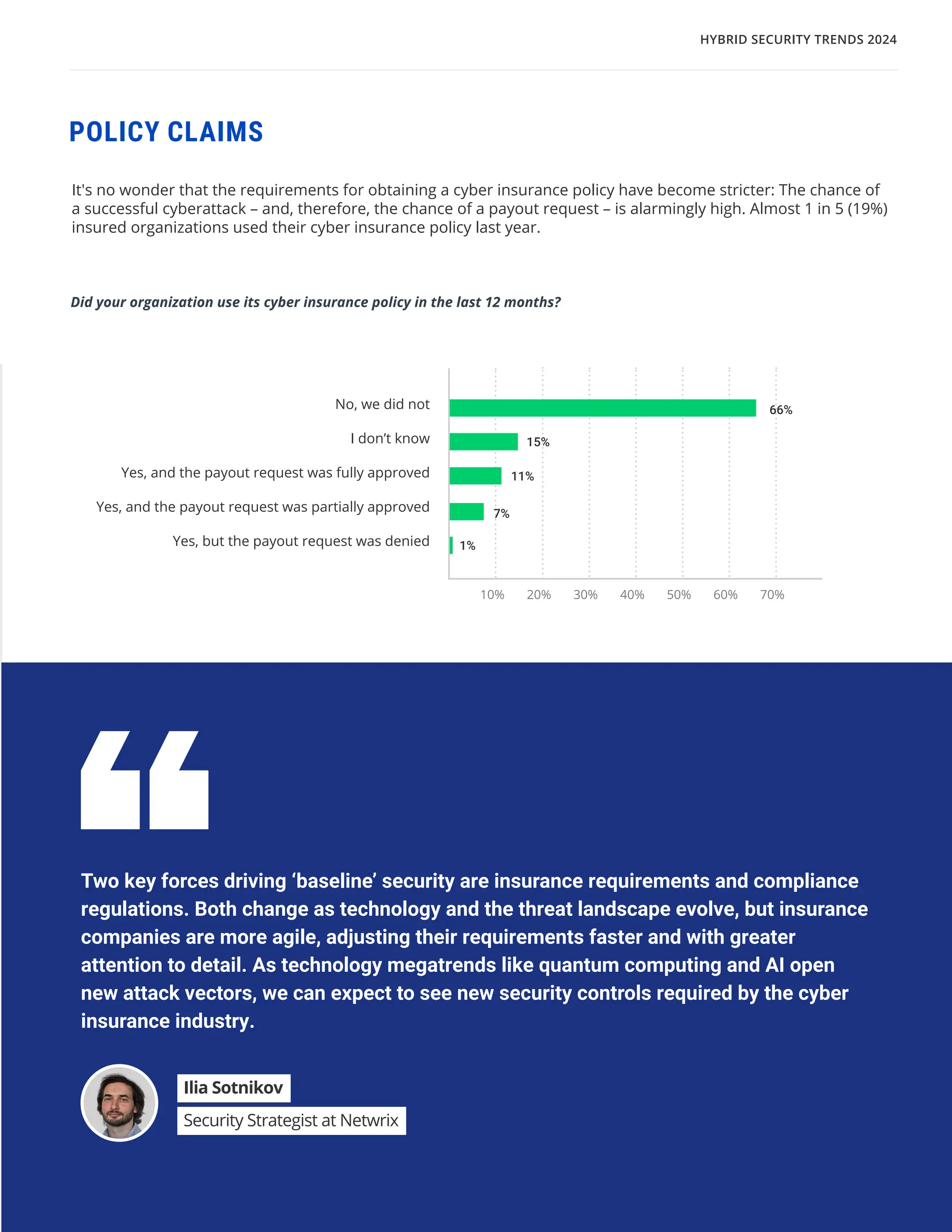
The 'Hybrid Security Trends 2024' report by Netwrix Research Lab reveals that approximately 75% of organizations now utilize a hybrid IT architecture, with a notable decrease in on-premises-only infrastructures. Security incidents have increased, with 79% of organizations reporting a cyberattack in the past year, and common incidents include phishing and account compromises, particularly in the cloud. The report emphasizes the need for organizations to enhance their security measures, focusing on identity governance and user-friendly controls to combat emerging threats.